In today’s high-stakes cybersecurity landscape, one truth stands out: if you can’t see it, you can’t secure it. And if you can’t act on what you see, you’re no better off. That’s why we’re focused on delivering continuous improvements that help security teams move faster, see further, and reduce risk where it matters most.
The last month brought a range of updates to the CyCognito platform, designed to simplify operations, strengthen visibility, and support smarter and faster decisions in exposure management. Here is a quick look at what is new.
Azure Cloud Connector Enhancements
We’ve streamlined the creation of Azure cloud connectors with a single-form setup process. Now, security teams can establish connectors at the management group level with automatic permission inheritance for new child accounts (figure 1). The result? Faster onboarding, less manual effort, and reduced risk of missing cloud assets in your attack surface inventory.
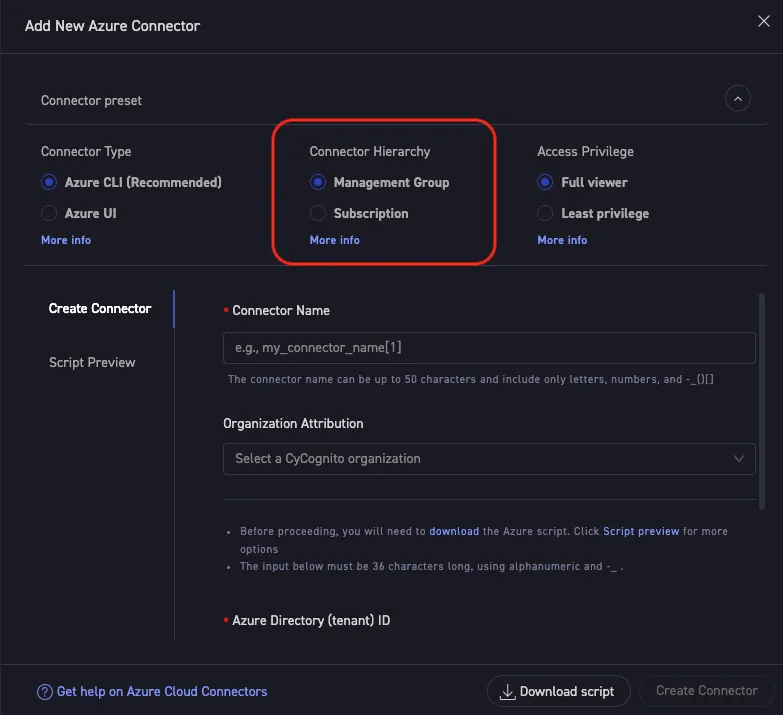
Figure 1: New Azure cloud connector hierarchy choice speeds time to value
WAF Protection Dashboard
Your web application firewalls (WAFs) are only as good as their coverage. Our new WAF Protection Dashboard provides a single view of WAF products across your organization, highlights protection gaps, and helps prioritize critical areas where controls are missing (figure 2). This provides instant visibility and closes the loop on security controls coverage: a critical focus for many security leaders today.
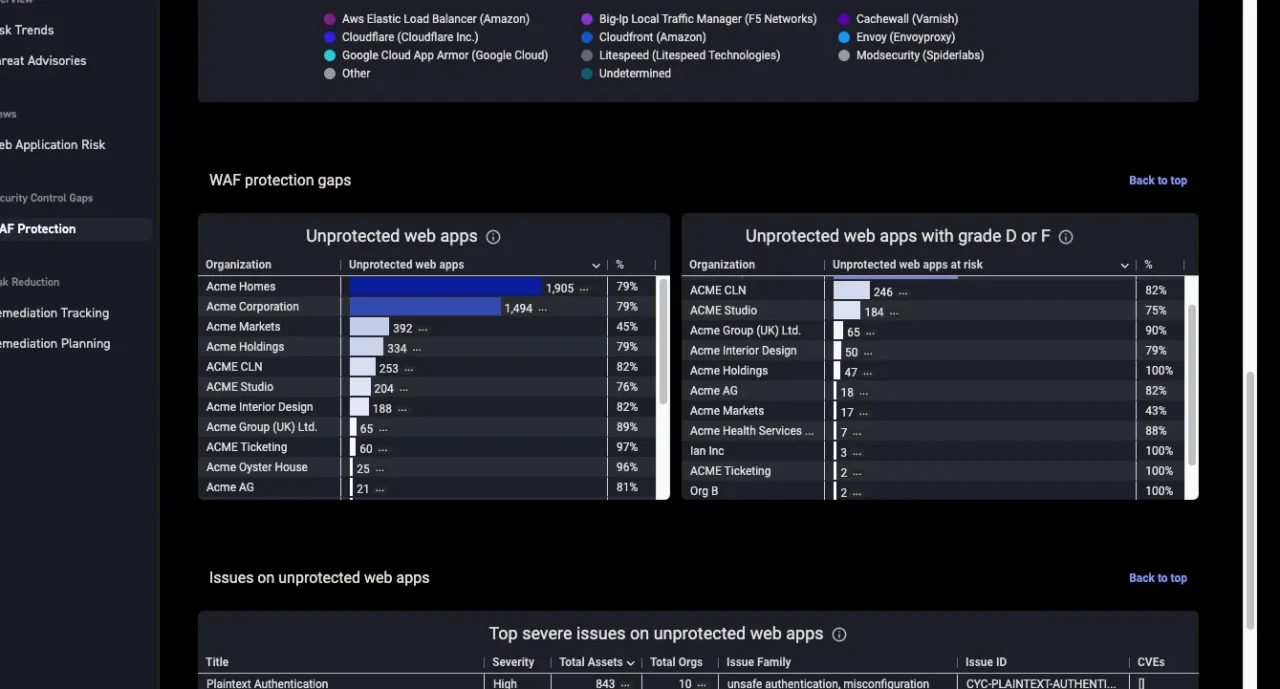
Figure 2: Spot protected and unprotected web apps in part of the new WAF dashboard
Historical DNS Tracking
Ever needed to investigate a domain’s history during an incident response? The new historical DNS tracking capability lets you view domain IP changes over time. This feature helps you track asset evolution and analyze potential exposure windows, supporting stronger investigations and audit readiness.
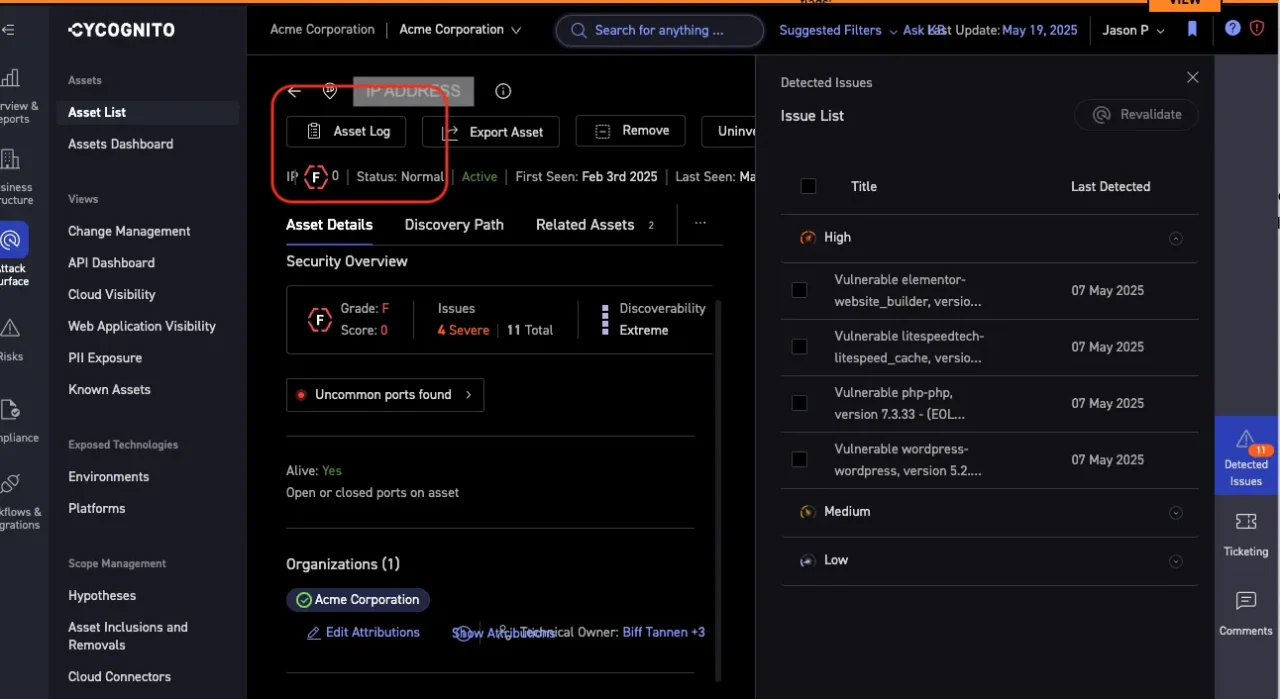
Figure 3: Historical DNS information is now included in the CyCognito asset log
Enhanced Domain Discovery
We’ve sharpened how the platform determines domain ownership. Our improved discovery engine aggregates and weights low-confidence signals to deliver higher-confidence domain associations (figure 4), helping you find more of what’s truly yours, without false positives.
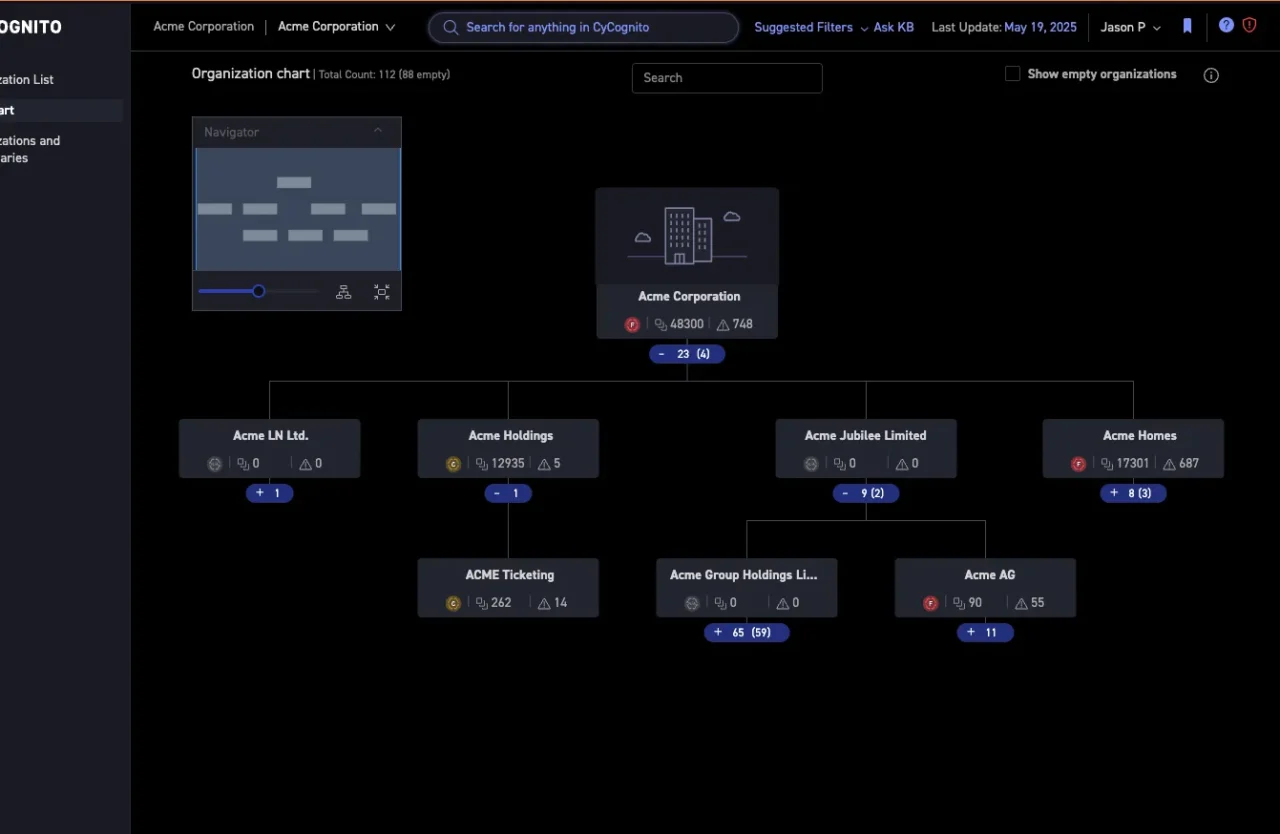
Figure 4. Domain discovery delivers attribution data for every asset, with zero reliance on input seeds.
🤖 AI-Driven Issue Verification Guide
Verifying issues just got easier. Our new verification guide for select issues offers step-by-step guidance (for example using a browser, cURL, Postman, etc.) to validate certain findings using CyCognito’s detection scripts. This empowers your teams to act confidently and independently, reducing friction in remediation workflows (figure 5).
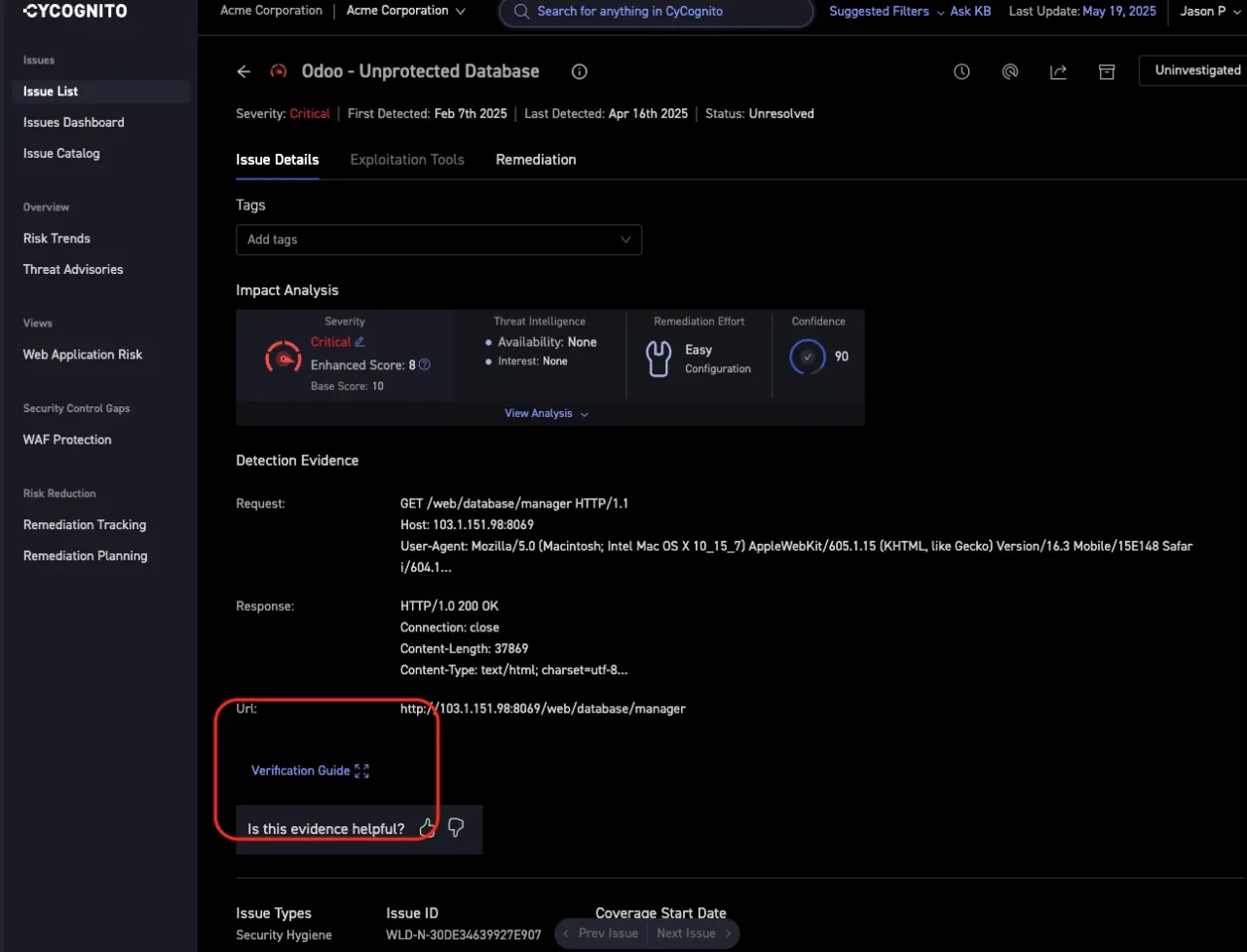
Figure 5: New verification guide button provides clear steps for validation
And More from Earlier This Year
Email Authentication Visibility
We added columns for DMARC, SPF, and DKIM configurations in your Asset List and exports. This enhancement makes it easier to spot email security gaps that could lead to spoofing and phishing attacks.
Enhanced Navigation
You can now open pages in new tabs directly from the CyCognito sidebar menu, making multitasking and investigations smoother across multiple views.
Uplevel your Exposure Management Program with CyCognito
These features reflect our commitment to helping security teams move beyond reactive asset management. They support a proactive exposure management strategy, one that delivers visibility, prioritization, and automation at scale, without adding complexity.
Ready to see it in action? Log in and explore the new capabilities today or contact us for a demo if you’re evaluating CyCognito as part of your exposure management journey.
Stay tuned for next month’s updates. Until then, happy securing!



