Pen testers use active testing technologies to probe and analyze systems dynamically, just as an attacker does. Active testing confirms whether a vulnerability is actually exploitable, providing security teams the insight they need to prioritize remediation.
Active security testing delivers confidence, sorely needed in today’s IT security world where noise and false positives have become a major part of an analyst’s day.
Unfortunately, active security testing is not without challenges. Considered by many to be slow and difficult to operationalize, it's often the opposite of the “faster fixes” most vulnerability management teams strive for, despite the confidence it delivers.
Follow along as we explore the value of active security testing and how it reduces detection and remediation times. We’ll look at what active testing is and provide an operational checklist for reaching faster fixes. And at the end, we will discuss how CyCognito delivers the security testing organizations need, as a fully automated service.
Defining the Active Security Testing Problem
Active security testing is both necessary and difficult. While it enables accurate vulnerability detection, it can also be complex, resource intensive, and potentially disruptive when run in production.
This creates a difficult trade-off: to properly perform active security testing, teams need time to thoroughly test and analyze, leaving vulnerabilities undetected for longer periods. Yet, this process can feel impossible to speed up, because rushing a test or omitting certain types of tests also leaves vulnerabilities undetected. It’s a no-win scenario.
With the right tools, security teams can break free from this trade-off and turn active testing into a driver of faster, more confident outcomes.
Measuring Success
Before we get into security testing, it’s important to remember the ultimate goal of vulnerability management—reducing dwell time. Active testing plays a direct role in achieving that.
In its most basic form vulnerability dwell has two phases: time to detection (TTD) and time to remediation (TTR). Together, they map the vulnerability management lifecycle and window of exposure (Figure 1).
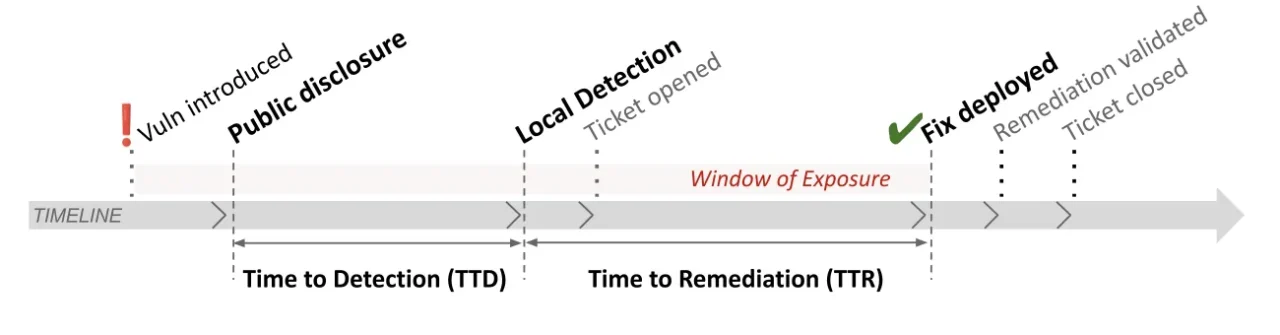
Figure 1: Basic Vulnerability Management Lifecycle
While the Cybersecurity and Infrastructure Security Agency (CISA) recommends TTR for critical vulnerabilities to be within 15 days, it’s not uncommon in practice for it to reach 270 days or even more. This is a significant disconnect, especially since according to CISA, 50% of known exploited CVEs are being used within 48 hours.
Accurate and Verified: The Power of Active Testing
Vulnerability management (VM) teams operate under constant pressure. Their mission is clear: find vulnerabilities, rank them, and fix them quickly. But without accurate data, their efforts slow down, leaving real risks unresolved for longer times.
Active security testing changes this dynamic. By delivering accurate results with rich context, it helps teams focus their efforts where it matters most; fixing real, exploitable vulnerabilities.
Accurate Results
Fast, accurate remediation starts with knowing which vulnerabilities are real. Active tests have built-in test logic that examines the response to each test input, marking steps as success or failure until a final assessment is reached. This eliminates the uncertainty that is typical with passive scanning technologies.
Let's look at an example: validating if an RDP endpoint is susceptible to BlueKeep (CVE-2019-0708). In this example, an active test using python opens a connection on port 3389 (RDP) and sends a crafted packet. If the RDP server responds in a specific way, it is vulnerable to BlueKeep (Figure 2).
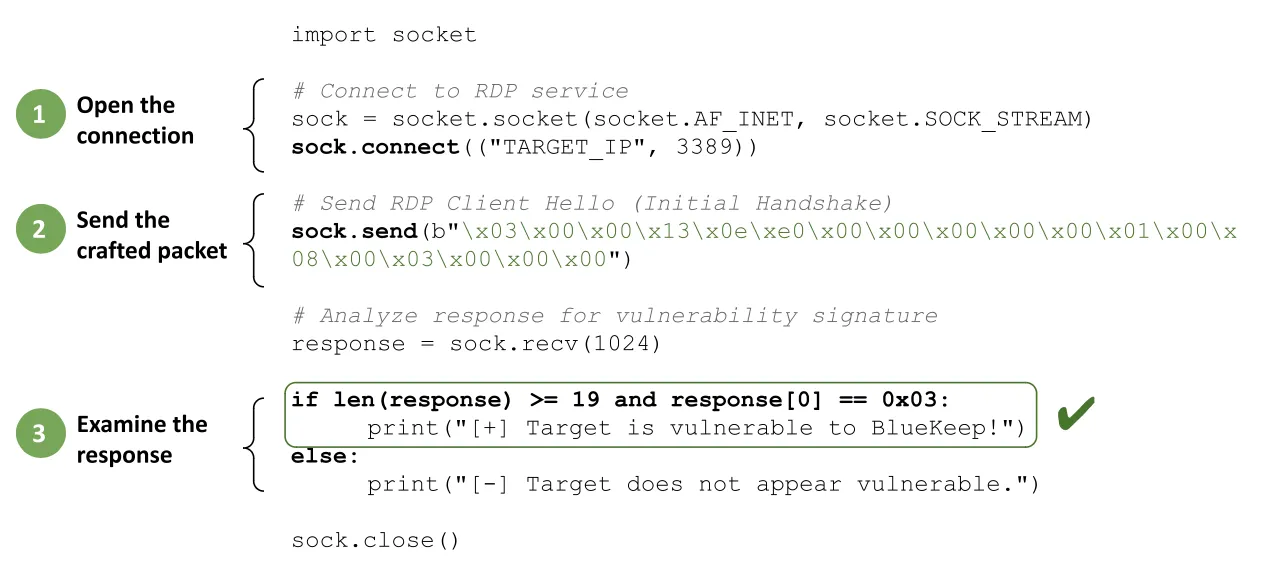
Figure 2. Example Active Test Payload That Identifies Bluekeep RCE Vulnerability
Detailed Context
Active security testing often involves multiple interactions to validate a vulnerability. During the testing process, asset and issue data is collected. Every piece of data gathered is context that shortens the repair process and keeps teams focused.
Let's look at some context examples:
- Proof of exploitability, such as the vulnerable server’s actual response to a crafted BlueKeep packet, for example 'MCS Disconnect Provider Ultimatum PDU - 2.2.2.3’
- Detection evidence, such as the default username/password that enables access, the missing S3 bucket that permits domain takeover, or the URL and file obtained in a path traversal attack
- Affected environments, such as content management systems, databases, javascript libraries, or remote connections
- Affected platforms, such as Drupal, Microsoft ASP.NET, or OpenLDAP
- Potential impact, such as loss of integrity and loss of confidentiality on an e-commerce web application
- Remediation guidance, such as which service package to update or port to close
Overcoming the Security Test Problem
It should be clear that the security testing problem is not if it should be done but rather how to do more of it.
Unfortunately, the ideal level of active testing–every exposed component of every exposed asset on a regular cadence–is not achievable using manual or semi-automated technologies. Even well-funded security teams struggle under the volume of tests required for most external attack surfaces.
To run more active tests you must overcome three challenges:
- Incomplete asset inventories
- Lack of business and attribution context
- Over reliance of inadequate testing levels and technologies
Achieving faster fixes is not about running more frequent pen tests. It requires fully automated active testing at scale. This means a completely hands-off process, from asset discovery to active testing and issue prioritization. With the right technology, you gain essential risk visibility across your global exposures without placing any additional burden on your teams.
Achieving Faster Fixes
The path to faster fixes starts by solving these three challenges. Here’s how to tackle each effectively.
Incomplete asset inventories
Full asset inventories are fundamental to accurate vulnerability management. If you don’t know what is exposed, you can’t assess them or fix them. Faster fix activities for this include:
- Weekly/bi-weekly asset discovery across known infrastructure
- Daily active scanning of known assets for port state, service information, etc.
Finding all assets for all divisions within your organization is very difficult to achieve at any sort of useful regular cadence using manual or even semi-automated tools.
Lack of business and attribution context
Asset context, obtained automatically, lets security teams know what the asset is, where it resides, and its business purpose. Activities here include:
- Bi-weekly/monthly business structure mapping using OSINT to track changes to infrastructure
- Asset alignment to business structure for ownership/attribution information
- Asset tagging with business function and type
Business purpose is crucial to assign remediation priority and ownership information enables your teams to efficiently assign remediation actions.
Over reliance of inadequate testing levels and technologies
This third requirement is where the rubber hits the road. Activities here include:
- Weekly/bi-weekly unauthenticated active security testing across all exposed assets running in production
- Evidence collection that follows test cadence
- Risk-based prioritization based on test results, business impact and threat intelligence
While vulnerability scanners also can test, they aren’t commonly configured to do so for a variety of reasons. Many organizations use them for software version grabbing and CVE lookups.
Want more details? Download your copy of the Faster Fixes checklist to ensure you have what you need to reduce remediation times.
What Fully Automated Testing Is (And Isn’t)
Fully automated testing helps maintain consistent baseline security coverage across all exposed assets. This allows security teams to focus their time and expertise on the most important manual testing efforts.
Fully automated testing eliminates labor-intensive test management; tracking changes to business structure, collecting OSINT, and choosing, scheduling and managing tests. It does the heavy lifting for monitoring test impact, collecting evidence, researching solutions and prioritizing results. No asset is ever put on hold “for the next quarter’s test schedule” due to lack of time.
Fully automated testing permits your teams to instantly reach a near ideal state of security testing (Figure 3).
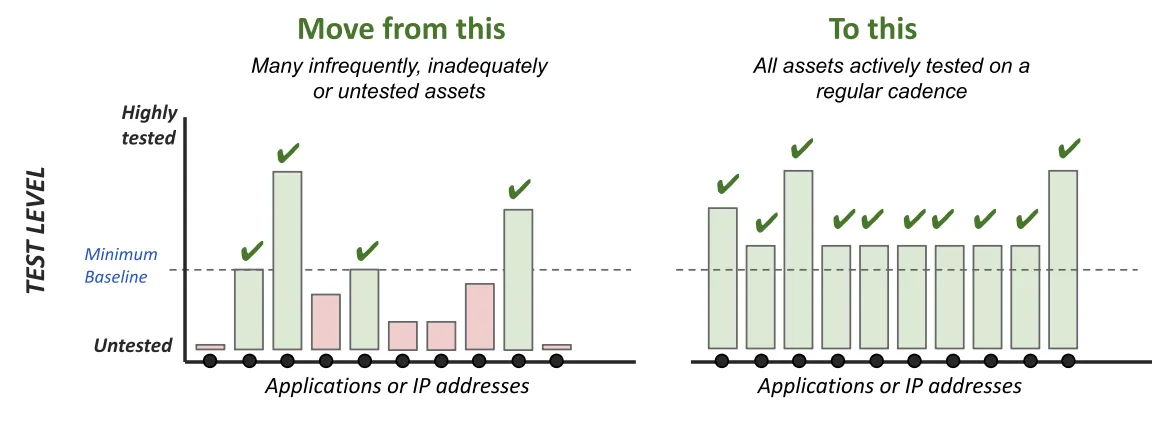
Figure 3. Fully automated testing enables you to uncover, monitor and test all assets continuously
You may think running vulnerability scans is close enough. They are important, but they are most commonly used in passive scanning mode, which only matches protocol banners to CVE databases. They don't actively test unless you set them up that way because of the resource impact to the tested asset, complexity and cost. For that reason testing is reserved for big ticket issues like detecting the Ivanti VPN zero-day or MOVEit transfer exploit. Vuln scanners also can’t find truly unknown assets like those in a remote division that you didn’t know was part of your organization. Real shadow IT.
It’s important to keep in mind that fully automated testing isn’t a replacement for a human tester. There are always situations or proprietary applications that cannot be tested without human control. But a well-designed automated discovery and test technology allows an organization to test more frequently at a deeper level than humans (and budget) permits.
Reduce your Window of Exposure with CyCognito
With CyCognito, you can test more assets, more completely, and uncover hidden risk. Because of the frequent cadence, time to detection is shorter. And with context and ownership information, the time to remediation is also shorter. The result is a lower window of exposure.
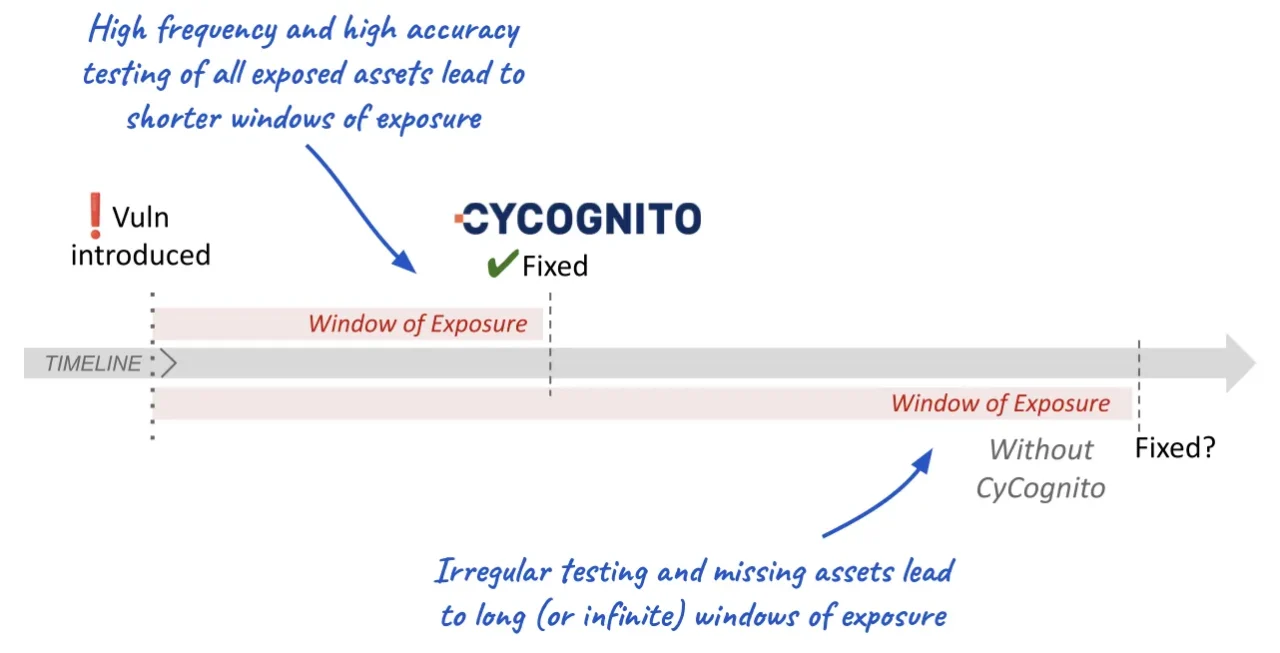
Figure 4: CyCognito decreases your window of exposure through high frequency testing of all assets
With strong customer reviews on Gartner Peer Insights and G2, CyCognito is recognized as a leader in external attack surWith strong customer reviews on Gartner Peer Insights and G2, CyCognito is recognized as a leader in external attack surface management. Our testing platform is purpose-built to help security teams move beyond alerts and into focused, measurable outcomes.
Organizations trust CyCognito for:
- Industry leading discovery engine
- Seedless, fully automated testing of exposed production assets
- Auto-configured and deployed tests for every asset
- Over 80,000 remote tests, including dynamic application security testing (DAST)
- Integration with industry leading tools
Ready to see it in action? Explore our platform through a self-guided, interactive product tour on our website. If you’re looking to understand how CyCognito can help your organization proactively identify and remediate threats across your external attack surface, request a personalized demo today.



