



CyCognito enables security and operations teams to proactively identify, prioritize, and remediate risk through comprehensive attack surface management.
According to the Verizon Data Breach Investigations Report, 83% of cyberattacks occur through external attack vectors.
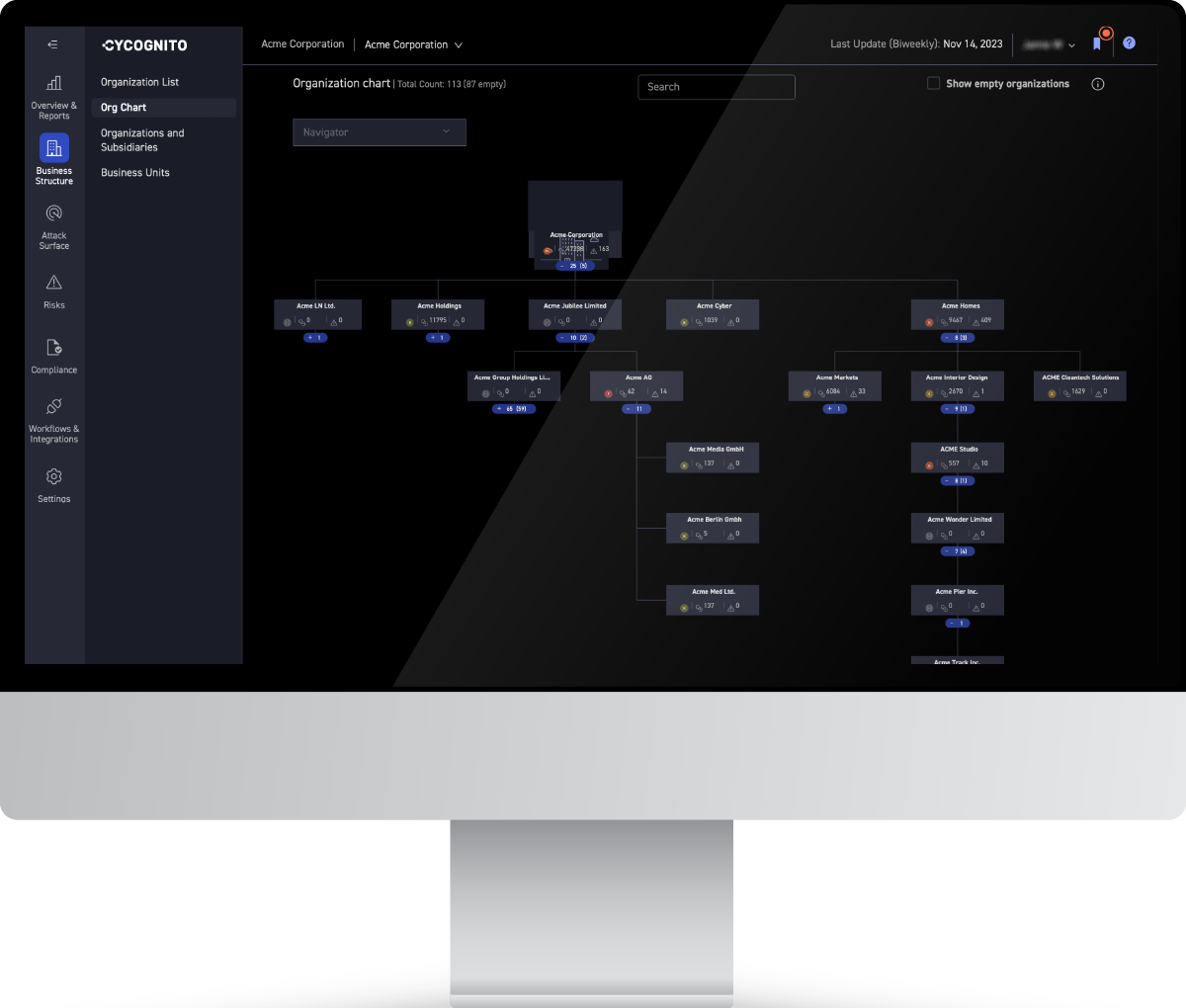
The CyCognito platform reveals more of your external attack surface than you were aware of previously. Most customers see at least 30% more. Our platform also tests more of your attack surface than you did before, so you can eliminate the gaps that attackers target and protect your entire attack surface.

Alex Schuchman | Chief Information Security Officer
Alex Schuchman
Chief Information Security Officer
Everything you need to know about our platform. Can’t find what you’re looking for? Please reach out to our team.
Organizations cannot remove all of their assets from the internet, otherwise they would be unable to do business in today’s digital world. Attack surface protection delivers more than just a digital asset inventory, it ensures that an organization’s exposed and connected IT assets are known, secure, monitored for issues and defended against attacks.
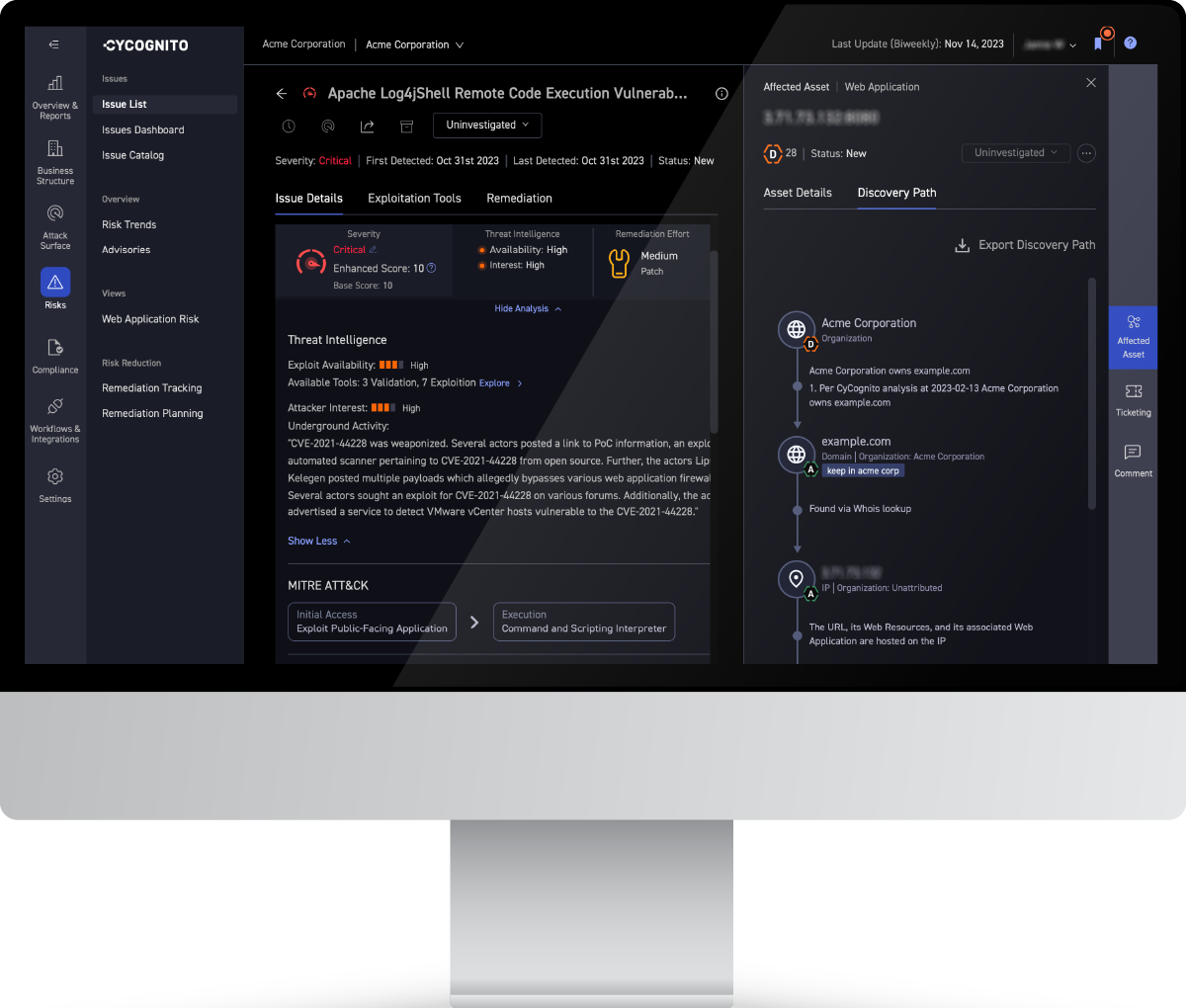
Attack surface protection best practice includes continuous asset discovery across the entire internet looking for new and existing internet-exposed assets that belong to your company, developing business context about how assets relate to the business, active security testing of those assets, and providing IT teams guidance to expedite remediation.
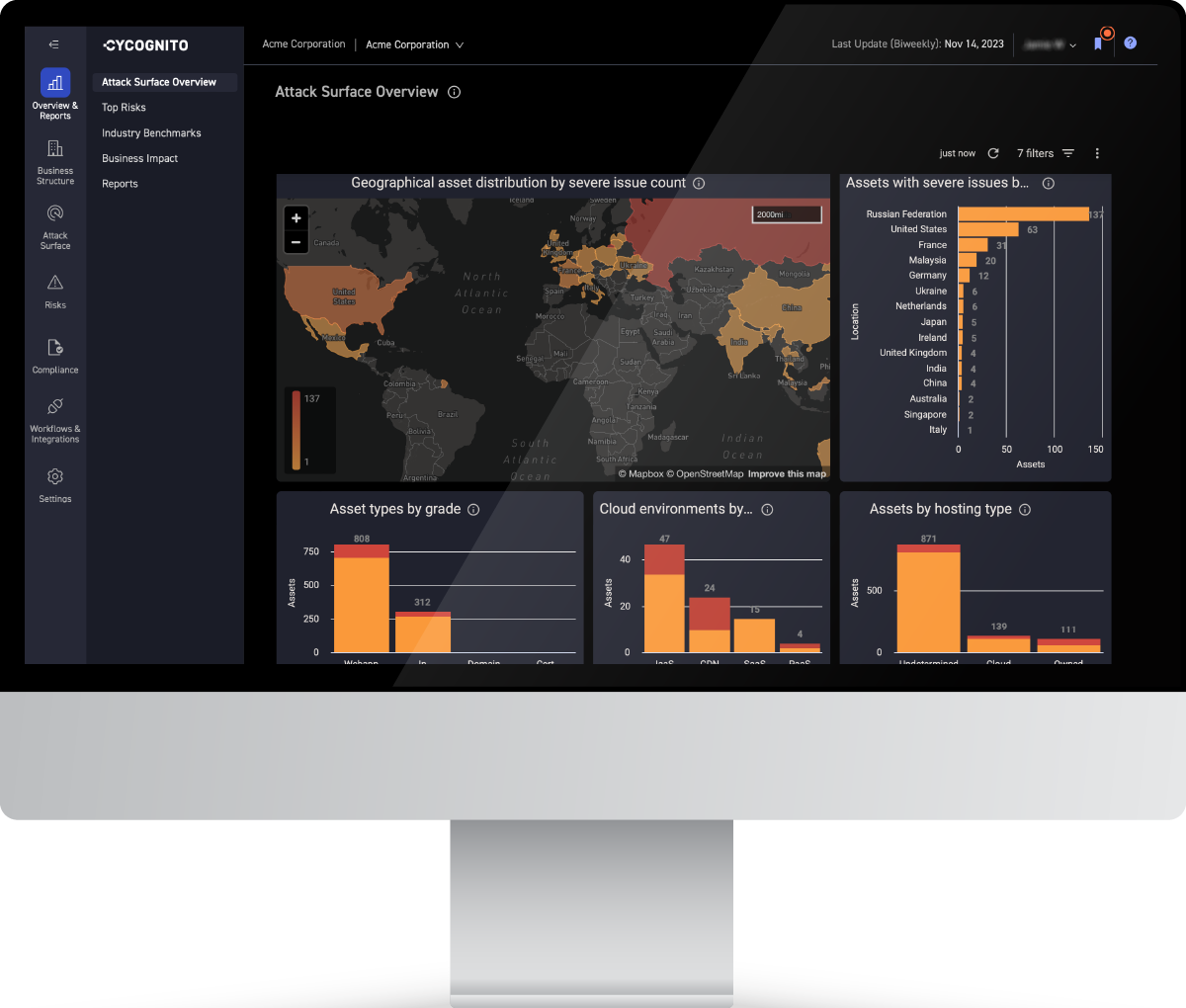
The platform provides the continuous visibility necessary to understand and truly know your attack surface, even when that attack surface grows and changes daily due to the proliferation of cloud and SaaS applications. The platform also provides the guidance needed by security operations teams to identify high risk areas, monitor threats, and secure those exposed assets.
Please see our blog on the “Build vs Buy” decision and speak to us about a Total Cost of Ownership workshop.
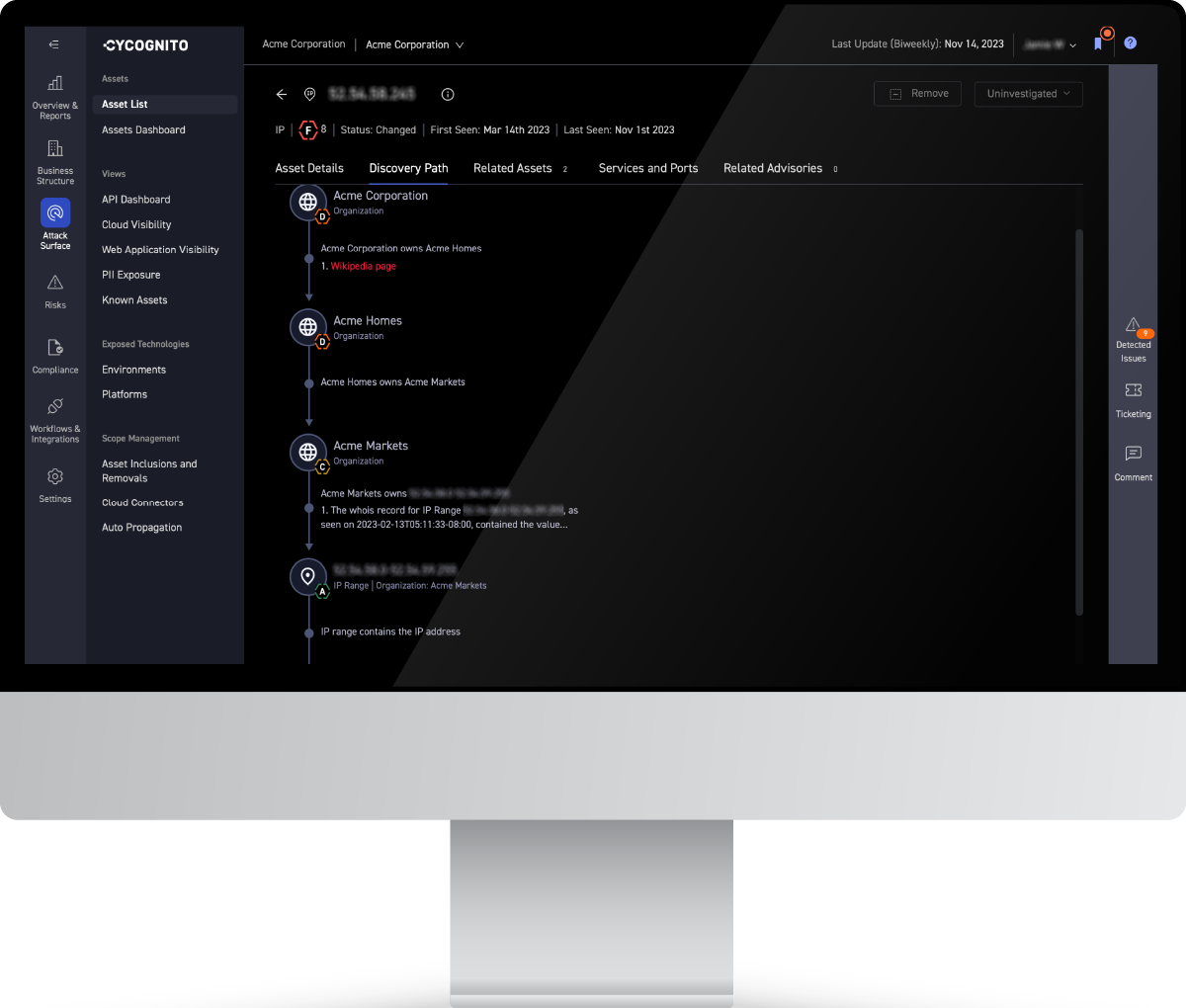
A variety of sources are used, including passive DNS, Wikipedia, public financial data, whois, and certificate databases.
The CyCognito platform discovers and tests all assets discoverable via the internet. This process finds assets that were previously unknown, unmonitored, and exposed to attack. The platform continuously monitors and tests all assets associated with an organization. It alerts to new, existing, or recurring issues, and provides remediation guidance to fix those issues and eliminate the risk presented by that asset.