What Is a Web Application Firewall (WAF)?
A web application firewall, abbreviated as WAF, is a specific form of firewall designed to monitor, filter, and block data packets as they travel to and from a web application. A WAF does this by adhering to a set of policies that help determine what traffic is malicious and what is safe. These policies are typically based on the various common vulnerabilities found in web applications.
WAF serves as a protective shield between a web application and the internet. It operates at the application layer (layer 7 of the OSI model) and can protect web applications from attacks such as cross-site scripting (XSS), SQL injection, and cookie poisoning. It's important to note that while a traditional firewall and a WAF both aim to protect assets and applications within a network, they do so in different ways and on different layers of a network.
This is part of a series of articles about application security.
The Importance of WAF in Protecting Web Applications
Protection Against Common Vulnerabilities
A WAF guards web applications against the most common vulnerabilities exploited by cybercriminals. While it does not fix the underlying vulnerabilities in a web application, it can detect and block attempts by cybercriminals to exploit them.
For instance, a WAF can protect against attacks like cross-site scripting (XSS), where malicious scripts are injected into trusted websites. It can also guard against SQL injection, where an attacker can manipulate a site's database by inserting malicious SQL statements. It does this by intercepting traffic exhibiting known attack patterns and blocking it before it can do harm.
Customizable Security Rules
There are many business applications, and each organization might have unique access patterns or configurations. With customizable security rules, a WAF can be tailored to fit the specific security requirements of a web application.
For example, an eCommerce site might need to prioritize protection against credit card fraud, while a content site might be more concerned about preventing comment spam. Customizable security rules allow businesses to prioritize their defenses based on their unique risk profiles.
Blocking Malicious Traffic
Another critical role of a WAF is blocking malicious traffic. A WAF can analyze all incoming traffic and block requests that appear to be malicious. This can include requests from known malicious IP addresses, requests that include malicious payloads, or requests that are designed to exploit known vulnerabilities.
By blocking malicious traffic, a WAF prevents potential attacks before they reach the web application. This proactive approach to security helps to prevent potential breaches and maintain the integrity of the web application.
API Protection
With the increasing use of APIs in modern web development, protecting them has become a crucial aspect of web application security. APIs can be a point of vulnerability, as they often allow third-party applications to interact with a web application's data. A WAF can provide critical protection for APIs, ensuring that only legitimate requests are allowed.
Through its rule-based approach, a WAF can identify and block malicious API calls, protecting the web application from potential attacks. This can include attempts to access sensitive data, denial-of-service attacks, or attempts to manipulate the API's functionality.
Reduction of Security Management Complexity
Managing web application security can be a complex task, with many different elements to consider. A WAF helps to reduce this complexity by serving as a centralized security solution. Instead of having to manage multiple different security tools, businesses can rely on a WAF to provide comprehensive protection for their web applications.
This can also help to reduce the potential for security gaps, as all traffic is analyzed and filtered through the same set of rules. It can also make it easier to update and manage security policies, as changes can be made centrally and then applied across the entire web application.
Related content: Read our guide to application security testing (coming soon)
6 WAF Cybersecurity Capabilities
While different WAF solutions might have different capabilities, here are the main features provided by most modern WAFs:
1. Rule-Based Traffic Filtering
Rule-based traffic filtering involves analyzing all incoming and outgoing traffic based on a set of rules, which can be tailored to the specific security needs of a web application.
For example, a rule might be set up to block all traffic from a specific IP address or to block requests that include a specific type of payload. This rule-based approach allows for a high degree of precision in identifying and blocking potential threats.
2. Customizable Security Policies
In addition to rule-based traffic filtering, a WAF also offers the ability to create customizable security policies.
For example, a security policy might be set up to require all users to authenticate before accessing certain parts of a web application. Some WAFs even provide built-in authentication mechanisms. Or, a policy might be set up to block all traffic from a specific country, if that country is known to be a source of many cyberattacks.
These customizable security policies allow businesses to take a proactive approach to security, defining their own rules and policies based on their unique risk profiles.
3. Application Profiling and Allowlisting
Application profiling involves understanding the normal behavior of an application in order to detect abnormal activity. It's a proactive way of identifying potential security threats before they cause harm.
Allowlisting involves allowing only approved traffic to access your web applications. This is achieved by creating a list of trusted traffic sources, such as IP address ranges or domains. Any traffic outside of this list is automatically blocked.
4. Rate Limiting and Bot Management
Rate limiting involves limiting the number of requests a user or IP address can make within a certain timeframe. By doing so, it helps prevent denial-of-service (DoS) attacks, which seek to overwhelm your web application with traffic to cause a crash, or brute force attacks that try to cycle through login credentials to gain unauthorized access.
Bot management involves identifying and managing automated web traffic, also known as bots. While some bots are harmless, others can be malicious, carrying out activities such as web scraping, credential stuffing, and automated vulnerability scanning. WAFs can identify bad bots and prevent them from accessing a web application, while allowing legitimate bots like search engine crawlers.
5. SSL/TLS Offloading and Inspection
SSL/TLS offloading and inspection is a feature of WAF security that helps manage encrypted traffic. It involves transferring the processing of SSL/TLS encryption and decryption from your web server to the WAF. This helps improve the performance of your web server by freeing up its resources.
SSL/TLS inspection is a complementary feature that decrypts and inspects encrypted traffic for potential threats. It can help identify hidden attacks that could otherwise bypass your security measures.
6. Integration with Other Security Solutions
WAFs commonly integrate with other security solutions such as Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and Security Information and Event Management (SIEM) systems. This integrated approach enhances overall security by combining the strengths of each system.
Integration with IDS and IPS allows the WAF to benefit from additional layers of network monitoring and protection. For example, while the WAF focuses on application-layer threats, the IDS can monitor network traffic for signs of suspicious activity, and the IPS can actively block identified threats.
Similarly, integration with SIEM systems can help centralize the management of security events and logs. SIEM systems aggregate and analyze data from various sources, including WAFs, to identify broader cyber threat patterns. This integration enables faster detection of complex attacks and improves incident response times.
Tips for Effectively Implementing WAF Security in Your Organization
Here are a few best practices that can help you make the most of WAF security solutions in your organization.
Regularly Update and Review Security Rules
To maintain effective security, it's crucial to keep the WAF's security rules up-to-date. Cyber threats evolve rapidly, and security rules must be revised regularly to address new vulnerabilities and attack patterns. Regular updates ensure that the WAF is equipped to identify and block the latest threats.
Additionally, reviewing existing rules is important to minimize false positives and ensure legitimate traffic is not inadvertently blocked. This process might involve analyzing traffic logs, adjusting sensitivity levels, and customizing rules to align with changing web application functionalities or usage patterns.
Conduct Periodic Security Audits and Reviews
Periodic security audits and reviews are essential to identify potential gaps in the WAF’s protection. These audits should include a comprehensive examination of the WAF's configuration, the effectiveness of its rules, and its integration with other security systems.
Regular reviews enable organizations to assess the WAF's performance in real-world scenarios, ensuring that it is effectively protecting against actual threats. These audits can also help in understanding user behavior patterns, refining security policies, and ensuring compliance with relevant regulations and industry standards.
Enable Real-time Monitoring and Alerts
Enabling real-time monitoring and setting up alerts is vital for immediate detection and response to potential security incidents. Real-time monitoring allows security teams to track all traffic passing through the WAF and quickly identify suspicious activities.
Customizable alerts can be set up based on specific criteria, such as repeated login failures, traffic spikes, or attempts to access restricted areas. These alerts enable security teams to respond promptly to potential threats, minimizing the risk of a data breach or other security incident.
Integrate WAF with Threat Intelligence
Integrating the WAF with threat intelligence feeds enhances its capability to preemptively block emerging threats. Threat intelligence involves gathering and analyzing information about new and existing cyber threats from various sources.
By integrating this intelligence, the WAF can be updated in real-time with information about new attack vectors, malware signatures, and IP addresses associated with malicious activities. This proactive approach allows the WAF to secure web applications against even the most recent and sophisticated threats.
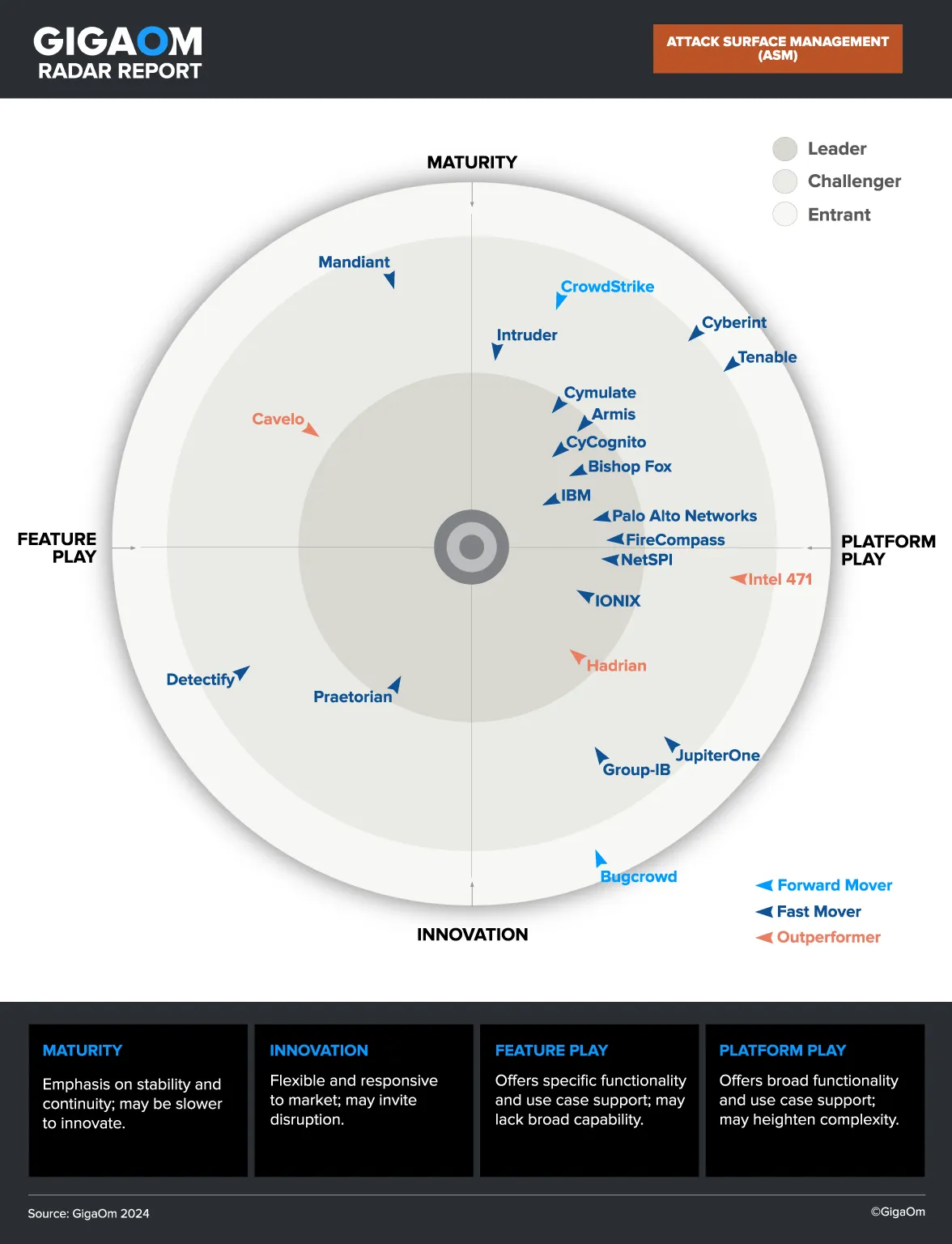
Enhancing WAF Security with CyCognito Attack Surface Management
Web applications are an essential part of the external attack surface and WAFs are an excellent starting point to protect these vital assets, but WAFs still need to be continuously monitored, tested, and adjusted to provide complete coverage.
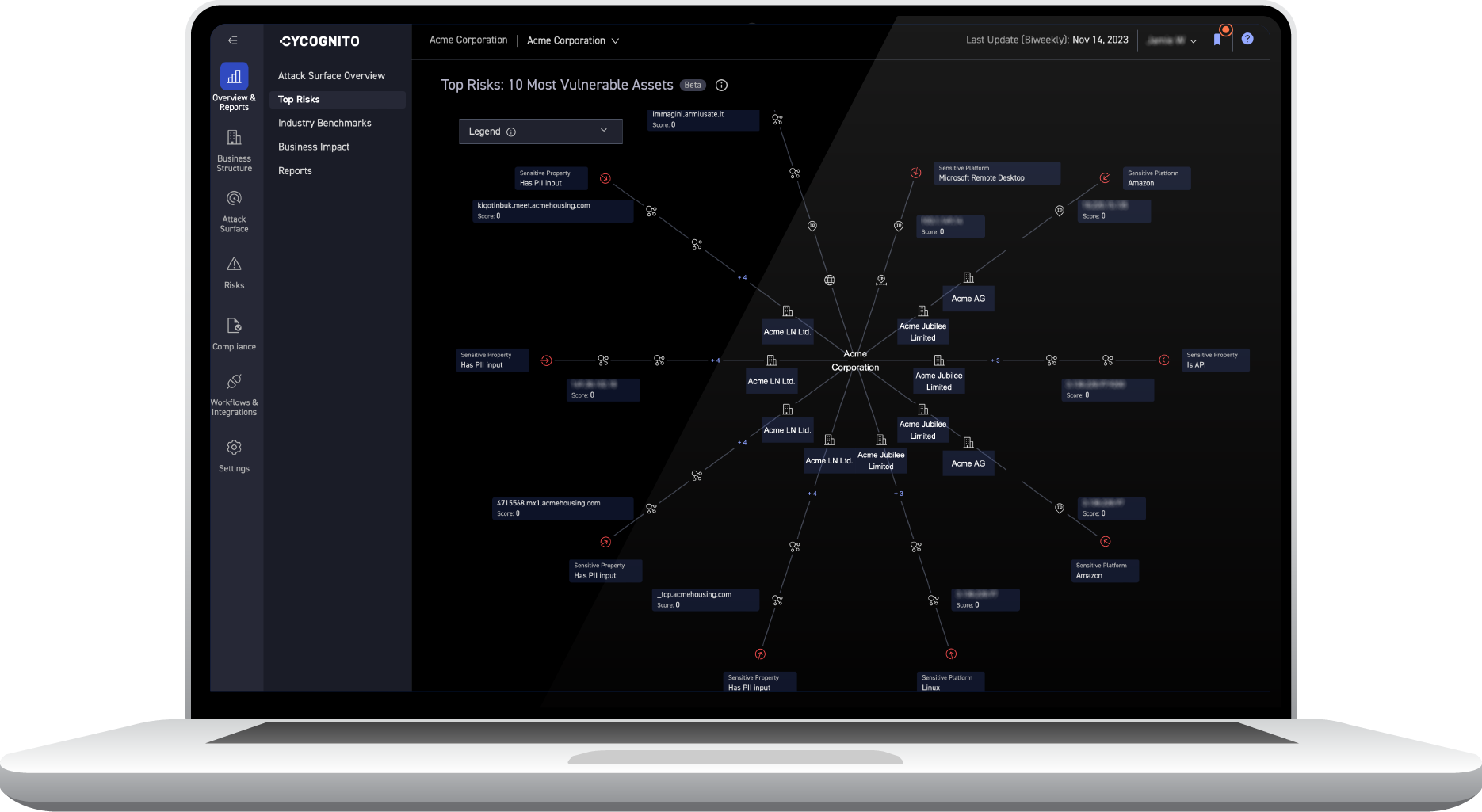
With CyCognito Automated Security Testing (AST), your organization can continuously actively test web applications for common vulnerabilities, identify which assets are protected by WAFs, and prioritize assets for remediation. CyCognito’s Exploit Intelligence module goes even farther, providing integrated tailored threat intelligence across your entire attack surface.
The CyCognito platform:
- Maps and discovers your entire external attack surface, ensuring that no web applications are left unmonitored.
- Assesses all assets for security protections and vulnerabilities, identifying web applications that are missing basic protections, like WAFs.
- Continuously tests your assets, prioritizes the most critical issues based on severity and business context, and provides remediation guidance.
- Provides real-time integrated threat intelligence, ensuring your risk assessment is always current and incorporates the latest attack vectors and cyber threats.
CyCognito identifies and tests your entire external attack surface, including web applications and WAFs, automatically, continuously, and at scale using CyCognito’s enterprise-grade testing infrastructure.
Learn more about CyCognito.