With the expansion of cloud services, remote access, business applications, and unmanaged devices accessing corporate networks, identifying and managing potential risks has grown complex. However, with the right tools and strategies, security and IT Operations teams can effectively mitigate risks and secure their internal and external assets. This is why we are very excited about the partnership between CyCognito and Axonius. Working together, we provide a broad picture of risk based on internal and external intelligence allowing mutual customers to efficiently prioritize threats based on their potential for real-world exposure.
The Challenge - Discovering the Unknown Unknowns
Today's attack surfaces are growing exponentially, leaving organizations in a constant state of catch-up. Managing this ever-shifting landscape is a complex challenge, fueled by diverse assets scattered across remote workforces and a network of applications in constant flux. The biggest risk lurks in the shadows: the "unknown unknowns" we can't see. Traditional security tools, working in isolation, are blind to these hidden threats and leave externally exposed assets vulnerable. These challenges, combined together with an ever evolving threat landscape (what was secure yesterday, may be vulnerable today), create a perfect storm of opportunity for threat actors and a nightmare of risk for security and operations teams.
Security and operations teams must gain a holistic view of their attack surface and develop strategies to mitigate their exposure.
The Solution
The first step in addressing these challenges involves gaining complete visibility into the attack surface. CyCognito and Axonius, working together, are essential solutions that allow an organization to identify, protect, and manage all of its digital assets effectively.
Gaining Comprehensive Visibility
The Axonius Platform, through its API connections to over 800 3rd party security and IT tools, gathers context-enriched data about internal assets. Joint customers who deploy the Axonius integration for CyCognito gain the external attacker view of exposure. CyCognito adds missing assets exposed externally along with the critical risks that could lead to compromise. The partnership enables organizations to prioritize threats based on their real-world potential for risk and impact, thus providing enhanced efficiency in remediation efforts.
How it Works
- Connect the CyCognito Adapter.
Supply CyCognito credentials to the Axonius Adapter and allow it to fetch asset and vulnerability data via a simple API key. - Identify Security Coverage Gaps
Utilize the Axonius Query Wizard to identify new assets, vulnerable software, open ports, missing patches, exposed APIs and data, and more. Axonius ensures comprehensive verification of assets examined by CyCognito, enhancing the integration's effectiveness. - Automating Enforcement
Take automated actions against prioritized threats through the Axonius Enforcement Center or CyCognito Community Library.
Axonius + CyCognito Controls Coverage Gap Analysis
Joint customers are able to visually and quickly understand their complete coverage, including what is unmanaged and at risk from an attacker's perspective.
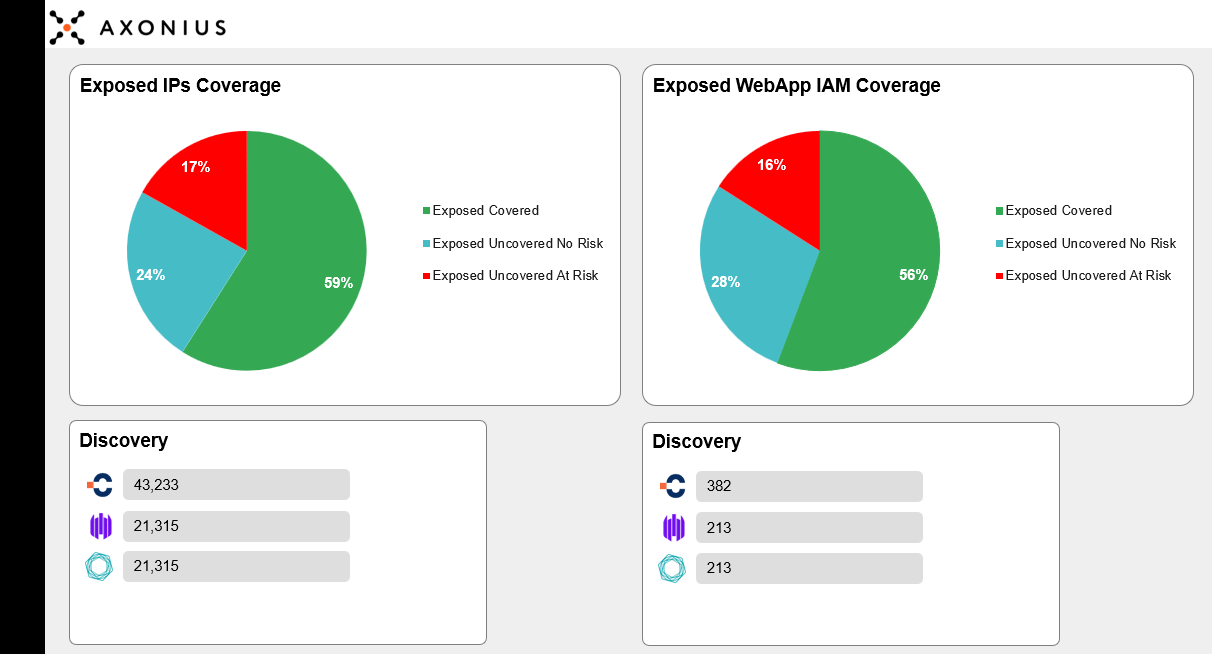
Figure 1. Visibility into assets at the greatest risk from an attacker's perspective
In Figure 1, the user can clearly see assets that were previously known in green, along with the external assets that were previously unknown (discovered solely by CyCognito) represented in blue and red. Additionally, CyCognito has identified the assets represented in red as externally exposed, previously unknown, and containing critical risks.
These assets represent the greatest risk to the organization from an attacker’s perspective.
Gaining complete visibility into an organization's attack surface is crucial for addressing the ever-evolving landscape of cyber threats. CyCognito, a leading attack surface management platform, excels at identifying previously unknown and hidden assets, while Axonius streamlines internal asset inventory and enforces security policy and prioritization. By working together, these tools provide a comprehensive view of an organization's digital environment, enabling them to effectively protect and manage their assets against a wide range of cyberattacks. Learn more about this integration.
CyCognito solves one of the most fundamental business problems in cybersecurity: seeing how attackers view your organization, where they are most likely to break in, what systems and assets are at risk, and how you can eliminate the exposure. If you are not a CyCognito customer and want to learn more about how we can help you ensure you have the most up-to-date external asset inventory, please contact us. To learn more about the CyCognito and Axonius partnership, please contact us at [email protected].



