



CyCognito Attack Surface Management, a component of the CyCognito external attack surface management (EASM) platform, scales to the risk needs of the world’s largest global organizations.
Make efficient decisions and bolster your organization against potential threats with clear and contextual risk insight. CyCognito’s continuous business structure mapping and active security testing eliminates gaps–across all subsidiaries and brands, automatically.
Focus your efforts on the critical 1% of issues that matter most and ensure your team efficiently operationalizes results with native integration to technologies such as Workato, Splunk and ServiceNow.
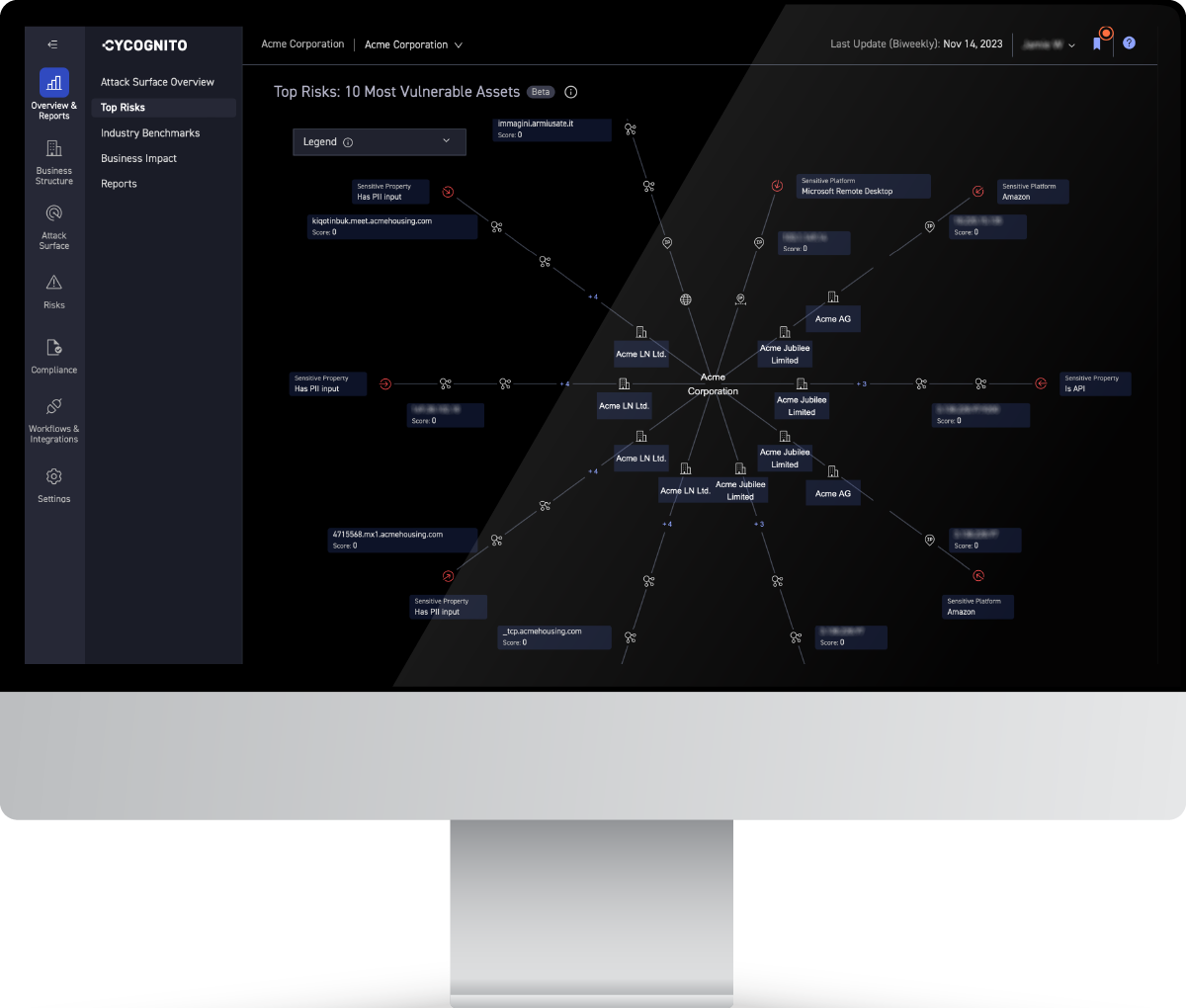
See how CyCognito maps an organization’s business structure, uncovers assets and finds the path of least resistance to the heart of an organization.
Experience how CyCognito’s built-in asset classification and attribution makes understanding your attack surface and prioritizing your team’s responses to threats simpler and faster than ever.
Gain full visibility into every part of your enterprise and the assets tied to it. Based only on the name of your organization, CyCognito uses artificial intelligence and machine learning to continuously map your organizational business structure to exposed assets, generating unique digital fingerprints that strengthens your security posture.
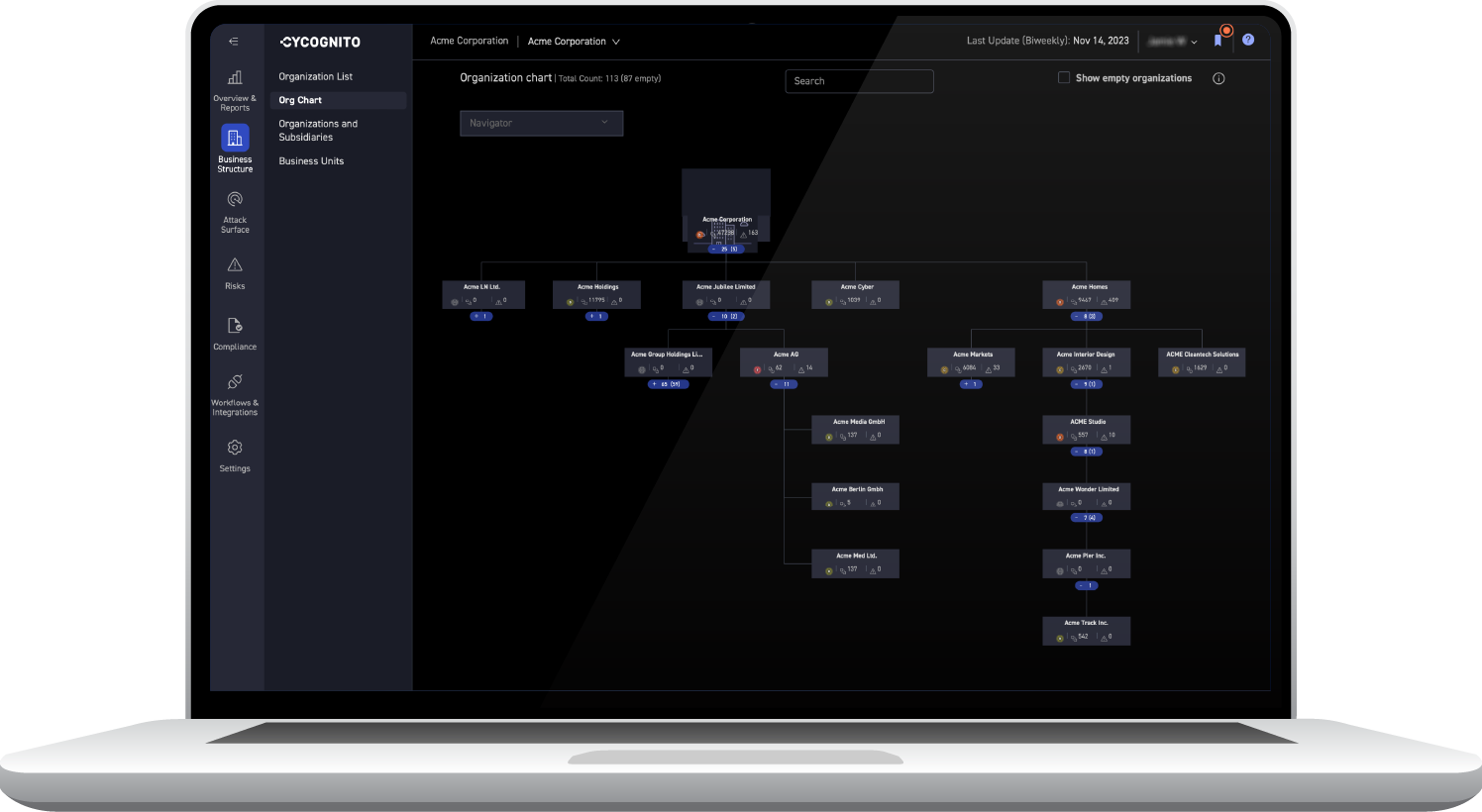
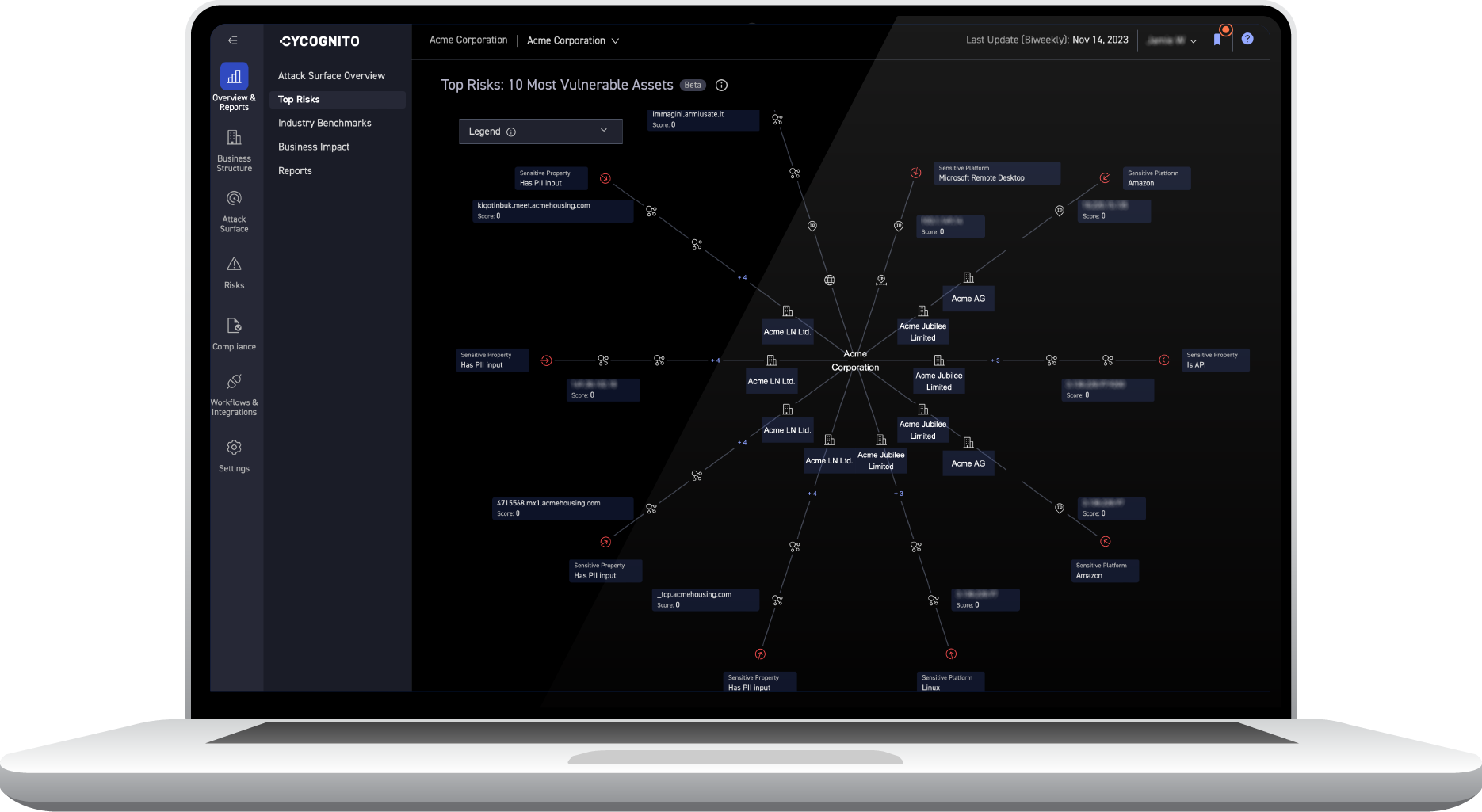
Uncover hidden links between machines and map them back to your organization by region, departments, subsidiaries and brand. CyCognito helps you remediate issues faster with detailed asset information, issue evidence, mitigation steps and ownership information at your fingertips.
Track the third-party software libraries and open source components that attackers can leverage to exploit your defenses. CyCognito provides early warning of risk from these often under-managed resources, allowing you to prioritize and respond to issues before they become incidents.
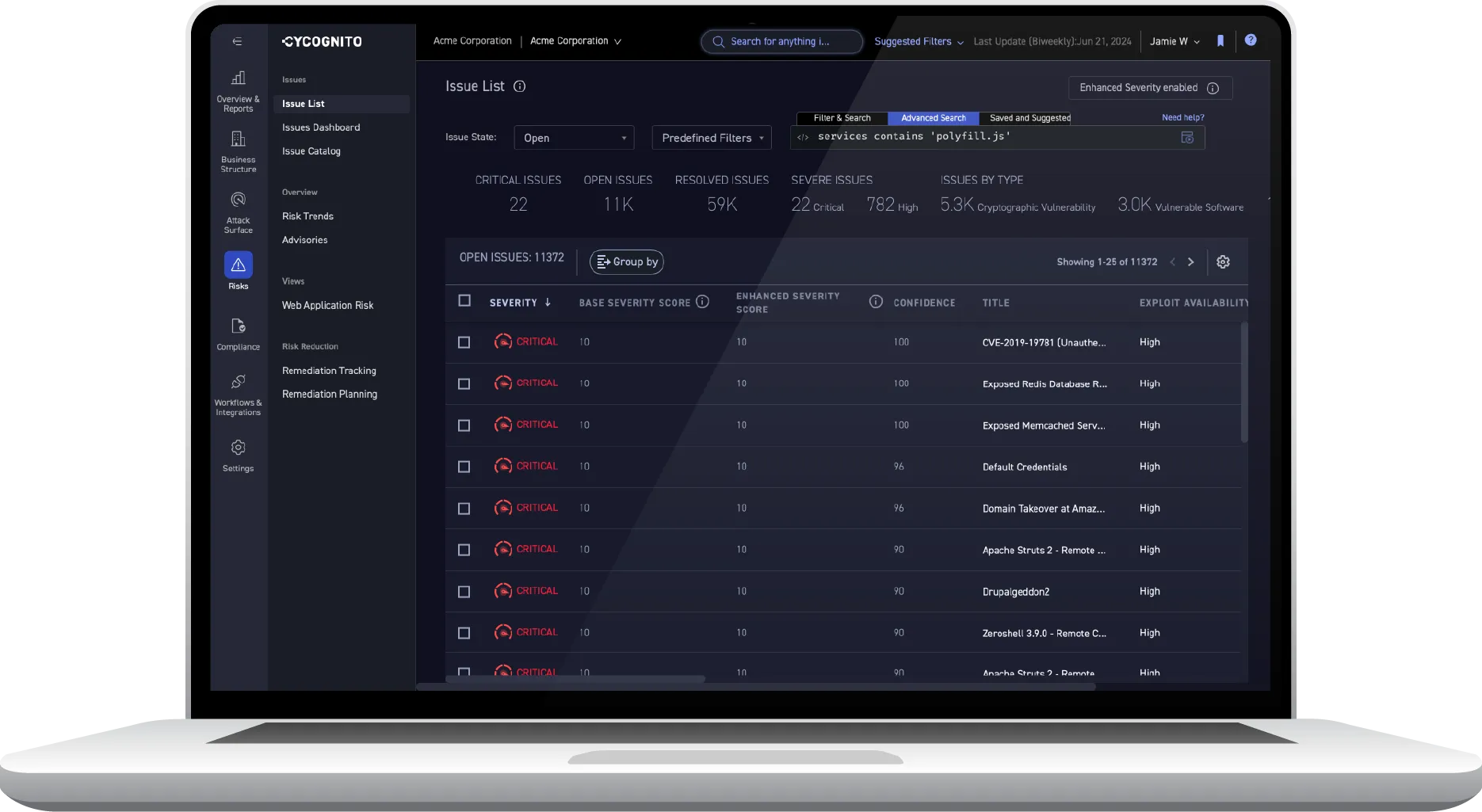
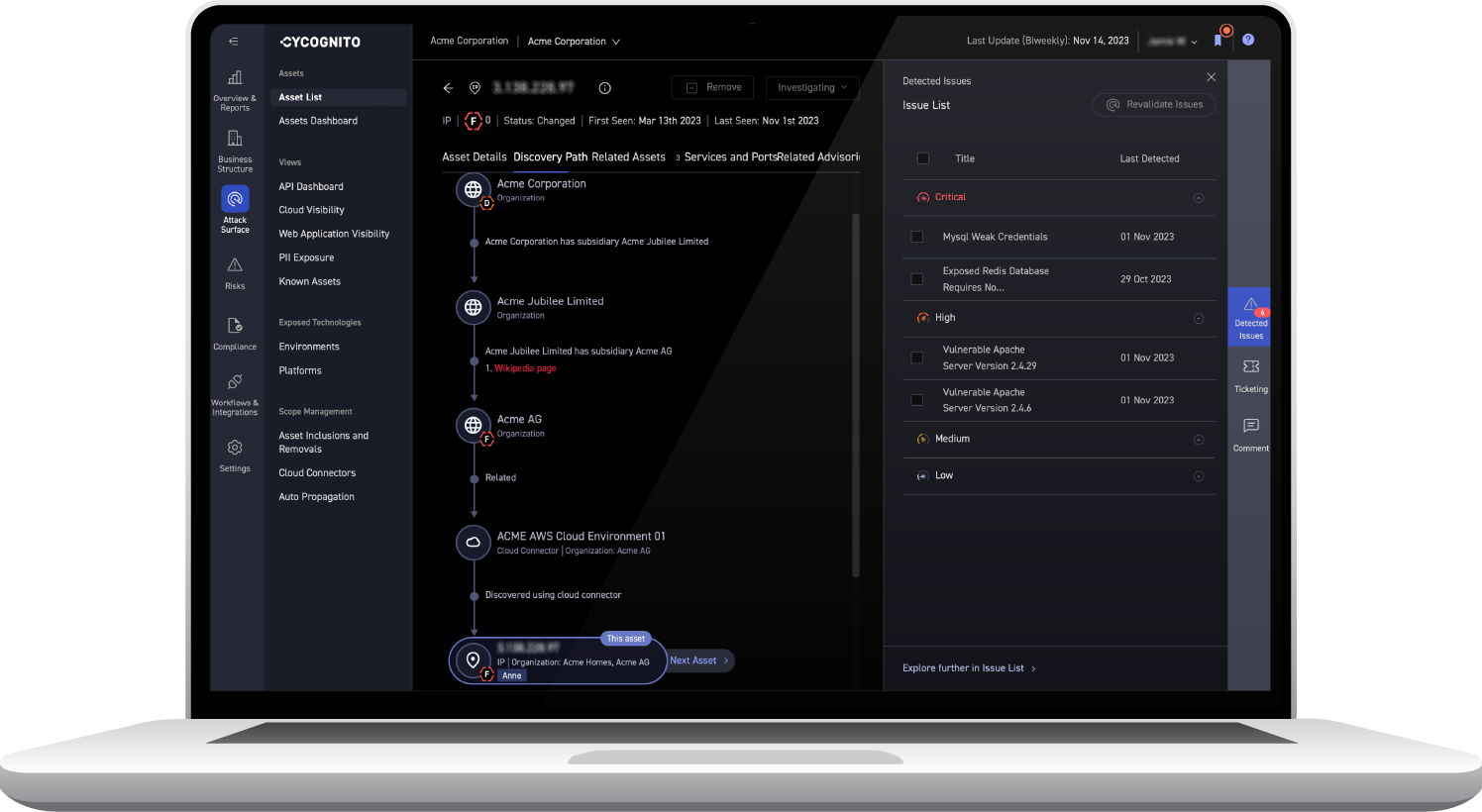
Access hundreds of contextual elements per asset, including security test results, to enable your teams to close more tickets, faster. CyCognito digs deep to uncover context based on an attacker’s perspective, including attribution and unique data such as discoverability and attractiveness.
Learn how you can uncover your full organizational structure with high accuracy, enterprise scale, details, and evidence so that you can properly understand who owns and manages each digital asset exposed to the internet.
See how our discovery engine uses graph data modeling to map your organization’s full attack surface. Review our core capabilities, key features and what differentiates us from legacy security tools.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
Learn more about key cybersecurity topics and how CyCognito addresses the challenges of managing risk across your external attack surface in the resources below.

Solving meaningful external risk challenges requires the right information at the right time in the hands of the right people.
 Attack Surface
Attack SurfaceThe definitive guide to attack surface management. Learn everything you need to know to reduce your cyber security risk with attack surface management.

In this report, we looked at where serious issues hide on the average attack surface, how basic protections can help (or fail to) protect critical assets, and the ways that deprioritizing issues can help security teams spend their time on the right vulnerabilities.
 Exposure Management
Exposure ManagementExposure management is a set of processes which allow organizations to assess the visibility, accessibility, and risk factors of their digital assets.