Move beyond passive discovery with seedless visibility and continuous automated testing to validate every external risk.
Get a Demo
Trusted by leading global enterprises.
















































Gain over 20 times more visibility into external exposures than traditional ASM tools, revealing every internet-facing asset attackers could exploit.
Autonomous, black-box pentesting powered by 90,000+ testing modules continuously validates exposures across your entire attack surface.
Focus on the top 0.01% of risks that truly matter; validated external-to-internal attack paths with real business impact.
Save up to $500,000 annually by reducing manual pentesting costs and minimizing dependency on bug bounty programs.
CrowdStrike's External Attack Surface Management (EASM) solution, Falcon Surface, launched after the 2022 acquisition of Reposify. Its reliance on passive discovery and testing methods limits its effectiveness in identifying and mitigating threats.


CyCognito doesn’t rely on what you know to find what you don’t.

Falcon Surface cannot keep up with your dynamic attack surface.


CyCognito starts by mapping your organization and continuously updates it as your business changes.

Falcon Surface limited discovery misses unknown assets and key asset types.

High confidence automated risk validation for all assets.
Get a Demo
CyCognito actively and non-intrusively tests for 10,000s of CVEs with more than 90,000 tests.

Falcon Surface makes security teams choose between limited passive testing or disruptive agent-based testing.


CyCognito’s single source of truth scales your red team and makes your pen-testing budget go further.

Falcon Surface leaves red teams wasting time on asset discovery and basic tests.


CyCognito’s prioritization considers asset attractiveness to attackers, business context, targeted threat intelligence, and results from 90,000+ tests.

Falcon Surface misses key context, assets, and issues, leading to ineffective prioritization.


CyCognito works directly with leading security solutions like Splunk, ServiceNow, and Armis.

Falcon Surface’s lack of connectors and remediation tools slows MTTR.
* According to their evaluation in the The Forrester Wave™: Attack Surface Management Solutions, Q3 2024
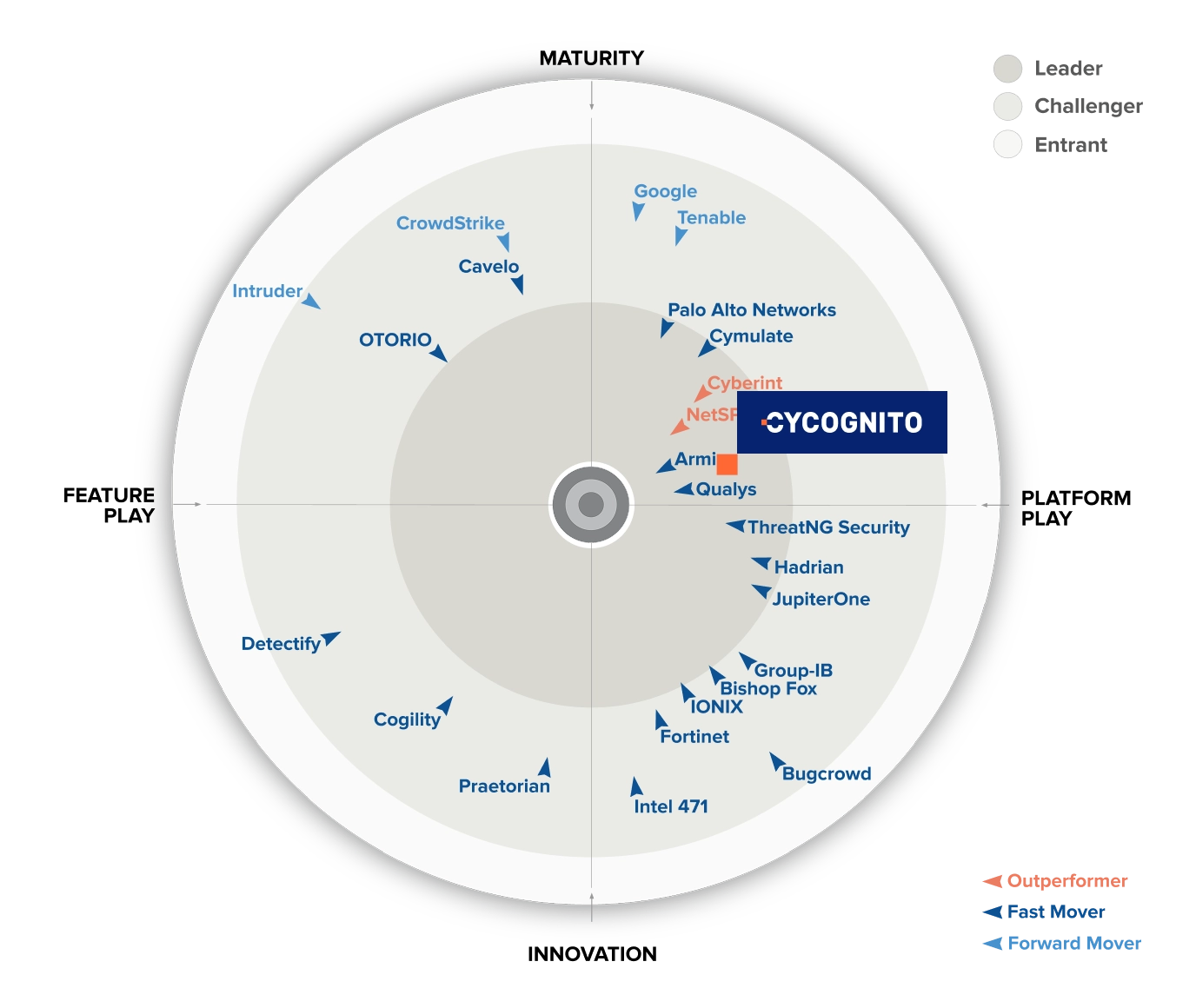
The 2025 GigaOm Radar recognizes CyCognito as an Attack Surface Management Leader for its depth of asset discovery, scalable automation, and precision in risk prioritization.
Read the report to compare internal and external ASM providers, see how they complement each other, and find the best fit for your organization.
Get Free Report