



The CyCognito platform enables security and operations teams to proactively identify, prioritize, and remediate exposed risks. With CyCognito, you get instant access to attacker-like reconnaissance, security test results, and prioritized guidance on what to fix first — all with flexible scanning options including daily, weekly, bi-weekly, or monthly cadences to match your team’s needs.
Automatically build a map of your organizational business structure and find assets distributed across your entire external attack surface.
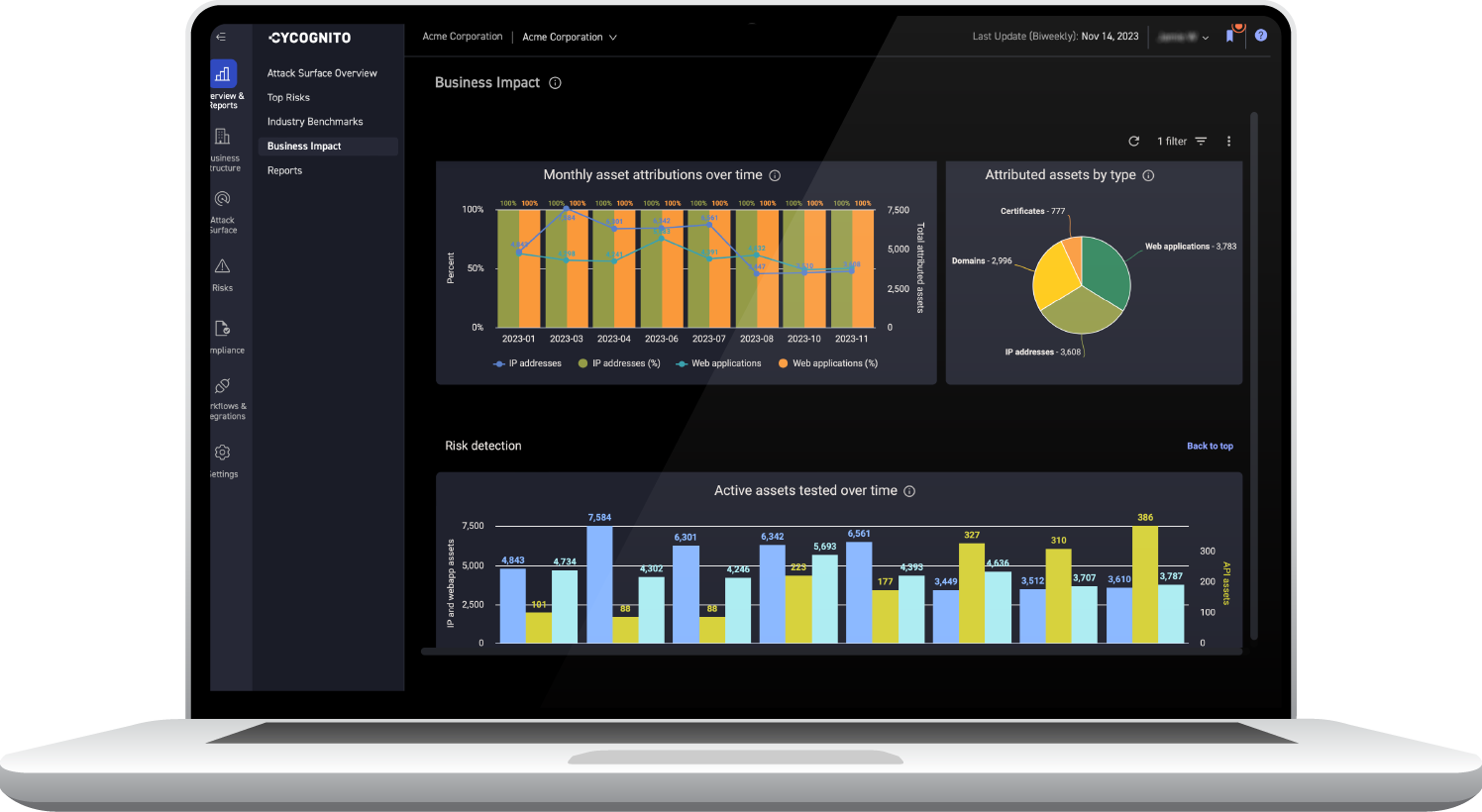
Identify all your organizational owners and classify all assets in order to close knowledge and record-keeping gaps and provide business context for potential risks.
Payload-based active security testing provides the accuracy and precision required to remediate confidently and reduce risk.
Identify your most immediate security challenges and provide a focused strategy on how to address them effectively.
Streamline remediation on vulnerable assets by sending activity and evidence flows directly to remediation tools and teams. Reduce validation time from months to hours.
See how our discovery engine uses graph data modeling to map your organization’s full attack surface. Review our core capabilities, key features and what differentiates us from legacy security tools.
In seconds, see the results of CyCognito’s built-in dynamic application security testing (DAST) and experience the accelerated response only CyCognito Automated Security Testing can provide.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
By clicking submit, I acknowledge receipt of the CyCognito Privacy Policy.
Click below to access your copy of the "Operationalizing CTEM With External Exposure Management" white paper.
Read the White Paper
CTEM breaks when it turns into vulnerability chasing. This whitepaper gives a practical starting point to operationalize CTEM through exposure management, with requirements, KPIs, and where to start.