CyCognito Attack Surface Management (ASM) now offers the ability to discover APIs on an organization’s attack surface. Given the proliferation of APIs and their attractiveness to attackers, this capability is an important new tool for security teams. This post describes the issue and how CyCognito ASM solves it.
Are APIs a Security Problem?
Most modern applications are built using APIs. This has caused an explosion in public-facing APIs on the internet. It’s not uncommon for an enterprise to have hundreds or even thousands of APIs exposed.
According to Gartner, 90% of web-enabled applications will have more attack surface area in exposed APIs rather than in the user interface. Gartner also predicted that in 2022, API abuses will move from infrequent to the most frequent attack vector. Salt Security research showed that 94% of organizations experienced security problems in production APIs in 2022, and one in five suffered a data breach due to security gaps in APIs.
Why APIs Are Attractive to Attackers
APIs, by nature, have access to application logic, sensitive data, databases, and the underlying infrastructure of applications using them. They are prime targets for attackers. Moreover, they are easy to deploy and integrate - making them harder to track and manage by security teams.
There are many ways attackers can threaten an API:
- Accessing information they should not be able to access, e.g., data exfiltration
- Changing or exploiting the API or underlying server, e.g., SQL injection
- Preventing the API from working by overwhelming it with a DDoS attack
What Are Rogue, Shadow, and Zombie APIs?
Many organizations now use API gateways to handle common management tasks like authentication, rate limiting, and reporting. APIs are deployed via the gateway and can therefore be managed and tested properly.
Not surprisingly, not every API is deployed using a gateway. These unmanaged APIs pose significant security risks. There are three classes of unmanaged APIs:
- Shadow APIs - Any undocumented and unmonitored API used in an application, including untracked use of a third-party API
- Zombie APIs - Any unmaintained API that is still accessible in production, often an old version
- Rogue APIs - Any API that provides unauthorized access to data or operations. These can be created with malicious intent or caused by security flaws.
All three of the above need to be known to an organization to manage risk.
Discovering and Viewing APIs Using CyCognito
To discover APIs, the Cycognito platform sends a normal HTTP request to each URL owned by an organization and then analyzes the response. If two or more of the following criteria are met, the platform tags that URL as an API endpoint:
- URL contains “api,” “apis” and the like.
- URL contains specific paths that are known to be APIs, for example ‘/xmlrpc.php’
- HTTP response contains known content which is related to APIs
- HTTP content type is either XML or JSON
The primary way to view APIs in the Cycognito platform is via the API Dashboard (Attack Surface > Views > API Dashboard). The following information is available, as shown in Figure 1 below.
- Total – Your total number of API endpoints discovered by CyCognito. (top left)
- At risk – The number of API endpoints that are considered to be at risk. This means the API is found on a web application that has critical- or high-severity issues. (top middle)
- The donut chart shows the distribution of API endpoints according to whether or not they are considered to be at risk
- APIs per organization – Shows how API endpoints are distributed across organizations. (lower left graph)
- Hosting type over time – Shows how API endpoints are distributed over time according to their hosting type: owned, cloud, or other. (lower right graph)
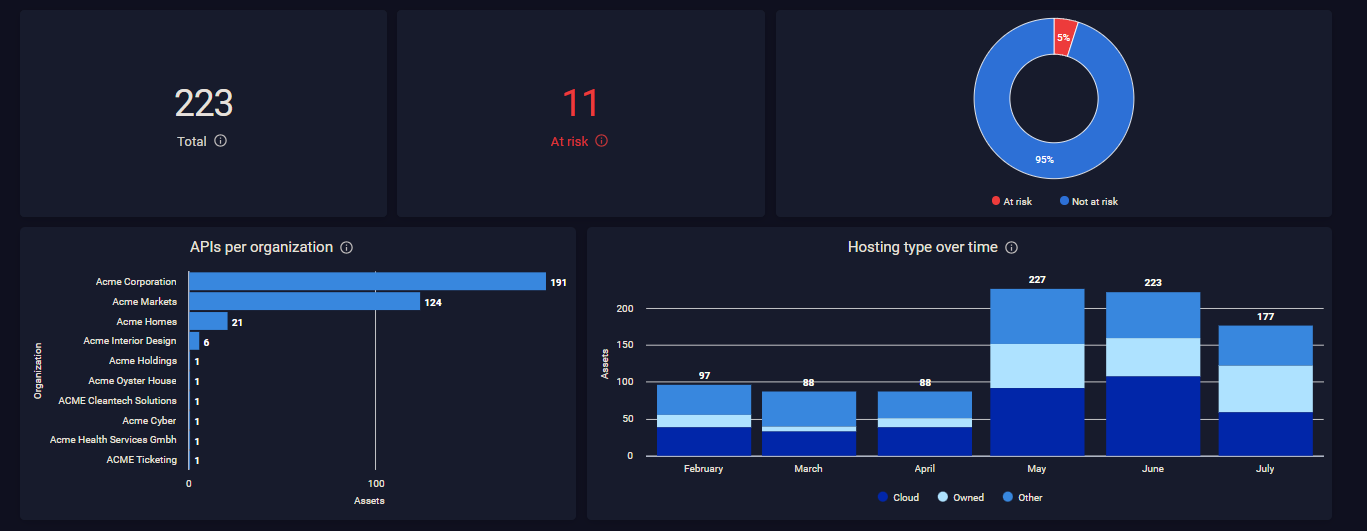
Figure 1: The API Dashboard shows total APIs by type, per organization, and those at risk.
The API Dashboard can also show you the security posture of your APIs. This allows you to assess the risk associated with your API endpoints and take necessary measures to enhance protection.
- HTTPS encryption adoption for API endpoints – Shows the distribution of API endpoints according to whether or not they have adopted HTTPS encryption.
- Web apps with API protected by WAF – Shows the distribution of API endpoints according to whether or not their hosting web application is protected by a WAF.
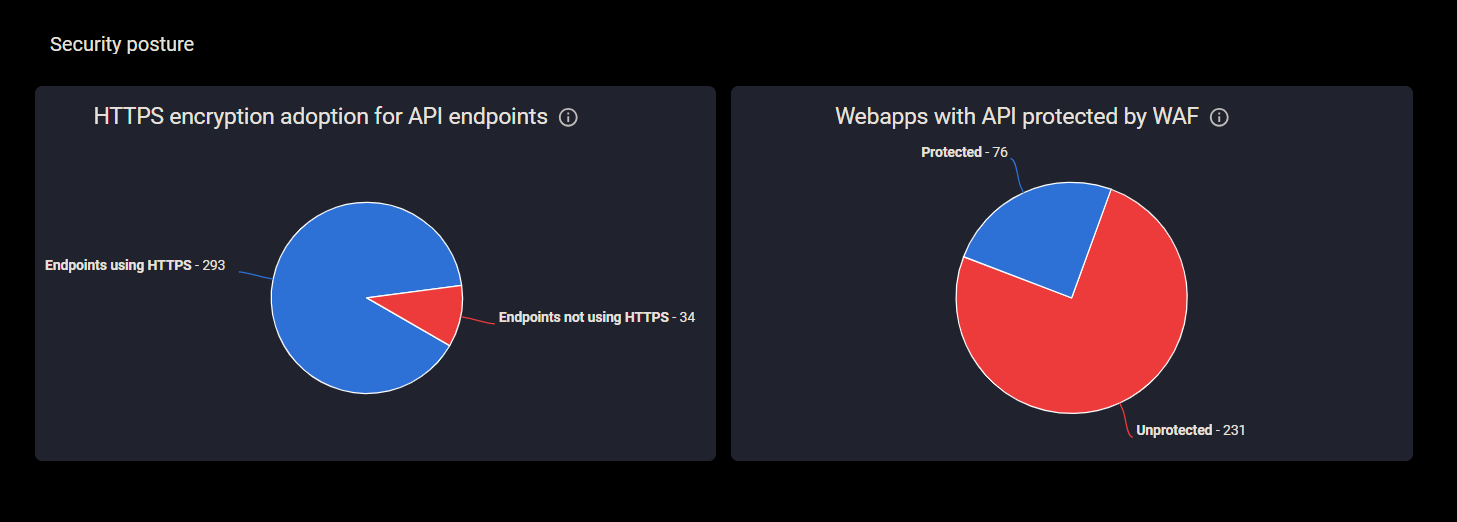
Figure 2: Security posture dashboard shows 34 endpoints without HTTPS and 231 without WAF protection.
The information can be accessed on the Asset List by using the Filter & Search keyword WEB APPLICATION CONTAINS API ENDPOINTS. The Asset Details page of a particular web application will also show related APIs. This information is also available via the CyCognito API.
Getting a Handle on Unmanaged APIs
One of the benefits of the CyCognito platform is asset attribution. Using this feature, a security team can understand what team owns the unmanaged API.
Typically, there are three ways to go for remediation, which include both ongoing management of the APIs and fixing any immediate security issue(s).
- Register in API Gateway - the Cycognito platform can export a list of APIs that an organization can import into an API Gateway like Apigee (Google), Kong, or Mulesoft (Salesforce).
- Register in API Security Tool - these tools have limited discovery capabilities. Importing a list of previously unknown APIs to a tool from vendors like Noname Security or Salt Security would add them to the ongoing testing of these APIs.
- Send to Security for Fix - use CyCognito integrations to send issues to a ticketing system (Jira, ServiceNow) or security orchestration, SOAR, platform like Palo Alto Cortex XSOAR. Configuring a WAF to protect an API would be a straightforward fix, for example.
The feature is currently available to all CyCognito customers. Simply navigate to the API Dashboard, shown above in Figure 1, to start. If you are not a CyCognito customer and are interested in a demo, please contact us.



