



CyCognito External Exposure Management platform delivers continuous visibility and active validation across your external footprint, so teams focus on exploitable risk and remediate efficiently.
Get a Demo
Trusted by leading global enterprises.

















































Seedless discovery maps your entire footprint. Uncover up to 20x more assets than other tools across SaaS, cloud, and on-prem environments.

Discovery alone is not enough. Leverage 90,000+ automated tests to validate exploitability and direct remediation where it has the greatest impact.

Combine exploitability, business context, and attack-path insight for a clear, short list of issues worth fixing first.

Map findings to owners and sync issues into existing workflows. Fixes move faster, with progress tracked through closure.

CyCognito allows us to see all of our vulnerabilities across our attack surface. You can find out things that nobody in the company may have known.
 Deloitte
Darrell Jones ・ Chief Information Security Officer
Deloitte
Darrell Jones ・ Chief Information Security Officer
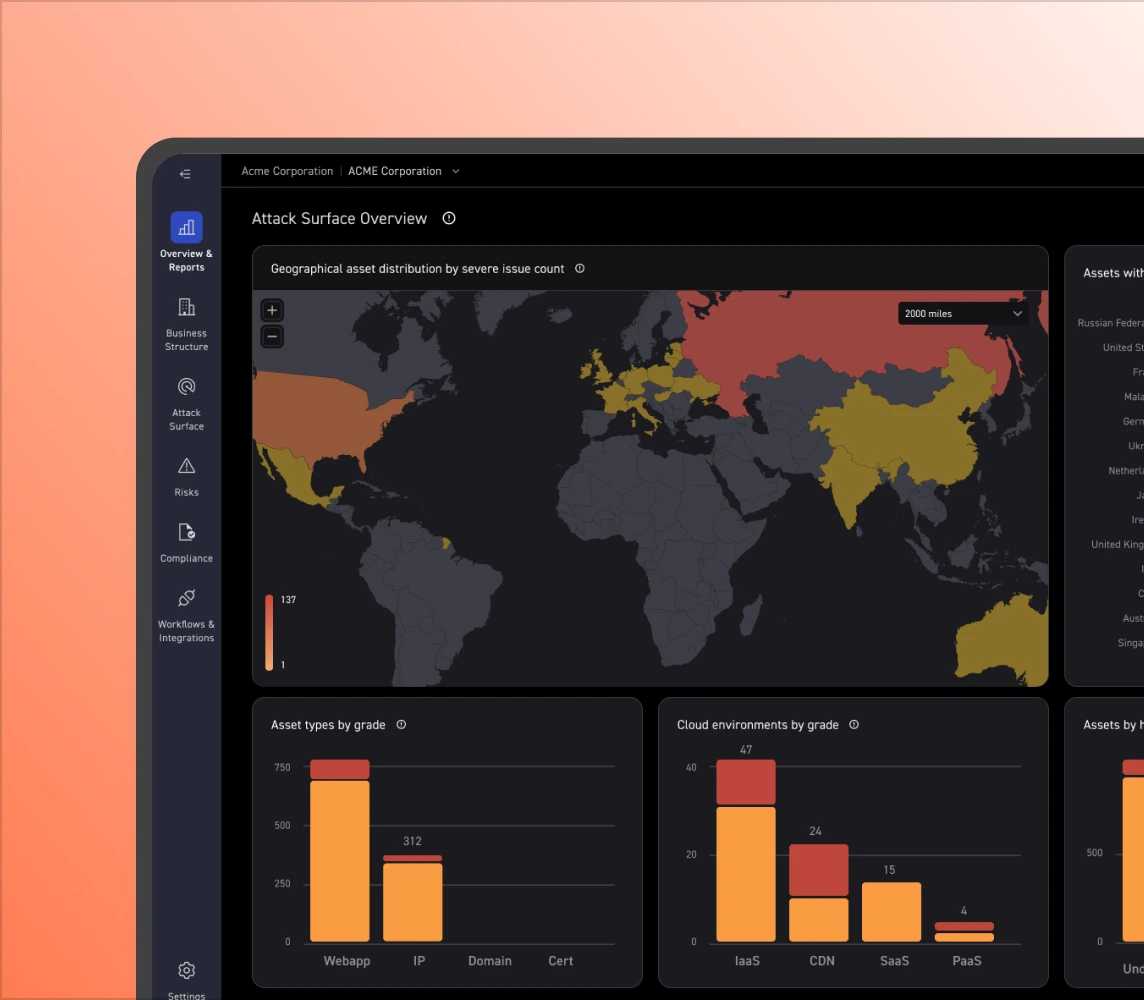
Real discovery surfaces assets you didn’t know to look for. CyCognito uses a 60,000+ node global network to continuously identify, classify, and map external assets across cloud services, web apps, APIs, on-prem, and more.
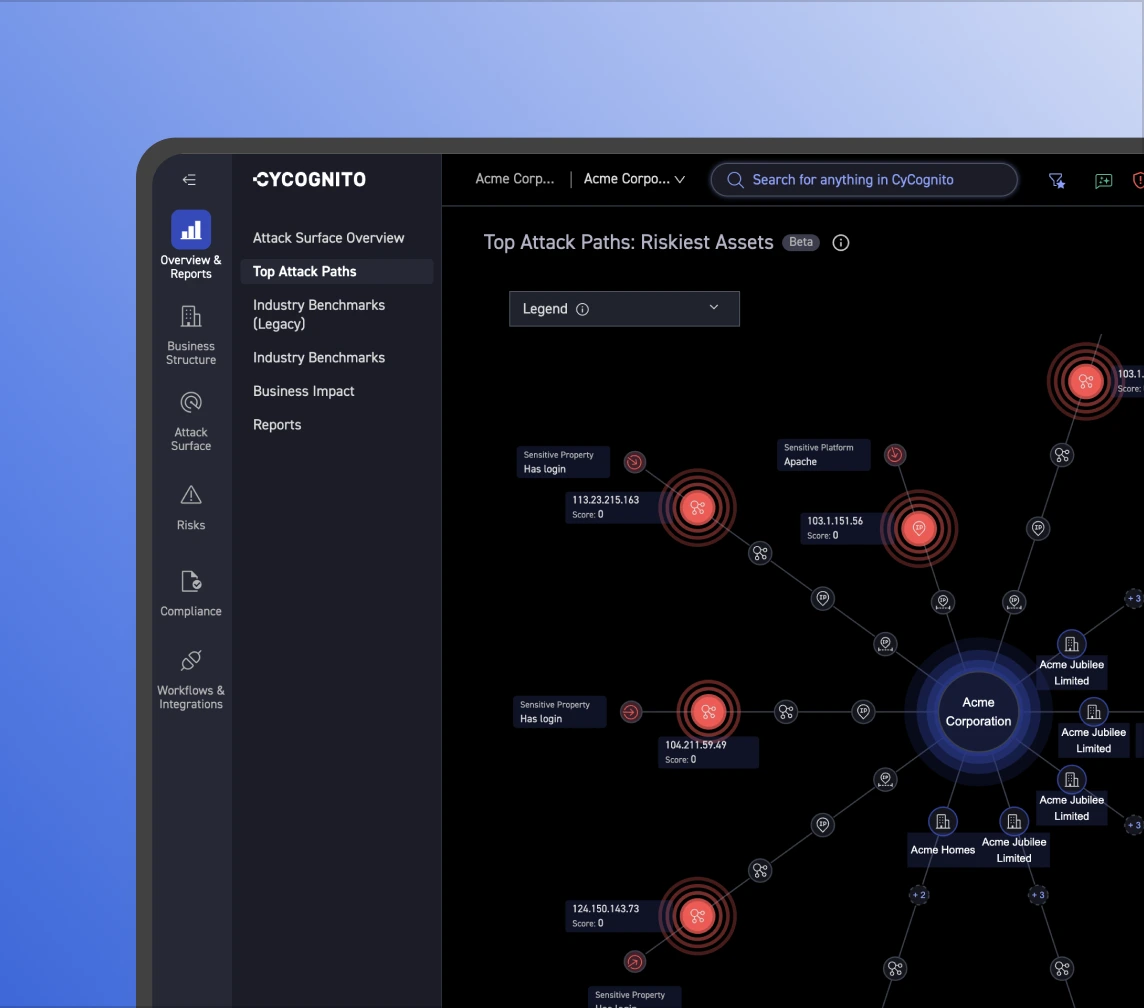
Validation separates exploitable risk from noise. Always-on security testing verifies exploitability across 30+ categories, covering OWASP weaknesses, data exposure, orphaned assets, authentication bypass risk, and more.
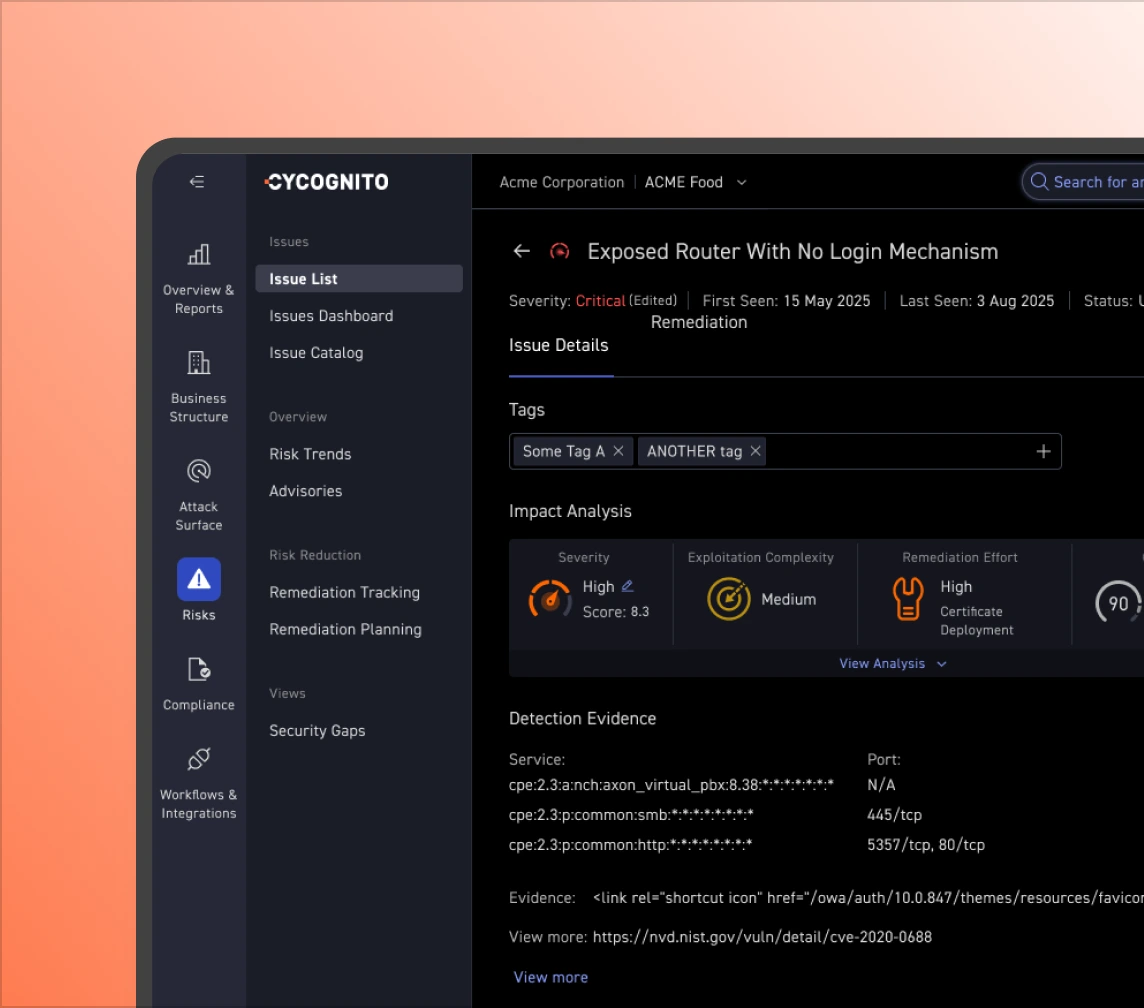
Prioritization falls short without context. Alongside active validation, CyCognito also use proprietary logic to link findings to business context, attack paths, and external threat intelligence to separate noise from exploitable issues.
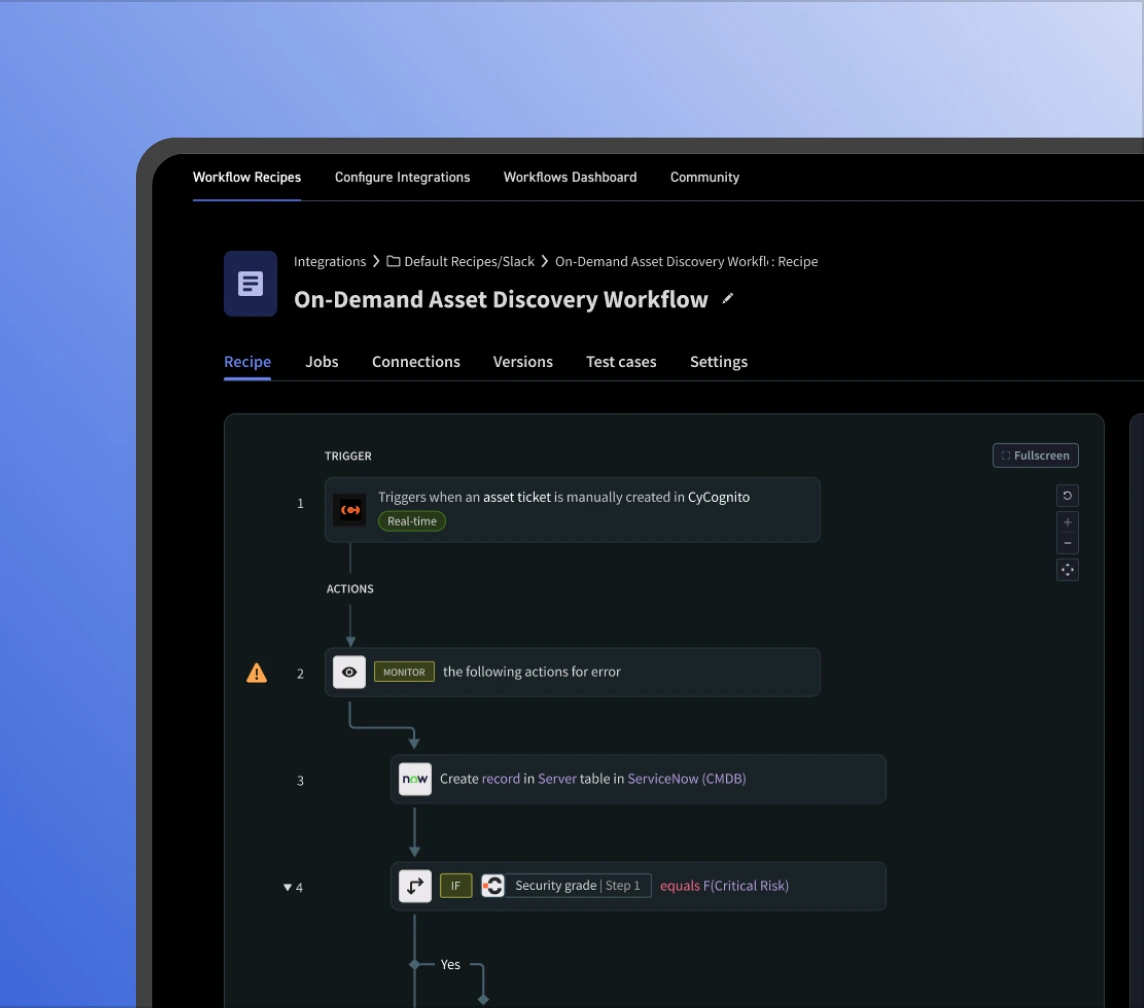
Up to 50% of tickets are closed without resolving the issue. CyCognito links findings to asset owners, routes them through integrated workflows, provides guided remediation steps, and automatically validates fixes to ensure security gaps are actually closed.