



CyCognito runs automated black-box testing to validate exploitability and prioritize remediation, reducing reliance on point-in-time pentests and lowering testing effort and cost.
Get a Demo
Trusted by leading global enterprises.

















































Seedless discovery identifies assets across your attack surface. Active testing confirms exploitability and continuously validates exposures as conditions change.

Coverage spans 90,000+ testing modules, including DAST and security control validation (WAF, API security, CSPM, and more). AI-assisted orchestration sequences test efficiently at scale.

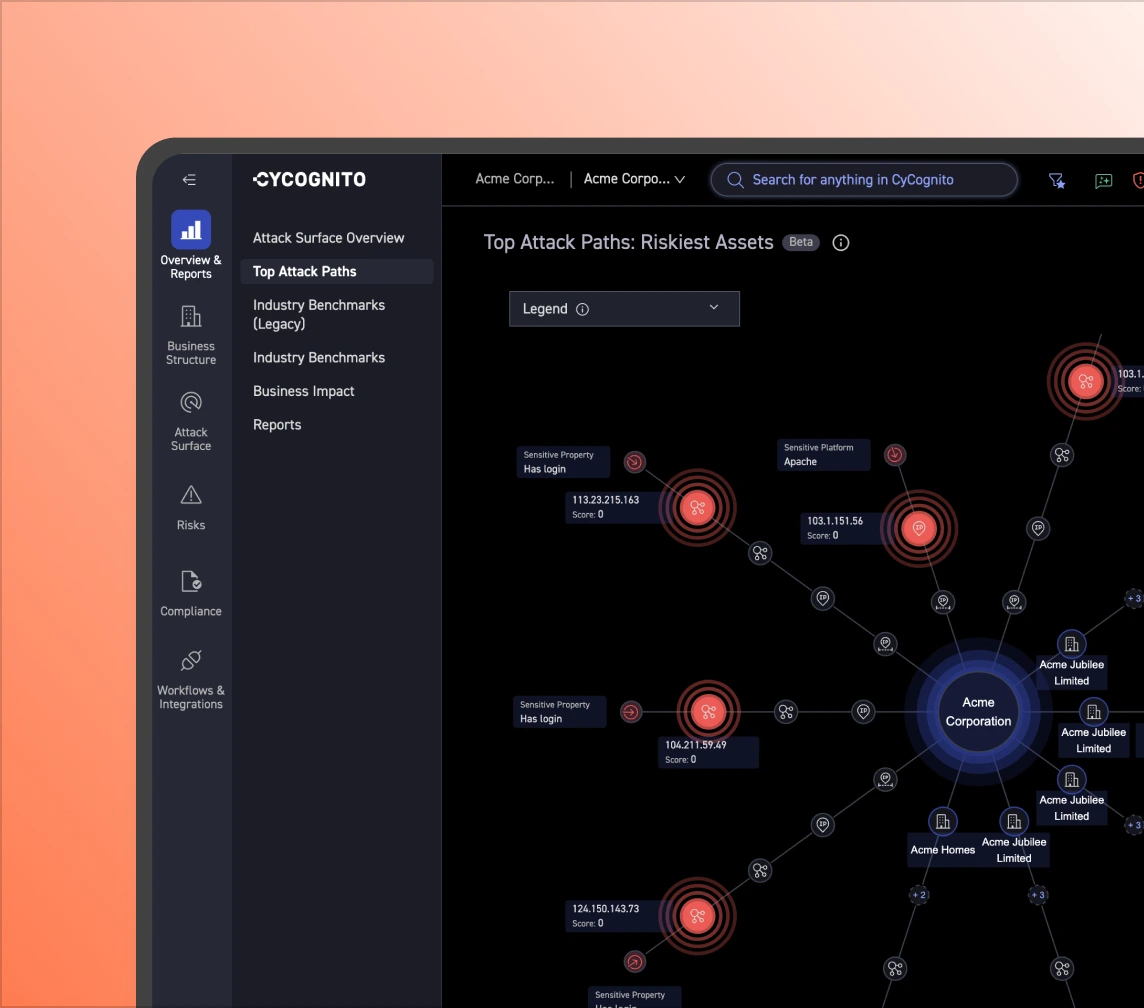
Prioritization goes beyond severity scores. Validated issues are mapped to business context, likely attack paths, and threat intelligence to surface the 0.01% worth fixing first.

Replace point-in-time assessments with continuous attacker-side testing. Reduce pentest and bug bounty spend over time by up to $500K.

In the first full year of running the platform, there were approximately 140 criticals that needed to be remediated in a timely manner. I'm pretty sure out of those 140 items, we would have only come across a fraction doing it ourselves manually.
 Berlitz
Daniel Schlegel ・ Global IT Operations Leader
Berlitz
Daniel Schlegel ・ Global IT Operations Leader
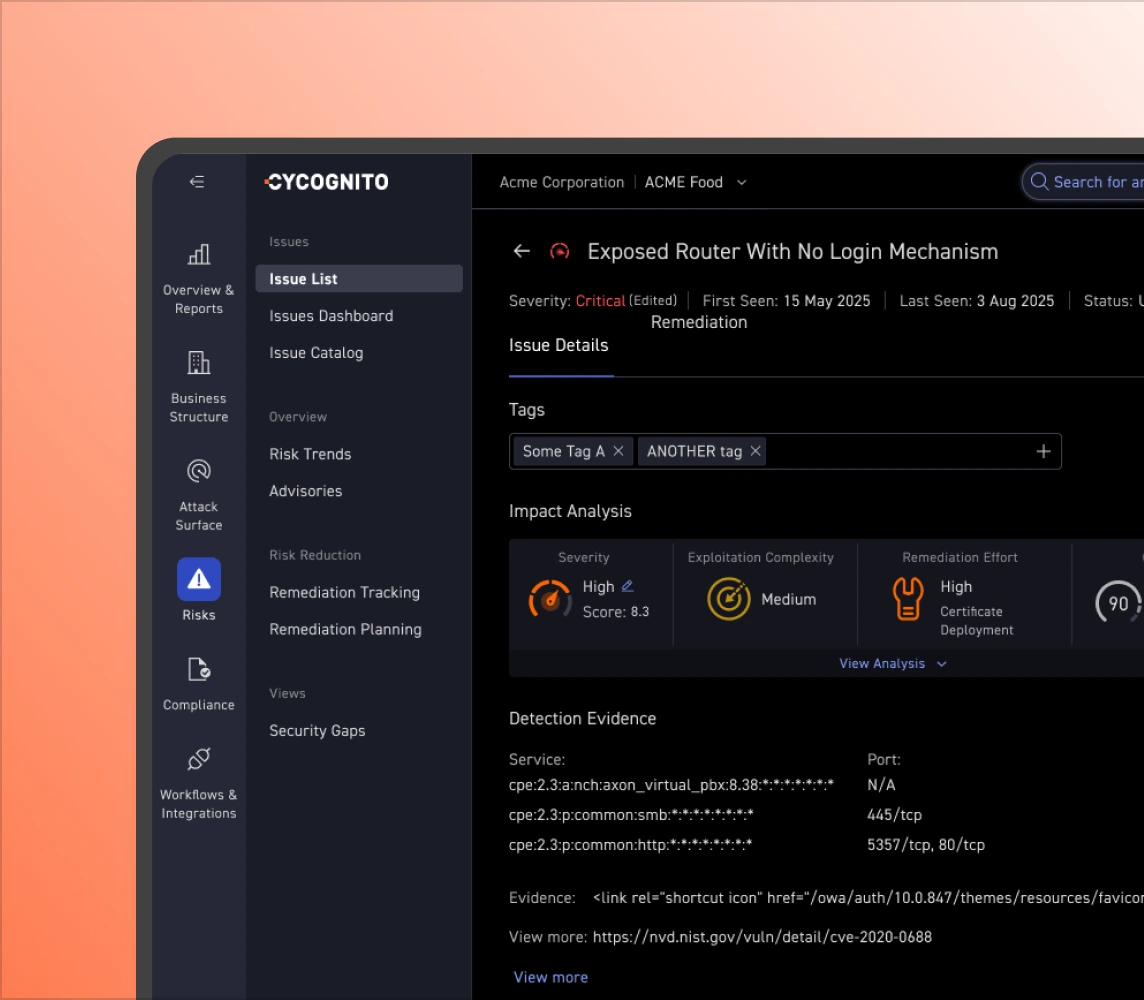
Manual testing can’t keep pace with attack surface changes. CyCognito combines automated reconnaissance with active security testing to maintain continuous coverage. Exposures are found and validated as they appear.
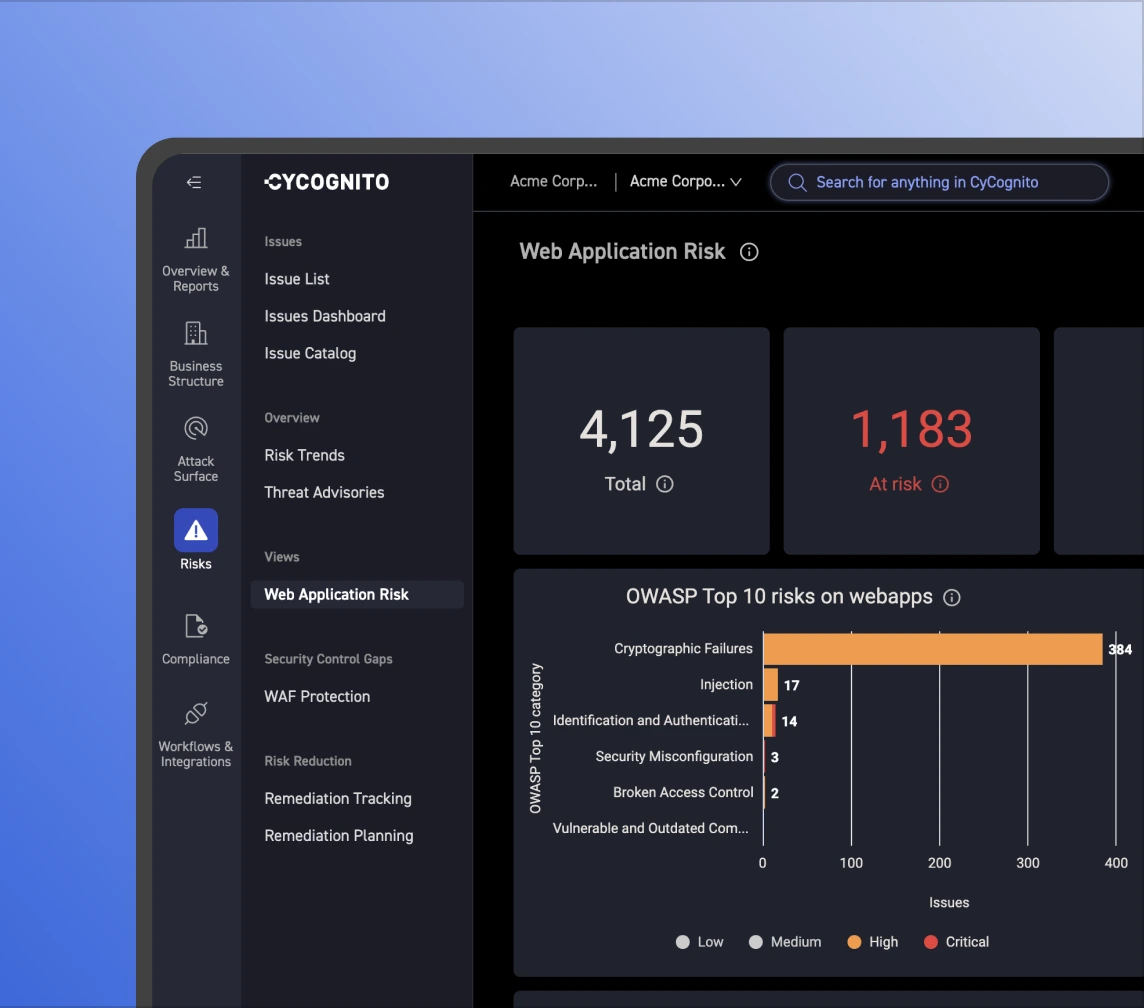
External risk takes many shapes, from application weaknesses to orphaned assets. Continuous active validation covers 30+ categories, including OWASP weaknesses, data exposures, abandoned assets, authentication bypass risk and more.
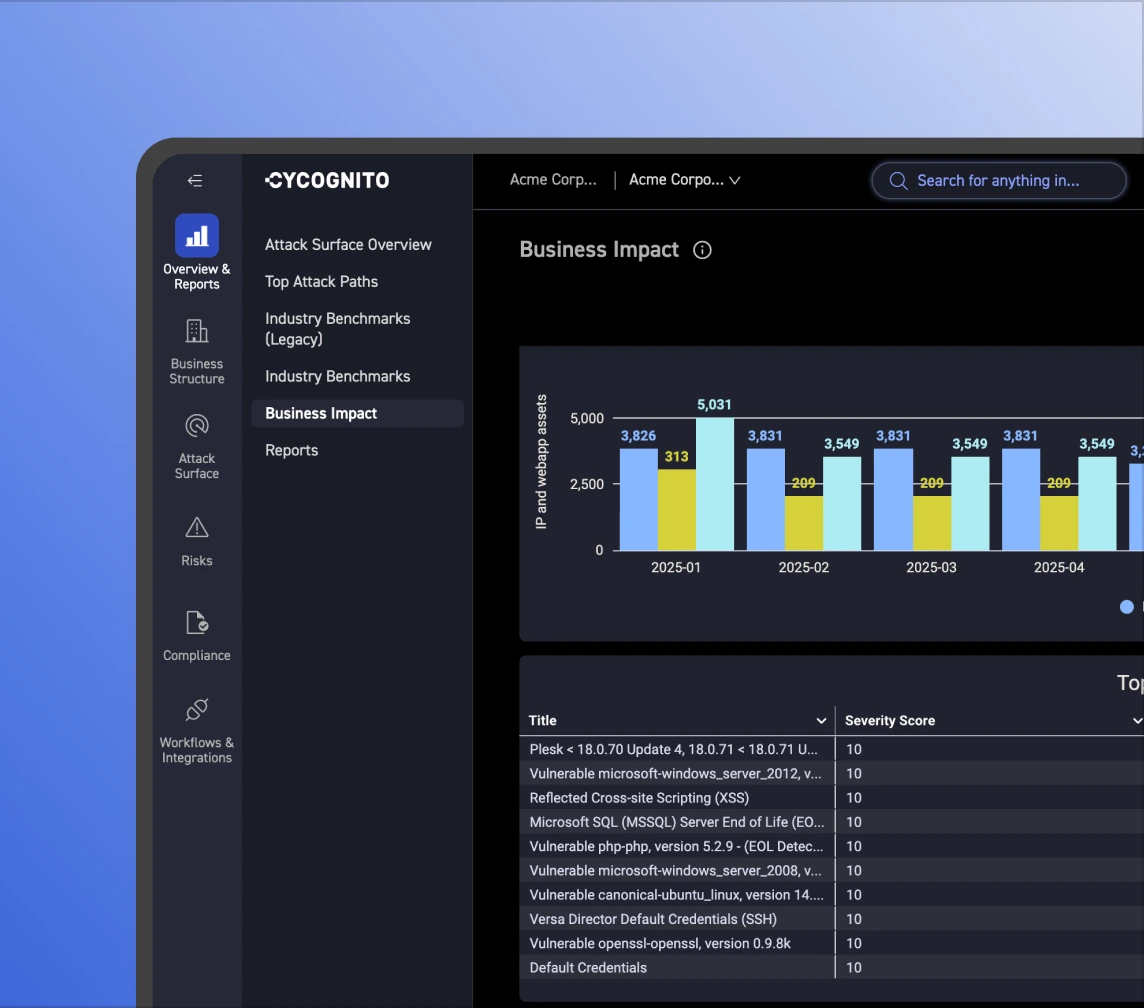
Severity scores don’t reflect risk. Our platform links validated findings to business context, attack paths, and threat intelligence to separate noise from exploitable issues. Customers see “critical” findings drop from about 25% to 0.1% after factoring in real-world exploitability.
Point-in-time testing forces tradeoffs between scope, speed, and budget. Always-on testing cuts repeat manual work, so teams focus on key decisions that require human judgment. The result is broader coverage, shorter cycles, and lower pentest and bug bounty spend.
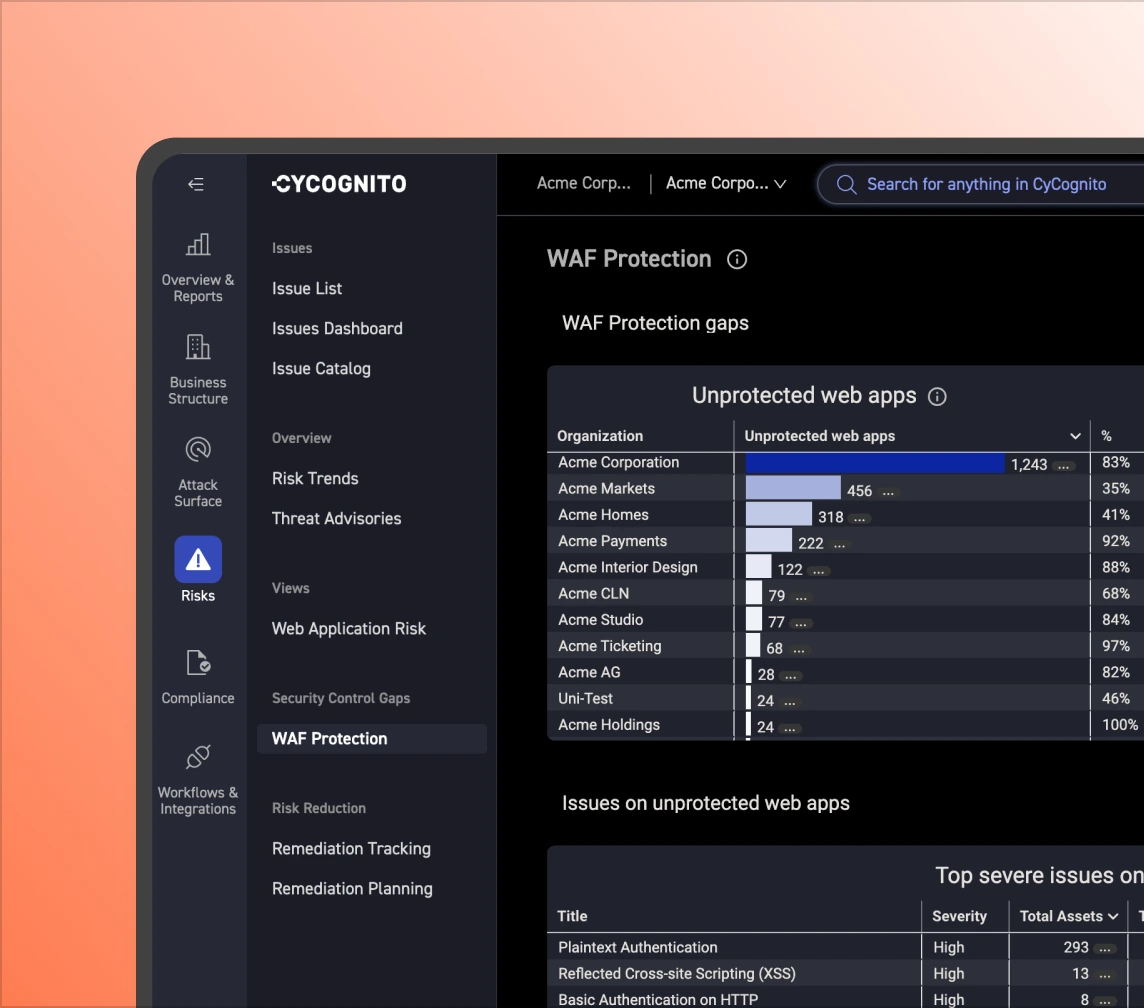
Assumed protection creates blind spots. CyCognito continuously tests exposed assets to confirm WAF, authentication, and access controls behave as expected, surfacing critical gaps.