Organizations rely on stable systems to run their operations. Unfortunately, the IP addresses representing these systems can change frequently. This is especially challenging for cybersecurity, where identifying and tracking assets by IP address is crucial.
Dynamic IP management is the practice of identifying, tracking, and contextualizing systems that use dynamic IPs to ensure accurate visibility, reduce noise, and maintain a continuous security posture.
Understanding different types of dynamic IPs and their impact on security is essential to addressing the challenges they pose. In this blog I will write about the different types of dynamic IP addresses, the challenges they create and how CyCognito addresses this challenge for our customers.
IP Management Challenges for Cybersecurity
Security teams often struggle to associate dynamic IPs with the systems they represent. A single external facing system can unpredictably appear as a new or different system, leading to security blind spots and operational inefficiencies (Figure 1).

Figure 1. Example of a support site with a new IP address assigned each day. (ACME-corp is a fictitious company)
Types of Dynamic IPs and Their Security Implications
Not all dynamic IPs behave the same way, nor do they carry the same security significance. To effectively manage them, it is crucial to understand the two primary delivery mechanisms: content delivery networks and load balancers.
- Content Delivery Networks (CDNs): CDNs use distributed servers to optimize performance and scalability by rerouting traffic. CDN delivered IP addresses are part of a global, shared infrastructure used by thousands of websites and services. They simply serve cached content, making them irrelevant in terms of security attribution.
Security Impact: CDN IP addresses do not hold customer-specific security risk and should be de-emphasized in attack surface monitoring.
- Load Balancers (LBs): Load balancers distribute network traffic among multiple servers to prevent congestion and enhance availability. Unlike CDN IPs, a load balancer is configured and controlled by the organization, carrying relevant security context.
Security Impact: LB IP addresses are meaningful from a security perspective and require continuous tracking to maintain an accurate risk profile.
Understanding these differences allows security teams to refine their approach to dynamic IP management, ensuring that they treat LBs as meaningful assets and CDNs on a more secondary level.
Why Dynamic IPs Are Challenging for EASM Solutions
External Attack Surface Management (EASM) solutions rely on IP addresses to track and monitor assets. However, when those IPs change frequently, several challenges arise:
- Lack of Context Beyond IPs: EASM solutions see IPs externally but often lack visibility into the stable systems they represent. This disconnect makes it difficult to correlate changing IPs to persistent customer assets.
- Loss of Historical State: When an IP rotates, it may appear as a brand-new asset, making it challenging to track long-term trends and maintain security oversight.
- False Positives and Inefficiencies: Rapid IP changes can trigger unnecessary alerts, leading security teams to chase non-issues rather than focusing on actual threats. Successful management of dynamic IPs requires differentiating between genuine changes in the actual stable system, and routine IP reassignments.
To address these challenges, an active approach is required, one that intelligently maps IP changes to stable entities while filtering out irrelevant noise.
The Impact of Dynamic IPs on Organizations
Failure to properly manage dynamic IPs can lead to operational inefficiencies and security blind spots:
- Inefficiency: Treating every new IP as a separate entity results in redundant work and unnecessary investigations.
- Traceability Issues: Historical tags, comments, and classifications tied to an old IP do not automatically transfer when an IP changes, causing gaps in asset management.
- Miscommunication: Asset owners may not recognize the new IP, leading to confusion and delays in remediation.
- Distorted Metrics: The attack surface appears to fluctuate artificially, making it difficult to track real security trends over time.
Dynamic IP management is not just improving efficiency—it is critical to maintaining an accurate and actionable attack surface representation.
How CyCognito Helps Manage Dynamic IPs
CyCognito addresses dynamic IP challenges by implementing behavior-aware asset tracking, contextual analysis, and enhanced scanning strategies. Together, these reduce noise and increase asset inventory accuracy.
The general workflow is shown in Figure 2.
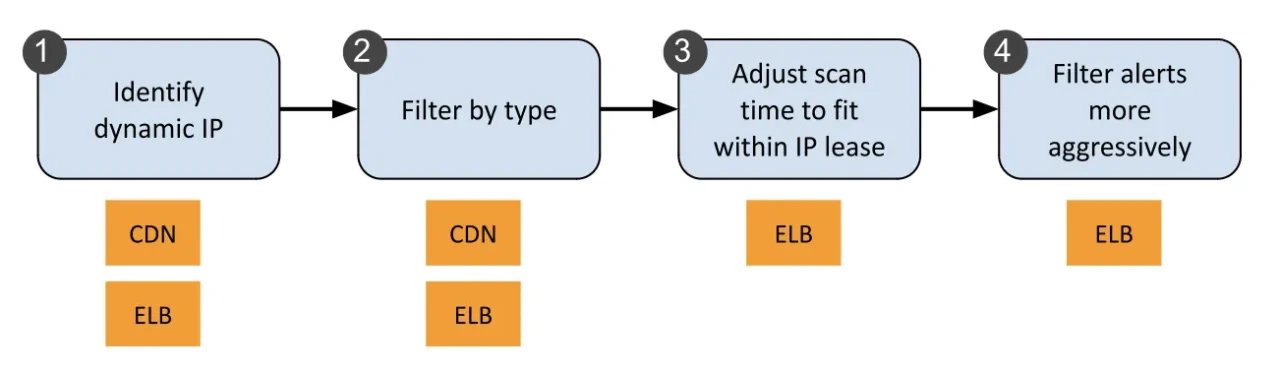
Figure 2. CyCognito automated workflow for Dynamic IP addresses
Step 1: Identifying Dynamic IPs
- Detect dynamic IPs by analyzing DNS resolution patterns and infrastructure behavior. This allows us to differentiate between stable assets and ephemeral IP assignments.
Step 2: Classify and Tag Dynamic IPs
- For CDNs: These IPs are categorized as semi-related assets, hidden from asset lists, and excluded from attack surface metrics to reduce noise.
- For ELBs: These IPs remain associated with customer environments, marked as dynamically resolved, and tracked over time for changes. Figure 3 shows how this is represented in the CyCognito console.
Figure 3. Dynamic IP Address Context Visible in the CyCognito Console
Step 3: Adjust scan time for ELBs
- More frequent port and vulnerability scanning of relevant IPs.
- Daily DNS resolution tracking to monitor infrastructure changes.
Step 4: Filter alerts more aggressively
- Context-aware filtering to suppress irrelevant alerts caused by transient IP reassignments.
- Keep detections that were detected only within the time frame in which the asset belonged to the specific customer’s host–dismiss any detections that were caused due to different, unrelated hosts.
By implementing this workflow CyCognito ensures that security teams focus on the risks that truly matter while eliminating distractions caused by routine infrastructure changes.
Future Outlook: Moving Beyond IPs to Stable Entities
CyCognito will continue to refine its dynamic IP management capabilities with the long-term goal to shift the focus from individual IPs to the stable entities behind them. We will also expand our adjustable scan time and alert filtering capabilities beyond IP addresses to web apps. By doing so, we provide our customers with a more accurate, continuous, and meaningful representation of their attack surface, regardless of how frequently their infrastructure changes.
This evolution will redefine how EASM solutions handle dynamic assets, ensuring that organizations maintain visibility, reduce inefficiencies, and enhance their overall security posture in an ever-changing digital landscape. Stay tuned for more!
Discover, Monitor and Test Your Dynamic Assets with CyCognito
CyCognito is an automated external exposure management platform with integrated reconnaissance and asset discovery. Designed from the ground up to remove the complexity of identifying and testing external facing assets, with CyCognito, your teams know:
- All exposed assets are continuously identified, validated and actively tested New business structures and related exposed assets will be added automatically, without manually entered seed information or prompts.
- Dynamic IP address based assets are identified and handled appropriately to ensure proper testing and visibility.
Reach out today to schedule a demo of the CyCognito platform and see how we will help your team reduce noise from dynamic IP addressed-based assets and maintain a continuous security posture.



