What Is Palo Alto Cortex Xpanse?
Palo Alto Cortex Xpanse is an active attack surface management (ASM) solution. It helps organizations discover, understand, and mitigate risks across their entire digital ecosystem. By continuously scanning the internet, it identifies and addresses vulnerabilities in connected systems and exposed services before attackers can exploit them. This ensures organizations can respond swiftly to risks from unknown or unmanagedassets.
Cortex Xpanse automates the discovery and remediation of security blind spots, scanning over 500 billion ports daily and indexing all IPv4 addresses multiple times a day. This allows it to provide comprehensive visibility into internet-exposed assets.
Key Features of Cortex Xpanse
Cortex Xpanse uses discovery, learning, and response mechanisms to help organizations identify and mitigate risks. Its key features include:
- Active discovery: Continuously scans the global internet to identify and index unknown risks in connected systems and exposed services. This feature spans on-premises and cloud environments.
- Automated risk mitigation: Built-in playbooks automate the remediation of risks, eliminating the need for manual ticket handling.
- Learning through machine learning: Utilizes supervised machine learning to map the organization’s attack surface, dynamically attributing internet assets and prioritizing critical issues without requiring agents or instrumentation.
- Zero-day vulnerability management: Assesses and mitigates exposure to the latest common vulnerabilities and exposures (CVEs).
- Shadow IT management: Identifies and mitigates risks associated with unsanctioned cloud resources and rogue IT assets.
- Security operations center (SOC) efficiency: Integrates with existing SOC workflows and tools, providing a consolidated platform to manage external attack surfaces.
- Ransomware defense: Automatically addresses vulnerabilities that could be exploited for ransomware attacks.
- Mergers and acquisitions security posture: Evaluates security risks associated with mergers and acquisitions, providing valuable insights during due diligence processes.
Cortex Xpanse Pricing
Pricing for Cortex Xpanse is not publicly disclosed and varies based on factors such as the number of assets monitored and specific organizational requirements. According to eSecurityPlanet, a web-based subscription covering up to 999 assets with basic customer support is priced at $95,000 peryear.
Cortex Xpanse Limitations
Cortex Xpanse has some limitations that organizations should consider. These include challenges related to integration, usability, and functionality. These limitations were reported by users on Gartner Peer Insights:
- Integration challenges: While Cortex Xpanse integrates with security information and event management (SIEM) tools, it primarily relies on syslog messages rather than providing native connectors for popular SIEM platforms. This approach can complicate integration efforts and may require additional configuration. Slack integration has been noted as intrusive for someusers.
- Accuracy and false positives: Asset classification and contextual information are not always precise, leading to false positives that require manual verification.
- Complex interface: Some users have noted there is room for improvement to enhance userexperience.
- Data overload: The extensive amount of data provided by Cortex Xpanse can overwhelm users, particularly those without dedicated resources to analyze and act on the findings.
- Reporting limitations: The tool’s reporting functionality, while valuable, lacks depth in some areas. More flexible reporting options are needed, including the ability to adjust reports for specific needs.
- Limited cloud capabilities: Currently, Cortex Xpanse’s cloud capabilities are tied to Prisma Cloud, and it does not support other cloud platforms.
- Scope for advanced metrics: Users have expressed a desire for financial risk scoring in addition to the standard risk scorecard. This addition would provide actionable insights for decision-makers assessing security risks in a business context.
Related content: Read our guide to attack surface analysis.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

Notable Cortex Xpanse Alternatives
In light of the above limitations, organizations should consider Cortex XPanse alternatives. Here are a few popular alternatives.
1. CyCognito
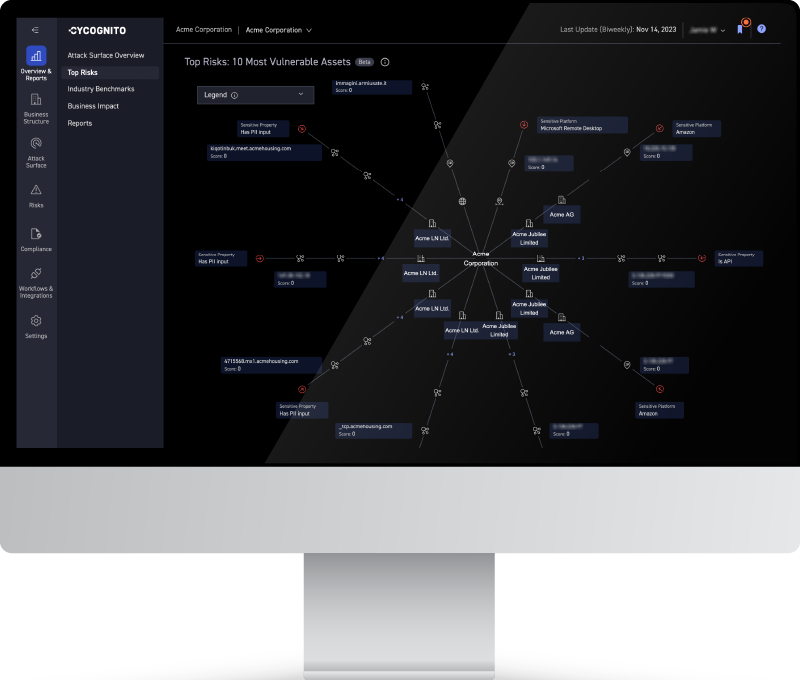
Source: CyCognito
The CyCognito platform addresses today’s exposure management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining an asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Application security testing, including dynamic application security testing, or DAST, which uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity.
- Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
Learn more about the Cycognito Attack Surface Management Platform.
2. Microsoft Defender EASM
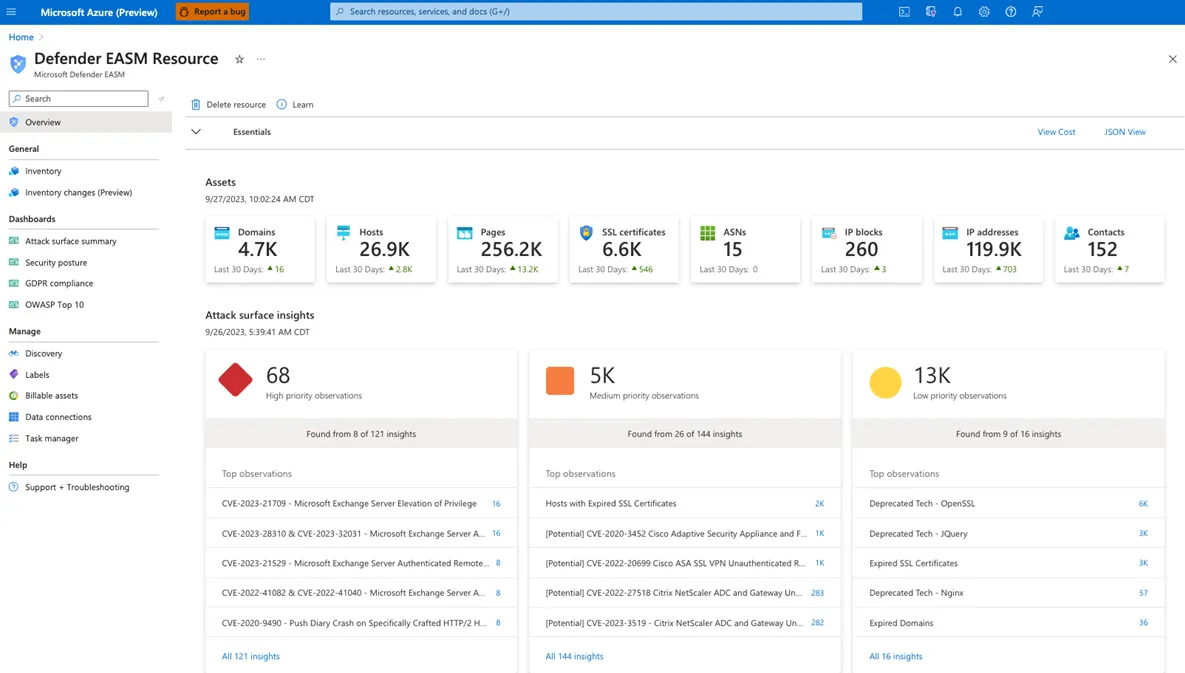
Source: Microsoft
Microsoft Defender EASM offers tools for managing and mitigating risks associated with external attack surfaces. It helps organizations maintain continuous visibility into unmanaged and shadow IT resources in dynamic, hybrid environments. Its AI-driven capabilities enable cloud security teams to discover, classify, and prioritize vulnerabilities.
Key features include:
- Real-time inventory monitoring: Continuously tracks and categorizes internet-facing assets, ensuring that newly added or modified resources are included in the attack surface.
- Multicloud visibility: Provides dynamic inventory and analysis across various cloud environments, including SaaS, IaaS, and hybrid setups.
- Shadow IT discovery: Identifies unmanaged resources resulting from business growth or employee-led initiatives.
- Exposure detection and prioritization: Uses AI to uncover and prioritize vulnerabilities and misconfigurations in exposed resources for effective risk mitigation.
- Generative AI insights: Delivers actionable recommendations on risky assets and external risks.
- Unified security view: Integrates insights across Microsoft’s security ecosystem to provide a consolidated overview of the organization’s risk posture.
3. CrowdStrike Falcon Surface Exposure Management
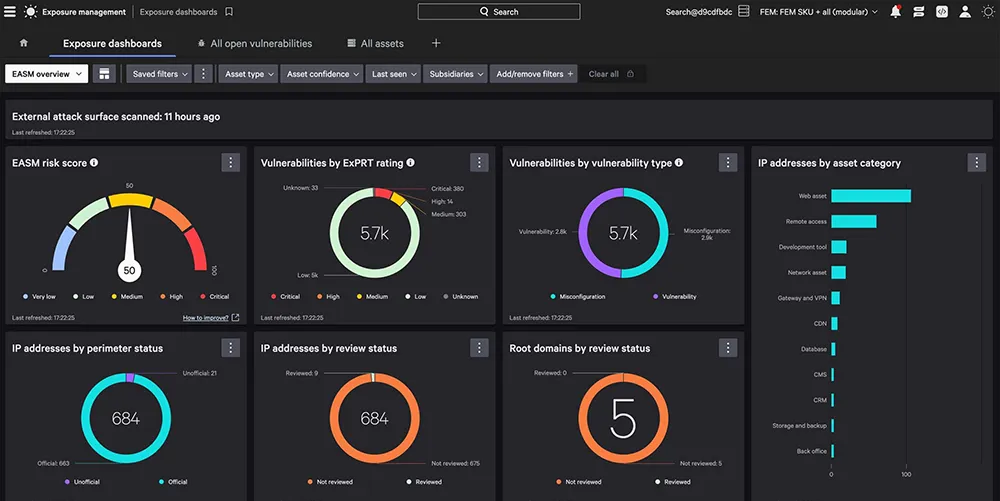
Source: CrowdStrike
CrowdStrike Falcon Surface provides external attack surface management (EASM) capabilities, helping organizations to discover, assess, and secure their internet-facing assets. By leveraging adversary-driven insights, it allows teams to identify and mitigate risks from exposed and unmanaged resources.
Key features include:
- Continuous internet mapping: Uses proprietary mapping technology to index the internet, automatically identifying known and unknown assets while monitoring security risks across environments.
- Shadow IT and hidden risk discovery: Detects unmanaged and exposed resources, including shadow IT, providing visibility to reduce breach risks.
- 24/7 attack surface monitoring: Continuously scans the internet to deliver insights into threats and vulnerabilities as they arise.
- AI-driven risk prioritization: Employs ExPRT.AI to assess vulnerabilities, offering guided steps to address exposures and reduce overall risk.
- Adversary-driven intelligence: Provides insights from an attacker’s perspective, enabling organizations to anticipate threats and act to secure their digital estate.
4. Mandiant Attack Surface Management
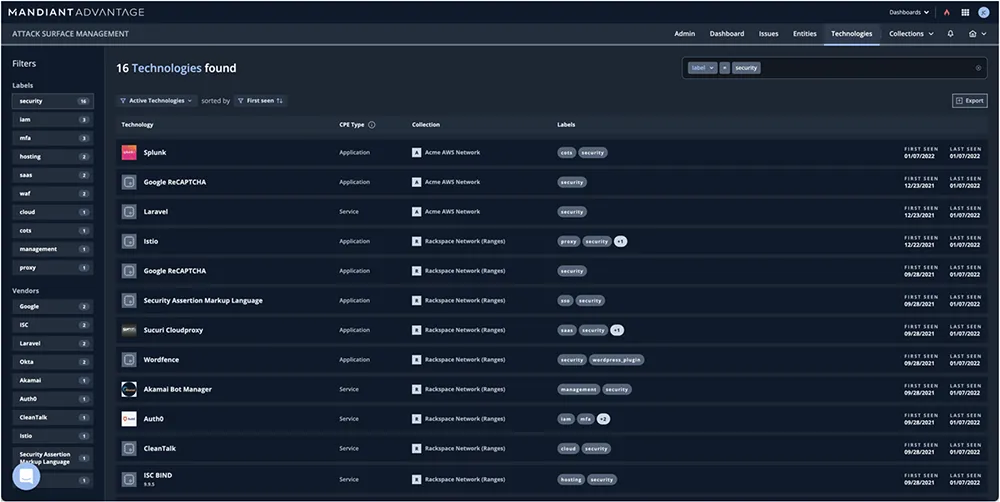
Source: Google Cloud
Mandiant Attack Surface Management offers organizations the ability to see their attack surface from an adversary’s perspective. By automating asset discovery and analysis, it identifies vulnerabilities, misconfigurations, and exposures across dynamic, distributed, and hybrid IT environments.
Key features include:
- Continuous monitoring: Provides daily, weekly, or on-demand scans to keep external asset visibility up-to-date and responsive to emerging threats.
- Active asset checks: Employs benign payloads based on Mandiant intelligence to validate when assets are vulnerable to exploitation, allowing teams to prioritize remediation.
- Outcome-based asset discovery: Enables tailored workflows for discovering assets aligned with business outcomes or security goals.
- Asset inventory: Creates detailed inventories of external applications, services, and technologies in the organization’s ecosystem.
- Shadow IT identification: Continuously monitors for unmanaged or unknown assets, providing daily summaries to maintain oversight of shadow IT.
5. Tenable Attack Surface Management
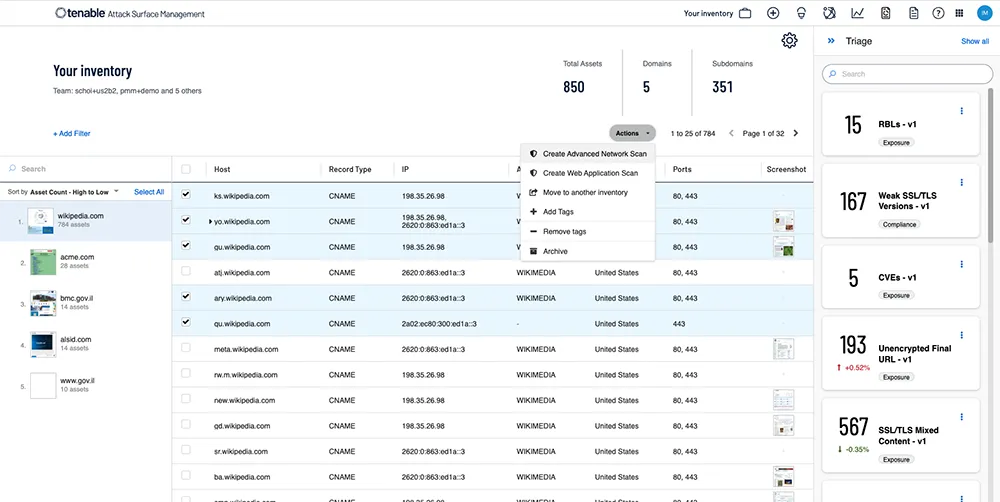
Source: Tenable
Tenable Attack Surface Management provides organizations with a view of their internet-connected assets, services, and applications, enabling proactive risk management. By mapping the internet, the tool uncovers known and unknown assets and integrates with Tenable’s broader suite of security tools for attack surface visibility and mitigation.
Key features include:
- Discovery: Maps over 5 billion assets across the internet to identify all domains and internet-facing resources, including previously unknown assets. Continuously monitors for changes in the attack surface and sends notifications.
- Contextual insights: Provides metadata, including over 200 fields, to help organizations assess the business context of discovered assets.
- Integrated cyber risk assessment: Connects with Tenable One, Tenable Vulnerability Management, and Tenable Security Center to scan for blind spots, assess vulnerabilities, and address risks across the external attack surface.
- Continuous monitoring: Delivers ongoing visibility into internet-connected assets to help organizations keep up with evolving threats.
- Compliance support: Identifies locations where personally identifiable information (PII) is captured and stored, ensuring compliance with industry regulations.
Conclusion
Organizations seeking external attack surface management solutions can choose from a variety of tools tailored to their needs. These alternatives provide capabilities such as continuous asset discovery, risk prioritization, shadow IT identification, and multicloud visibility, often integrating with existing security workflows. By leveraging automated analysis and actionable insights, these tools enable businesses to mitigate risks and improve their overall security posture.