What Is Application Security Testing?
Application security testing is a systematic process of evaluating the security aspects of a software application to identify potential vulnerabilities and weaknesses that could be exploited by malicious actors. This testing is essential for ensuring that the application's code, configuration, and infrastructure are resilient against cyber attacks.
Security testing has become an inseparable part of the software development lifecycle (SDLC). By conducting thorough security testing, organizations can mitigate the risks of data breaches, unauthorized access, and other security threats, safeguarding sensitive information and maintaining the trust of their users.
3 Approaches to Application Security Testing
Here are three primary application security testing approaches:
Black-Box Security Testing
Black-box security testing, also known as external testing, involves assessing the security of an application from an external perspective, without access to its internal code or architecture. Testers simulate real-world attack scenarios to identify vulnerabilities that could be exploited by external adversaries.
By emulating the behavior of potential attackers, black-box testing helps uncover security weaknesses that may not be apparent from an internal vantage point, providing valuable insights into the application's susceptibility to external threats.
White-Box Security Testing
White-box security testing, also known as internal testing, involves analyzing the application's internal code, architecture, and design to identify potential security vulnerabilities. Testers have full access to the application's source code and can conduct in-depth assessments of its security controls, authentication mechanisms, and data handling processes.
By scrutinizing the application's internal components, white-box testing uncovers vulnerabilities that may not be apparent through external assessments, allowing for targeted remediation of security weaknesses at the code level.
Gray-Box Security Testing
Gray-box security testing combines elements of both black-box and white-box testing, offering a balanced approach to assessing application security. In gray-box testing, testers have limited knowledge of the application's internal workings, allowing them to simulate attacks from a semi-internal perspective. This approach enables testers to gain a deeper understanding of the application's security posture while still maintaining an element of external assessment.
Types of Application Security Testing Solutions
Here are the common types of security solutions used to perform application security testing:
Static Application Security Testing (SAST)
Static application security testing, commonly referred to as SAST, involves analyzing the application's source code, configuration files, and dependencies to identify potential security vulnerabilities and coding errors.
SAST solutions use automated scanning techniques to examine the codebase for known security issues, coding best practices, and compliance with security standards. By conducting static code analysis, organizations can proactively detect and remediate security vulnerabilities early in the software development lifecycle, reducing the potential impact of security flaws in production environments.
Dynamic Application Security Testing (DAST)
Dynamic application security testing, known as DAST, focuses on evaluating the security of running applications by simulating real-world attack scenarios and identifying potential vulnerabilities from an external perspective.
DAST solutions interact with the application in a manner similar to that of a potential attacker, probing for security weaknesses related to input validation, authentication mechanisms, and session management. By conducting dynamic testing, organizations can gain insights into the application's runtime behavior and identify vulnerabilities that may not be apparent through static code analysis alone.
Learn more in our detailed guide to
DAST tools.
Interactive Application Security Testing (IAST)
Interactive application security testing, or IAST, represents a hybrid approach that combines elements of SAST and DAST to provide real-time security analysis during the application's runtime.
IAST solutions instrument the application to monitor its behavior and interactions with the underlying infrastructure, identifying security vulnerabilities and data flow anomalies as they occur. By offering continuous security assessment capabilities, IAST makes it possible to detect and address complex security issues in real time.
Vulnerability Scanning
Vulnerability scanners use various techniques to collect protocol headers of running services, including applications delivered over HTTP/HTTPS. Vulnerability scanners are either authenticated (have login access to the system) or unauthenticated (do not have login access to the system).
Strictly speaking, vulnerability scanners are not considered testing, because they are limited to identifying common vulnerabilities and exposures (CVEs) issues based on the version of runtime code. However, they are commonly used as part of a holistic application security testing program.
Software Composition Analysis (SCA)
Software Composition Analysis (SCA) is a process that allows security analysts to identify and manage open-source components within a software project. The primary objective of SCA is to manage security risks associated with open-source components.
SCA enables organizations to keep track of the open-source components used in their applications, thereby helping them identify any known vulnerabilities in these components. By using SCA, organizations can also ensure that they are in compliance with the licenses of the open-source components they use.
Runtime Application Self-Protection (RASP)
Runtime Application Self-Protection (RASP) works by embedding itself within an application or its runtime environment, thus allowing it to control the execution of the application.
RASP solutions can detect attacks in real-time by analyzing both the application's behavior and the context of that behavior. If an attack is detected, RASP can take action to prevent the attack, such as terminating the user session or alerting the security team.
Mobile Application Security Testing (MAST)
Mobile Application Security Testing (MAST) focuses on identifying vulnerabilities in mobile applications. Given the widespread use of mobile applications today, MAST has become increasingly important.
MAST involves testing mobile applications for potential security vulnerabilities. This includes testing the application's code, its interaction with other applications, and how it handles data. By conducting MAST, organizations can ensure that their mobile applications are secure and that they are not exposing sensitive data to potential threats.
Application Security Testing Best Practices
Application security testing is more than just tools. Here are some best practices that will help you set up an effective application security program in your organization.
Shift Left
Shifting left refers to the practice of integrating security testing earlier in the Software Development Life Cycle (SDLC). Instead of waiting until the later stages of the SDLC to conduct security testing, shifting left involves integrating security testing as early as possible.
By shifting security testing left, organizations can detect and address security vulnerabilities earlier in the development process. This not only reduces the time and resources required for remediation but also reduces the risk of security breaches. This requires close collaboration between development, security, and operations teams, a paradigm known as DevSecOps.
Use Multiple Testing Techniques
To effectively practice application security testing, it is important to combine several testing methods, such as static analysis, dynamic analysis, and manual code review, to ensure comprehensive coverage of potential security vulnerabilities.
By using multiple testing techniques, organizations can ensure that they are covering all possible angles, and detecting a wider range of vulnerabilities, improving the overall security posture of their applications. Organizations should also carefully evaluate their external attack surfaces, including cloud services and shadow IT applications, and make sure they are covered by security tests.
Test Internal Interfaces, Not Just APIs and UIs
Effective application security testing should address not only external interfaces but also the internal interfaces of the application. Internal interfaces often handle sensitive data, and if these interfaces are insecure, they can expose this data to potential threats.
By testing internal interfaces, organizations can ensure that even if attackers penetrate their environment, they will be limited in their ability to move laterally and escalate privileges.
Identify Internal and External Attack Surfaces
An attack surface comprises all the points where an unauthorized user can try to enter data to or extract data from an environment. The internal attack surface refers to the components within the organization's network, such as internal applications, databases, and internal user interfaces, where potential vulnerabilities may exist. External attack surfaces include publicly exposed elements like websites, external APIs, and mobile apps that can be accessed from outside the organization's network.
Understanding and mapping these surfaces is critical for effective security testing. By identifying these areas, organizations can focus their security efforts on areas that are most vulnerable to attacks. Regularly scanning and monitoring these surfaces can help in early detection of vulnerabilities and potential breaches.
Prioritize Security Issues
Not all security issues pose the same level of risk to an organization, and it's important to allocate resources effectively to address the most critical ones first.
Prioritization involves assessing the severity of each identified vulnerability, taking into account factors like the ease of exploitation, the potential impact of a successful attack, and the likelihood of exploitation in the real world. Organizations should use a standardized scoring system like the Common Vulnerability Scoring System (CVSS) to ensure a consistent approach.
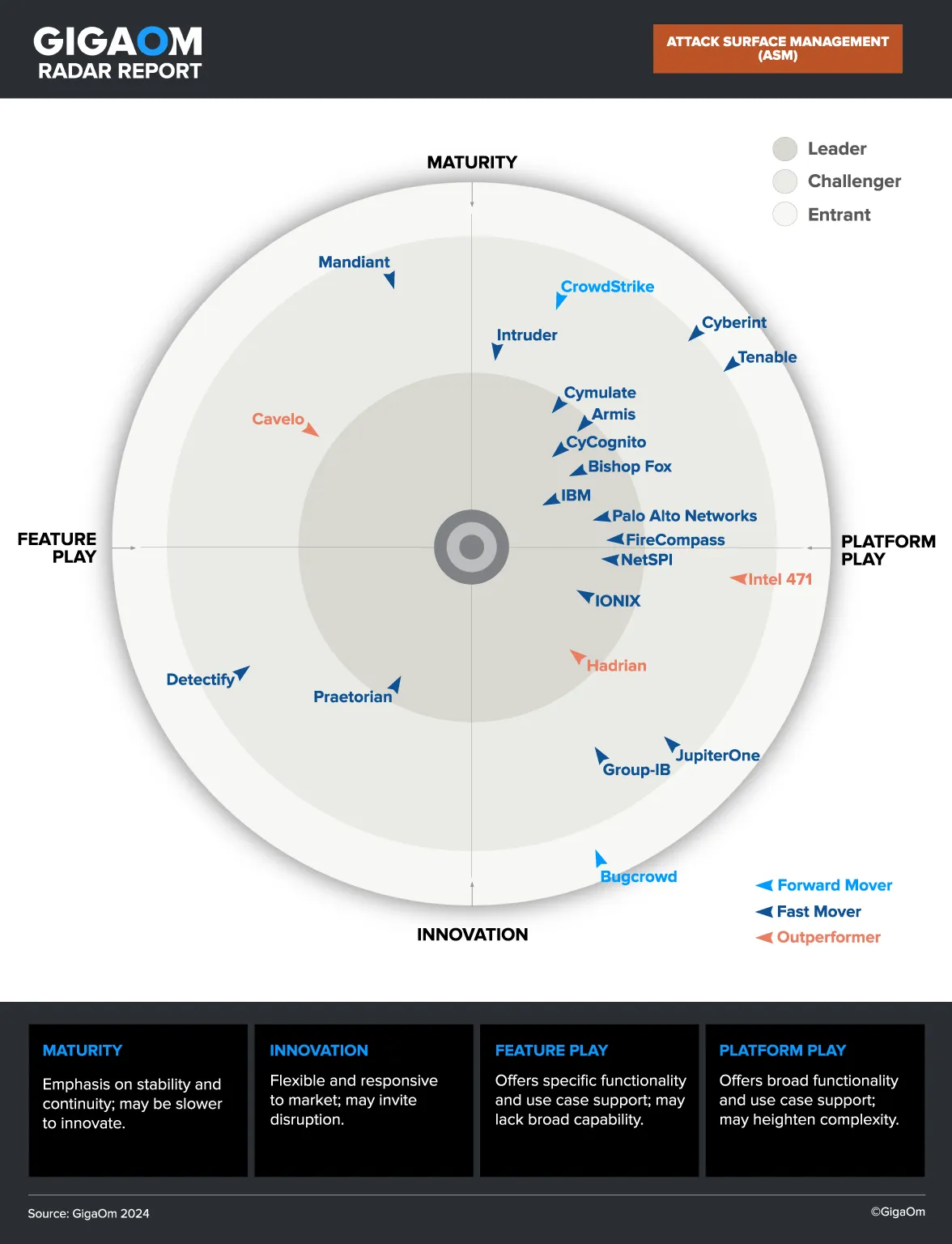
How CyCognito Performs Security Testing for All Externally Exposed Applications
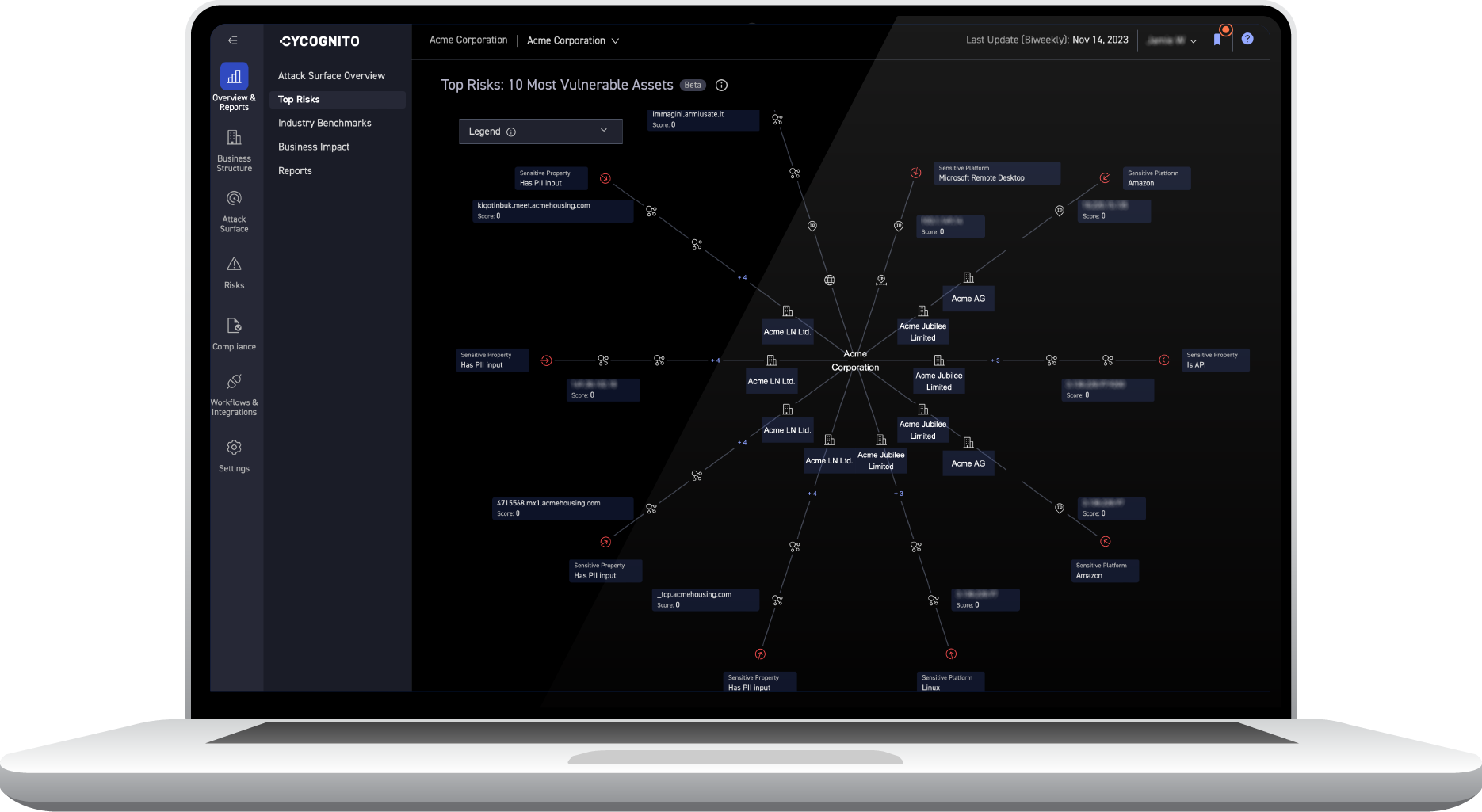
Most organizations test a fraction of externally exposed assets. With CyCognito Automated Security Testing (AST), IT security teams have continuous access to the top risks attackers will use against an infrastructure.
Integrated active security testing, including web application testing/DAST, detects issues that are far beyond common vulnerabilities and exposures (CVEs), including exploitable application code, system misconfigurations, exposed data, default credentials, certificate validity issues, and more.
CyCognito provides automated active testing, including web application testing/DAST at enterprise scale:
- Test for tens of thousands of attacks: CyCognito’s payload-based active testing, including DAST, provides comprehensive visibility into complex risks.
- Test the entire external asset inventory: CyCognito’s active testing is integrated with the CyCognito asset discovery and contextualization engine. This eliminates visibility gaps and removes manual effort.
- Eliminate asset resource impact: CyCognito’s active testing is architected as “low and slow” and is monitored carefully. This enables production systems to be tested without impact or need for complex scheduling.
- Achieve >90% confidence: CyCognito’s active testing has >90% accuracy in identifying risk exposures. High accuracy and low false positives lead to confident IT security staff and faster MTTR.
- Validate remediation efforts: CyCognito’s active testing is automatic and continuous. Only active testing can confidently validate remediation remediation efforts.
CyCognito takes the burden and costs out of managing security testing; recon and security tests are completed automatically, at scale, using CyCognito’s enterprise-grade testing infrastructure.
If you are not a CyCognito customer and want to find out more about how we can help automate security testing across your full external attack surface, please contact us at [email protected].
Learn more about CyCognito.