Know the Risk Before You Buy
No longer base your M&A risk decisions on incomplete or incorrect information. Common M&A challenges include accuracy in security posture assessment, timely access to information, and lack of risk exposure inside subsidiaries.
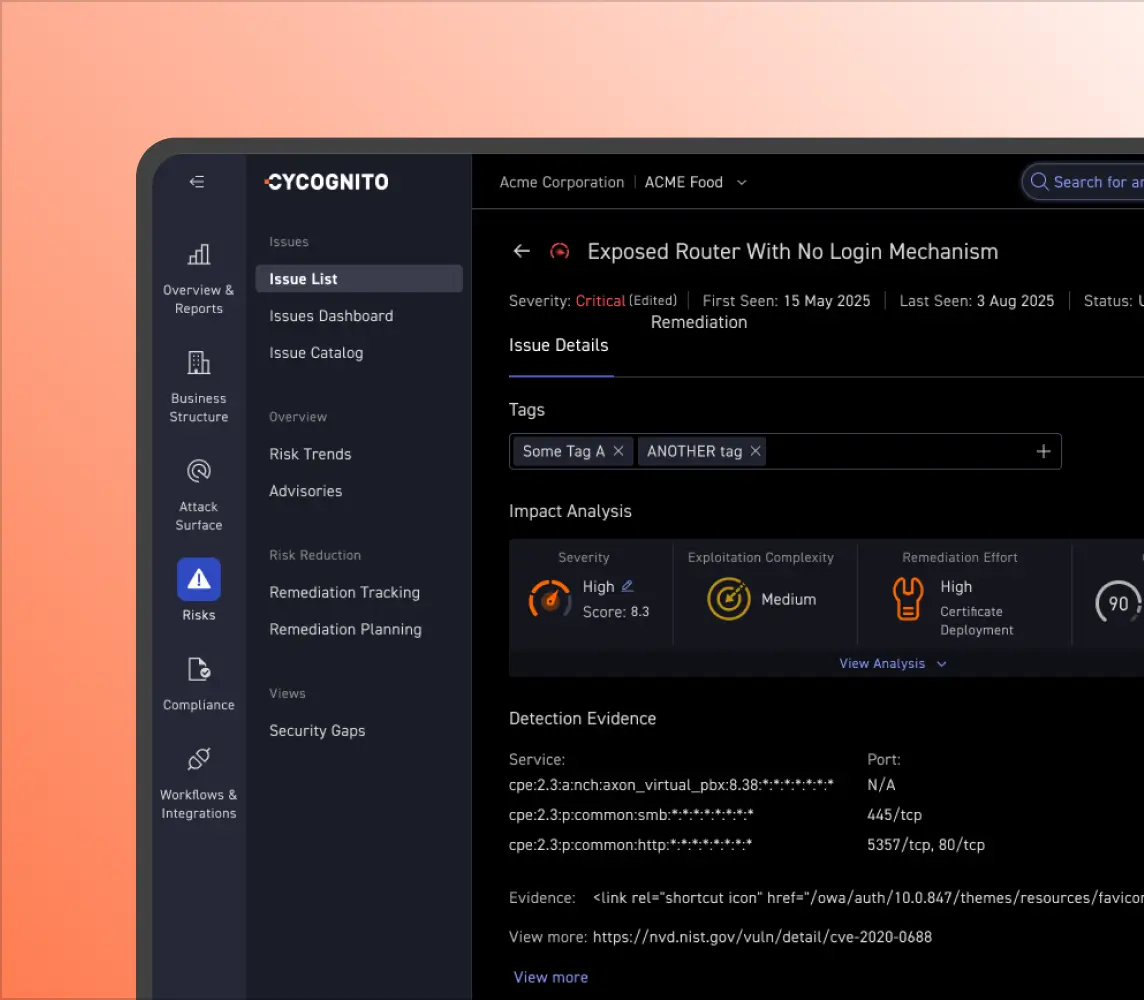
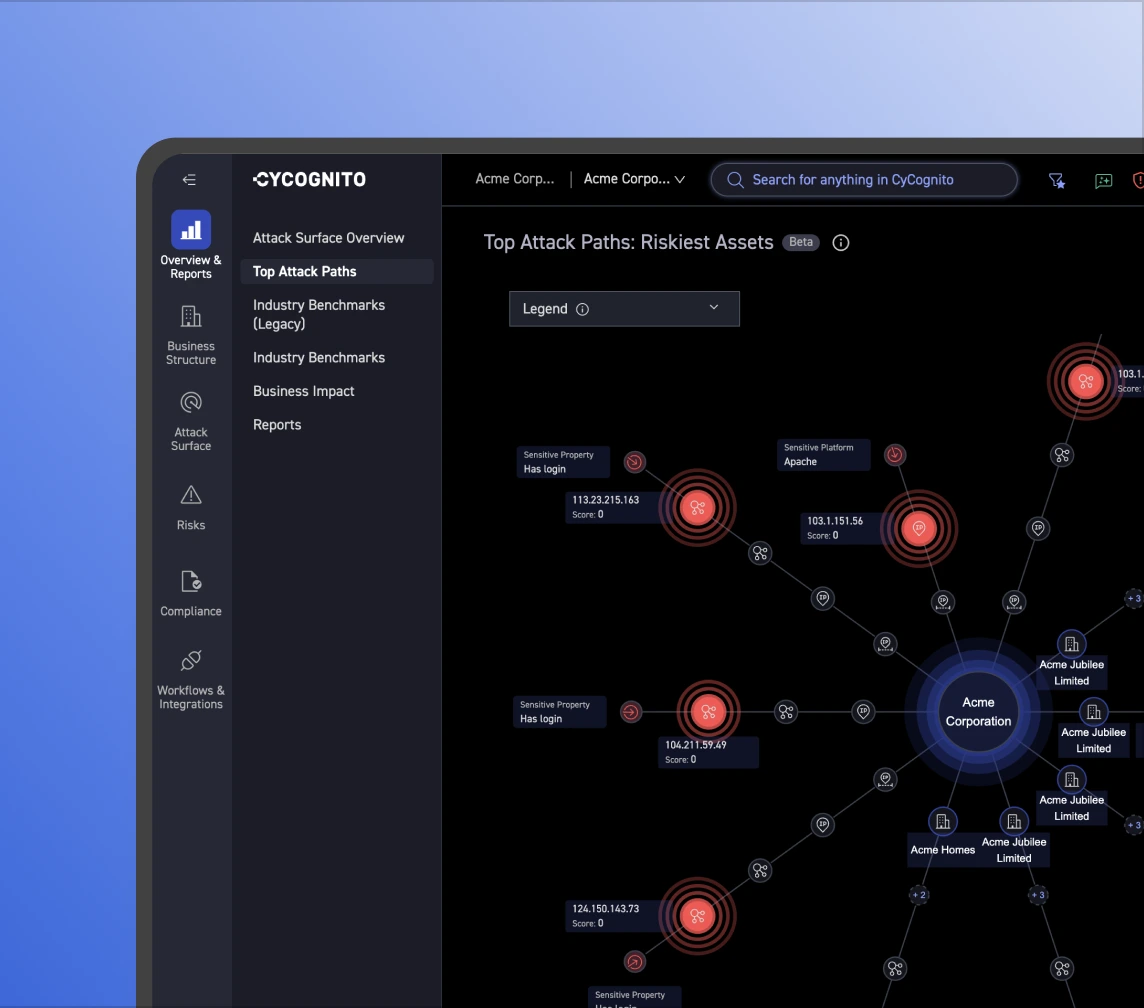
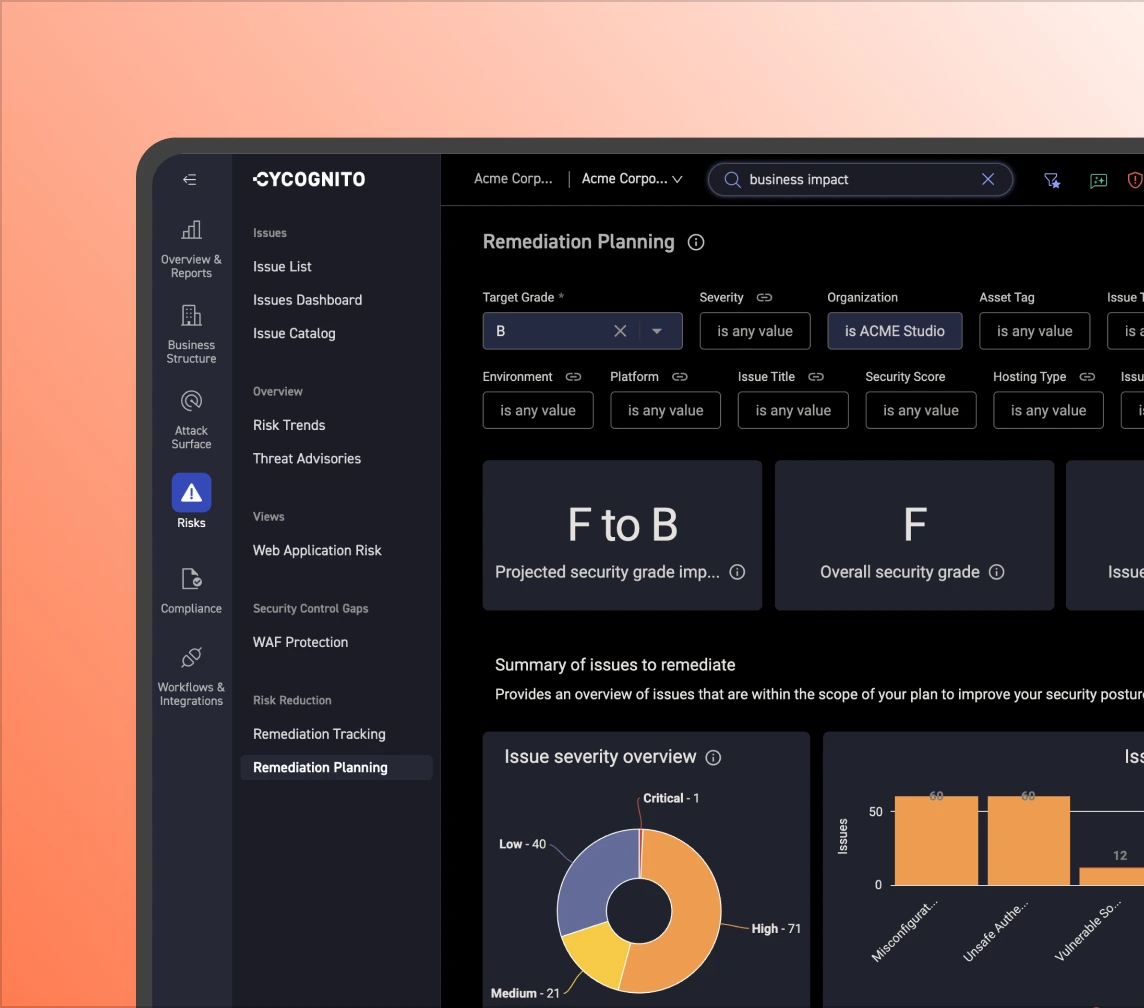
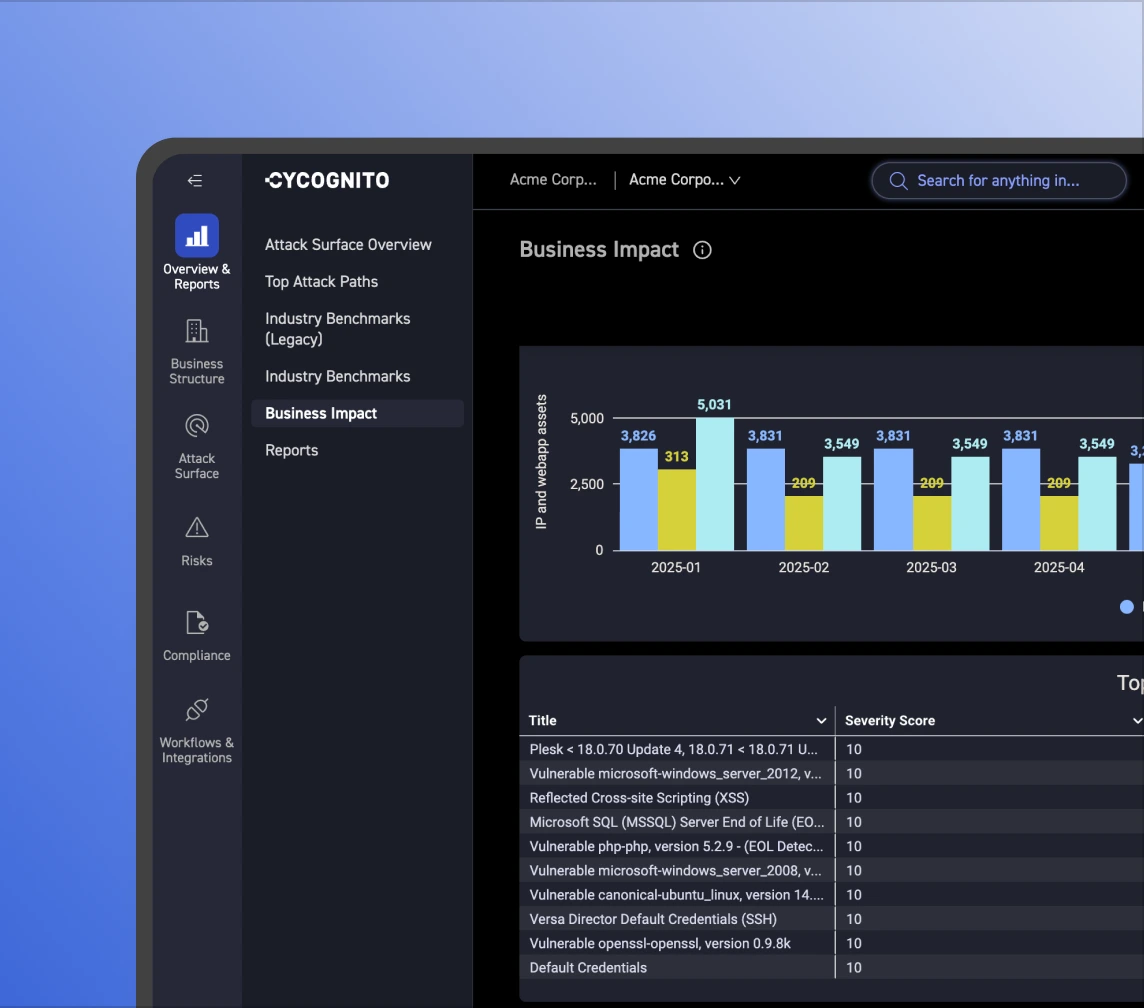
With CyCognito, you have instant access to your M&A candidate's external attack surface and which assets pose the most risk. It identifies the effectiveness of its security controls without requiring any deployment or configuration.