



CyCognito covers web apps, APIs, exposed endpoints, authentication surfaces, and third-party applications across your attack surface. Continuous security testing validates exploitability and control coverage, driving prioritized remediation.
Get a Demo
Trusted by leading global enterprises.

















































Use active external reconnaissance to map your full digital footprint, finding exposed web apps and APIs without seed data or manual scoping.

Run safe, unauthenticated black box DAST to catch runtime issues without disrupting users or affecting live traffic.

Identify exposed apps that collect or process PII and rank related findings higher based on potential impact.

Validate security controls under real-world conditions, confirming where WAF and other controls work, where coverage is missing, and which services are left open.

Combine exploitable findings with asset context, control coverage, and business function to produce ordered remediation lists that plug into existing workflows.

What was really interesting was to see the amount of cross-site scripting and other web application vulnerabilities we had in websites we own that have not been used by attackers as far as we know, and those have been fixed.
 Ströer
Ben Bachman ・ Vice President Group Information Security
Ströer
Ben Bachman ・ Vice President Group Information Security
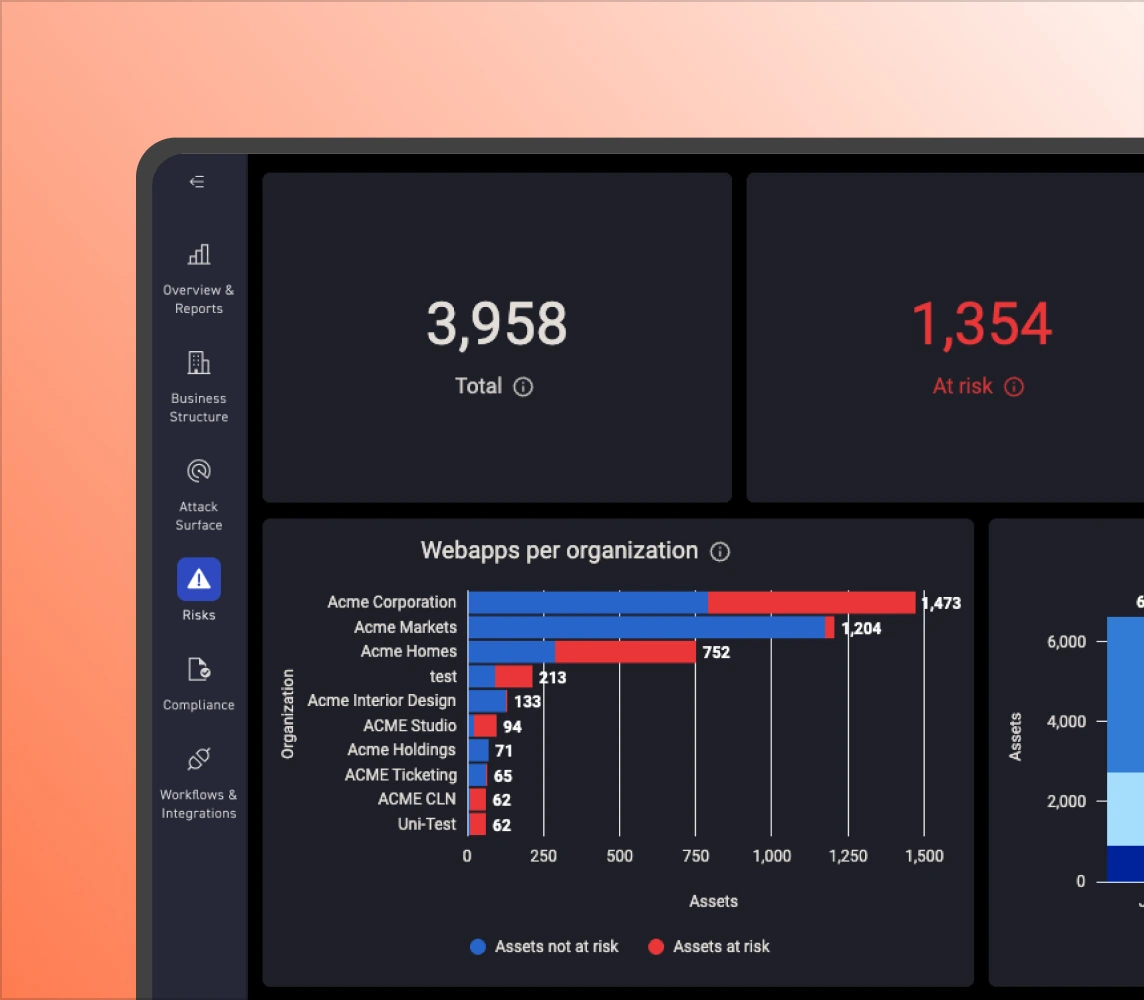
App inventories miss unknown and unmanaged applications. CyCognito maps externally accessible applications from the outside in, surfacing shadow apps, forgotten environments, and orphaned pages so teams have a complete view of what attackers can reach.
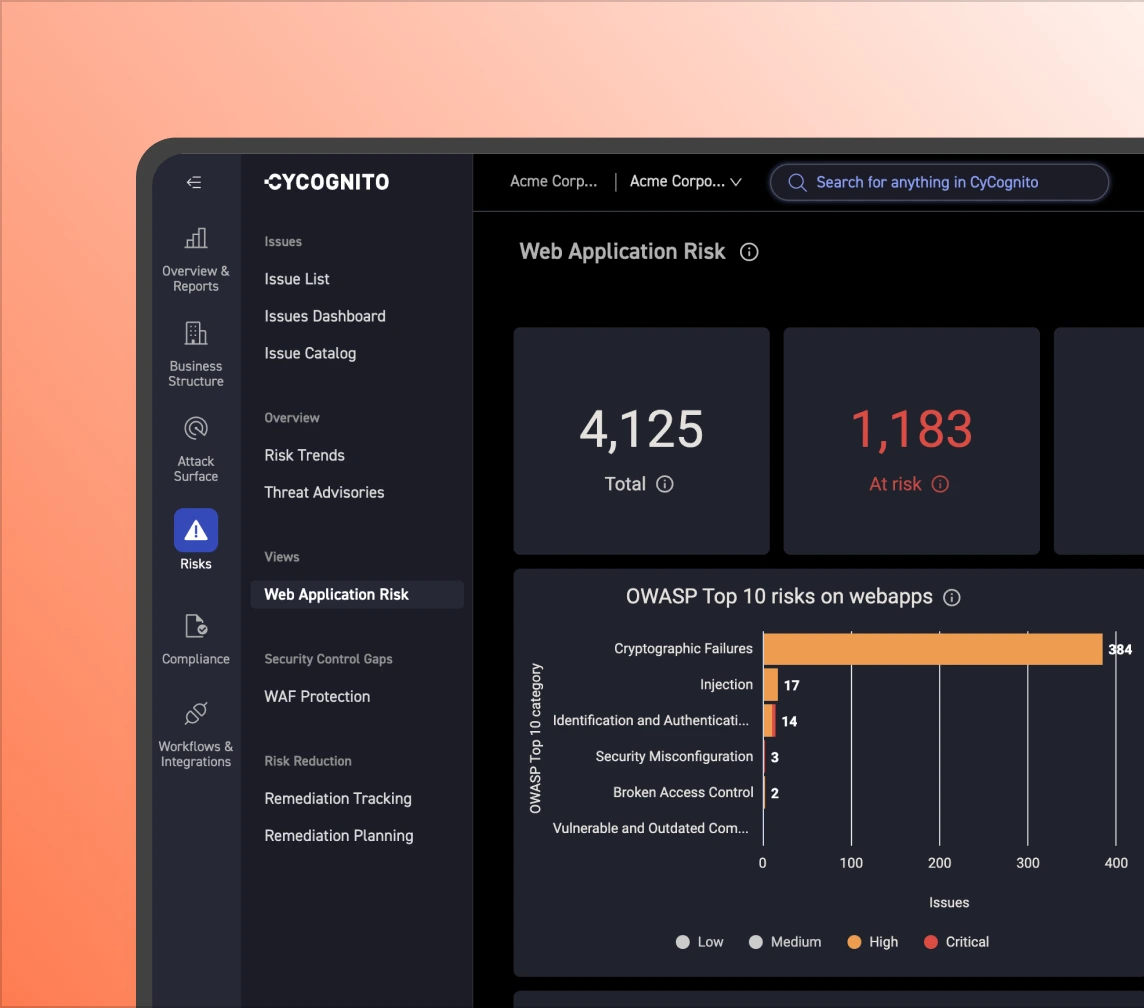
Point-in-time testing lags behind attack surface changes. Our platform runs continuous unauthenticated black-box testing (including DAST) across 30+ categories, covering OWASP weaknesses, data exposures, abandoned assets, authentication bypass risk, and more.
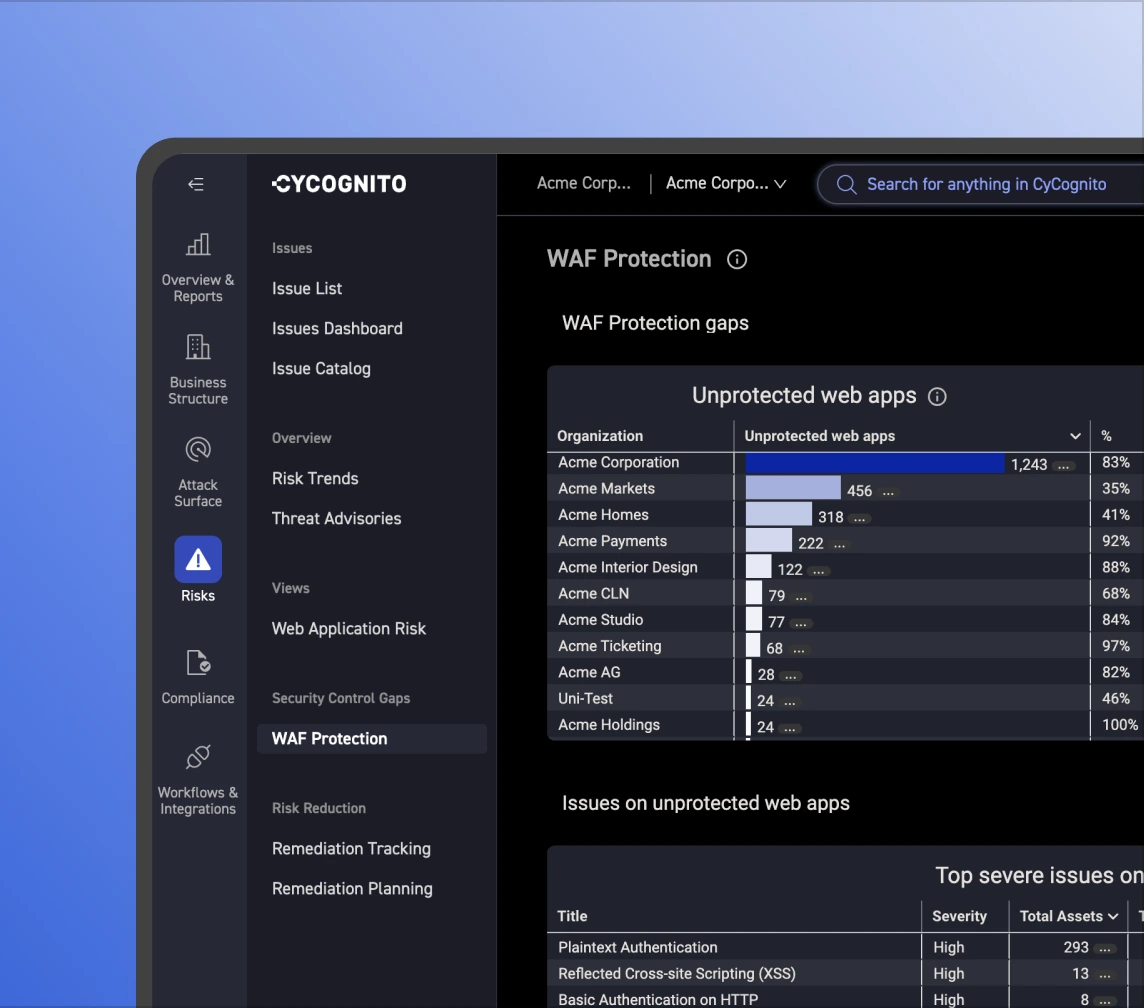
Controls reduce risk only when they actually work. CyCognito validates WAF and other application security protections, surfacing coverage and configuration gaps so teams can fix control failures before they become incidents.
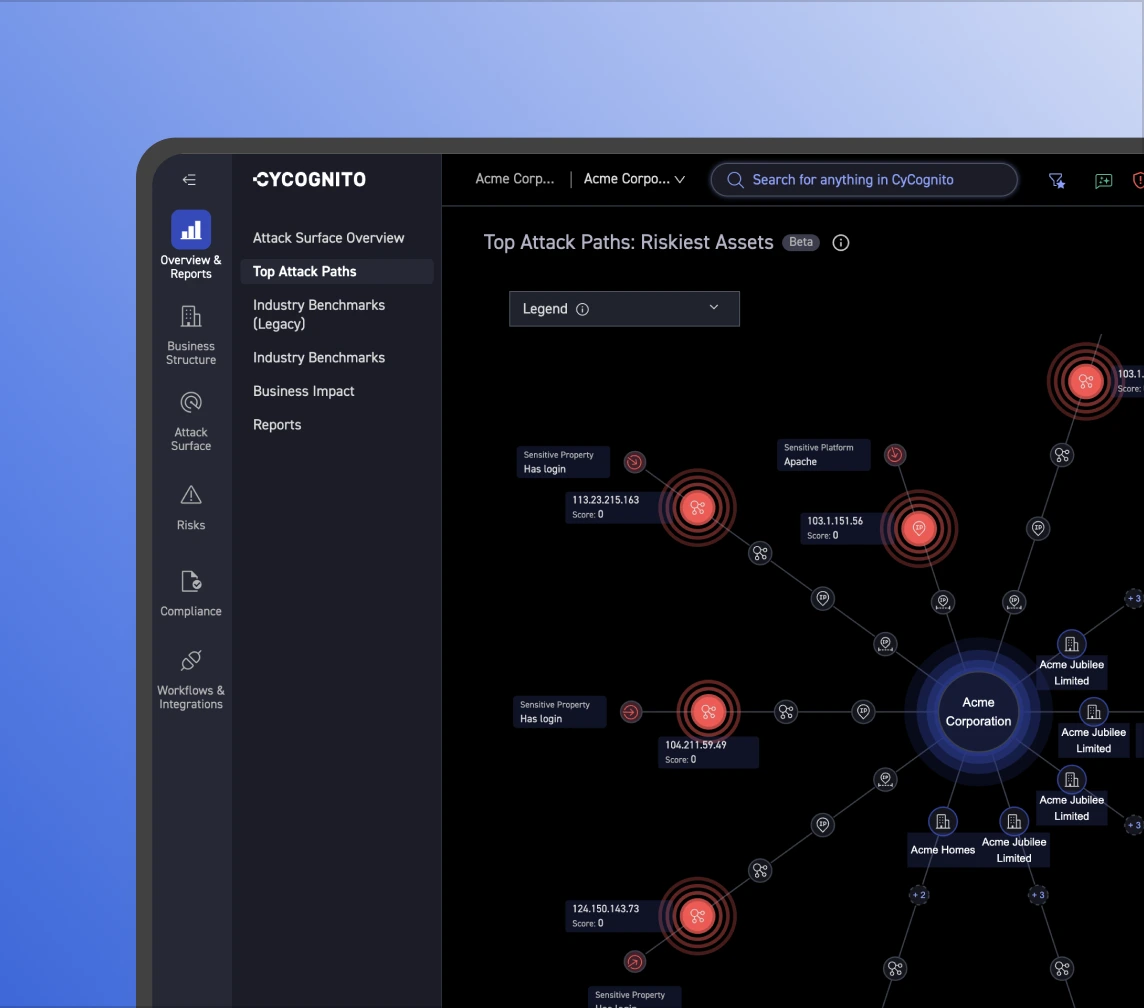
Long vulnerability lists don’t reflect real threats. Outside-in analysis, driven by proprietary prioritization logic, highlights the easiest paths into your environment and the fixes that break the most likely attack routes.
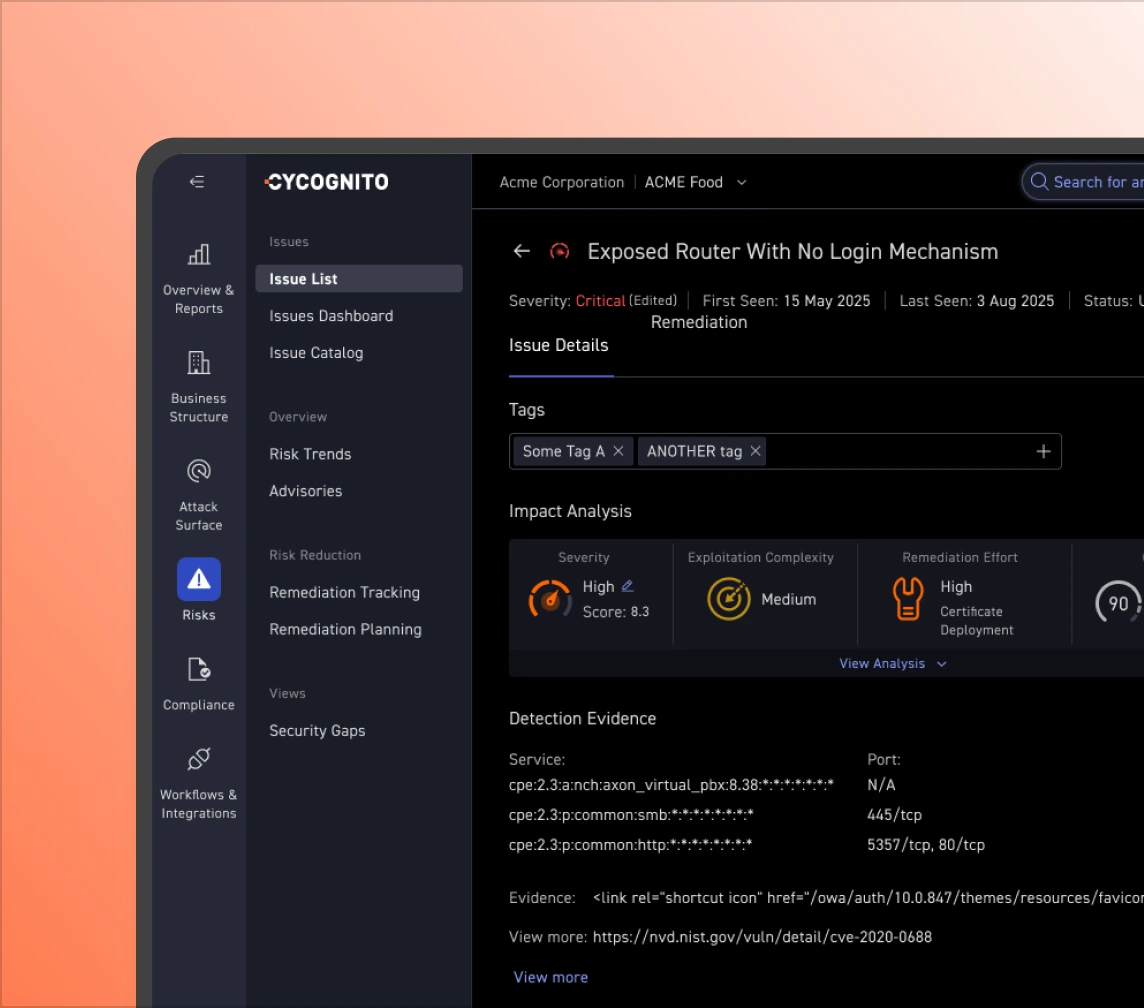
Not all apps carry the same impact. Key apps and pages (such as those that collect or process PII) are identified and prioritized, helping teams strengthen governance and compliance while separating theoretical issues from material risk.