What Are IT Asset Discovery Tools?
IT asset discovery tools are specialized software solutions designed to automatically identify and catalog all the digital assets within an organization’s network. These tools play a crucial role in managing and securing an organization’s IT environment. By scanning networks, servers, workstations, and other devices, IT asset discovery tools collect detailed information about each asset, such as its type, configuration, installed software, and usage data.
CThe primary objective of these tools is to provide IT administrators with a comprehensive view of the organization’s IT assets, enabling them to make informed decisions about asset management, security, and compliance. This visibility is essential for maintaining an accurate inventory, identifying unauthorized devices, ensuring software licenses are up to date, and detecting potential vulnerabilities within the network.
This is part of a series of articles about attack surface management.
Key Capabilities of IT Asset Discovery Tools
Network Scanning and Reconnaissance
Network scanning is a critical component of IT asset discovery tools. It allows these tools to identify all connected devices within a network, categorizing them based on their type, such as servers, computers, or printers. This enables network management and enhances security by pinpointing unauthorized devices.
Furthermore, advanced network scanning features can detect the operating systems and open ports on these devices. This aids IT professionals in identifying vulnerabilities and outdated systems that need updates or patches, improving the organization’s overall security posture.
In the context of security testing, the primary objective of network scanning is reconnaissance. It enables an initial assessment and ongoing evaluations of the network to identify all connected devices and services. This allows organizations to discover not just authorized but also unauthorized devices and services that could represent potential security threats.
Software License Management
Software license management ensures that all software on the network is appropriately licensed, helping organizations avoid legal issues and penalties associated with unlicensed software use. This also supports cost management by identifying unused or underutilized licenses that can be reassigned or discontinued.
Additionally, it provides insights into software compliance and usage patterns. Organizations can optimize their software inventory, ensuring they invest only in necessary licenses. This not only helps in maintaining legal compliance but also significantly reduces software costs.
Inventory Management
Inventory management features within IT asset discovery tools keep track of all hardware and software assets in an organization. This facilitates a clear understanding of what assets the organization owns, where they are located, and how they are being used. Such insights are essential for strategic planning and budgeting.
Effective inventory management also aids in lifecycle management by tracking the age and performance of assets. Organizations can plan for timely upgrades or replacements, ensuring the IT infrastructure remains up-to-date and performs optimally.
Security Monitoring
Security monitoring features in IT asset discovery tools allow for continuous surveillance of the network for suspicious activities or potential security threats. They provide real-time alerts about vulnerabilities or unauthorized access attempts, enabling quick response to potential security incidents.
Moreover, security monitoring helps in compliance with various regulatory standards by ensuring that security protocols are in place and functioning correctly. This is essential for maintaining the integrity and confidentiality of organizational data and ensuring resilience against cyber threats.
Configuration Management Database (CMDB)
A Configuration Management Database (CMDB), often used as a standalone platform, can also be integrated with asset discovery tools. A serves as a centralized repository that stores information related to all the significant components of an information system. CMDBs are used to track the assets of an organization and the relationships between these assets. Asset discovery tools are commonly used to update a CMDB to reflect the current state of the network.
By managing this data, CMDB helps IT teams understand the organization’s IT environment in terms of the interrelations and dependencies among assets, such as hardware, software, network infrastructure, and business services. This is crucial for effective change management, incident management, and risk assessment.
Related content: Read our guide to attack surface discovery.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

8 Notable IT Asset Discovery Tools
1. CyCognito
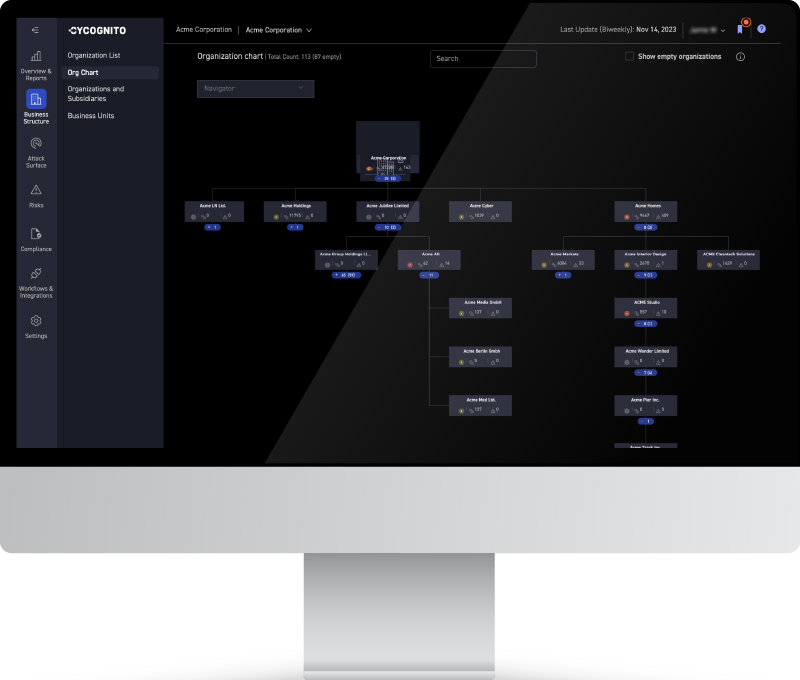
Source: CyCognito
CyCognito introduces a dynamic approach to asset inventory management with a focus on security, employing natural language processing (NLP) for organizational reconnaissance and advanced analysis of open-source intelligence (OSINT) to create a comprehensive asset inventory. This system provides a live, continuously updated view of an organization’s external assets, displayed in a graph data model that illustrates the interconnections between assets.
Key features of CyCognito include:
- Automatic discovery process: Eliminates the need for manual input or configuration. The platform employs attacker reconnaissance tools and methodologies to proactively identify and classify exposed external assets.
- Support for hybrid environments: Covers not only company-owned resources but also those in traditional data centers, SaaS, IaaS, as well as assets linked with partners, subsidiaries, and interconnected companies.
- Broad coverage: Discovers assets beyond the typically known IT environment, often covering over 90% of the IT ecosystem exposed to potential cyber threats.
- Automatic mapping of business structure: Provides visibility into business-relevant applications and their criticality, a crucial feature in a landscape where attack surfaces are constantly evolving.
- Advanced automation: Leverages machine learning, NLP, and graph data models to reveal the full spectrum of organizational relationships, effectively adjusting to structural changes and maintaining an accurate, real-time inventory.
Learn more about asset discovery in the CyCognito attack surface management platform
2. NinjaOne
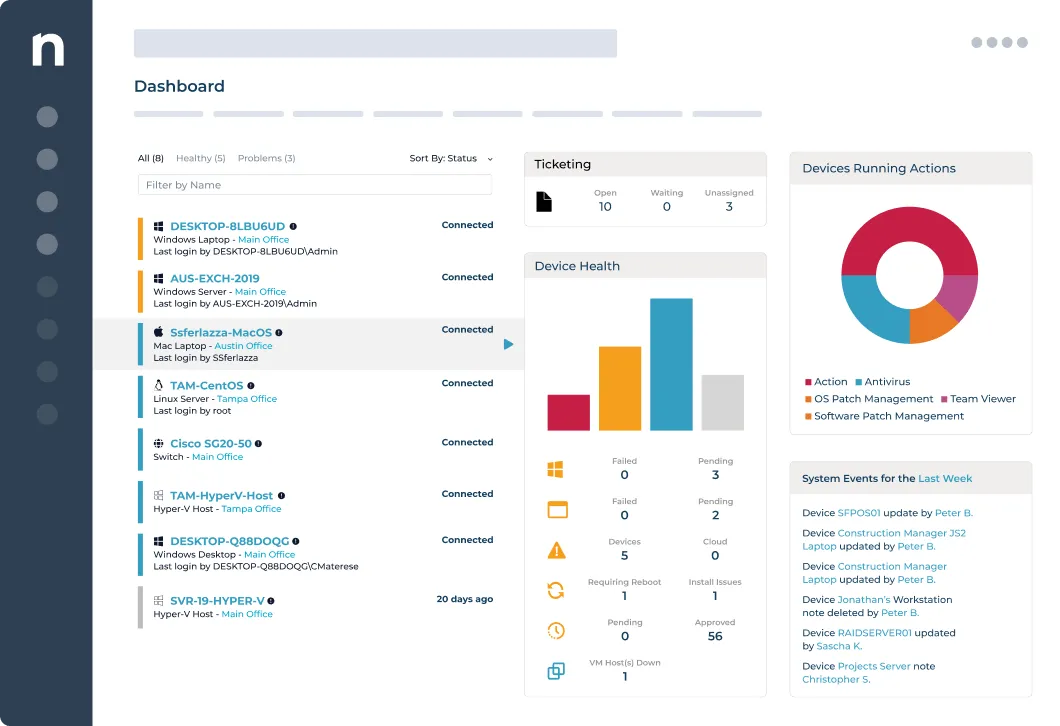
Source: NinjaOne
NinjaOne is an IT asset management solution that automates the discovery and management of IT assets. It provides visibility and control over all endpoints, including servers, workstations, and laptops (supporting Windows, MacOS, and Linux), as well as VMWare and Hyper-V hosts, guests, and SNMP devices.
Key features of NinjaOne include:
- Automated IT asset discovery and management: Automates the process of identifying and managing all endpoints, ensuring comprehensive visibility and control.
- Integration with Microsoft Active Directory: Enables scheduled scans for unmanaged devices and seamless deployment of management agents.
- Supports security and compliance: Ensures all devices are fully managed, reducing IT asset risk and enforcing asset policies to limit exposure.
- Cost reduction: Aids in minimizing the expenses related to supporting and enabling endpoints through automation and visibility.
- Improved workflow efficiency: Integrates IT asset data directly within management and support workflows, streamlining operations and enhancing team productivity.
3. SolarWinds
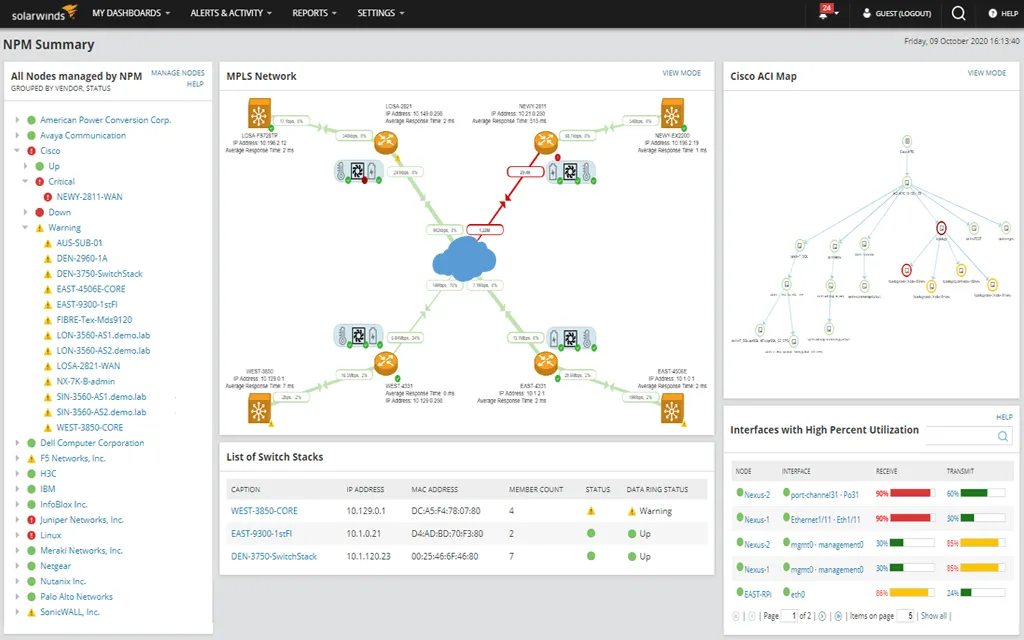
Source: SolarWinds
SolarWinds is an IT asset management solution that aligns with services and processes critical to IT. It helps manage and track hardware, software, licenses, and even non-IT assets throughout their lifecycle. With a focus on automation, SolarWinds simplifies the management of various assets, providing a centralized platform for IT management and visibility.
Key features of SolarWinds include:
- Fully integrated IT asset management: Manages and tracks hardware, software, and licenses throughout their lifecycle in one interface.
- Automated tracking and tagging: Automates tracking of hardware properties, software titles, and user and location history across Windows, iOS, and Chrome OS devices.
- Contract service level management: Simplifies vendor data, warranties, lease terms, and agreement management in a single location.
- Enhanced asset visibility: Automatically captures each asset’s incident history, expediting problem resolution within service desk tickets.
- Real-time IT asset management: Offers a full understanding of how incidents, problems, changes, and releases impact assets through an integrated service desk.
4. Qualys
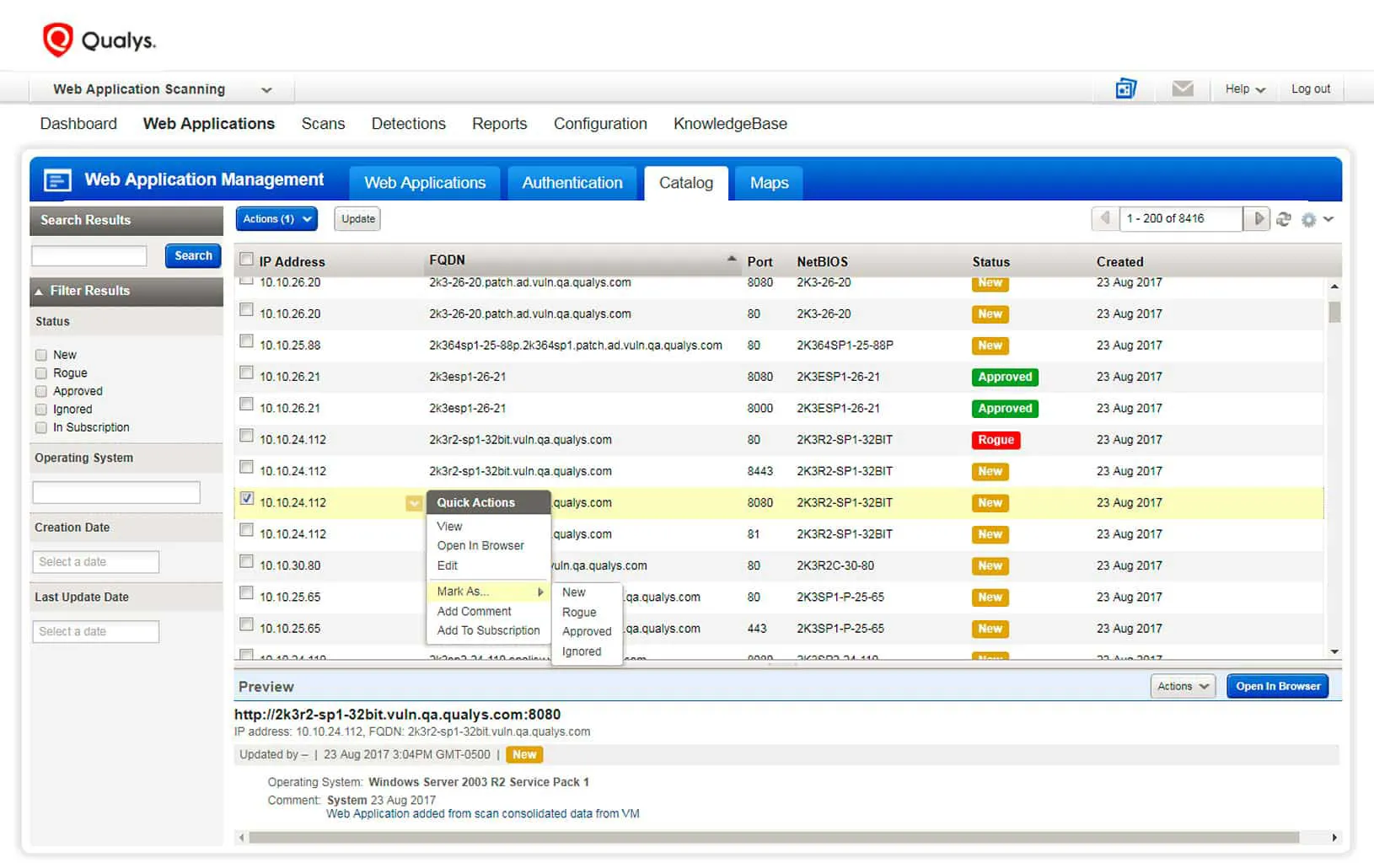
Source: Qualys
Qualys Global AssetView is a cloud-based IT asset management solution that provides visibility into an organization’s hybrid IT environment. It promises to make every IT asset visible, enhancing security and operational efficiency. Qualys is affordably priced, with unlimited assets across all pricing plans.
Key features of Qualys Global AssetView include:
- Unlimited, continuous discovery: Automatically discovers all known and unknown assets, including on-premises devices, mobile, endpoints, clouds, containers, operational technology (OT), and internet of things (IoT).
- Normalization and categorization: Standardizes raw asset data into organized, consistent categories, handling variations in product and vendor names.
- Detailed asset information: Provides comprehensive data on each asset, including hardware details, running services, installed software, and advanced metadata like lifecycles and license types.
- Custom tagging: Offers the flexibility to label and organize assets with custom tags, enhancing asset management and identification.
5. Intruder
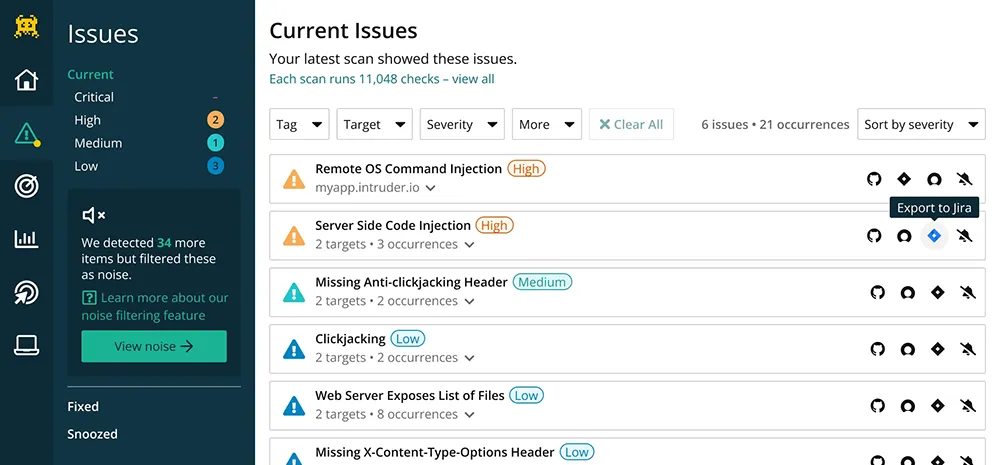
Source: Intruder
Intruder is a platform designed to simplify the process of securing digital assets. It provides a user-friendly interface for asset visibility, with continuous monitoring and automated scanning to quickly identify vulnerabilities. Intruder aims to provide a clear view of the attack surface, prioritizing issues to ensure they are addressed efficiently.
Key features of Intruder include:
- Easy setup and scanning: Set up in minutes with Intruder’s online vulnerability scanner for infrastructure, web apps, or APIs.
- Continuous vulnerability scanning: Automatically initiates scans upon detecting changes, exposed services, or new threats.
- Eases compliance: Generates concise, actionable results and audit-ready reports to effortlessly demonstrate security compliance, supporting compliance standards like SOC 2 Type 2.
- Vulnerability management: Offers regular vulnerability scans and proactive threat scans in one platform, integrating into CI/CD pipelines for DevOps environments.
- Supports cloud environments: Monitors live cloud services and automates vulnerability scans for any changes.
6. Lansweeper
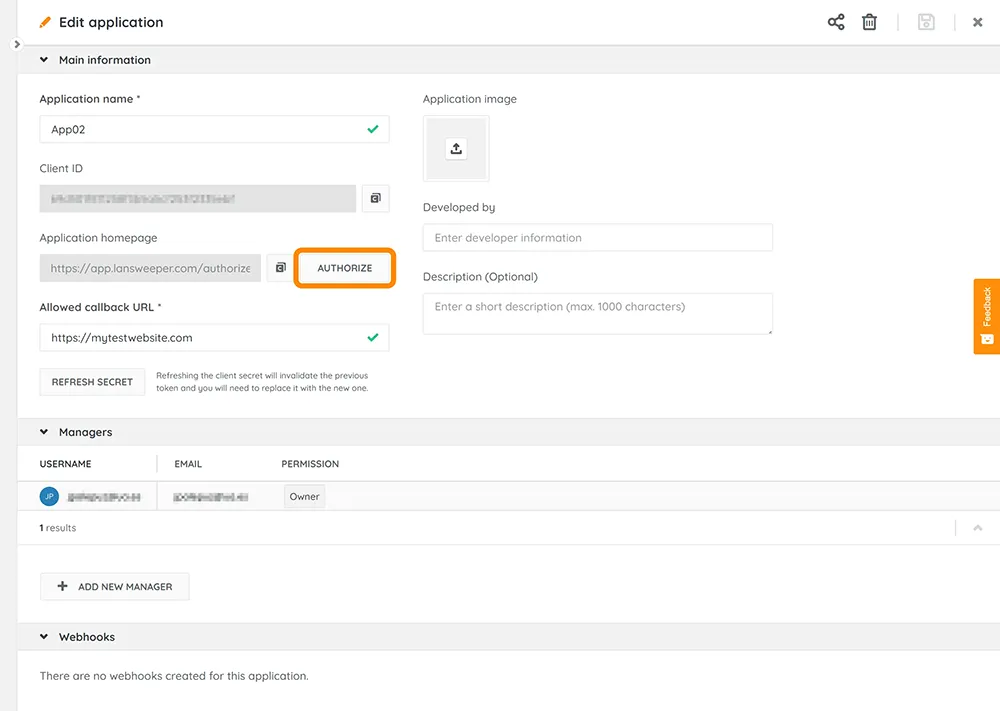
Source: Lansweeper
Lansweeper is an IT asset management solution that aims to provide complete visibility into an IT estate. It emphasizes the importance of a single, accurate source of truth for managing the lifecycle of IT hardware, software, and networking devices, ensuring they are implemented, supported, upgraded, and discarded as needed.
Key features of Lansweeper include:
- Automated asset management: Streamlines management of IT assets, offering a comprehensive overview of hardware, software, and networking devices.
- Single source of truth: Creates an always-accurate inventory, centralizing information and providing a unified view for IT teams to manage assets efficiently.
- Optimization of IT budgets: Helps in understanding the total cost of ownership (TCO) of IT assets, optimizing the use of resources, and reducing licensing and support costs.
- Supports modern IT Asset Management (ITAM): Elevates ITAM from a niche specialty to a core function, supporting all common IT use cases.
7. Asset Panda
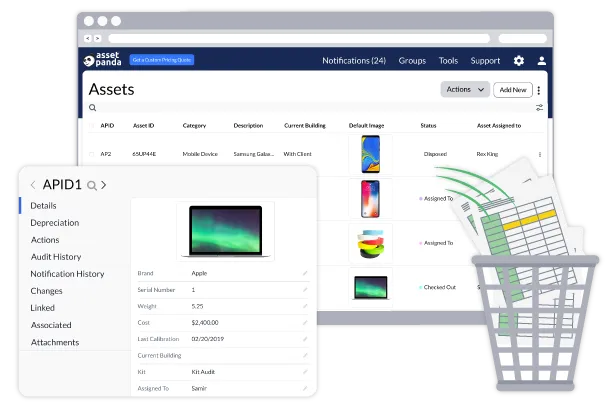
Source: Asset Panda
Asset Panda is a cloud-based asset management and tracking platform. With a focus on adaptability, Asset Panda caters to a wide range of industries and asset types, from IT and construction to education and retail. This platform supports both digital and physical assets, including contracts, software licenses, laptops, and vehicle fleets. It allows businesses to track everything from computers to contracts without altering their operational workflows.
Key features of Asset Panda include:
- Flexible platform: Tailored to meet the unique needs of businesses, tracking a wide variety of asset types and use cases.
- Enhanced asset tracking: Improves business performance by maintaining equipment in working order and preventing losses due to damage or theft.
- Comprehensive asset information: Consolidates full action histories, warranty information, user manuals, and photos in one place, offering an alternative to cluttered spreadsheets.
- Unlimited user accounts: Facilitates organization-wide adoption, from executives viewing reports to front-line workers managing assets on the move.
8. SysAid
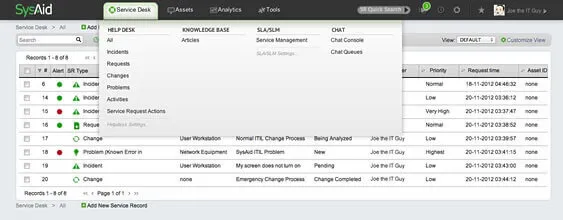
Source: SysAid
SysAid provides an IT asset management solution integrated directly within a service desk platform. This integration enhances the efficiency and effectiveness of asset management and IT service management (ITSM) processes, allowing for seamless handling of incidents, problems, and changes.
Key features of SysAid include:
- Comprehensive inventory management: SysAid’s advanced discovery solutions automatically detect and catalog all IT assets within the organization.
- Real-time monitoring: SysAid provides custom alerts for various changes in the network, such as CPU usage, memory usage, and network equipment status.
- Configuration Management Database (CMDB): SysAid automatically imports asset data into a CMDB, offering a centralized repository for tracking the interrelations and dependencies among IT assets.
- Remote control: The platform allows service desk agents to remotely resolve end-user issues, enhancing responsiveness and user satisfaction.
- Software management: SysAid facilitates efficient management of installed software, including automation of renewal reminders.
- Network discovery: The built-in network discovery capabilities continuously scan the IT environment, updating asset information automatically.
- Patch management: SysAid integrates patch management into its ITAM solution, allowing for the deployment of patches according to customized policies.
- Service desk integration: By including relevant asset information in service desk tickets, SysAid streamlines issue resolution.
Tips from the Expert

Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you better leverage IT asset discovery tools for enhanced attack surface management:
- Integrate with Threat Intelligence Platforms: Complement your asset discovery tools by integrating them with threat intelligence feeds. This allows for real-time updates on emerging threats, enabling proactive identification and protection of vulnerable assets before they are targeted.
- Prioritize Shadow IT Discovery: Focus on uncovering and managing shadow IT assets—unauthorized devices, applications, or services used within the organization. These are often the weakest links in your security posture, so identifying and mitigating risks associated with them is crucial.
- Implement Continuous, Adaptive Discovery: Ensure that your asset discovery tools support continuous monitoring rather than periodic scans. Adaptive discovery that responds to network changes in real-time can help you detect new or modified assets more quickly, reducing potential exposure.
- Automate Response Actions: Integrate your asset discovery tools with automated response systems. For example, automatically isolate a newly discovered, suspicious device from the network until it is properly assessed and secured.
- Customize Alert Thresholds Based on Asset Criticality: Tailor alert thresholds for different assets based on their criticality to your business operations. High-priority assets should trigger alerts more quickly for even minor deviations, ensuring rapid response.
Conclusion
IT asset discovery tools are critical for organizations seeking to maintain a visible and secure IT environment. These tools automate the tedious process of cataloging and managing assets, enabling IT professionals to focus on strategic tasks such as cybersecurity, compliance, and operational efficiency.
By providing a comprehensive view of all assets, their configurations, and usage, these tools play a key role in optimizing IT asset management and safeguarding the network from potential threats. Their adaptability across various IT environments, coupled with features like continuous monitoring and vulnerability assessment, makes them a crucial component in the toolbox of modern IT management.
Learn more about asset discovery in the CyCognito attack surface management platform.














