



CyCognito extends CAASM with a complete view of external exposure, where more than 80% of attacks start. It discovers externally accessible assets, analyzes them from an attacker’s perspective, and feeds validated findings into existing CAASM workflows to strengthen governance, security, and compliance.
Get a Demo
Trusted by leading global enterprises.

















































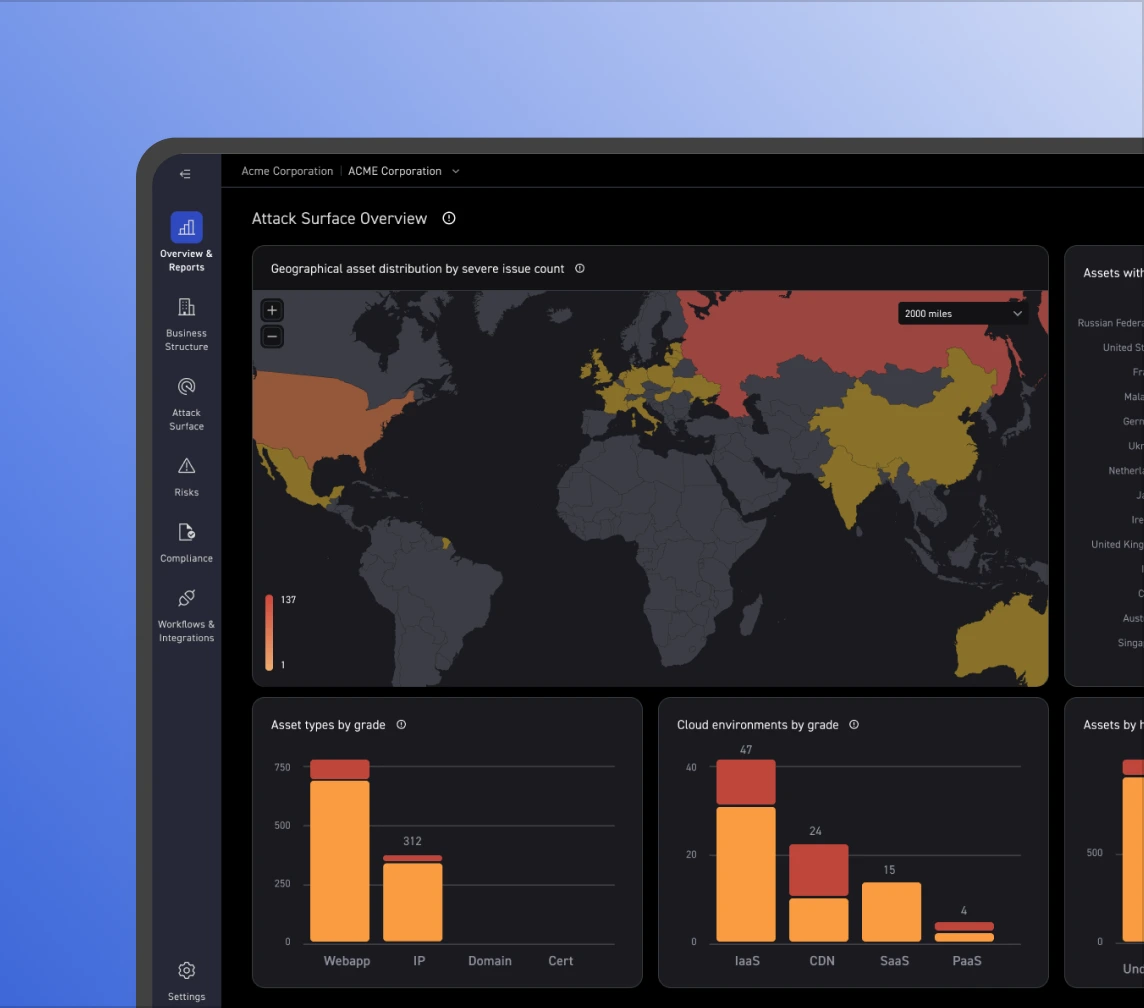
Reveal unmanaged and unknown external assets your CAASM misses, so no exposed system is left off inventory.

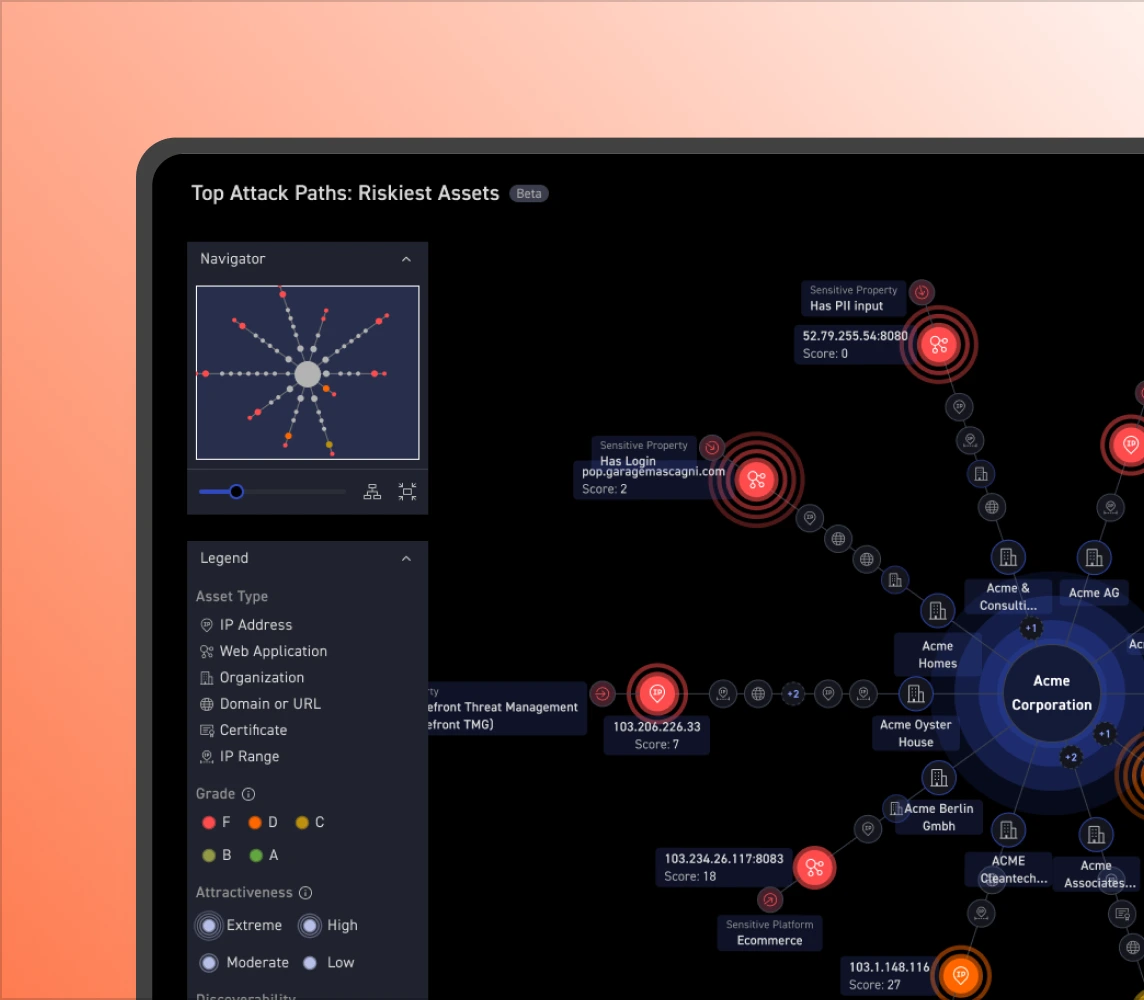
See how exposed external assets lead to critical systems, identities, and data, providing real outside-in attack-path context.

Identify owners and group related issues so teams fix top exposures first, address over 80% of risk, and cut MTTR by up to 88%.

Gain an actionable view of external exposure with a quantified and prioritized risk profile so teams know what to fix first.

I can’t point to another tool that does as thorough a job of exploring and exposing those assets that you didn’t even know you had. It’s so valuable.
 Light & Wonder
Kevin Kealy ・ Chief Information Security Officer
Light & Wonder
Kevin Kealy ・ Chief Information Security Officer
Asset inventories often stop at what teams already know. CyCognito uses seedless discovery to identify assets that sit outside CAASM visibility and maps them back to your organization, revealing exposed apps, cloud resources, shadow IT, and other “unknown unknowns”.
Asset lists miss attack paths. Through integrations, CyCognito connects external security findings to internal systems and identities, exposing outside-in attack paths that show how attackers could move from exposure to impact.
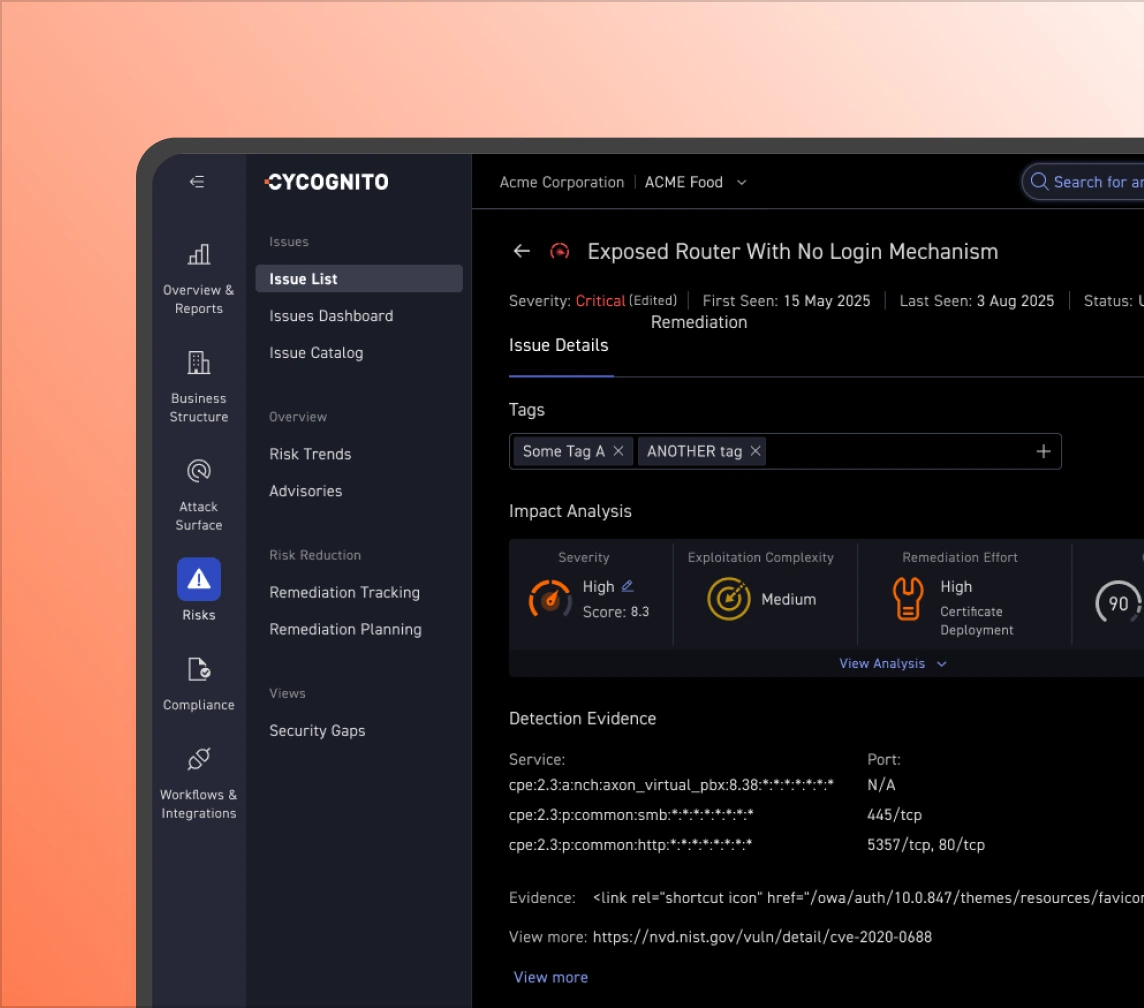
Signals without validation create noise. Our platform runs 90,000+ security tests to confirm exploitability and feeds those findings into CAASM, so prioritization reflects real risk, not just inventory signals or CVSS-based severity scores.
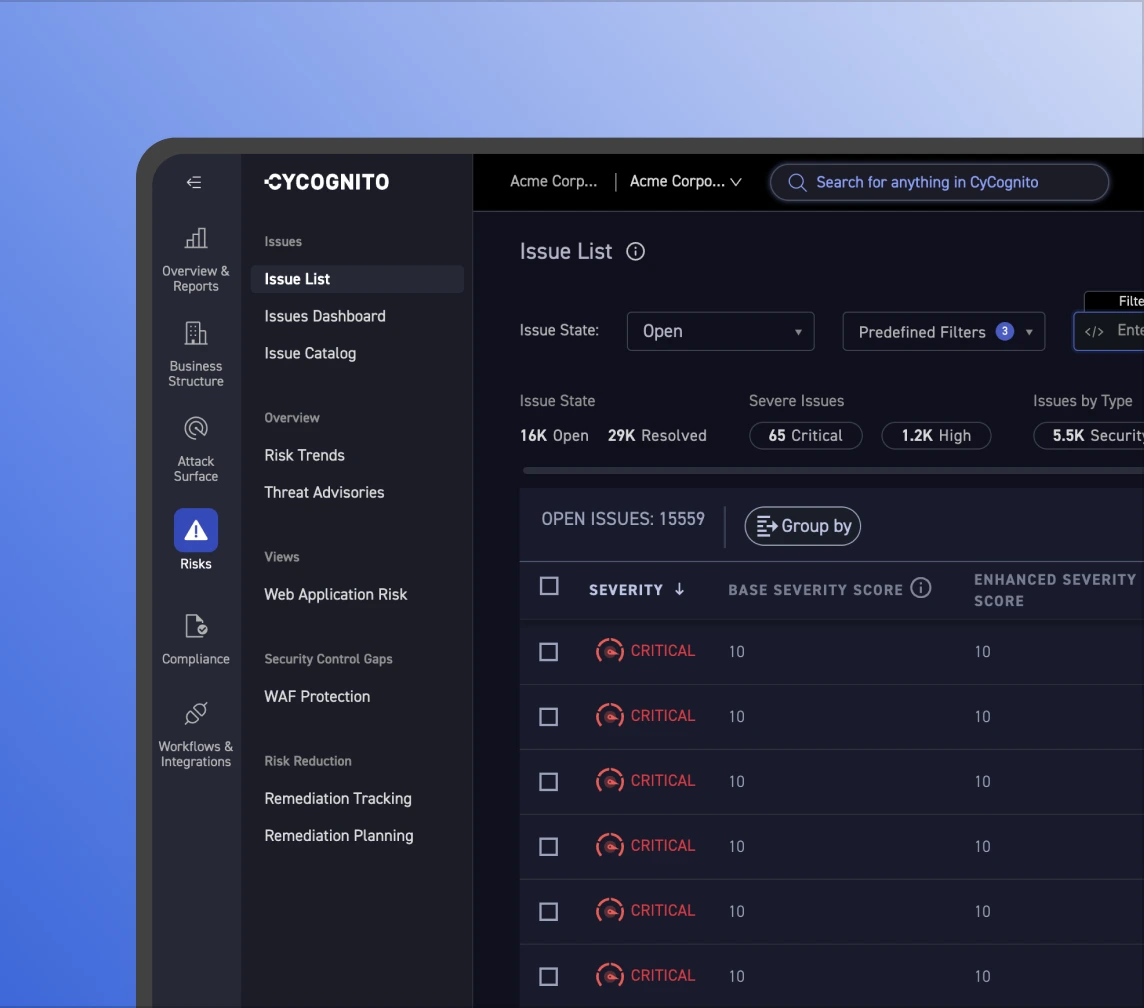
Useful inventory drives action. Ownership and risk context are added to CAASM, enabling consistent policy management, shorter remediation cycles, and stronger governance and compliance across environments.