



CyCognito turns CTEM from a framework into an operating rhythm: exposing what is truly reachable, validating real‑world impact, and mobilizing the right team without crying wolf.
Get a Demo
Trusted by leading global enterprises.

















































Exposure is scattered across clouds, subsidiaries, partners, and Shadow IT, making it hard to track your external attack surface.

Tools stop at CVEs, leaving security teams without the business and attacker context to focus on exposures that actually matter.

Point‑in‑time testing can’t keep up with constant change, so validation is always a step behind reality.

Alert fatigue and unverifiable findings erode trust with engineering, so critical issues go unaddressed.
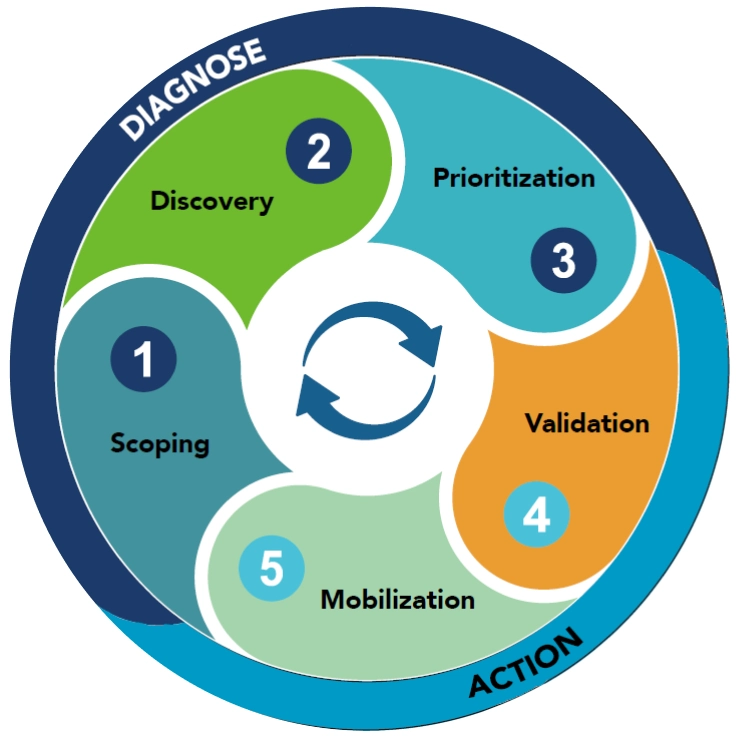
Attack surface assessment, delivered via external attack surface management tools, helps organizations understand visibility and reachability, but must be combined with prioritization, validation and mobilization.
 Gartner
Reference Architecture Brief: Exposure Management
Gartner
Reference Architecture Brief: Exposure Management
Scoping defines what your CTEM program will focus on and why. It aligns exposure management with business priorities, not just technical inventory.
CyCognito Approach
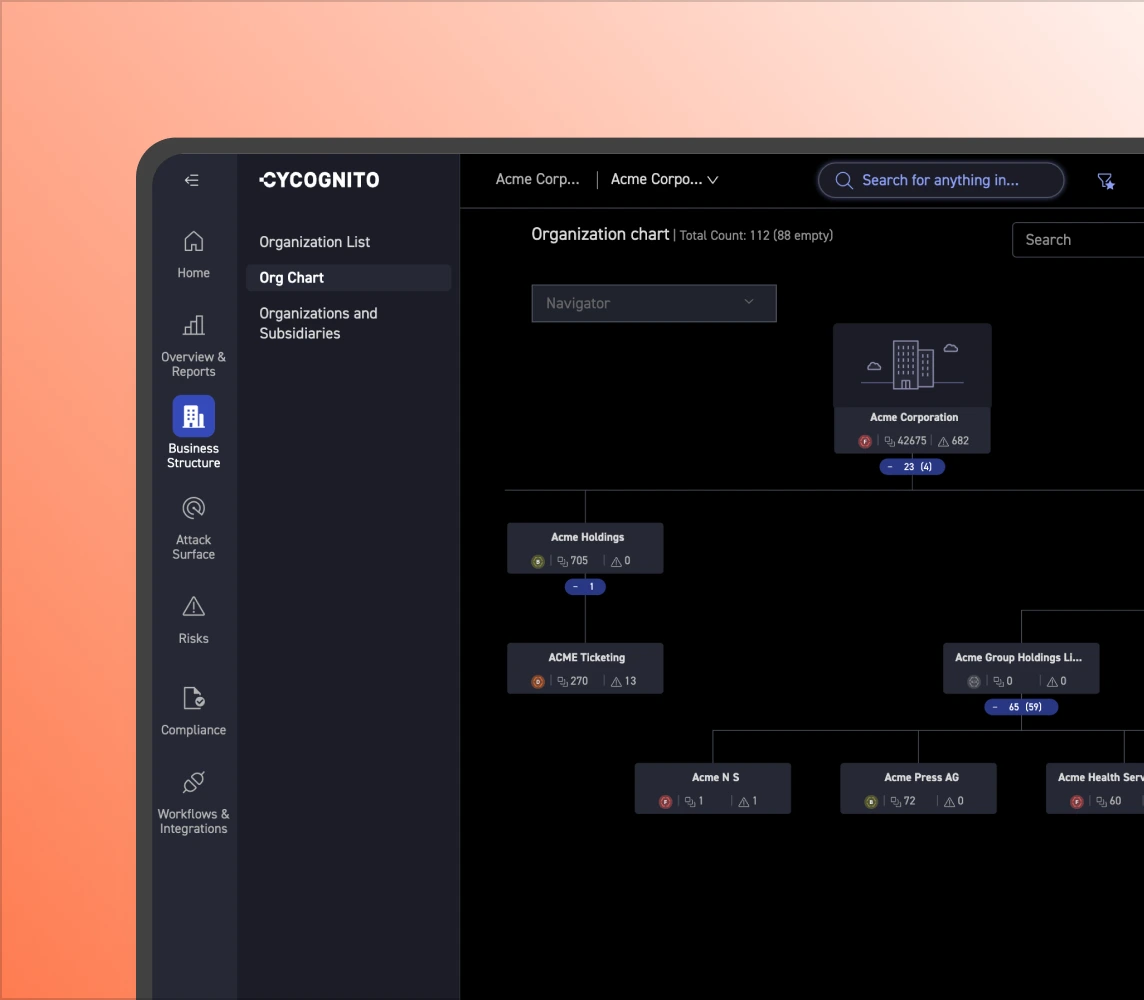
Discovery identifies all assets and their risks. The goal is not the volume of findings, but accurate visibility into what's exposed and its potential business impact.
CyCognito Approach
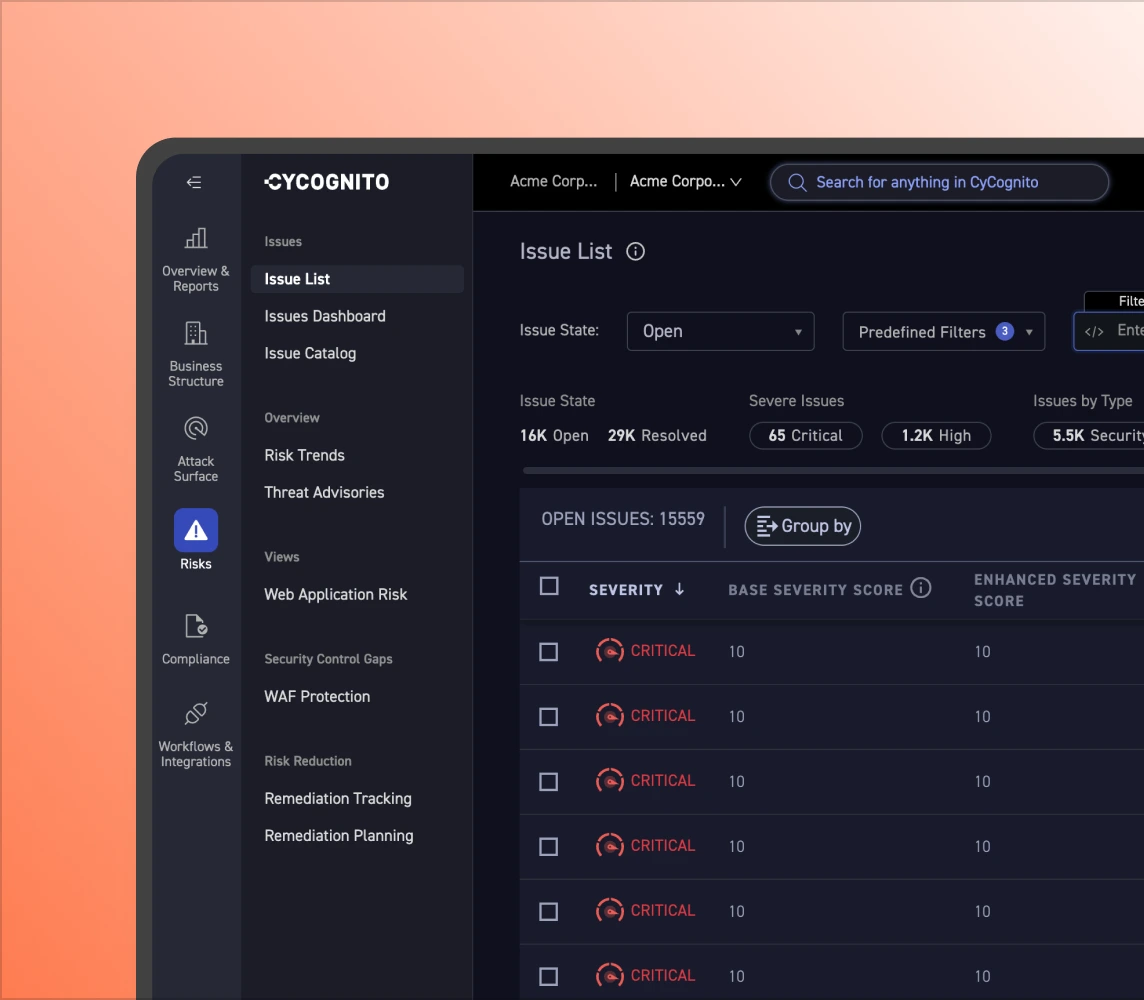
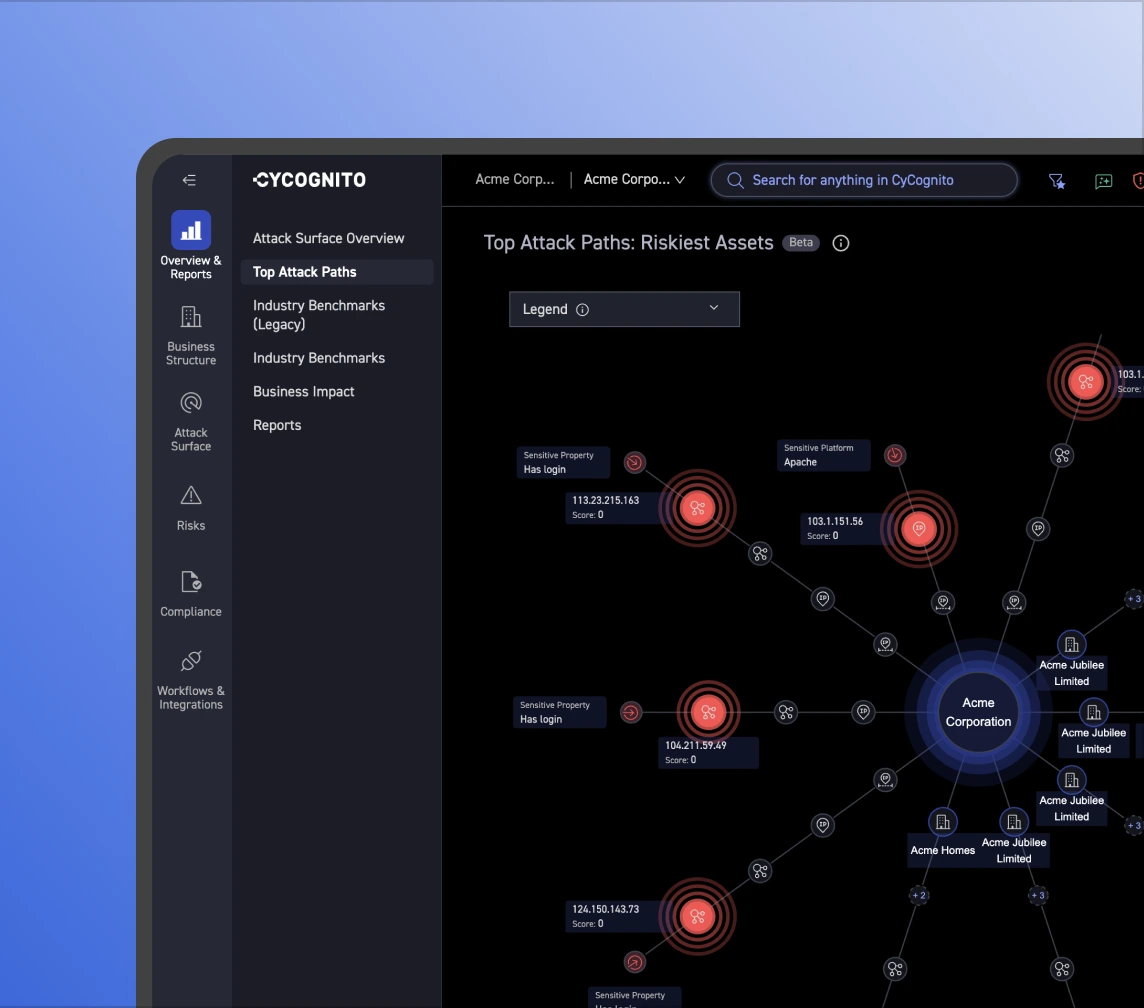
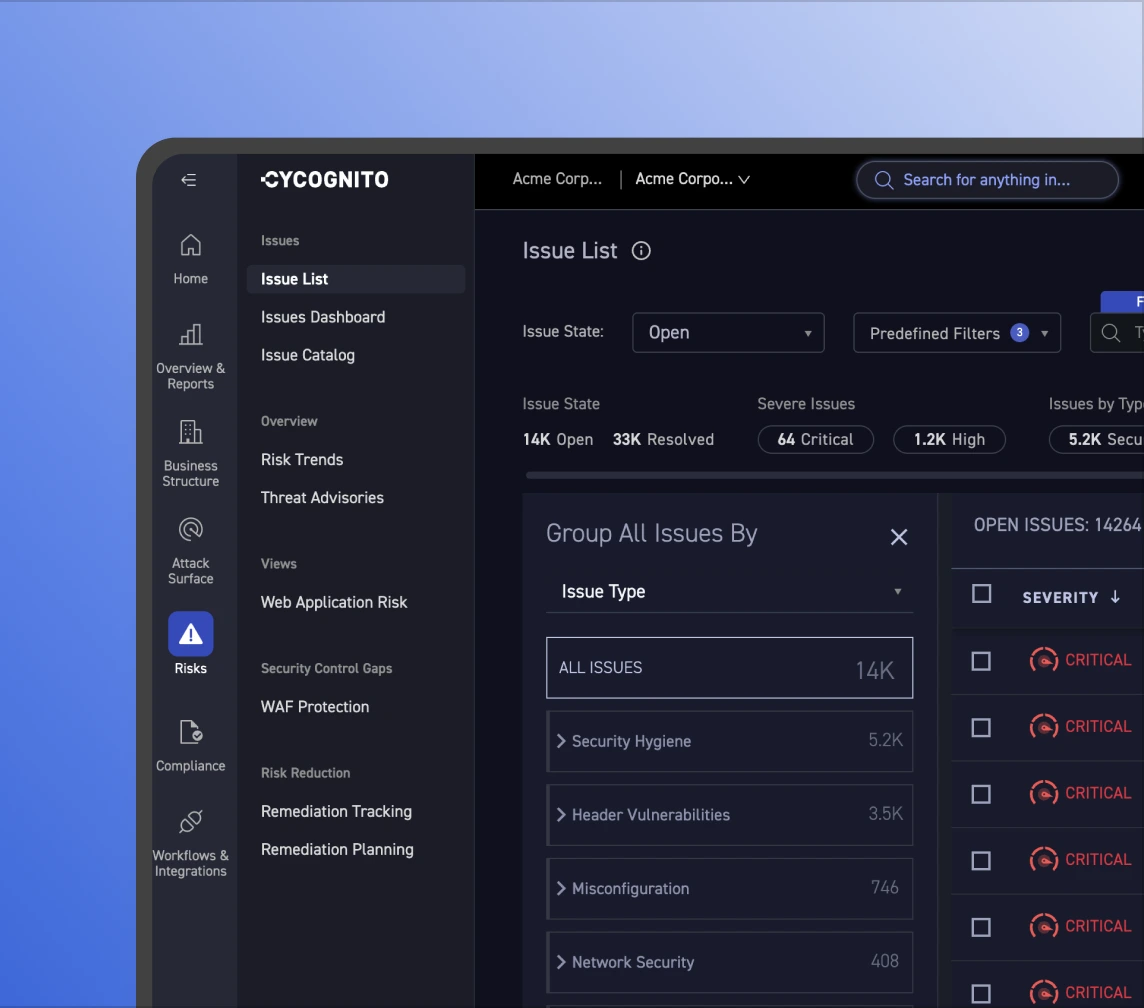
Prioritization separates real risk from noise. It combines exploitability, security controls validation, and business criticality to focus remediation where it matters.
CyCognito Approach
Validation confirms whether exposures can actually be exploited. It turns theoretical risk into a decision by using active testing aligned with real attacker methods.
CyCognito Approach
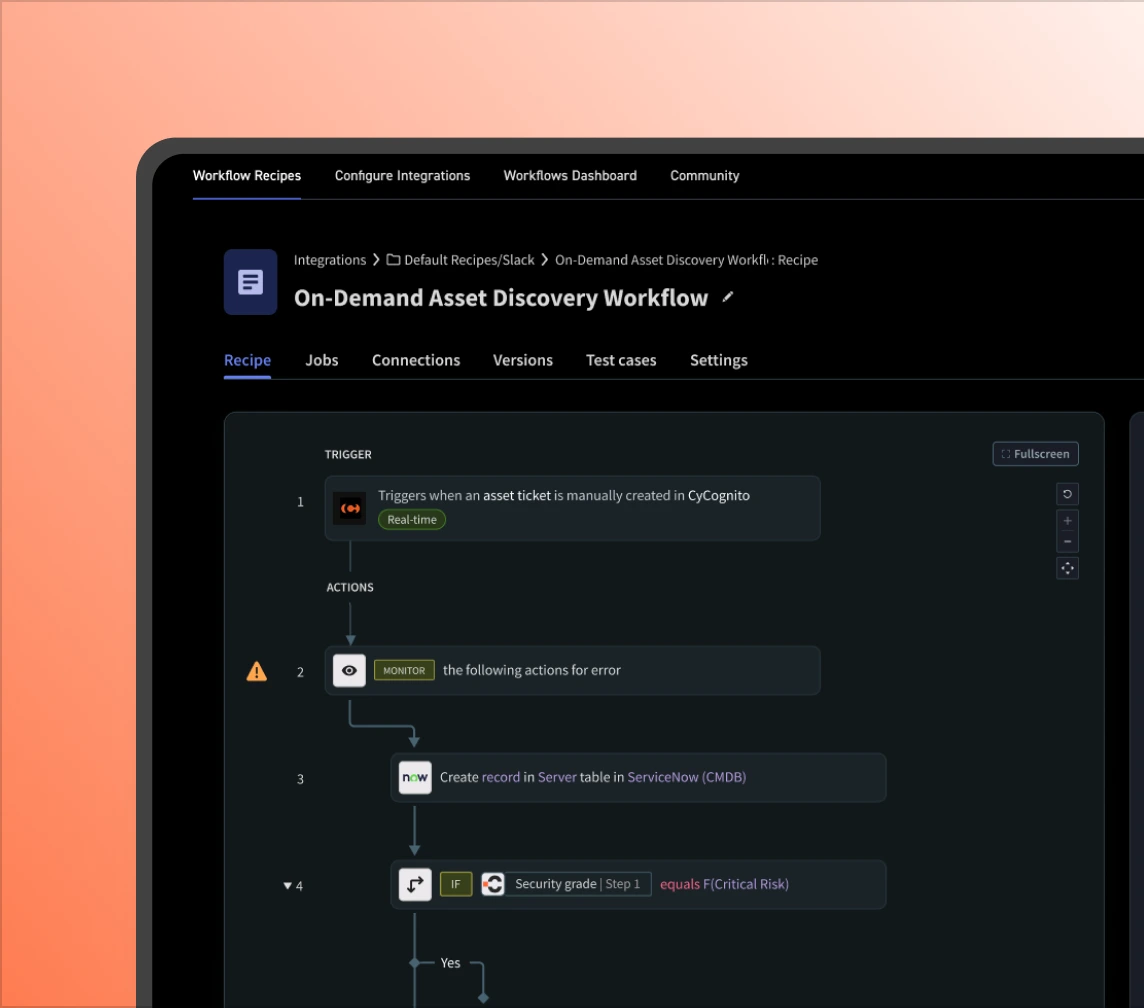
Mobilization ensures validated exposures turn into coordinated action. It routes findings to the right teams so exposure reduction can be tracked and verified.
CyCognito Approach