



CyCognito continuously identifies and validates critical exposures to help you act fast where it matters most.
Get a DemoTrusted by leading global enterprises.
















































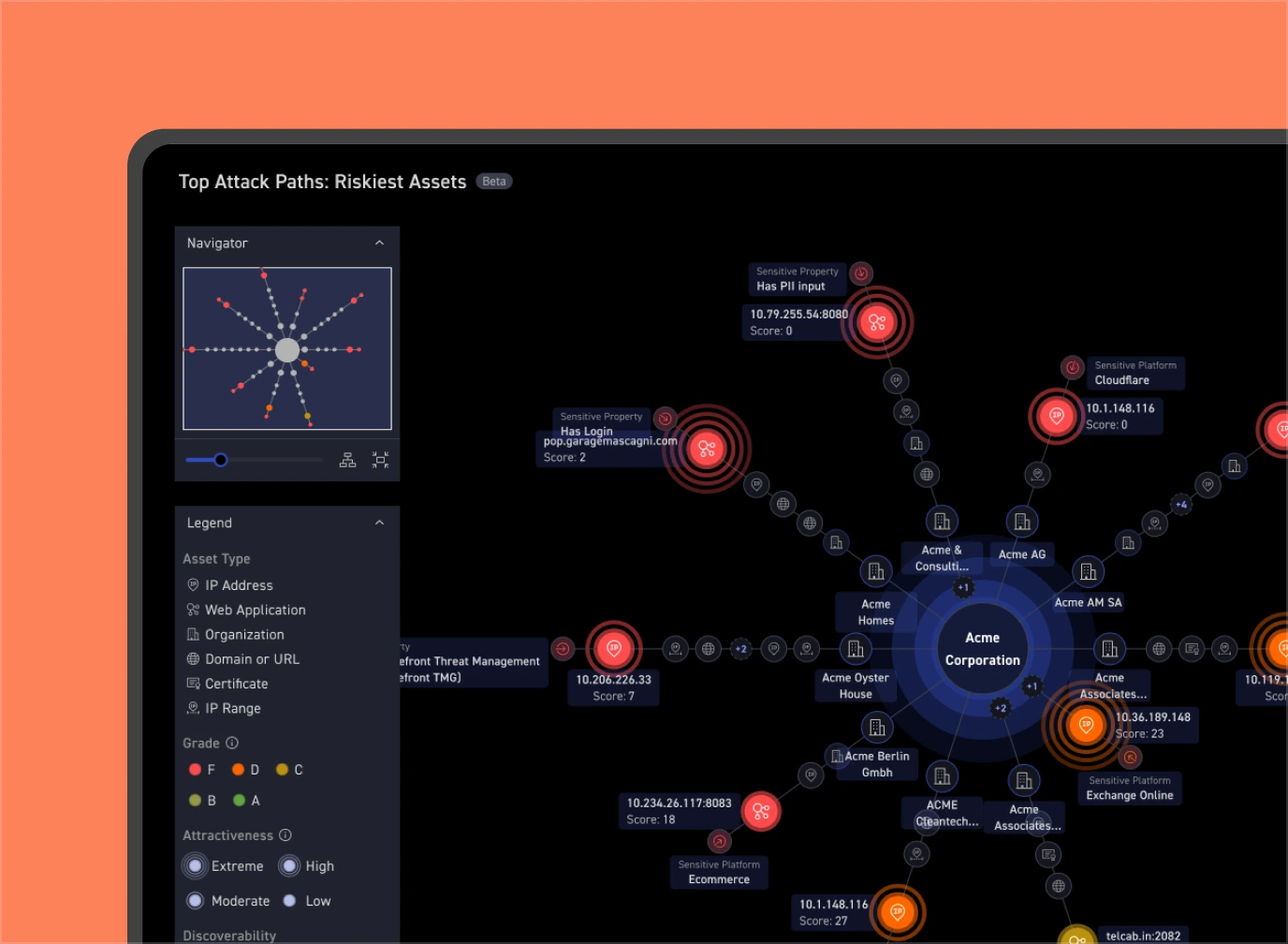
See your attack surface instantly, just like attackers do. Find up to 20× more exposures than other tools. No asset lists or setup needed.
Discover where most risk accumulates—untracked IP ranges, inherited and third-party assets, and other unknown unknowns.
Maintain visibility with daily scans, keeping the inventory up to date and accounting for new risks and exposures.
Empower modern exposure management.
Connect. Contextualize. Mobilize.












"CyCognito provides our company with cutting-edge technology, enabling my team to have global visibility into our web-facing assets in an easy-to-use interface."


Identify, validate, and prioritize risk with the CyCognito platform. Integrate seamlessly to extend visibility, automation, and control across your ecosystem.

Discover exposed assets, validate real risks, and prioritize what to fix, guided by the business context.

Automatically test exposed assets using diverse security methods to uncover real attack paths.

Unmanaged assets are invisible to CAASM solutions. Close the gaps in your cyber asset inventory system.

Prioritize your vulnerabilities based on real risks in your attack surface.

See what your CNAPP solution is missing and test 100% of your exposed cloud assets.

Discover web applications and APIs, perform continuous DAST and ensure WAF coverage.
The 2025 GigaOm Radar recognizes CyCognito as an Attack Surface Management Leader for its depth of asset discovery, scalable automation, and precision in risk prioritization.
Read the report to compare internal and external ASM providers, see how they complement each other, and find the best fit for your organization.
Get Free Report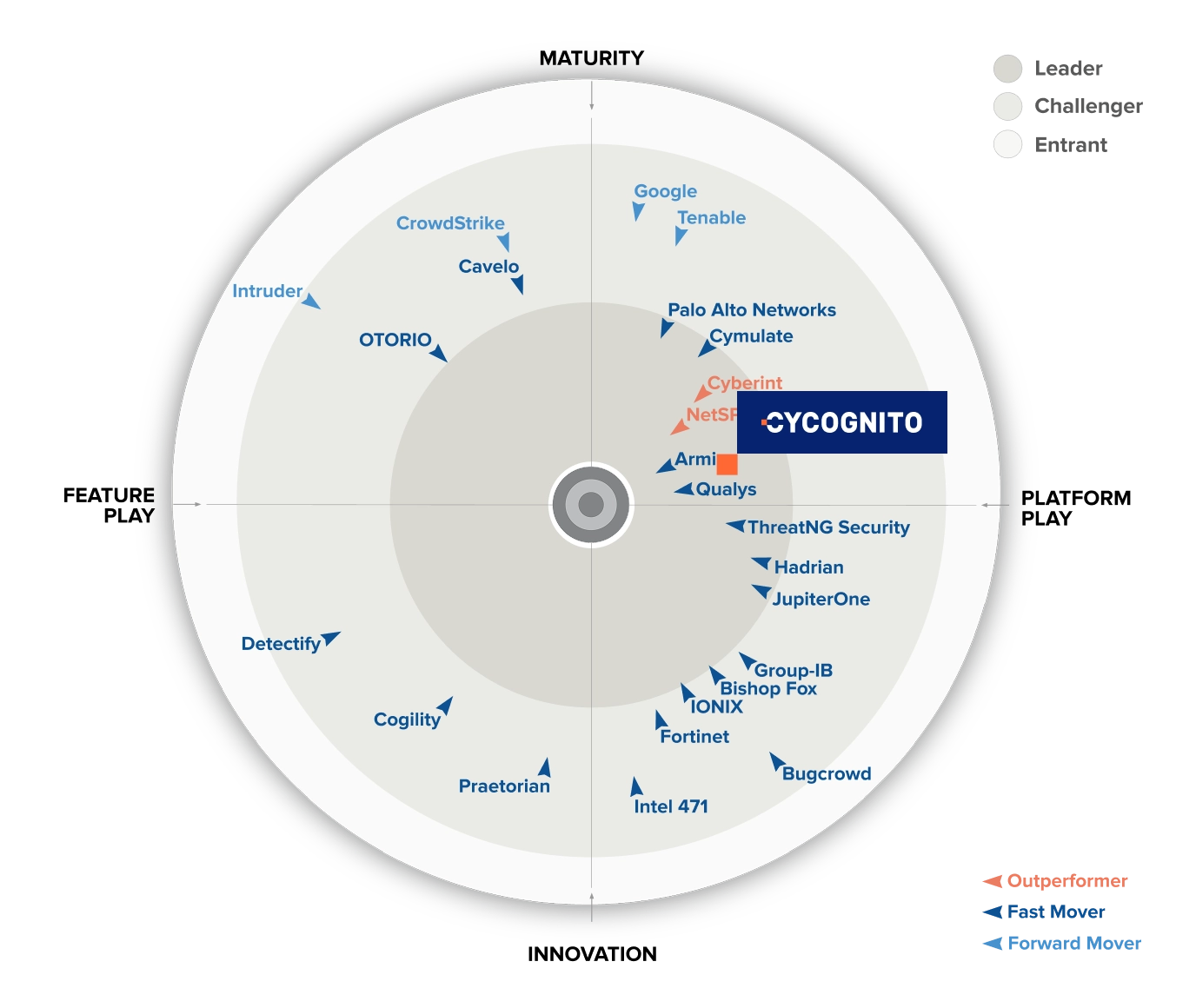
Security teams are faced with stagnant or reduced budgets, yet need to increase the value of their security testing programs.
Answer a few questions and receive a custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
Find Your Savings