What Is Cloud Application Security?
Cloud application security is the discipline and process of protecting cloud-based applications from external and internal threats, as well as ensuring compliance with relevant regulations. It encompasses a range of policies, technologies, applications, and controls utilized to secure cloud environments.
This security domain requires a specialized approach compared to traditional IT security, as it deals with securing data across various cloud platforms and service models (IaaS, PaaS, and SaaS). It involves managing access, protecting the integrity of data in transit and at rest, and ensuring that applications are free from weaknesses that could be exploited by attackers.
The Importance of Cloud Application Security
As organizations migrate more of their data and applications to the cloud, the potential impact of security breaches magnifies. Ensuring the security of cloud applications is crucial for the protection of sensitive data and for maintaining customer trust and compliance with data protection laws.
A robust cloud application security strategy also supports business continuity by preventing outages and attacks that could disrupt operations. It enables organizations to take advantage of cloud computing services while minimizing risks, ensuring a secure and resilient digital environment for their operations.
Cloud Application Security Threats and Risks
Here are some of the main security threats and risks affecting applications in the cloud.
Insecure APIs
Application programming interfaces (APIs) serve as the primary mode of interaction and communication between cloud services and clients. Insecure APIs expose applications to various security risks, including unauthorized access and data breaches. Ensuring APIs are secure involves implementing strong authentication, encryption, and access controls.
Lack of secure coding practices can result in vulnerabilities within APIs that attackers can exploit. Therefore, organizations need to adopt comprehensive security testing and monitoring strategies for APIs to detect and mitigate potential threats promptly.
Cloud Misconfiguration
Misconfiguration is one of the most common security risks in the cloud, arising from improper setup and management of cloud resources. These vulnerabilities can lead to unauthorized access, data leaks, and service disruptions.
Organizations can prevent misconfigurations by employing automated compliance checks and management tools. Regular audits of cloud environments help ensure that configurations align with the organization’s security standards and best practices.
Phishing and Social Engineering
Phishing and social engineering tactics exploit human vulnerabilities to gain unauthorized access to cloud applications. Attackers deceive users into providing sensitive information or executing malicious actions.
Combatting these threats requires ongoing user education on recognizing phishing attempts and implementing advanced email filtering technologies. Additionally, organizations should enforce strict policies and verification processes for sensitive operations.
Account Hijacking
Cloud accounts are often hijacked through phishing, malware, or credential misuse. Attackers gaining control of a user's account can access sensitive data, manipulate services, and potentially compromise other accounts within the same network.
To mitigate these risks, organizations should employ two-factor authentication, rigorous access management practices, and educate users on recognizing and avoiding phishing attempts.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks are a prevalent threat to cloud applications, aiming to overwhelm resources and disrupt service availability. These attacks are challenging to defend against and demand scalable, intelligent solutions.
Cloud services typically offer defensive measures against DDoS attacks, but organizations should also consider additional protection. These include traffic analysis and filtering, overprovisioning bandwidth, and implementing dedicated DDoS protection services.
Bots and Automated Attacks
Bots and automated attacks target cloud applications to steal data, disrupt services, or launch further attacks. Protecting against such threats involves deploying bot management solutions that can distinguish between legitimate traffic and malicious bots.
Regularly updating applications and infrastructure to patch vulnerabilities is also crucial in preventing automated attacks. The use of Web Application Firewalls (WAFs) and rate limiting can further reduce the risk of bot-related incidents.
Types of Cloud Application Security Technologies and Tools
There are several types of security solutions that are specifically designed for cloud computing environments
Cloud Access Security Broker (CASB)
CASBs act as intermediaries between users and cloud services, offering visibility, compliance, data security, and threat protection. They enable organizations to extend their security policies to the cloud and monitor user activity and sensitive data movement across apps.
CASBs can enforce access controls, encrypt sensitive data, and identify risky behaviors. They help in aligning cloud usage with an organization's security requirements.
Cloud Workload Protection Platform (CWPP)
CWPPs focus on protecting workloads such as virtual machines, containers, and serverless functions, across various cloud environments, including IaaS and PaaS. They offer capabilities such as system integrity monitoring, vulnerability management, and network security. By securing workloads from potential attacks and vulnerabilities, CWPPs can detect and mitigate risks in dynamic cloud ecosystems.
Cloud Security Posture Management (CSPM)
CSPM tools automate the identification and remediation of risks across cloud infrastructure. They provide continuous compliance monitoring, security assessment, and the management of cloud misconfigurations.
Implementing CSPM helps organizations enhance their security posture by proactively identifying vulnerabilities and ensuring compliance with industry standards. This proactive approach to cloud security management is useful for avoiding potential breaches and maintaining operational integrity.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM solutions manage identities and access entitlements within cloud environments, addressing the complexity of cloud access policies and permissions. They help in enforcing the principle of least privilege and identifying excessive permissions that could be exploited by attackers.
By continuously monitoring and managing cloud access entitlements, CIEMs contribute to reducing the risk of unauthorized access and potential insider threats, ensuring that only necessary access rights are granted.
Cloud-Native Application Protection Platform (CNAPP)
A Cloud-Native Application Protection Platform (CNAPP) is a security solution that combines several security tools to protect cloud-native applications throughout their development and deployment lifecycle. According to Gartner, CNAPP includes capabilities like Cloud Workload Protection Platforms (CWPP), Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM), and vulnerability assessment—all integrated into one cohesive platform.
Related content: Read our guide to DAST tools.
Cloud Application Security Best Practices
Here are some important practices for securing cloud applications.
1. Enforce the Principle of Least Privilege
The principle of least privilege (PoLP) necessitates granting users and systems the minimum level of access required to perform their functions. Implementing the PoLP reduces the attack surface of cloud applications by limiting opportunities for unauthorized access and data breaches.
This approach involves regular reviews and adjustments of access rights, ensuring that permissions align with the current needs and roles of users. Automation can also aid in managing and monitoring access controls.
2. Implement Strong Password Policies
Policies for strong passwords are critical in protecting accounts and services from unauthorized access. These policies should mandate the use of complex passwords that are difficult to guess and incorporate multi-factor authentication (MFA) where possible.
Educating users on creating strong passwords and the importance of password security can further reinforce defenses against account compromise. Regularly updating passwords and using password management tools can help maintain password hygiene.
3. Apply Cloud Governance Policies
Implementing effective cloud governance policies ensures that the usage of cloud services aligns with an organization's security requirements and compliance obligations. Governance encompasses risk management, regulatory compliance, and operational control.
By establishing clear guidelines for cloud adoption and usage, organizations can maintain control over their cloud environments, mitigate risks, and ensure compliance. Cloud governance should also foster a culture of security and accountability, supporting safe cloud operations.
4. Monitor the Attack Surface
Continuous monitoring of the attack surface is vital to detecting and responding to cloud application threats in a timely manner. This includes tracking changes in the cloud environment, identifying vulnerabilities, and assessing the efficacy of security controls.
Utilizing security monitoring tools and services that offer real-time insights and analytics can enable organizations to quickly identify suspicious activities and mitigate potential threats. A proactive monitoring strategy enhances the organization’s security posture and operational resilience.
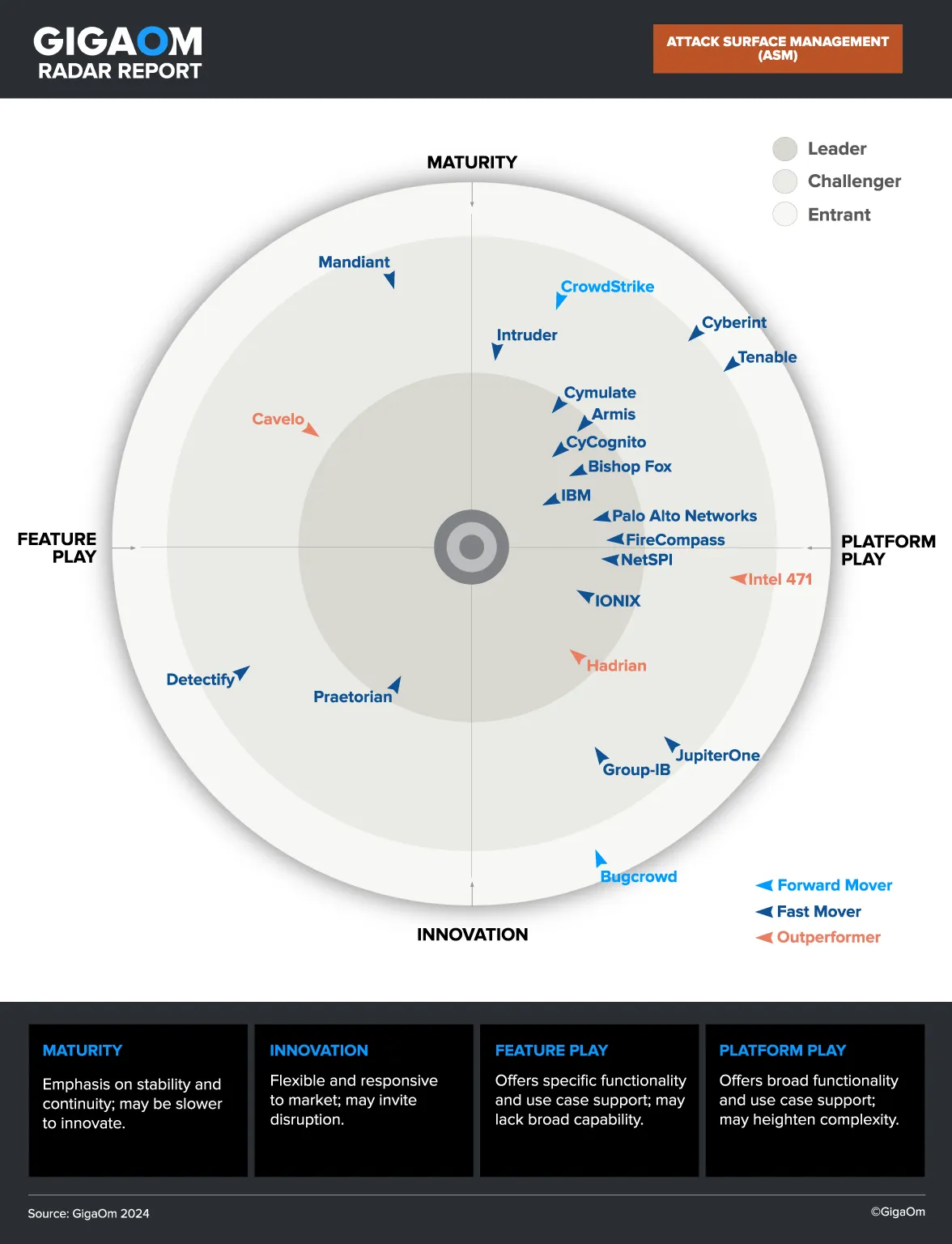
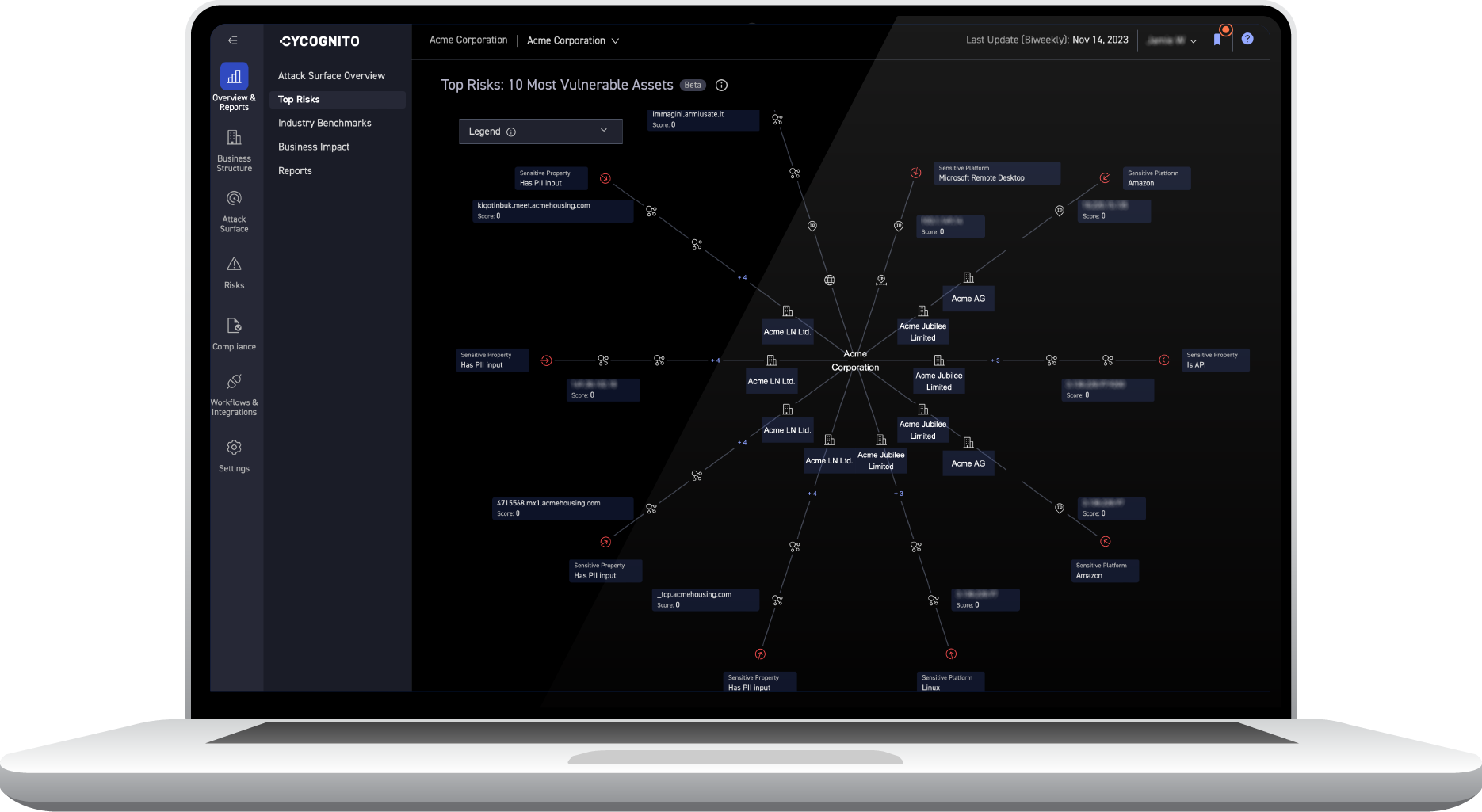
Cloud Application Security with CyCognito
CyCognito identifies application security risks through scalable, continuous, and comprehensive active testing that ensures a fortified security posture for all external assets.
The CyCognito platform helps secure cloud applications by:
- Using dedicated cloud connectors for AWS, Azure, and GCP to directly identify and test cloud assets in critical environments.
- Using payload-based active tests to provide complete visibility into any vulnerability, weakness, or risk in your attack surface.
- Going beyond traditional passive scanning methods and targeting vulnerabilities invisible to traditional port scanners.
- Employing dynamic application security testing (DAST) to effectively identify critical web application issues, including those listed in the OWASP Top 10 and web security testing guides.
- Eliminating gaps in testing coverage, uncovering risks, and reducing complexity and costs. Offering comprehensive visibility into any risks present in the attack surface, extending beyond the limitations of software-version based detection tools.
- Continuously testing all exposed assets and ensuring that security vulnerabilities are discovered quickly across the entire attack surface.
- Assessing complex issues like exposed web applications, default logins, vulnerable shared libraries, exposed sensitive data, and misconfigured cloud environments that can’t be evaluated by passive scanning.
CyCognito makes managing web application security simple by identifying and testing these assets automatically, continuously, and at scale using CyCognito’s enterprise-grade testing infrastructure.
Learn more about CyCognito Active Security Testing.