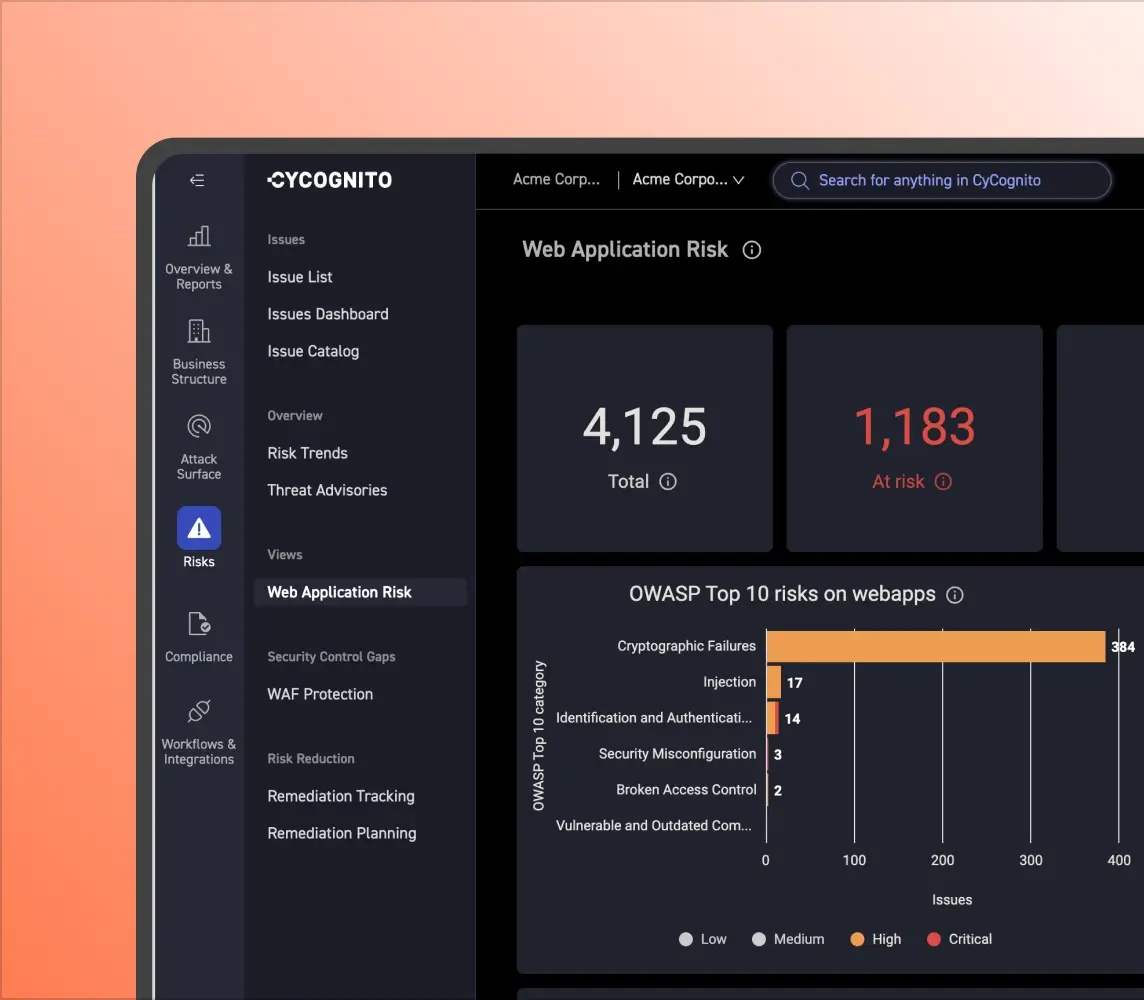
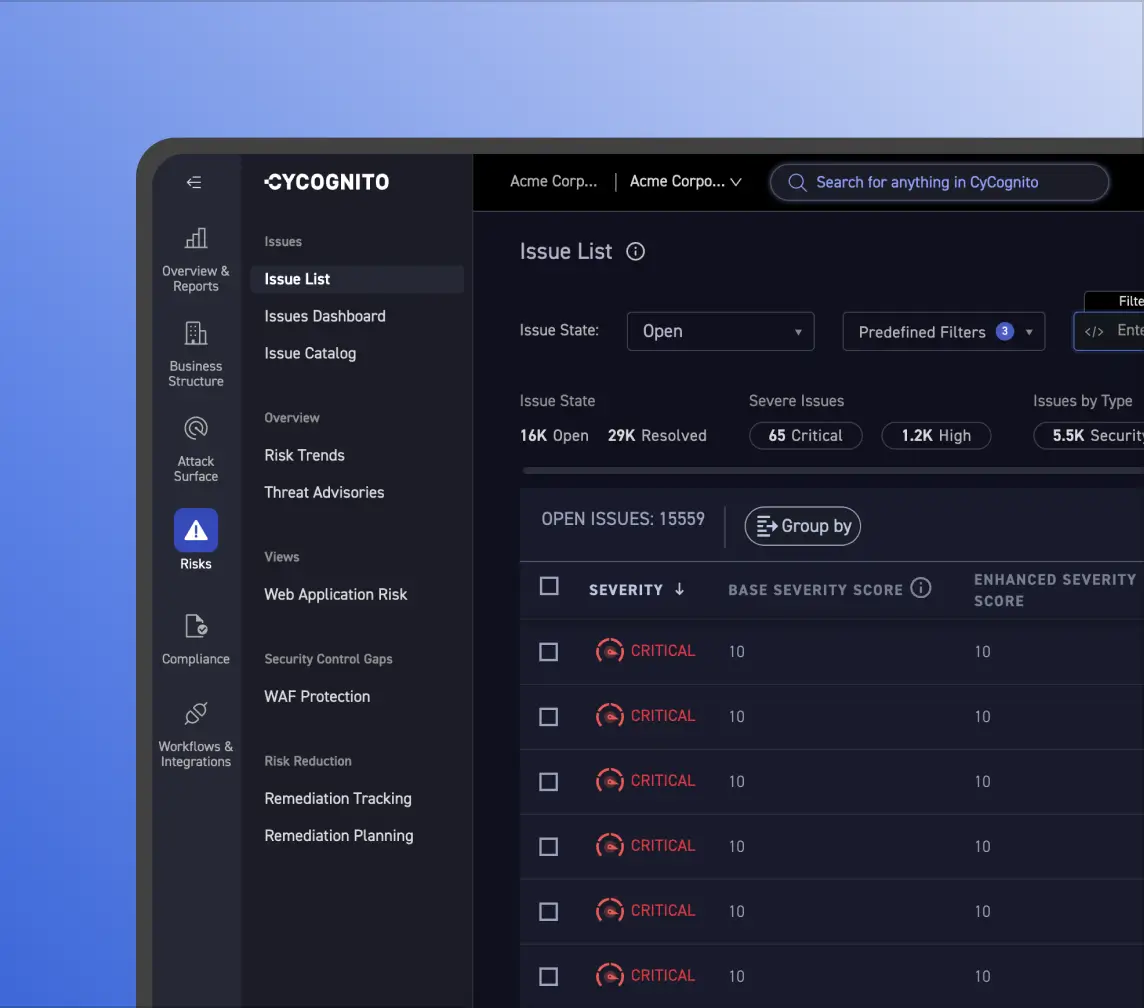
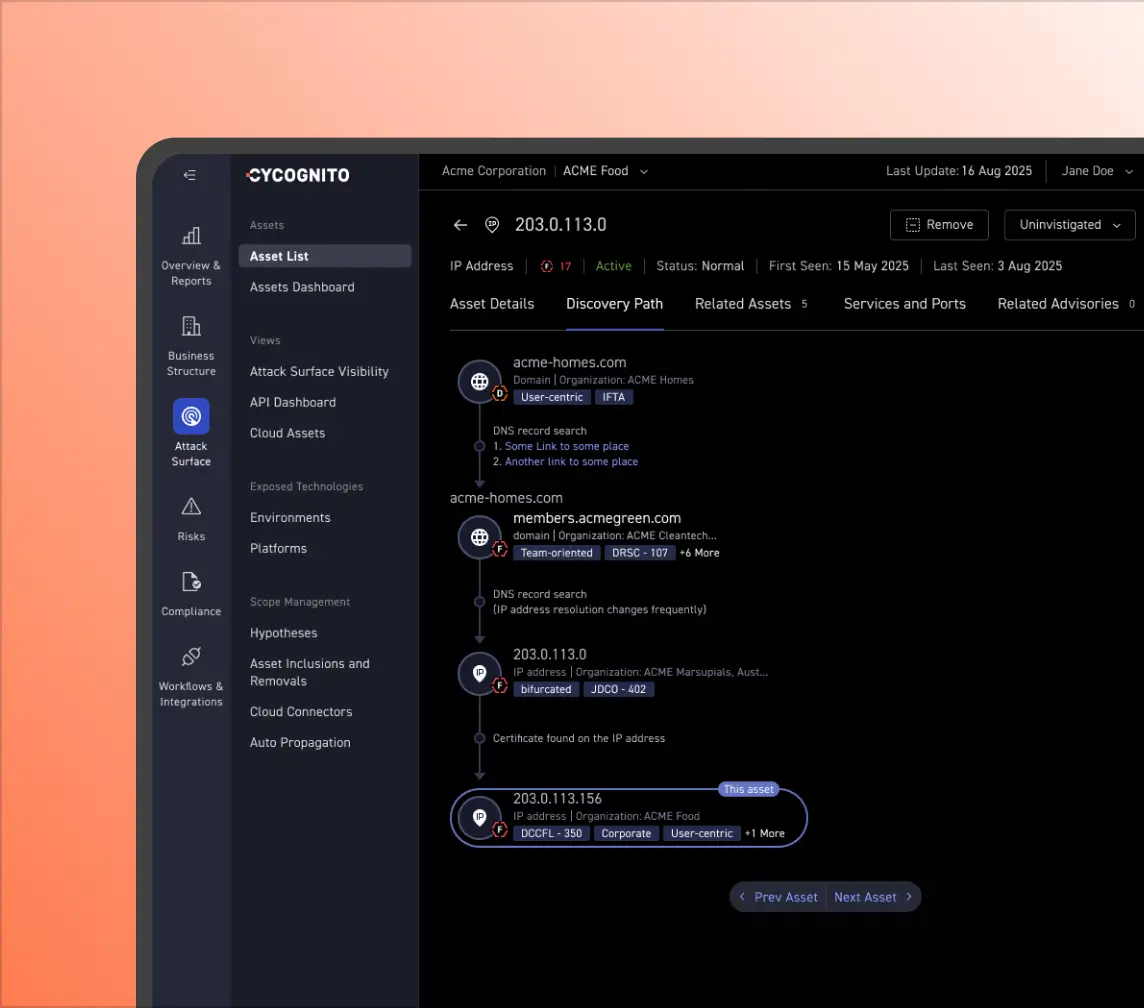
Gain Visibility into Third-Party Risk
According to Gartner, 60 percent of organizations work with more than 1,000 third parties. Many of these third parties provide hardware and software that can be misconfigured or vulnerable to attackers, placing their customers at risk.
- Polyfill.js: Attackers injected malicious JavaScript into polyfill.js for phishing and malicious advertising (CVE-2024-38526)
- MoveIT Transfer: Allowed remote code execution and stealing data using SQL injection (CVE-2023-34362)
- Apache Log4J: Allowed remote code execution in the Java-based logging utility (CVE-2021-44228)