



CyCognito expands security coverage and cuts alert noise through active validation. Teams move past inflated severity lists and focus on the small set of exploitable issues that matter most.
Get a Demo
Trusted by leading global enterprises.

















































Augment vulnerability management with outside-in discovery that continuously maps external assets, including shadow IT and other 'unknown unknowns'.

Move beyond CVSS noise. Combine exploitability, business context, and threat intelligence to reduce “critical” findings from about 25% to 0.1% or less.

Group related issues and apply fixes along real attack paths to reduce MTTR and close multiple gaps at once.

Replace point-in-time assessments with continuous attacker-side testing. Reduce pentest and bug bounty spend over time by up to $500K.

CyCognito became a cornerstone of our security set-up by solving multiple pain points with automatic detection of assets, continuously analyzing for vulnerabilities, and by providing an easy-to-use and comprehensive platform to manage these issues.
 Berlitz
Stefan Romberg ・ Global CISO
Berlitz
Stefan Romberg ・ Global CISO
Internal scanners show what you deploy, not what attackers see. CyCognito maps the external attack surface from the outside in, revealing assets and access paths attackers can actually reach before they are exploited.
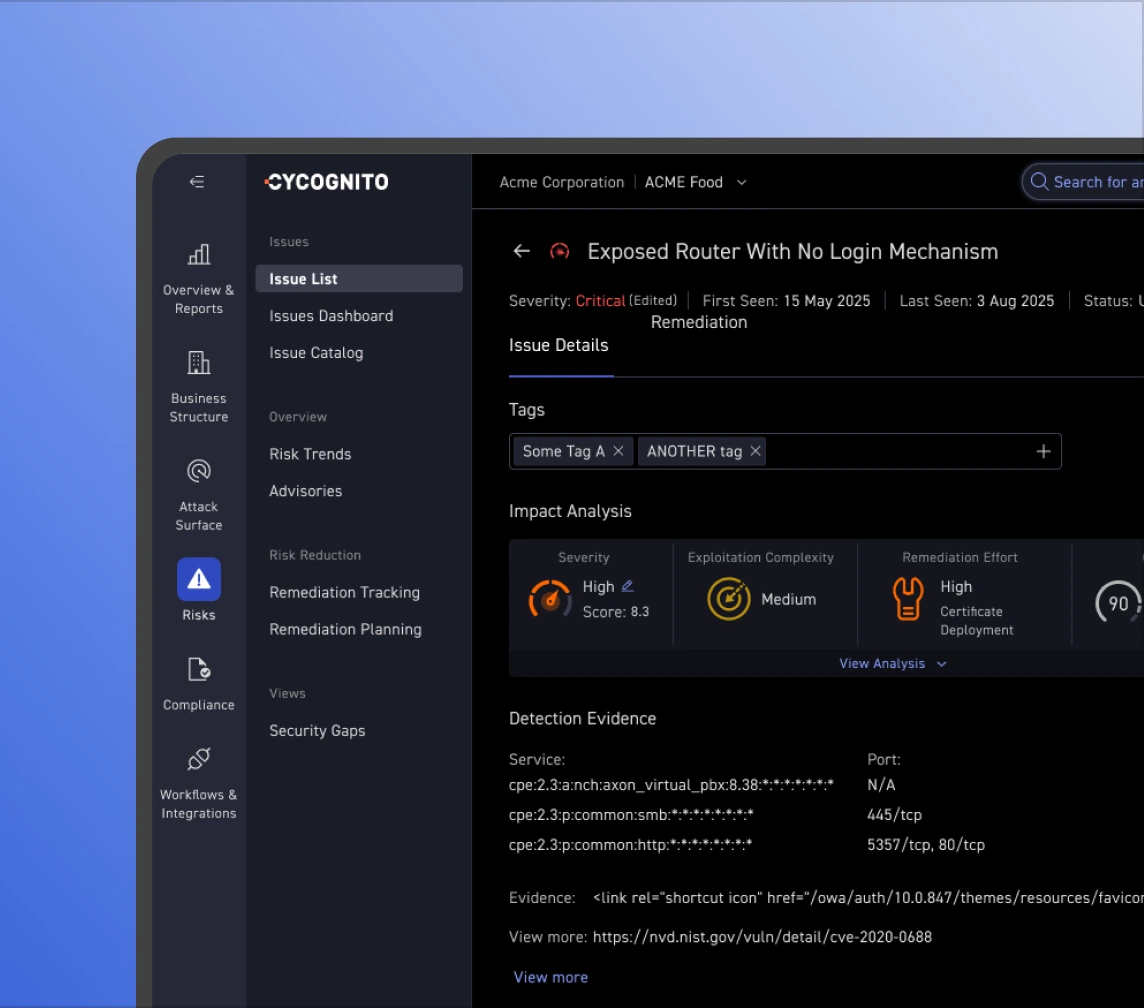
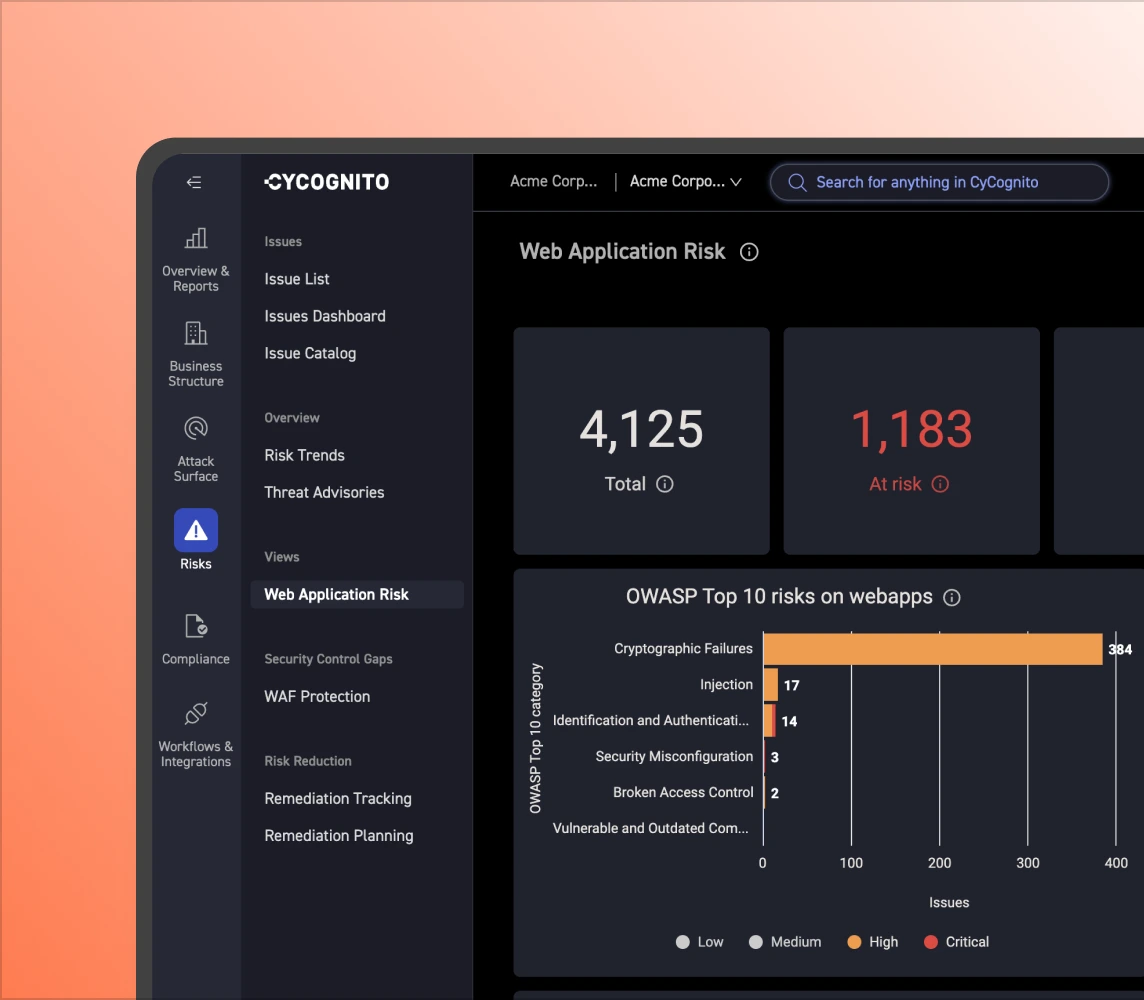
Severity scores alone inflate risk. Active testing validates which findings are actually exploitable, deprioritizing theoretical CVEs and surfacing the small set of issues that demand action.
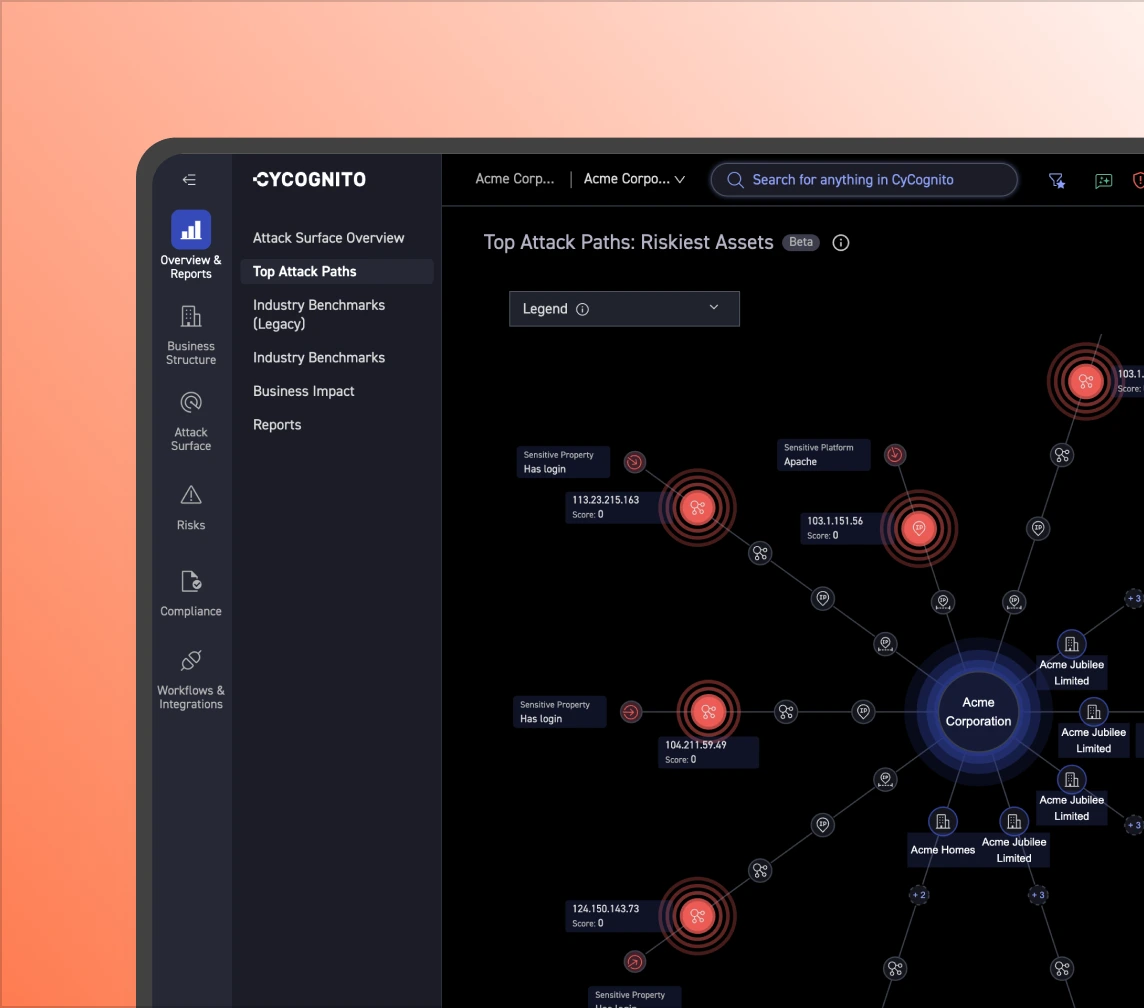
Fixing isolated issues does not stop attacks. Attack-path mapping shows how attackers could move across external assets and where a small number of fixes can break paths and reduce risk fastest.
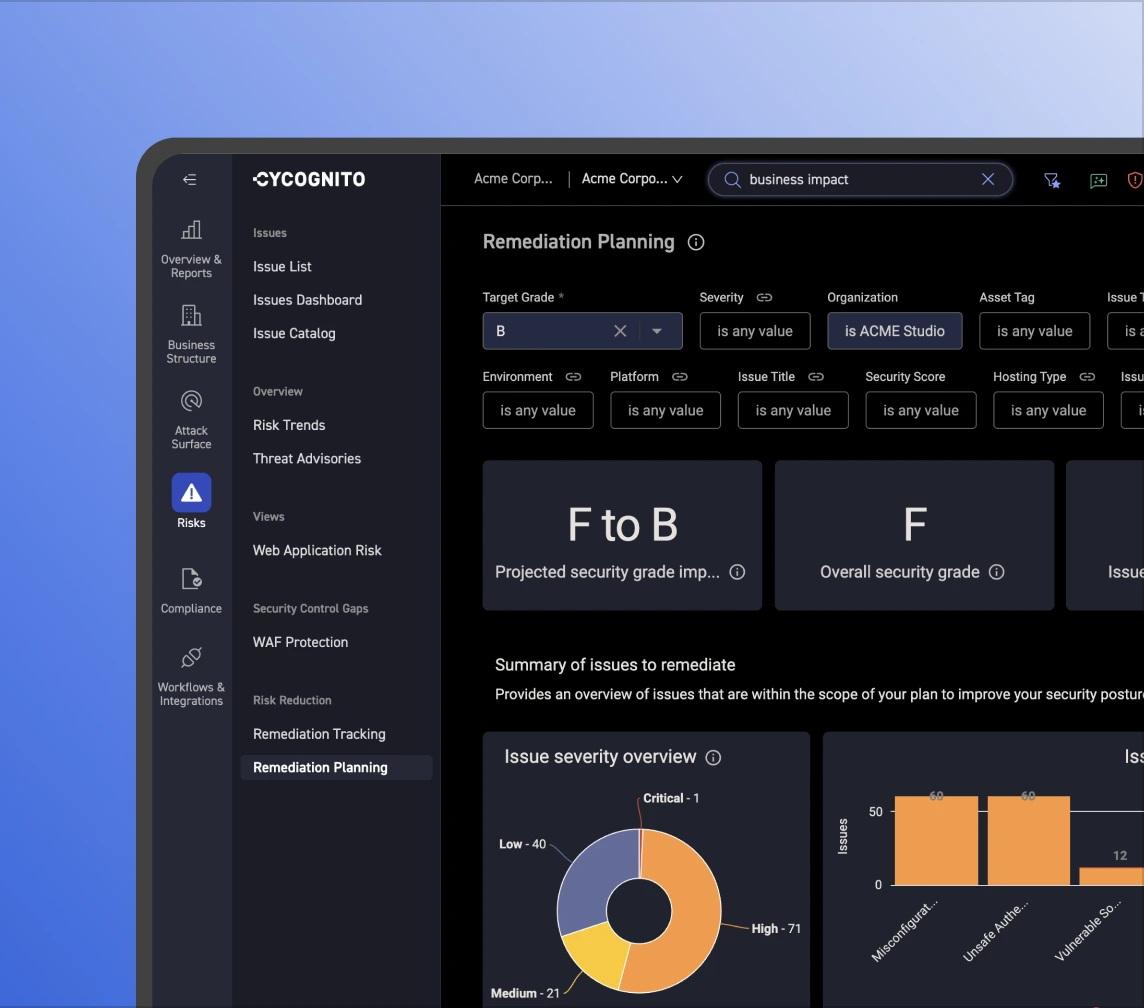
Point-in-time testing creates gaps and compounding recurring costs. Our platform provides continuous attacker-side testing that replaces repeated manual assessments with ongoing validation, helping teams reduce external spend while maintaining coverage.