Dynamic application security testing, a type of black-box testing, is a technique used to assess the security of web applications by simulating real-world attacks. Unlike SAST, which analyzes the source code of an application, DAST examines the application in its running state. It focuses on identifying security weaknesses that can be exploited by hackers to gain unauthorized access, compromise data, or disrupt the functionality of the application.
DAST involves sending a series of carefully crafted requests to the target application, mimicking various attack scenarios. The tool then analyzes the responses received from the application, looking for any indications of security weaknesses. By taking this approach, DAST can assess the application's security posture, detecting exposures that may have been missed during the development process.
How Does DAST Work?
Scanning
The first stage in the DAST process is scanning. During this stage, the DAST tool scans the entire web application to create a map of its pages and functionalities. The tool crawls through the application, exploring every page, every form, and every function. This thorough exploration allows it to understand the structure of the application, which is crucial for the next stage.
Attack Simulation
After the scanning stage, the DAST tool proceeds to the attack simulation stage. During this stage, the DAST tool simulates various attack scenarios to test the application's response. The tool uses the map generated during the scanning stage to simulate attacks on different parts of the application.
The simulated attacks can range from inputting malicious data into form fields to executing complex attack sequences. The aim of this stage is to identify security weaknesses that an attacker could exploit. The DAST tool uses different techniques to simulate these attacks, including fuzzing and injection.
Assessment
During this stage, the DAST tool analyzes the responses from the application during the attack simulation stage. It checks for abnormal behavior or responses that indicate a vulnerability.
For example, if the application returns a database error after the tool inputs unexpected data into a form field, it could indicate a SQL Injection vulnerability. By analyzing the application's responses, the DAST tool can identify potential security issues that need to be addressed.
Reporting
The final stage in the DAST process is reporting. Once the tool has identified potential issues, it generates a comprehensive report detailing its findings. This report includes information about the identified security issues, their potential impact, and recommendations for fixing them.
The report serves as a guide for developers, helping them understand where the exposures lie and how they can fix them. By following the recommendations in the report, developers can improve the security of their application, making it more robust against potential attacks.
DAST vs. SAST
While both DAST and SAST are essential components of an application security strategy, they play different roles. SAST primarily focuses on identifying security issues in the source code of an application during the development phase. It scans the codebase to detect potential coding errors, insecure coding practices, and other issues that may lead to security breaches. However, SAST may not be able to identify exposures that arise due to the configuration or runtime behavior of the application.
On the other hand, DAST provides a holistic assessment of the application's security by analyzing it in its running state. It identifies exposures that may be introduced due to misconfigurations, insecure server settings, or other factors that may affect the application's security posture. DAST also simulates real-world attack scenarios, making it an effective technique for identifying security weaknesses that can be exploited by hackers.
DAST Benefits
Detecting Runtime Issues
Dynamic application security testing stands out from other testing methods due to its ability to detect security issues during the runtime of an application. DAST can help understand how an application behaves when it interacts with external elements, such as user input or server responses.
DAST can detect runtime issues like session management flaws, insecure direct object references (IDOR), and cross-site scripting (XSS) vulnerabilities. Furthermore, by detecting runtime issues, DAST enables us to understand the security posture of an application from an attacker's perspective. This offers a proactive approach to application security, where developers can anticipate and mitigate potential attacks before they are exploited.
Low False Positive Rates
In the field of cybersecurity, false positives—alerts indicating a potential security issue where none exists—can be a significant drain on resources. Because DAST actively tests software for exposures, it can accurately pinpoint real security issues.
DAST engages with the application, interacting with it much like an attacker would. This active engagement results in a more accurate picture of potential exposures, leading to a reduction in false positives.
Language Agnostic
Many applications are developed in a multitude of programming languages, and organizations often maintain applications that are built using different technologies. Each language comes with its distinct security implications and weaknesses.
Because DAST interacts with the running application, rather than its source code, it is language agnostic and can be used to test any web application. This feature makes DAST an extremely versatile tool in a multi-language environment.
DAST Limitations
Late Appearance in SDLC
DAST tests applications when they are in a running state, which usually means that the application has reached the later stages of development. If a significant security flaw is detected at this stage, resolving it might require substantial code changes, leading to potentially costly and time-consuming revisions. This makes it important to complement DAST with tools like SAST that can identify security issues early in the software development lifecycle (SDLC).
Identifying Exposure Location in Code
Another limitation of DAST is related to pinpointing the location of exposures within the application's source code. While DAST excels at identifying security issues during runtime, it does not provide specific information about where these issues are located in the code. This can make it more difficult to identify and remediate security issues.
Code Coverage
Due to its dynamic nature, DAST can only test the parts of an application that it can interact with during runtime. This means that certain areas of the code that are not executed during the test will remain unchecked. Again, this can be mitigated by combining DAST with SAST or other source code analysis tools that can offer full code coverage.
Only Covers Known Applications
DAST solutions do not include discovery features, so they are limited to assets already known to IT or security teams. This means that if an application or a service is not explicitly included in the DAST scan scope, it will remain untested.
This limitation can pose a problem in larger environments where new applications and services are regularly deployed, and in organizations operating in cloud environments where new applications and services can be deployed dynamically on a daily basis.
Best Practices for Implementing DAST Tools
Here are a few best practices that can help your organization implement DAST effectively in a development environment.
Regular and Consistent Testing
It is important to routinely examine applications to identify potential new security issues. The frequency of your testing should be determined by factors like the complexity of your applications, the rate at which they're updated, and the potential impact of a security breach. For instance, if your applications undergo frequent changes, you may need to conduct DAST more often to ensure that no new security issues have been introduced.
Integrating Automated and Manual Testing Efforts
Automated tools like DAST may miss certain exposures, especially those that require a nuanced understanding of the application's functionality. To mitigate this, it's imperative to integrate automated and manual testing efforts. Manual testing methods, such as penetration testing, allow for a more in-depth analysis of potential security issues, while automated testing helps to quickly identify a wide range of potential issues.
A common way to combine automated and manual testing is to use tools like DAST for an initial sweep of your applications, identifying obvious exposures, and following up with manual testing for deeper investigation and discovery of additional weaknesses.
Prioritizing and Remediating Detected Exposures
Not all exposures pose the same level of risk. Some may have a minor impact on your application's functionality, while others can lead to serious security breaches. It's crucial to prioritize detected security issues based on their potential impact.
Once exposures have been identified and prioritized, it's time to address them. This involves creating a remediation plan that outlines the steps needed to fix each vulnerability. The plan should include the resources required, the estimated timeline, and the potential impact on the application's functionality.
Learn more in our detailed guide to DAST tools (coming soon)
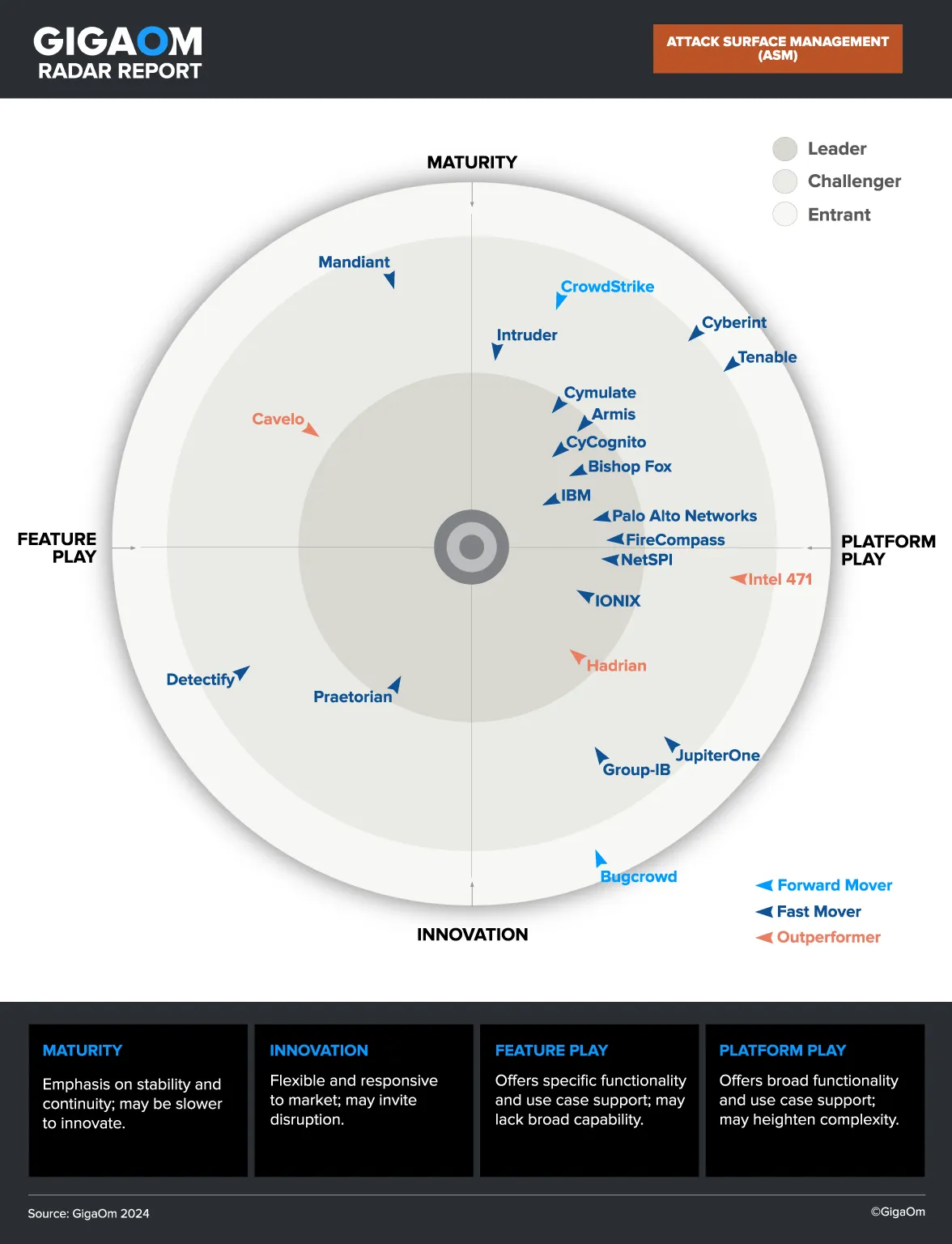
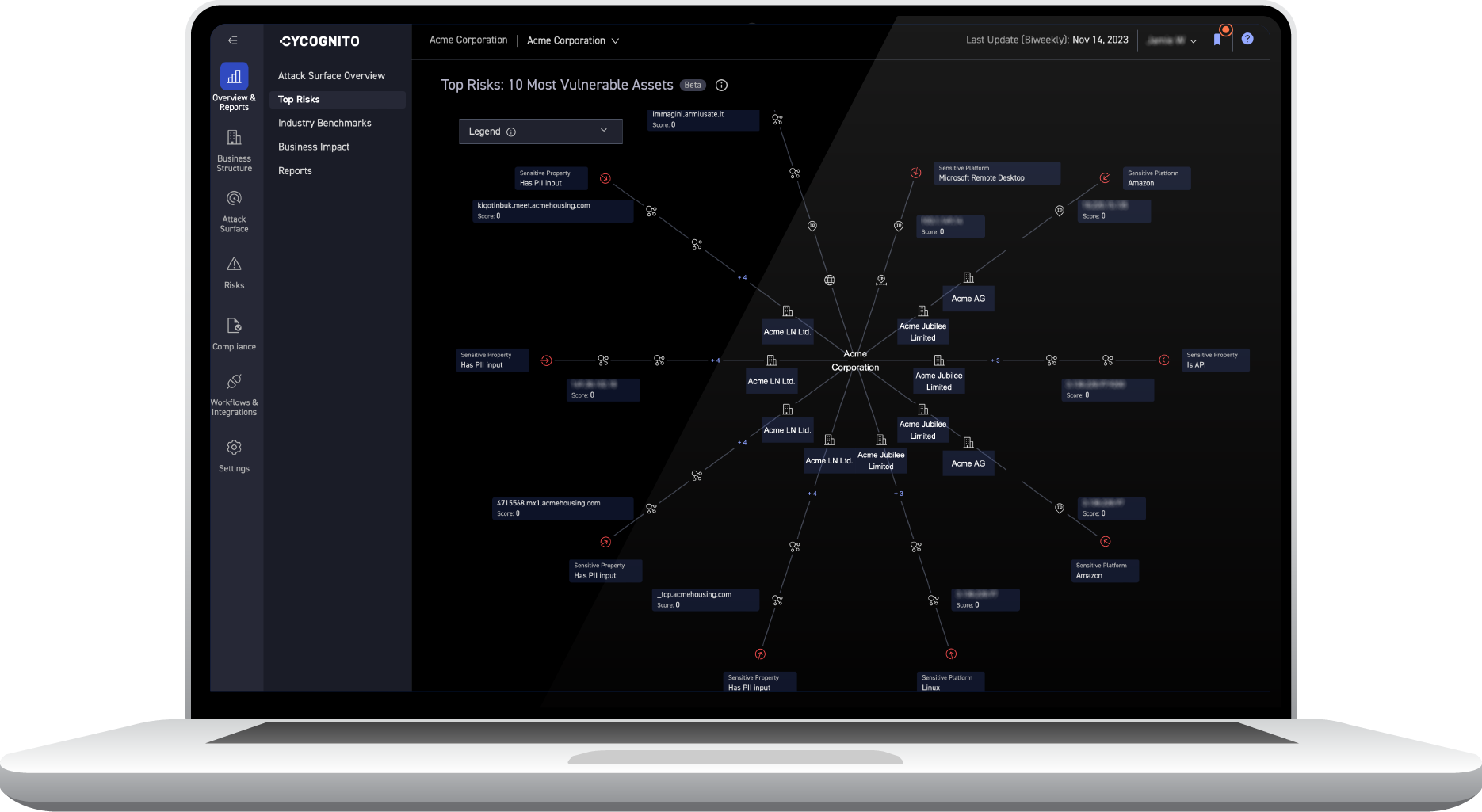
How CyCognito DAST Tests Exposed Web Applications
Most organizations test only a fraction of exposed applications. CyCognito’s integrated active testing, or DAST, is performed across the full application inventory, not just those pre-identified or tied to a portion of IP ranges.
CyCognito’s DAST detects exploitable application code, identifying complex risks that include sensitive data exposure, authentication issues, vulnerable content management systems, default credentials, certificate validity issues, and OWASP top 10 issues (e.g. injection attacks, broken access control, etc.)
Through CyCognito, organizations:
- Test for tens of thousands of attacks: CyCognito’s payload-based active testing, including DAST, provides comprehensive visibility into complex risks.
- Test the entire external asset inventory: CyCognito’s active testing is integrated with the CyCognito asset discovery and contextualization engine. This eliminates visibility gaps and removes manual effort.
- Eliminate asset resource impact: CyCognito’s active testing is architected as “low and slow” and is monitored carefully. This enables production systems to be tested without impact or need for complex scheduling.
- Achieve >90% confidence: CyCognito’s active testing has >90% accuracy in identifying risk exposures. High accuracy and low false positives lead to confident IT security staff and faster MTTR.
- Validate remediation efforts: CyCognito’s active testing is automatic and continuous. Only active testing can confidently validate remediation remediation efforts.
CyCognito takes the burden and costs out of managing security testing; recon and security tests are completed automatically, at scale, using CyCognito’s enterprise-grade testing infrastructure.
Learn more about CyCognito Automated Security Testing.