Continuous threat exposure management, or CTEM, is a holistic approach in cybersecurity that aims to continuously identify, assess, and mitigate risks posed by cyber threats. It involves the constant monitoring of an organization’s digital assets and network infrastructure, as well as their potential vulnerabilities. It's a strategy that helps an organization stay ahead of the constantly shifting cyber threat landscape.
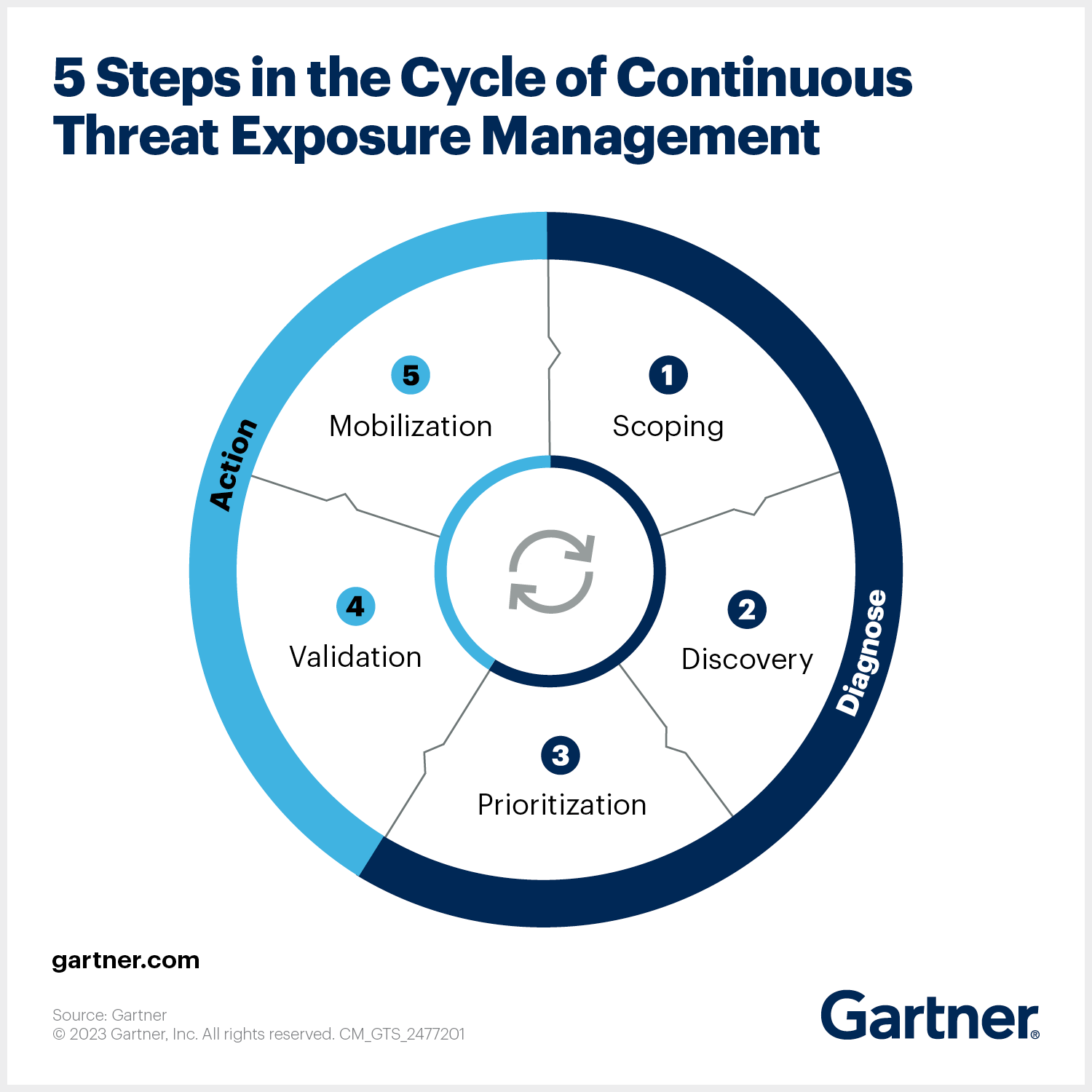
CTEM is an ongoing process that involves five stages: scoping, discovery, prioritization, validation, and mobilization. The goal is to ensure that an organization’s cybersecurity measures are always up-to-date and effective against current threats. CTEM focuses not just on the detection of threats but also on their mitigation and prevention.
The unique value of CTEM is that it helps in identifying gaps in an organization's security architecture and provides a roadmap for addressing those gaps. It fosters a proactive rather than reactive approach towards managing cyber threats and ensures that cybersecurity measures evolve in tandem with the shifting threat landscape.
This is part of a series of articles about Exposure Management.
Benefits of Implementing a CTEM Program in an Organization
Proactive Risk Management
One of the key benefits of implementing a CTEM program is its emphasis on proactive risk management. Traditional cybersecurity measures often operate on a reactive basis, addressing threats as they arise. However, this approach can leave organizations vulnerable to ever-evolving cyber threats.
CTEM maintains a proactive stance towards risk management. It involves continuous threat monitoring and identification, which allows for the early detection of potential vulnerabilities and threats. This early detection enables organizations to take preemptive actions to mitigate risks, thereby reducing the possibility of successful cyber attacks.
Prioritization of Threats
Not all threats pose the same level of risk to an organization. Some threats might pose a significant risk, while others might be less harmful. CTEM enables organizations to prioritize threats based on their potential impact, thereby allowing for more efficient resource allocation.
In a CTEM program, threats are continuously monitored and assessed. The data gathered from this process is then analyzed to determine the potential impact of each threat. This analysis enables organizations to prioritize threats and allocate resources accordingly. This approach ensures that the most critical threats are addressed first, maximizing the effectiveness of cybersecurity measures.
Actionable Insights
CTEM provides organizations with actionable insights by continuously collecting and analyzing threat data. This data provides valuable insights into the organization's security posture, the effectiveness of its security measures, and the nature of the threats it faces.
The insights provided by CTEM can be used to inform decision-making, guide the development of security strategies, and identify areas for improvement. For example, if the data reveals that a particular type of threat is consistently bypassing the organization's security measures, this information could be used to improve those measures and prevent future breaches.
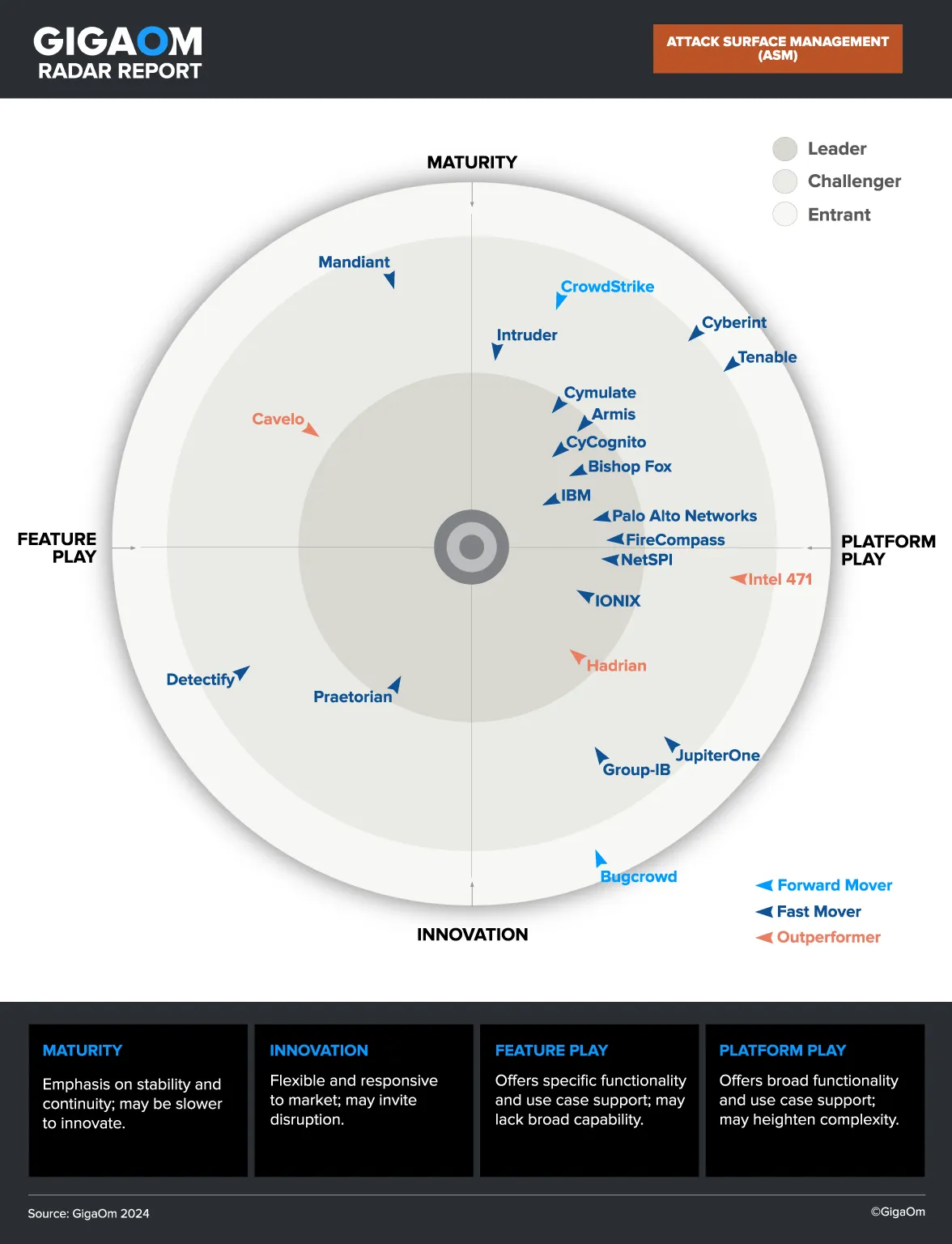
5 Stages of CTEM
1. Scoping Stage
This stage identifies an exposure assessment scope based on key business priorities and risks, considering the potential business impact of a compromise rather than primarily focusing on the severity of the threat alone.
The scoping stage is crucial for setting the groundwork for the subsequent stages by defining what will be assessed, why it's being assessed, and how it will be conducted. It helps ensure that exposure management efforts are focused, targeted, and aligned with organizational objectives and priorities.
This stage requires collaborative efforts from different departments within the organization to ensure a comprehensive understanding of the digital landscape.
2. Discovery Stage
The discovery stage will identify and classify assets, vulnerabilities, and potential threats based on the defined scope. Many tools and techniques can be used in this phase to automate discovery which often includes conducting attack surface discovery and testing, vulnerability assessments, penetration testing, and other security audits.
The discovery stage also includes threat modeling, which involves identifying potential threat actors, their motivations, and capabilities. This information is then used to map out possible attack vectors and understand the potential impact on the organization's digital assets. The discovery stage is crucial for understanding the cyber threat landscape and preparing for potential attacks.
3. Prioritization Stage
Once vulnerabilities have been identified, they must be ranked based on their potential impact and the likelihood of exploitation. The goal of exposure management is not to try to remediate every issue identified but to identify and address the threats most likely to be exploited against the organization. This prioritization process helps the organization focus its resources on the most significant threats.
During the prioritization stage, organizations also consider the cost and feasibility of implementing security controls to mitigate the identified vulnerabilities. This helps in making informed decisions about where to allocate resources and efforts. Prioritization is a critical step in the CTEM process because it ensures that the most significant threats are addressed first.
4. Validation Stage
During this stage, the organization verifies if the risk is real or if mitigation techniques can be applied without damaging the core business. Validation requires that the discovered and prioritized exposures are confirmed that attackers could really exploit the critical business asset, identify all potential attack paths, and validate that the processes to respond and remediate are fast enough and adequate for the business.
This is done through both manual and automatic validation methods. for example, with red teams and security tools, such as automated active security testing, pen testing, and breach and simulation.
The validation stage is crucial for ensuring that the organization's cybersecurity measures are effective. It also allows for adjustments and improvements to be made as necessary, making the organization's security posture more robust over time.
5. Mobilization Stage
The mobilization stage involves deploying the necessary resources to mitigate the identified threats and vulnerabilities. This could include implementing new security controls, improving existing ones, or even changing business processes to reduce exposure to threats.
The mobilization stage is not a one-time event but a continuous process. As new threats emerge and the organization’s digital landscape evolves, the CTEM process must be revisited and updated. This ensures that the organization remains proactive in managing its cyber threat exposure.
CTEM vs. Traditional Vulnerability Management Programs
Proactive vs. Reactive Approach
One of the main differences between CTEM and traditional vulnerability management programs is the approach towards threat management. While traditional programs tend to be reactive, dealing with threats as they occur, CTEM takes a proactive stance. This means that instead of waiting for a threat to materialize, CTEM aims to identify and mitigate potential vulnerabilities before they can be exploited.
Business-Aligned Prioritization
Another key difference is the way vulnerabilities are prioritized based on business impact. Traditional vulnerability management programs often prioritize vulnerabilities based on their severity, for example using the Common Vulnerability Scoring System (CVSS).
In contrast, CTEM prioritizes vulnerabilities based on their potential impact on the business from the perspective of the attackers. This ensures that resources are allocated where they can have the most significant effect on reducing business risk.
Integration with Security Controls
CTEM also differs from traditional vulnerability management programs in its integration with security controls. While traditional programs often treat security controls as separate entities, CTEM sees them as integral parts of the threat management process. This integrated approach ensures that all aspects of the organization's security posture are considered when managing cyber threats.
Emphasis on Validation
Finally, CTEM places a strong emphasis on the validation stage. This involves continuously monitoring and testing the effectiveness of security controls, something that is often overlooked in traditional vulnerability management programs. This focus on validation ensures that the required security measures are really in place, are effective, and remain effective over time.
How Can Organizations Measure the Success of Their CTEM Program?
A key aspect of CTEM programs is to measure and improve their effectiveness over time. Here are a few metrics that can help:
Mean Time to Detect (MTTD)
MTTD refers to the average time it takes for an organization to detect a cyber threat or incident. It is a crucial factor in cybersecurity as the quicker a threat is detected, the sooner it can be addressed, reducing potential damage.
Measuring the MTTD involves tracking the time from when a threat first appears to when it is detected by the organization's security systems or team. This time frame can range from a few minutes to several months, depending on the sophistication of the threat and the effectiveness of the organization's detection systems.
A shorter MTTD indicates a more effective CTEM program. It signifies that the organization's cyber threat detection systems are efficient and that the security team is vigilant and responsive.
Mean Time to Respond (MTTR)
MTTR refers to the average time it takes for an organization to respond to a detected cyber threat. The response could include investigating the threat, containing it, and initiating a recovery process.
Determining the MTTR involves recording the time from when a threat is detected to when a response is initiated. Like MTTD, a shorter MTTR is desirable as it means that the organization is quick to respond to threats, thereby limiting potential damage.
A quicker and more effective response reflects a successful CTEM program. However, CTEM alone is not enough to ensure fast MTTR. The organization must also have a robust incident response process, which is the subject of the next metric.
Incident Response Time
Incident response time refers to the total time taken to manage a cyber incident, from detection to recovery. It includes the MTTD and MTTR and the time taken to restore systems to their normal functioning.
The incident response time is an essential indicator of an organization's overall cyber threat management capability. A shorter time signifies effective incident response capabilities. However, CTEM can impact incident response times by reducing the frequency of incidents and the severity of their impact.
Vulnerability Remediation Rate
The vulnerability remediation rate measures the speed at which an organization can identify and fix vulnerabilities in its systems. Vulnerabilities are weaknesses that can be exploited by cyber threats. The quicker these vulnerabilities are remediated, the less likely they are to be exploited, reducing the organization's exposure to threats.
The vulnerability remediation rate is calculated by dividing the number of vulnerabilities remediated within a specific period by the total number of identified vulnerabilities. A higher rate indicates a more successful CTEM program.
Coverage of Assets
Coverage of assets refers to the extent to which an organization's CTEM program encompasses all critical assets, including systems, applications, and data repositories. Full coverage is vital for ensuring that no part of the organization's infrastructure is left unprotected and vulnerable to cyber threats.
Measuring coverage of assets involves auditing and mapping all assets and comparing this inventory against the assets monitored by the CTEM program. It's not just about the quantity of assets covered but also the criticality and sensitivity of these assets.
High coverage indicates a comprehensive CTEM program that leaves minimal gaps for potential threats to exploit. Conversely, low coverage could indicate areas of the digital infrastructure that are overlooked and could become points of vulnerability. This metric is fundamental in ensuring that the organization's cybersecurity measures are holistic.
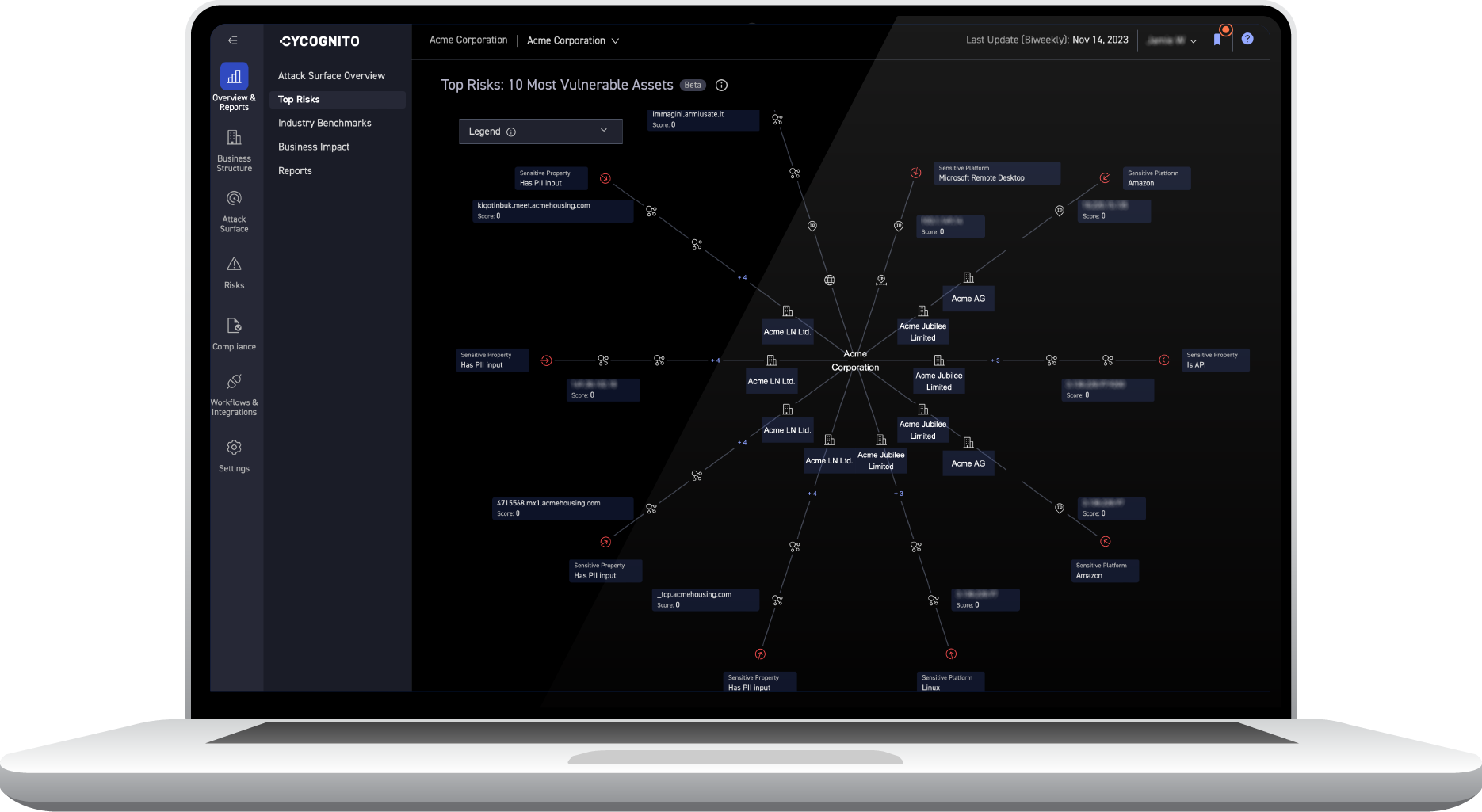
Exposure Management with CyCognito Attack Surface Management Platform
The CyCognito platform addresses today’s exposure management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining a dynamic asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Actively testing all discovered assets to identify risk. Active testing, including dynamic application security testing, or DAST, uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity. Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
Learn more about the Cycognito Attack Surface Management Platform.