What Are Attack Surface Management Tools?
Attack surface management (ASM) tools are software solutions that map and manage the elements of an IT infrastructure that can be targeted by cyber attacks. These tools provide visibility into an organization’s potential attack vectors, including hardware, software, and network components.
ASM tools continuously monitor for vulnerabilities, misconfigurations, and unauthorized changes, allowing organizations to mitigate potential risks. They help in identifying, assessing, and prioritizing threats. By providing actionable insights into the current state of an organization’s security posture, these tools enable IT teams to enhance defenses and reduce attack surfaces.
This is part of a series of articles about attack surface management.
Key Features of Attack Surface Management Software
ASM tools typically include the following capabilities.
Asset Discovery
Asset discovery involves identifying all assets within an organization’s network. This includes devices, applications, and cloud services that might be overlooked. It creates an accurate inventory, which serves as the foundation for further security measures. Automated tools are often used to conduct continuous scans, ensuring that no asset goes undetected.
This feature is essential because overlooked assets can become vulnerabilities. Identifying assets manually is impractical due to the scale and complexity of modern IT environments. ASM tools simplify this process and significantly reduce the risk of hidden threats by ensuring that every asset is accounted for and monitored.
Inventory and Classification
Inventory and classification involve organizing the discovered assets into categories based on their function, criticality, and risk level. This helps in understanding which assets are most vital to an organization and which ones pose the greatest security risks. By maintaining a detailed and up-to-date inventory, organizations can prioritize their security efforts more effectively.
Classification also involves tagging assets with metadata such as ownership, lifecycle stage, and compliance requirements. This ensures that all assets are adequately protected and that high-risk areas receive the necessary attention. It also simplifies the process of applying security policies and responding to incidents.
Risk Scoring and Security Grading
Risk scoring involves evaluating the potential impact and likelihood of security incidents on identified assets. ASM tools assess vulnerabilities, threat levels, and the criticality of assets to assign a risk score. This score helps organizations understand the relative danger each asset poses to the overall security posture.
By quantifying risk, these tools enable organizations to prioritize their resources and efforts on the most significant threats. Security grading provides an overall assessment of an organization’s security posture. It considers the effectiveness of existing security controls, the presence of vulnerabilities, and compliance with industry standards.
Risk Detection and Prioritization
Risk detection involves identifying potential security issues within an organization’s assets. ASM tools use automated scanning and analysis techniques to uncover vulnerabilities, configuration errors, and signs of malicious activity. The detection process covers known threats and also identifies new, emerging vulnerabilities that could be exploited by attackers.
Prioritization is the next step, where detected risks are ranked based on factors such as the severity of the vulnerability, the value of the affected asset, and the potential impact on the organization. This allows IT teams to focus their efforts on addressing the most critical issues first.
Continuous Monitoring
Continuous security monitoring provides ongoing assessment and vigilance over an organization’s attack surface. Unlike periodic assessments, continuous monitoring offers real-time insights into security posture, allowing for immediate detection and remediation of vulnerabilities and threats.
This capability is essential for maintaining a resilient security posture in the face of evolving cyber threats. Continuous monitoring relies on automated processes and advanced analytics to ensure that security measures are always up-to-date and effective. It also supports compliance with regulatory requirements by providing continuous evidence of security activities.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Notable Attack Surface Management Solutions
CyCognito
The CyCognito platform addresses today’s exposure management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining an asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Application security testing, including dynamic application security testing, or DAST, which uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity.
- Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
Learn more about the Cycognito Attack Surface Management Platform.
Mandiant
Mandiant’s attack surface management solution offers tools to identify and manage external assets and vulnerabilities, providing insights to strengthen an organization’s cybersecurity posture.
Key features of Mandiant attack surface management include:
- Improvement of cyber resiliency: Monitors cloud environments for potential exploit impacts and keeps organizations aware of their exposure to new vulnerabilities.
- Merger and acquisition assessment: Generates dynamic lists of external assets, monitors them continuously, and aids in assessing the security posture of potential acquisitions.
- Identification of unsanctioned resources: Continuously discovers and monitors assets, identifying unmanaged or unknown resources to prevent potential security risks.
- Subsidiary monitoring: Provides centralized visibility and ensures subsidiaries adhere to security policies, maintaining standardization across the organization.
- Digital supply chain monitoring: Maintains an up-to-date inventory of supply chain vendors and assesses their security postures, helping manage third-party risks.
Qualys CAASM
Qualys offers a cybersecurity asset management solution that provides organizations with visibility and control over their digital assets. It focuses on identifying and managing known and unknown assets across the enterprise’s attack surface.
Key features of Qualys ASM Include:
- Asset discovery: Performs continuous discovery of all assets, including those that are Internet-facing. It uses a combination of active and passive scans, open-source intelligence, and API connectors to identify devices, applications, and cloud services.
- External attack surface monitoring: Provides an “outside-in” view of an organization’s IT infrastructure, continuously monitoring for vulnerabilities, misconfigurations, and potential security risks.
- Risk assessment and prioritization: Through the Enterprise TruRisk™ platform, offers a unified view of cyber risks, enabling organizations to assess the security posture of their assets. It prioritizes vulnerabilities and risk factors, such as exposed ports and outdated software, to focus remediation efforts on the most critical threats.
- Integration with other Qualys tools: Integrates with Qualys solutions like Vulnerability Management, Detection, and Response (VMDR), and Web Application Scanning.
- Real-time alerts and reporting: Provides instant alerts and detailed reports, helping security teams stay informed about the latest threats and vulnerabilities affecting their attack surface.
UpGuard
UpGuard is a vendor risk management solution providing visibility into the attack surface and third-party risks. It offers continuous monitoring and automated risk assessments to help organizations manage and mitigate potential vulnerabilities.
Key features of UpGuard include:
- Always-on vendor risk management: Offers clarity into the attack surface and third-party risks, while reducing the team’s workload through automated processes and continuous monitoring.
- Complete visibility of third party risk: Helps identify vendor risks sooner and complete risk assessments twice as fast with automated scanning, evidence analysis, and questionnaire insights.
- Daily scanning for constant vendor monitoring: Provides alerts whenever there are changes in the security posture of a third or fourth party.
- 360° risk assessments: Offers a view of vendor risks from all angles through automated scanning and detailed evidence analysis.
- Single workspace for end-to-end workflows: Simplifies processes with a single platform for identifying, managing, and remediating risks, moving away from outdated spreadsheets and static data.
- Real-time scanning for continuous attack surface monitoring: Protects domains, IPs, and external assets with real-time scans, ensuring a current and complete picture of the attack surface.
Panorays
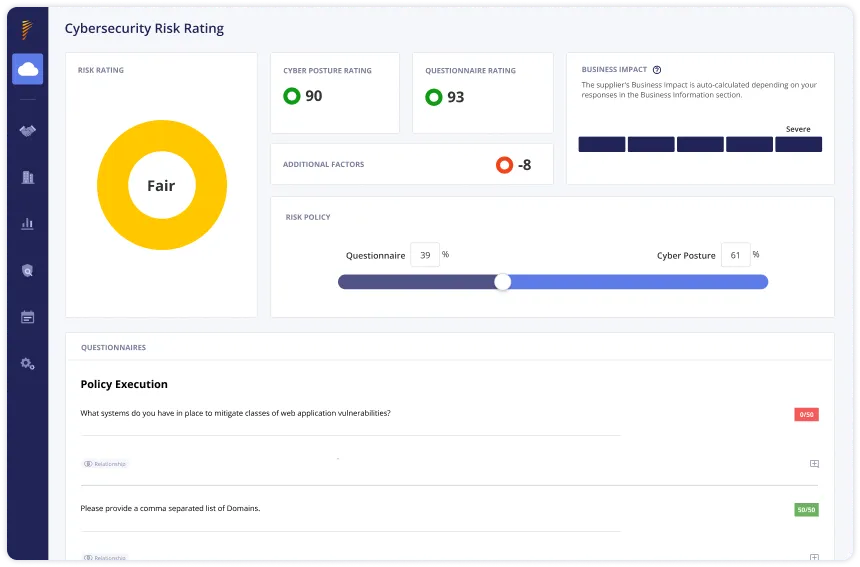
Panorays is a platform for external attack surface management, offering visibility into your organization’s and the supply chain’s cyber risks. It provides real-time, accurate data to help security teams evaluate and mitigate third-party cyber threats.
Key features of Panorays include:
- External attack surface monitoring: Scans thousands of assets across the supply chain, providing real-time, reliable data to evaluate third-party cyber risks.
- External attack surface insights: Reveals shadow IT and discovers fourth and fifth parties in the supply chain, allowing teams to assess the cyber posture of indirect parties. Critical vendors can be selected for continuous monitoring to stay ahead of risks.
- Real-time data on evolving risks: Panorays’ Risk Insights Portal delivers instant alerts on cybersecurity threats, including breaches, vulnerabilities, and zero-day attacks, with detailed analysis of their impact on the supply chain.
- Securing the supply chain: Maps out cyber risks across the digital supply chain and identify which third, fourth, and Nth parties are affected. This visibility helps prevent data breaches, protect business reputation, and ensure business continuity.
- Responding to risks proactively: Helps address critical threats and remediate security gaps before attackers exploit them.
SecurityScorecard
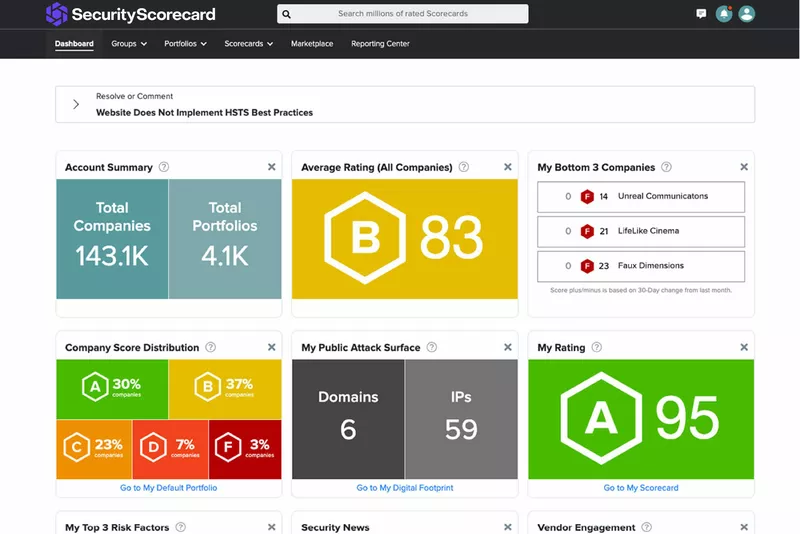
SecurityScorecard is a tool for uncovering external vulnerabilities and remediating cyber risks. It provides continuous monitoring of the attack surface, benchmarking against industry peers, and integrating external cybersecurity capabilities with the security operations center (SOC).
Key features of SecurityScorecard include:
- Proactive external attack surface management: Empowers security and risk teams to stay ahead of cyber threats with a proactive external perspective on cyber risks. This enables them to mitigate threats and demonstrate cybersecurity capabilities to the C-suite and boards.
- Identifying and eliminating cyber risks: Provides visibility into the attack surface to identify and eliminate cybersecurity vulnerabilities and issues that could be exploited by malicious actors.
- Benchmarking against industry peers: Uses security ratings to compare an organization’s cybersecurity performance against industry peers.
- Support for board-level communication: Helps security teams meet regulatory requirements such as SEC, DORA, and other mandates, making it easier for CISOs to communicate with boards and demonstrate cybersecurity preparedness.
- Consolidation into a single platform: The platform bridges external cybersecurity capabilities with the SOC, eliminating the need for multiple disparate tools and providing a unified approach to managing cyber risks.
Axonius
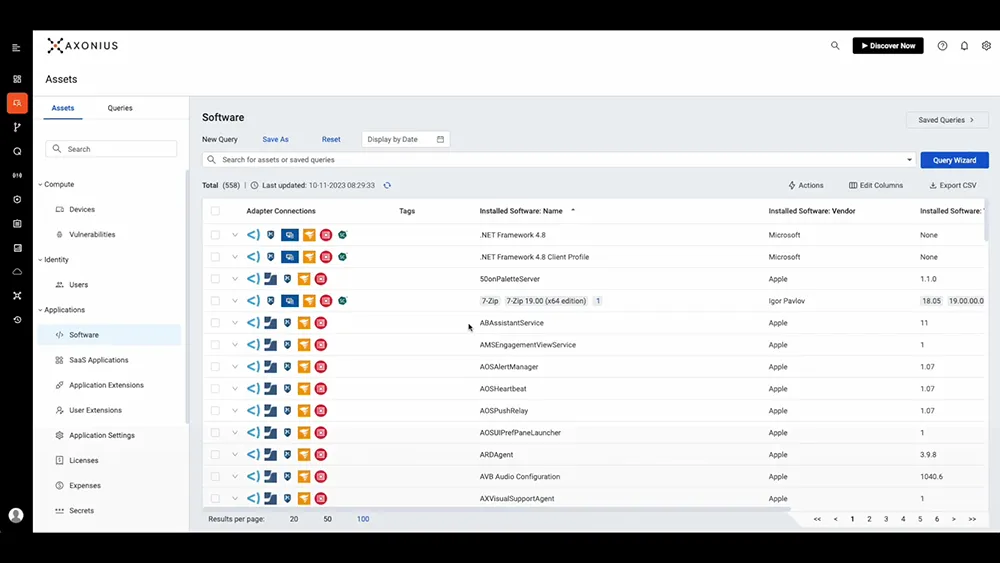
Axonius is a platform for cyber asset attack surface management (CAASM), providing a contextualized view of an organization’s entire asset inventory. Beyond listing assets, Axonius uncovers the security state, relationships, and context of each asset to help address risks.
Key features of Axonius include:
- Secure the attack surface: Axonius connects to all existing tools, providing a holistic view of the attack surface, including internal and Internet-facing assets, observed vulnerabilities, user accounts, and installed software. It also offers context on whether exposed assets are protected with mitigating security controls.
- Identify high risk assets: The platform aggregates and correlates data from the entire infrastructure to automatically identify vulnerable assets and their usage.
- Visualize the attack surface: The interactive Axonius Asset Graph helps users assess the “blast radius” and manage asset-related vulnerabilities.
- Answer any security question: The Axonius Query Wizard addresses questions about assets and helps quickly identify potential threats. Organizations can track compromised devices or users, monitor access tokens, and detect recently announced zero-day threats in their environment.
Tenable.io
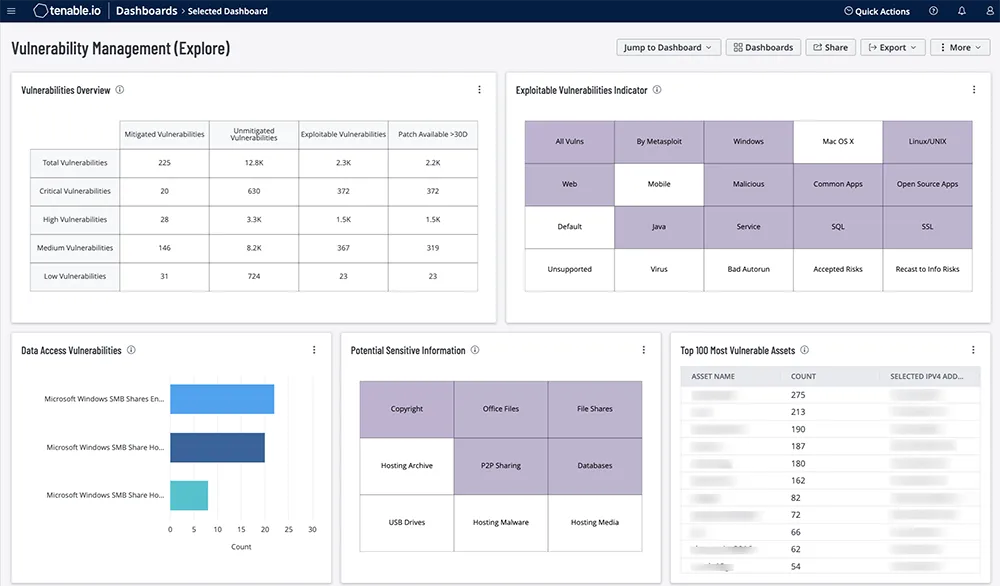
Tenable.io offers attack surface management capabilities, providing visibility into all Internet-connected assets, services, and applications. This enables organizations to understand their full digital footprint and assess and manage risks.
Key features of Tenable.io include:
- Visibility into the external attack surface: Continuously maps the entire Internet to discover connections to Internet-facing assets. This helps organizations assess the security posture of their entire external attack surface.
- Discovery: Provides an attack surface map of over 5 billion assets, discovering domains related to assets in the inventory. Offers notifications on changes in the attack surface for continuous monitoring.
- Business context: Utilize over 200 fields of metadata to gain full business context of previously unknown internet-connected assets. Filters, tags, and datatypes streamline asset management and provide a clear understanding of your external footprint.
- Cyber risk assessment: External attack surface assets and exposure data can be integrated into Tenable One, Tenable Vulnerability Management, and Tenable Security Center. Scans can uncover blind spots and ensure coverage across the attack surface.
Hunto.ai
Hunto.ai is an attack surface management tool designed to give organizations the perspective of an attacker, enabling them to anticipate and mitigate potential cyber threats proactively. By providing visibility and optimized resource allocation, Hunto.ai helps organizations manage their expanding digital footprints.
Key features of Hunto AI include:
- Stay ahead of attackers: Helps understand the attack surface from an attacker’s perspective to anticipate potential threats and mitigate them proactively.
- Optimized resource allocation: Helps prioritize vulnerabilities to allocate resources more effectively, addressing the most critical threats first. This ensures that the most pressing issues are dealt with promptly, reducing overall cyber risk.
- Enhanced visibility: Provides a clear view of all external-facing assets, ensuring no potential vulnerability goes unnoticed.
- Continuous external IT asset discovery: Automatically identifies and catalogs all external digital assets, including web applications, cloud services, IoT devices, and overlooked or forgotten assets. This ensures a complete view of the organization’s digital exposure.
- Brand reputation: Protects against threats that can negatively impact the reputation or perceived value of a brand, such as online phishing scams, social media threats, and rogue mobile applications.
Bitsight

Bitsight provides external attack surface management (EASM) capabilities, offering visibility into the expanding attack surface. By tracking vulnerabilities, prioritizing critical issues, and implementing long-term solutions, Bitsight helps organizations mitigate cyber risks.
Key features of Bitsight include:
- Instant visibility into the external attack surface: Bitsight maps the external attack surface, tracking over 10,000 common vulnerabilities and exposures (CVEs) daily.
- Digital asset monitoring: Monitors numerous digital assets, including operational technology (OT) and cloud infrastructure, at any given moment.
- Proactively manage exposure: Reduces the risk of cyber attacks and maintains a strong security posture by fixing immediate exposure issues and addressing their root causes.
- Efficient asset discovery and risk analysis: Automatically discovers assets, analyzes risks, and sends remediation suggestions. This efficiency helps prevent breaches and service disruptions.
- Rapid response to new vulnerabilities: Allows teams to act on exposure issues before attackers do. With continuous monitoring and instant alerts, teams can respond quickly to new vulnerabilities and protect the organization from emerging threats.
Tips from the Expert

Dima Potekhin, CTO and Co-Founder of CyCognito, is an expert in mass-scale data analysis and security. He is an autodidact who has been coding since the age of nine and holds four patents that include processes for large content delivery networks (CDNs) and internet-scale infrastructure.
In my experience, here are tips that can help you better leverage Attack Surface Management (ASM) tools:
- Integrate with DevSecOps pipelines: ASM tools should be part of the DevSecOps process, ensuring security checks and asset discovery are integrated into CI/CD pipelines. This helps in identifying and addressing vulnerabilities early in the software development lifecycle.
- Focus on user behavior analytics: Combine ASM with User and Entity Behavior Analytics (UEBA) to detect anomalies not just in systems but also in user activities. This can help uncover insider threats or compromised credentials.
- Implement deception technology: Integrate deception tools within your ASM strategy to lure attackers towards decoy systems. This provides early warning and diverts malicious activities away from critical assets.
- Establish a bug bounty program: Complement your ASM efforts with a bug bounty program to encourage external security researchers to report vulnerabilities. This can uncover issues that automated tools might miss.
- Ensure visibility across hybrid environments: Ensure your ASM tools provide comprehensive visibility across on-premises, cloud, and hybrid environments. This includes monitoring for shadow IT and rogue assets that may not be officially sanctioned but pose significant risks.
Conclusion
Attack surface management tools are essential for organizations to gain comprehensive visibility into their IT infrastructure and identify potential vulnerabilities. By automating asset discovery, classification, and continuous monitoring, these tools help prioritize risks and streamline remediation efforts. ASM solutions are crucial for maintaining a strong security posture in the face of evolving cyber threats, enabling organizations to protect sensitive data and maintain business continuity.














