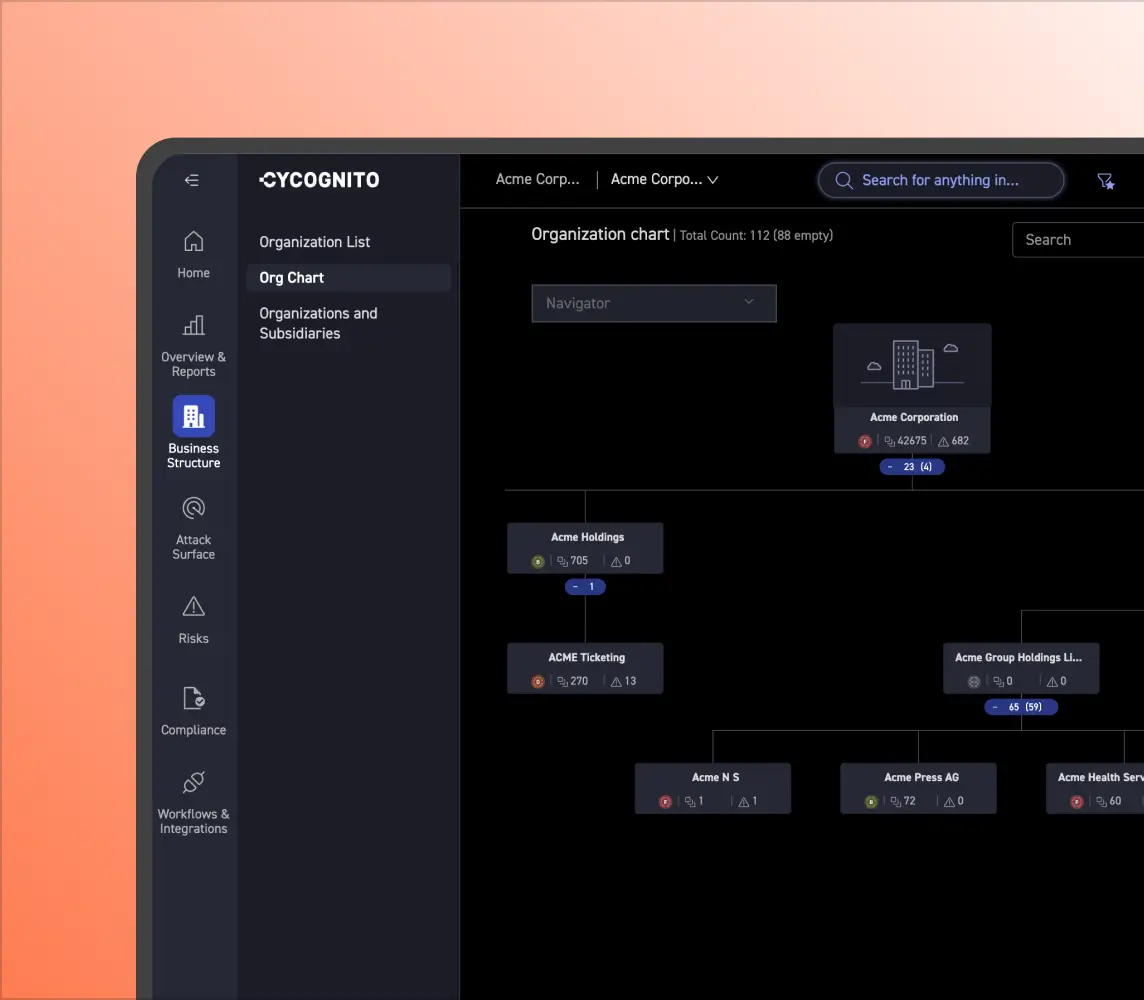
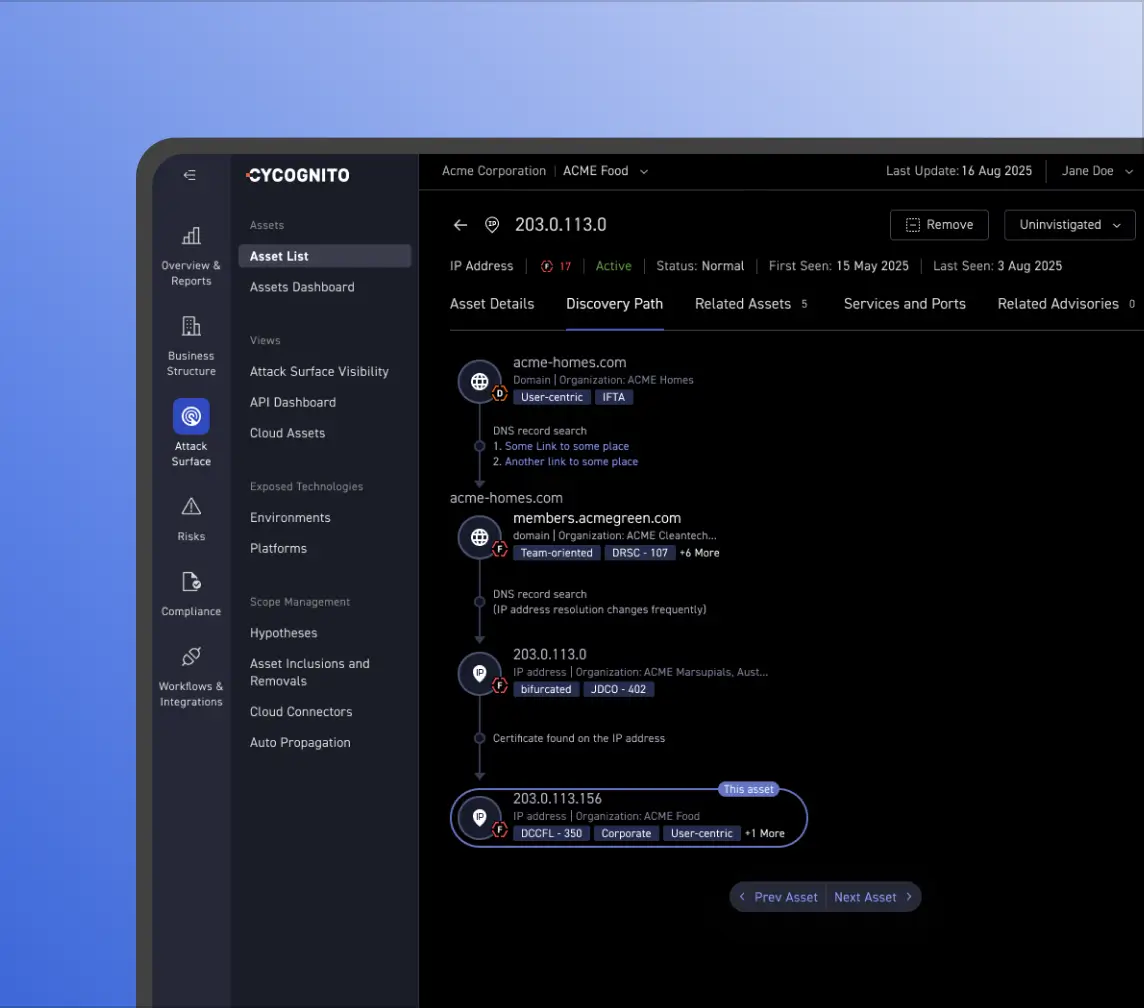
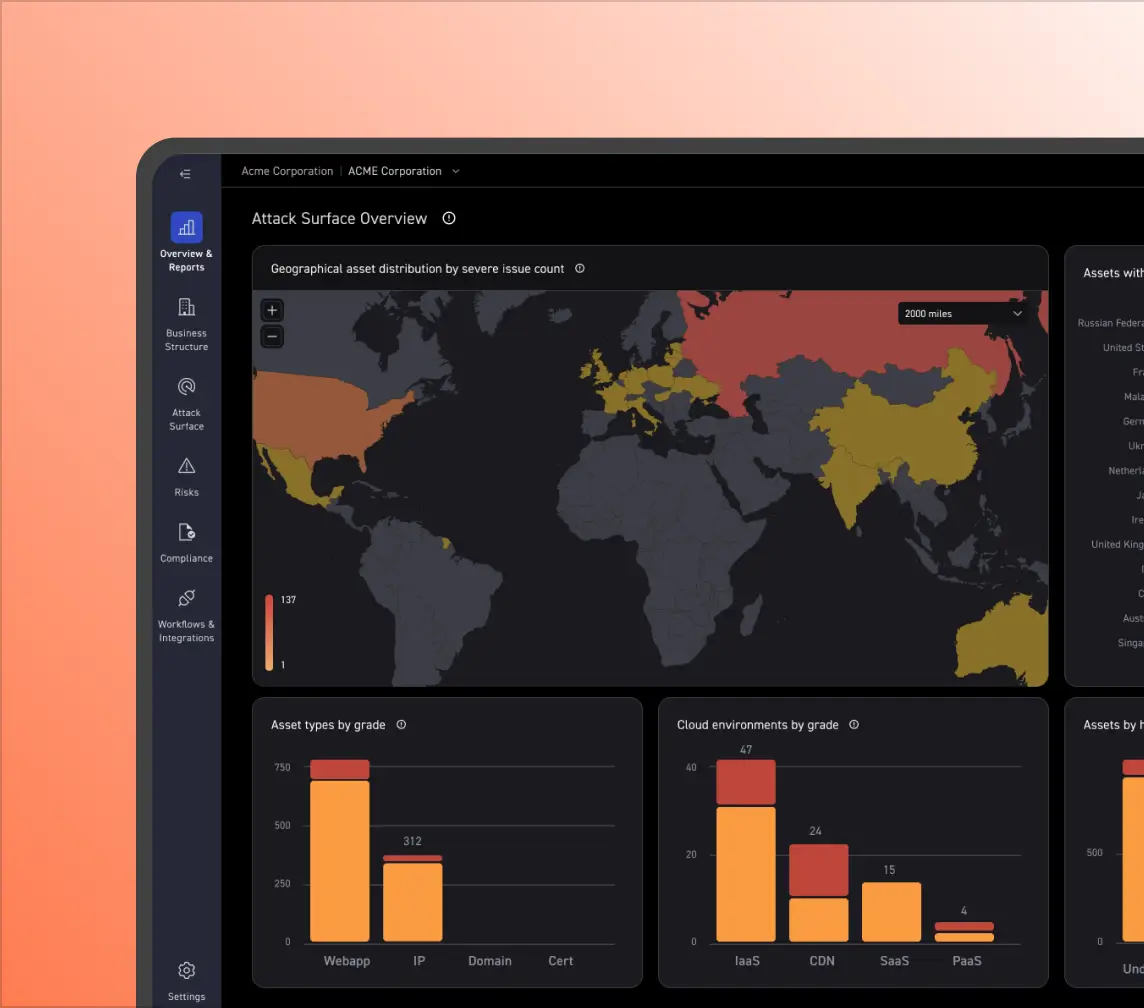
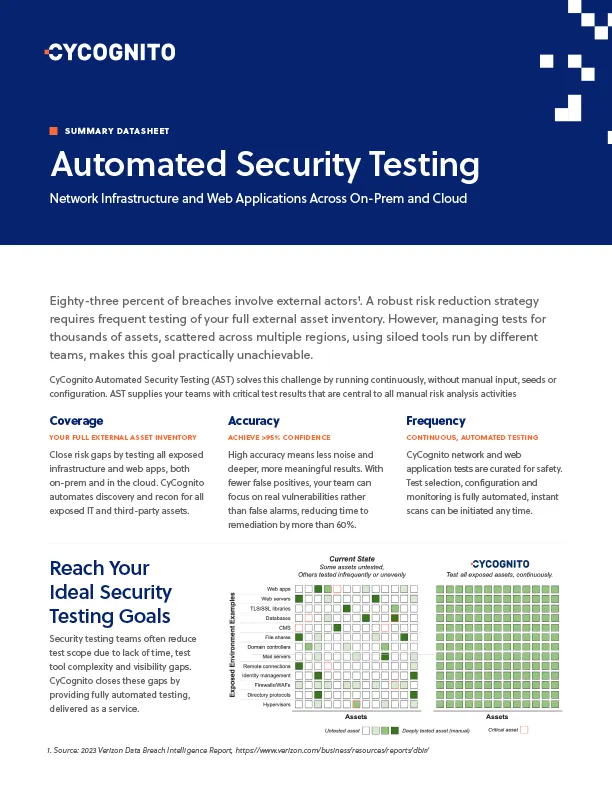
Discovering Shadow Risks
One of CyCognito's customers, a telecommunications company, deployed a defensive security solution, known as a deception system. The system was misconfigured by the vendor's engineer, exposing the company’s entire management system on the open web.
The CyCognito platform discovered the misconfiguration immediately, enabling the company to resolve the security weak spot before attackers could exploit it.