EASM Concepts Deep Dive
What are the Three Categories of Attack Surface Threats?
The three primary categories of attack surface threats are:
- Physical Threats: Physical threats primarily involve human (physical) access to an organization's premises, facilities, or devices. Examples include unauthorized entry, theft of hardware, or tampering with physical infrastructure components.
- Network Threats: Network threats target an organization's network infrastructure, including routers, switches, firewalls, and other network devices. They aim to exploit vulnerabilities in network configurations, protocols, or services to gain access, which enables lateral movement, data exfiltration, or disruption of network operations.
- Software/Application Threats: Software threats involve exploitation of vulnerabilities in software applications, operating systems, or web services/APIs. They can include techniques like code injection, cross-site scripting (XSS), SQL injection (SQLi), or leveraging unpatched vulnerabilities to gain access, steal data, or disrupt services.
Under the Hood of EASM Solutions
External attack surface management (EASM) platform typically involves a combination of automated tools and manual analysis. Automated tools scan the organization's external digital footprint, including websites, servers, and other exposed assets, to identify vulnerabilities and potential entry points for attackers. These tools may employ techniques such as port scanning, vulnerability scanning, web application security testing and review of open-source intelligence (OSINT).
Manual analysis may complements the automated tools by validating and interpreting the scan results. Security professionals review the findings, analyze the context, and assess the potential risks associated with the identified vulnerabilities. This analysis helps prioritize remediation efforts and determine the most effective strategies for securing the external attack surface.
Once vulnerabilities are identified, organizations can take actions such as applying patches, configuring security controls, strengthening access controls, and implementing other security measures to mitigate the risks. Regular scanning and monitoring of the external attack surface are crucial to stay ahead of emerging threats and ensure ongoing protection.
EASM may also involves proactive measures like threat intelligence gathering and analysis. By monitoring threat feeds, security blogs, and other sources, organizations can stay informed about new attack techniques, vulnerabilities, and threat actors targeting their industry. This information helps in adjusting security strategies and prioritizing efforts to address the most relevant threats.
Overall, EASM provides a systematic approach to safeguarding an organization's external attack surface by continuously identifying, analyzing, and addressing vulnerabilities and risks, thereby reducing the potential for successful cyber attacks.
EASM Technologies and Techniques
Examples of EASM tools and techniques include:
- Web Application Scanners: These tools analyze web applications for vulnerabilities like SQL injection, cross-site scripting, data exposure, and insecure configurations.
- Network Scanners: These tools scan network infrastructure, ports, and services to identify weaknesses and potential entry points for attackers.
- Threat Intelligence Platforms: These platforms gather and analyze threat intelligence data to provide insights into emerging threats and malicious activities targeting the organization.
- Vulnerability Management Systems: These systems help identify, track and prioritize vulnerabilities across the external attack surface, enabling efficient remediation.
- Attack Surface Monitoring Services: These services continuously monitor an organization's digital footprint, including websites, domains, and online assets, to identify changes, vulnerabilities, or potential risks.
WHat Is the Difference Between Attack Surface Management and Vulnerability Management?
Attack surface management (ASM) and vulnerability management (VM) are distinct but interconnected aspects of cybersecurity.
Attack surface management focuses on identifying, analyzing, and securing an organization's externally-exposed digital assets, such as websites, servers, and network infrastructure. It involves understanding the organization's digital footprint visible to potential attackers and implementing measures to minimize vulnerabilities and risks associated with the external attack surface.
Vulnerability management focuses on the identification, assessment, and remediation of vulnerabilities across an organization's entire infrastructure, both internal and external. It encompasses scanning systems, applications, and networks to discover vulnerabilities, prioritizing them based on severity, and applying patches or implementing mitigation strategies to address those vulnerabilities.
Vulnerability management typically focuses on digital assets found in known IP ranges, while attack surface management produces a dynamic asset inventory independent of known systems, providing additional insight and risk visibility.
While attack surface management primarily focuses on the external-facing assets, vulnerability management takes a broader approach, covering both internal and external vulnerabilities within an organization's infrastructure.




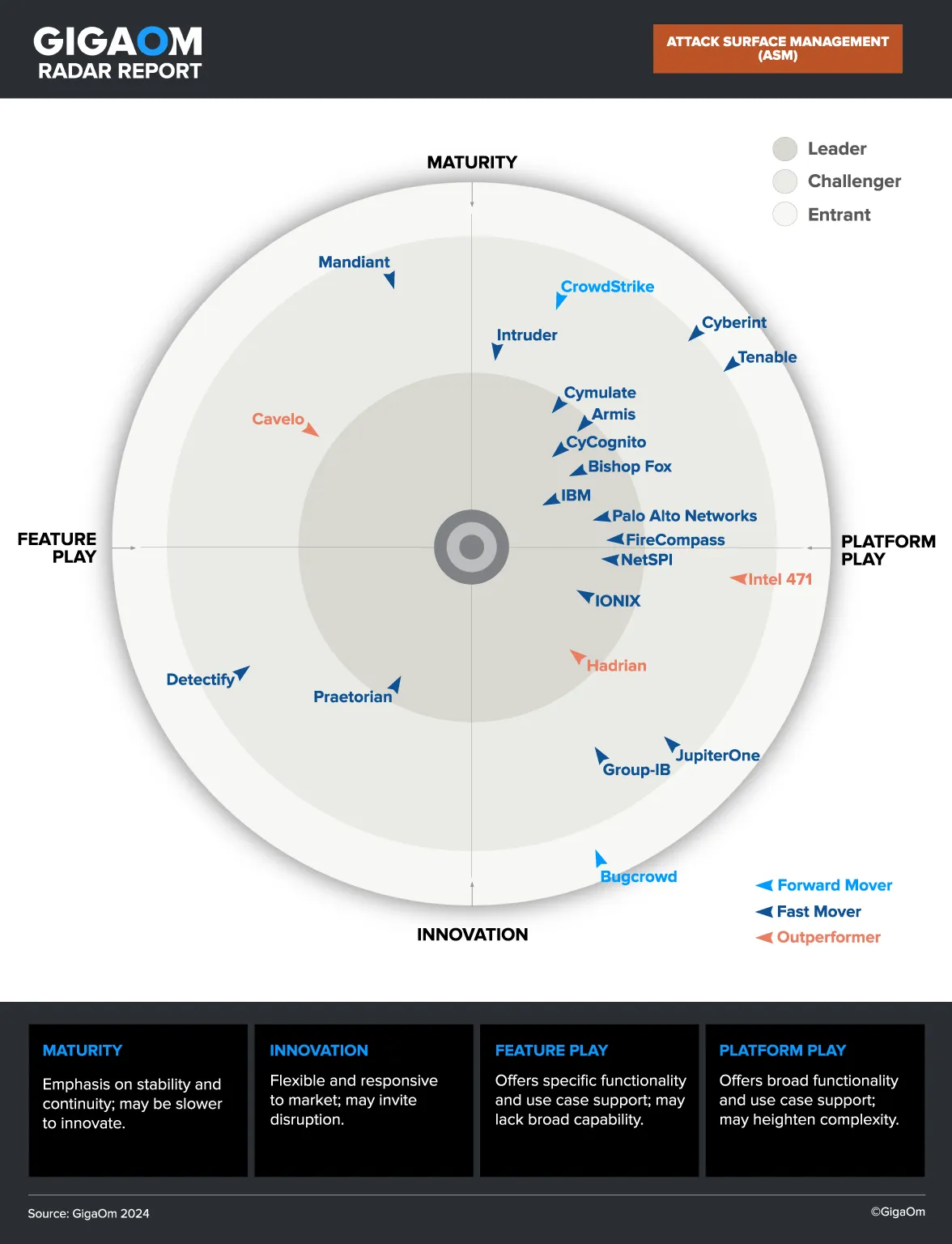

 Live CyCognito Demo
Live CyCognito Demo