What Are Vulnerability Detection Tools?
Vulnerability detection tools are software applications used to identify, assess, and manage vulnerabilities within a network or system. These tools serve to detect weaknesses that cybercriminals might exploit to gain unauthorized access to sensitive data. They scan the system, analyze the results, and provide a report detailing potential vulnerabilities, their severity, and suggested remediation actions.
The continuous evolution of cyber threats and proliferation of IT assets makes it impossible for manual efforts to keep up. Vulnerability detection tools automate this process, constantly scanning systems for known and emerging vulnerabilities, providing real-time alerts and reports, and prioritizing vulnerabilities based on their potential impact. They are an invaluable asset for any organization's cybersecurity posture.
This is part of a series of articles about vulnerability assessment.
Key Features of Vulnerability Detection Tools
Automated Scanning Capabilities
Automated scanning enables continuous monitoring of systems and networks, significantly reducing the time and resources required for vulnerability assessment. Scans can be scheduled to run at regular intervals or triggered by specific events, ensuring that no potential vulnerability goes unnoticed.
Automated scanning identifies known security vulnerabilities, but it can also detect configuration errors and other potential weaknesses that could compromise system security.
Comprehensive Vulnerability Databases
Vulnerability detection tools rely on vulnerability databases to identify known weaknesses in systems and applications. These databases are regularly updated with information about new vulnerabilities, their severity, and potential remediation measures.
These databases, which are constantly updated by security research organizations, allow vulnerability detection tools to identify and protect against both known and emerging threats.
Prioritization and Risk Assessment Features
Given the vast number of potential vulnerabilities that can be present in a system or network, it's vital to prioritize them based on their severity and potential impact. Vulnerability detection tools feature prioritization and risk assessment capabilities that automatically rank vulnerabilities based on these factors.
This prioritization allows organizations to focus their resources on addressing the most critical vulnerabilities first, ensuring that their systems and data are protected against the most potent threats.
Real-Time Alerting Systems
Some vulnerability detection tools offer real-time alerting, notifying the relevant parties as soon as a potential vulnerability is detected, to ensure immediate action is taken.
Alerts can be customized based on the severity of the vulnerability, its potential impact, and the system or application it affects. By providing real-time alerts, these tools ensure that critical vulnerabilities are promptly addressed, significantly reducing the damage they could cause.
Reporting and Compliance Support
Vulnerability reports provide an overview of the system's security posture, detailing the vulnerabilities detected, their severity, and recommended remediation actions.
These tools also support compliance efforts by providing evidence of regular vulnerability assessments and the steps taken to address identified vulnerabilities. By documenting these processes, these tools assist organizations in demonstrating their compliance with various regulatory requirements.
Integration with Development Tools
Vulnerability detection tools are much more useful when they can integrate with other development tools. This integration allows for continuous testing and assessment during the development process, identifying and addressing vulnerabilities before the software is deployed.
Developers can integrate these tools into their Integrated Development Environments (IDEs) or Continuous Integration/Continuous Deployment (CI/CD) pipelines, ensuring that code is automatically scanned for vulnerabilities at every stage of the development process. This proactive approach reduces the risk of vulnerabilities making it to the production environment.
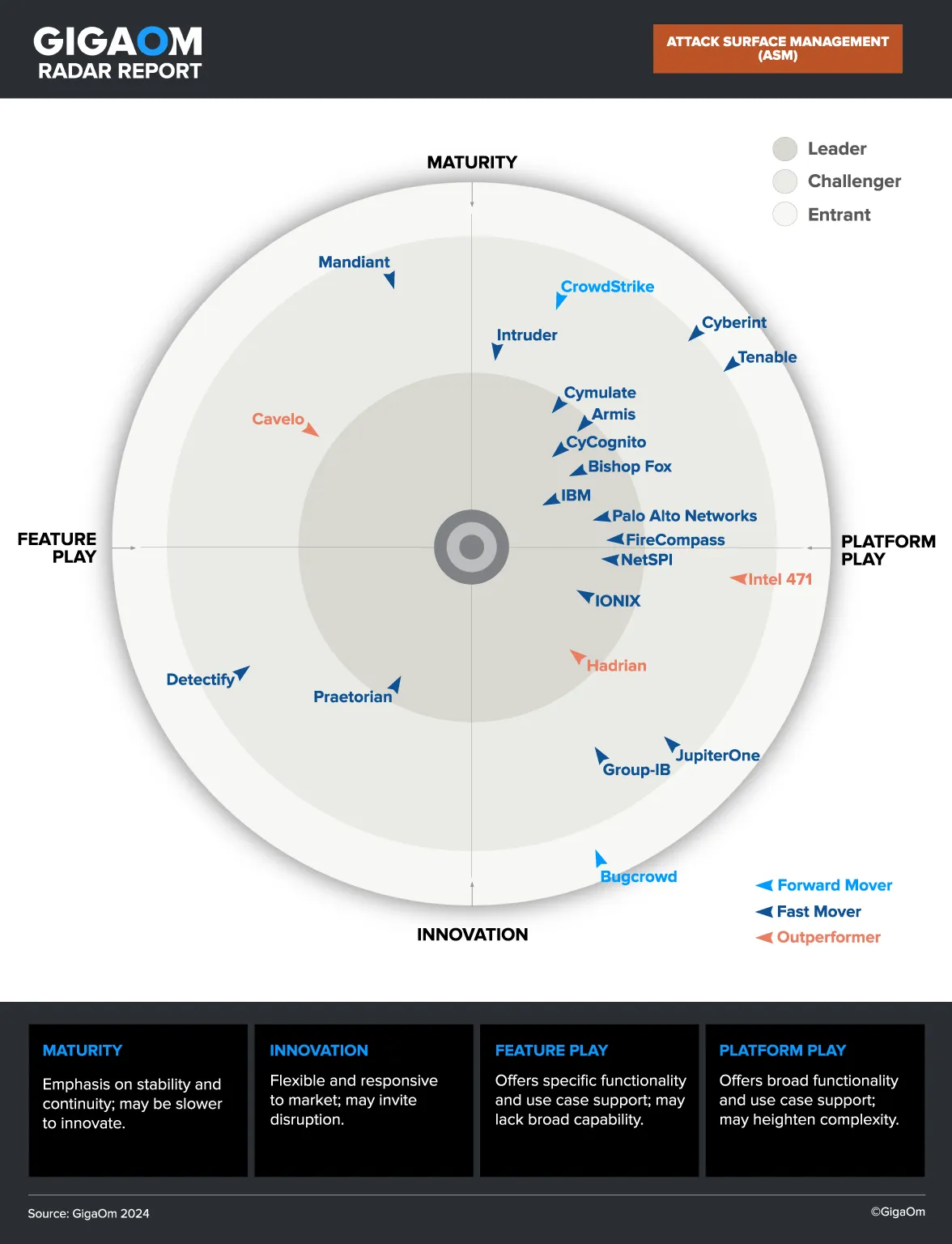
6 Notable Vulnerability Detection and Scanning Tools
1. CyCognito
The CyCognito platform addresses today’s vulnerability management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
Key features:
- Maintains a dynamic asset inventory with classification of the entire external attack surface
- Actively tests all discovered assets to identify risk
- Prioritizes critical issues, guiding security teams to focus on the most urgent threats
- Streamlines communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset
Learn more about CyCognito for vulnerability management.
2. OpenVAS
Source: Wikimedia
The Open Vulnerability Assessment Scanner (OpenVAS) is an open-source vulnerability scanner developed and maintained by Greenbone Networks, alongside a dedicated community of developers and researchers. It provides both local and cloud-based deployment options.
OpenVAS was born in 2006 as a derivative of the Nessus open source project. OpenVAS boasts similar scanning and customization features to the current Nessus products, which facilitate identification and management of vulnerabilities within individual hosts.
Key features:
- Scans systems for known threats and unpatched weaknesses
- Maintains a regularly updated list of vulnerabilities
- Identifies potential attack vectors that could lead to exploitation
- Provides in-depth remediation insights.
3. Burp Suite
Source: PortSwigger
Burp Suite Professional provides free but feature-limited tools with manual penetration testing capabilities, while the Burp Suite Enterprise Edition provides automated dynamic web vulnerability scanning. It integrates with all major bug-tracking systems and CI/CD platforms.
Burp Suite identifies bugs and vulnerabilities with an innovative approach called out-of-band application security testing (OAST). OAST can identify vulnerabilities that are difficult to detect with dynamic application security testing (DAST), such as asynchronous and blind vulnerabilities, while reducing the false positives of static application security testing (SAST).
Key features:
- Scans web applications and APIs for bugs and vulnerabilities
- Multi-user role-based access control (RBAC)
- Dashboards, issue reporting, graphs, and vulnerability reports
- Automatically generates compliance-specific reports
4. Nmap
Source: Nmap
Originally developed for Linux, the Nmap Security Scanner now provides binary packages for Windows, macOS, and Linux. It functions as a port scanner, using IP packets to determine what hosts, services, and operating systems are available from a device. Penetration testers and IT teams can use it to list open ports on a system and perform scripted vulnerability scans.
Key features:
- Quick host discovery to determine available IP addresses and open ports on a network
- Uses TCP/IP stack characteristics to guess device operating systems
- Growing library of 500 scripts for network discovery and vulnerability assessment
5. Intruder
Source: Intruder
Intruder is designed to scan cloud-based storage and networks. It is capable of managing a large number of devices. Intruder is fully automated and can constantly monitor vulnerabilities in cloud environments.
Key features:
- Integrate with popular cloud services like AWS, Azure, and Google Cloud.
- Supports both external scanning (for publicly exposed systems) and internal scanning.
- Customizable scanning profiles, allowing for targeted scanning based on unique aspects of a network.
6. Acunetix
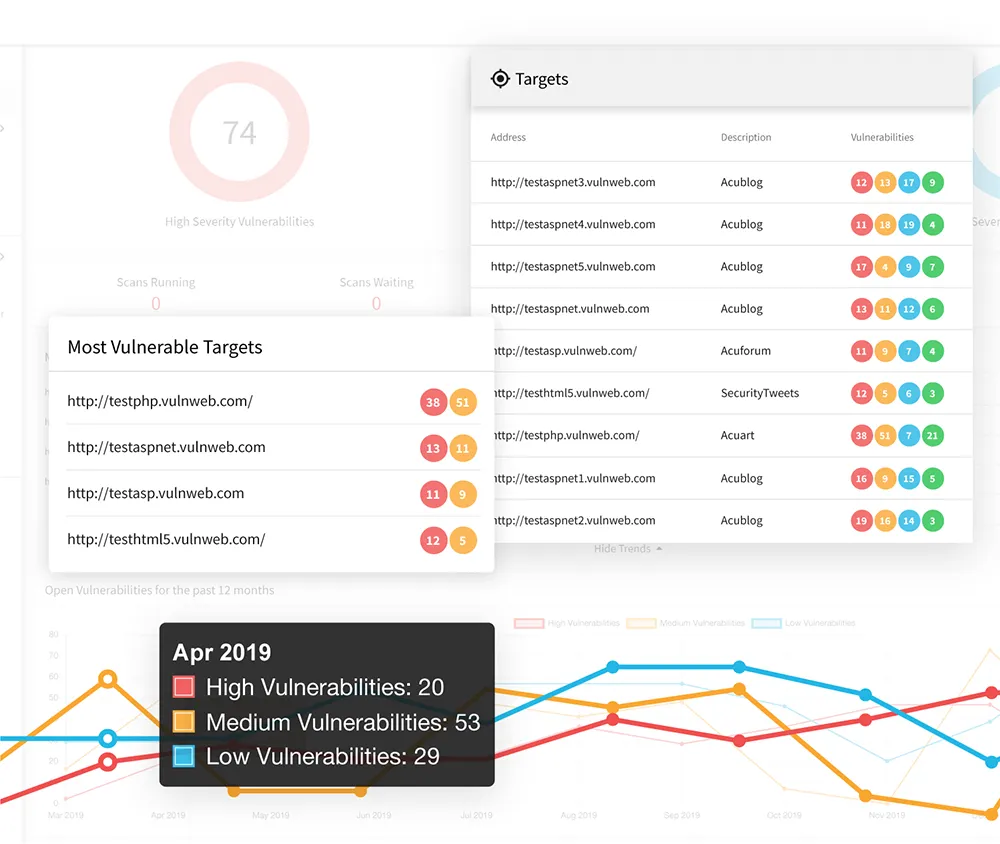
Source: Acunetix
Invicti's Acunetix is a web vulnerability scanning tool, known for its advanced crawling capabilities. It can efficiently scan any type of webpage, including those that are password-protected, identifying vulnerabilities. It is deployed on-premises or in the cloud, and is compatible with a range of operating systems including macOS, Linux, and Windows.
Acunetix uses dynamic application security testing (DAST) technology to detect vulnerabilities from an attacker’s perspective, and also provides network security scanning and interactive application security testing (IAST) capabilities.
Key features:
- IAST scanning engine can discover over 7,000 vulnerabilities in Java, PHP, or .NET code.
- Capable of scanning complex application paths and multi-level forms.
- Can effectively scan single page applications (SPAs), password-protected areas, unlinked pages, and websites with JavaScript or HTML5 scripts.
- Integrates with OpenVAS to enable network security scanning.
Related content: Read our guide to vulnerability scanning tools (coming soon)
Conclusion
In conclusion, vulnerability detection tools are essential in today's IT environment, where the complexity and frequency of cyber threats is on the rise. These tools automate the process of detecting vulnerabilities and also provide access to extensive vulnerability databases, prioritization of risks, real-time alerting, and integration with software development processes.
Vulnerability detection tools are essential for maintaining an organization's cybersecurity posture, ensuring that vulnerabilities are identified, assessed, and remediated promptly. These tools play a critical role in safeguarding sensitive data and systems, and can also assist in compliance with regulations and industry standards.
Learn more about the CyCognito Platform.