



An attack surface is the sum of an organization’s attacker-exposed IT assets, whether these digital assets are secure or vulnerable, known or unknown, in active use or not, and regardless of IT or security team awareness of them.
An organization’s attack surface changes continuously over time, and includes digital assets that are on-premises, in the cloud, and in subsidiary networks, as well as those in third-party vendors' environments. Due to this complex web, cyber asset attack surface management tools are becoming more critical.
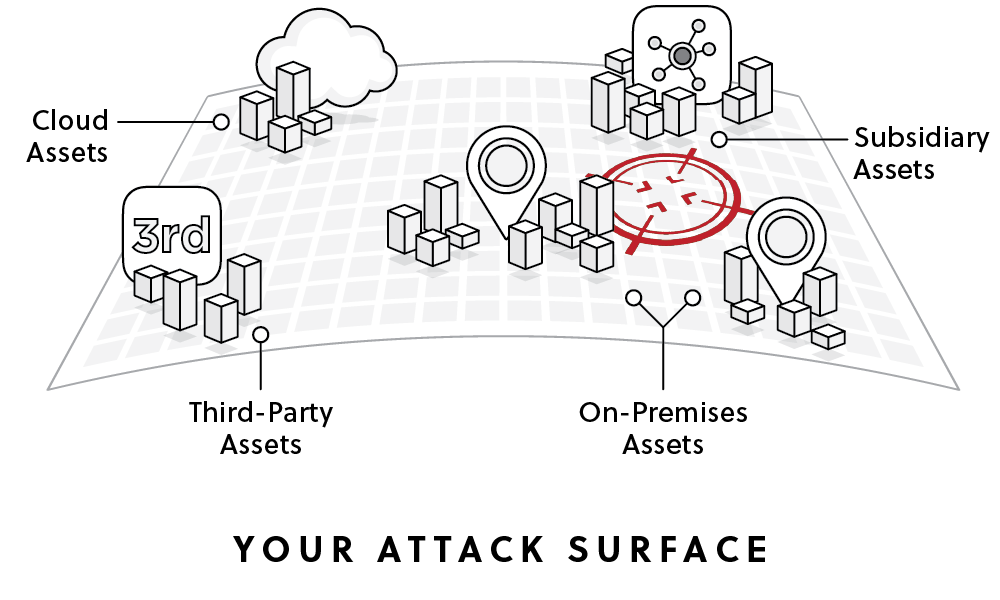
Attack surface management (ASM) is the process of continuously identifying, analyzing, prioritizing, remediating, and monitoring an organization's cybersecurity vulnerabilities and potential attack vectors. The goal of ASM is to reduce the number of options hackers have to breach a network perimeter by keeping the attack surface minimal.
This vital risk management process is now being aided by various attack surface management solutions available in the market.
With the rush to digital transformation, your attack surface has both grown exponentially and become immeasurably harder to define and defend. Add to that the rise in cyberattacks and breaches, and it’s evident why continuous attack surface management is imperative.
Effective attack surface monitoring and management is a process that enables you to continuously discover, classify and assess the security of your IT ecosystem. Attack surface management activities can be broadly divided into two categories:
You don’t have to look far to find stories about the danger of ever-growing attack surfaces.
Take the SolarWinds attacks in which malware was introduced via organizations’ supply chains, routes that are often overlooked on the assumption that they are implicitly secure. This exploit continues to turn up victims, including the email systems of government and international aid agencies that have been critical of the alleged perpetrators.
Another oft-forgotten attack vector is out-of-date software and hardware that is still in use, such as the exploited remote code execution vulnerabilities that have existed on Microsoft Exchange servers as far back as 2010. Remote code execution vulnerabilities were also exploited in attacks against Accellion customers using the company’s legacy File Transfer Appliance (FTA).
Ransomware, as demonstrated by the Colonial Pipeline attack, is another example. The attack targeted remote services such as Citrix, Remote Desktop Web (RDWeb), or remote desktop protocol (RDP) to initially gain unauthorized access. Because organizations are working with largely-remote workforces due to the pandemic, the timing couldn’t have been worse.
In each of these breaches, attackers made their way in through a route that was either unknown by security or considered unimportant. Given the vast number of devices and services spanning your enterprise, it is easy to see how something could be overlooked, especially if you are examining your attack surface from the perspective of most security teams– that is to say, the inside out.
Why organizations turn to attack surface management:
ASM is a continuous process that involves the following steps:
Discovering all the assets within an organization that could be potential targets for cyberattacks. This includes everything from on-premises servers and databases to cloud services, third-party vendor systems, and even shadow IT assets that might be unknown to the IT department. Comprehensive identification requires the use of automated tools that scan for known assets and perform deep discovery to find unknown or forgotten assets.
Once assets are identified, the next step is to analyze them for vulnerabilities and potential attack vectors. This involves assessing the security posture of each asset, identifying outdated software, misconfigurations, open ports, and other vulnerabilities that could be exploited by attackers. Analysis tools use threat intelligence feeds and vulnerability databases to identify known vulnerabilities.
Not all vulnerabilities pose the same level of risk. Prioritization involves evaluating the identified vulnerabilities to determine which ones need immediate attention based on the potential impact and likelihood of exploitation. This step typically uses risk scoring frameworks such as CVSS (Common Vulnerability Scoring System) or Exploit Prediction Scoring System (EPSS), using factors like asset criticality, exposure level, and the presence of active exploits in the wild.
Taking steps to fix the identified issues. This can include applying patches, changing configurations, decommissioning outdated systems, or implementing additional security controls. The goal of remediation is to reduce the attack surface by addressing the most critical vulnerabilities first, reducing the risk of a successful attack.
Ensures that the attack surface is continuously scrutinized for new vulnerabilities and changes in the IT environment. This involves continuous scanning, real-time alerting, and regular reassessment of assets and their security postures. Ongoing monitoring helps in maintaining a dynamic view of the attack surface and quickly addressing any emerging threats or vulnerabilities as they arise.
The expansion of an organization's attack surface continues to present a critical business challenge. Download the GigaOm Radar for Attack Surface Management to get an overview of the available ASM solutions, identify leading offerings, and evaluate the best solution for you.
Here are some of the challenges involved in managing an organization’s attack surface.
As organizations adopt new technologies, the volume and variety of assets that need to be managed and secured is growing. This includes cloud services, IoT devices, remote workforces, and third-party integrations, each introducing new vulnerabilities and adding complexity to the security posture.
The external attack surface of an organization includes all the IT assets and resources that are accessible over the internet. This includes not only websites, web applications, and cloud services but also exposed APIs, remote access points, and email systems.
As businesses increasingly operate online and move more services to the cloud, the external attack surface expands, introducing new points of vulnerability that can be exploited by cybercriminals.
Unknown IT assets are often added to the networks without proper oversight or documentation. This includes the concern of unauthorized cloud services or applications, known as Shadow IT. Unknown assets increase the organization's exposure as they may not be subject to regular security policies and practices.
New technologies often come with new types of vulnerabilities, and attackers are constantly evolving their tactics to exploit these weaknesses. The challenge for organizations is to stay ahead in this arms race by continuously updating their ASM processes and tools to detect and mitigate these evolving threats.
Effective attack surface management is a continuous, five-step process used to keep your organization up-to-date with the most important attack vectors.
You can’t manage an asset if you don’t know it exists. Most enterprises have a surprising variety of “unknown unknowns,” such as assets housed on partner or third-party sites, workloads running in public cloud environments, IoT devices, abandoned or deprecated IP addresses and credentials, services enabled by Shadow IT, and more. Legacy tools and processes can easily miss these attack surface assets, but they can be found quickly by a modern attack surface management program and solution using the same sophisticated reconnaissance techniques as attackers.
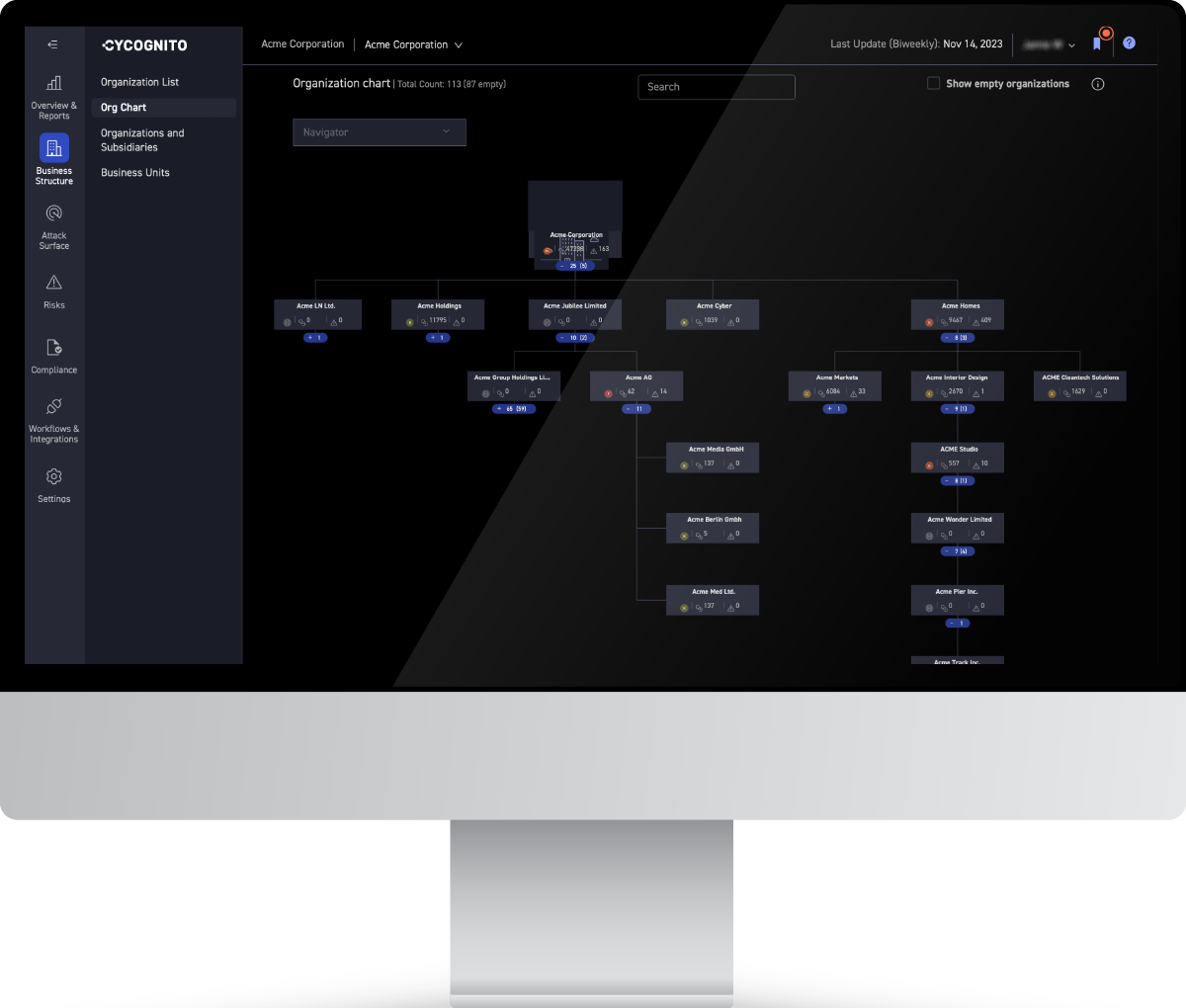
Because not all attack vectors are created equal, business context and ownership are vital parts of attack surface management. However, legacy tools and processes don’t typically provide context in a consistent way, making it difficult to prioritize fixes. An effective attack surface management approach requires information such as IP address, device type, whether it is in current use, its purpose, its owner, its connections to other assets, and possible vulnerabilities contained within it. This can help your security team prioritize the cyber risk and determine if the asset should be taken down or deleted, patched, or simply monitored
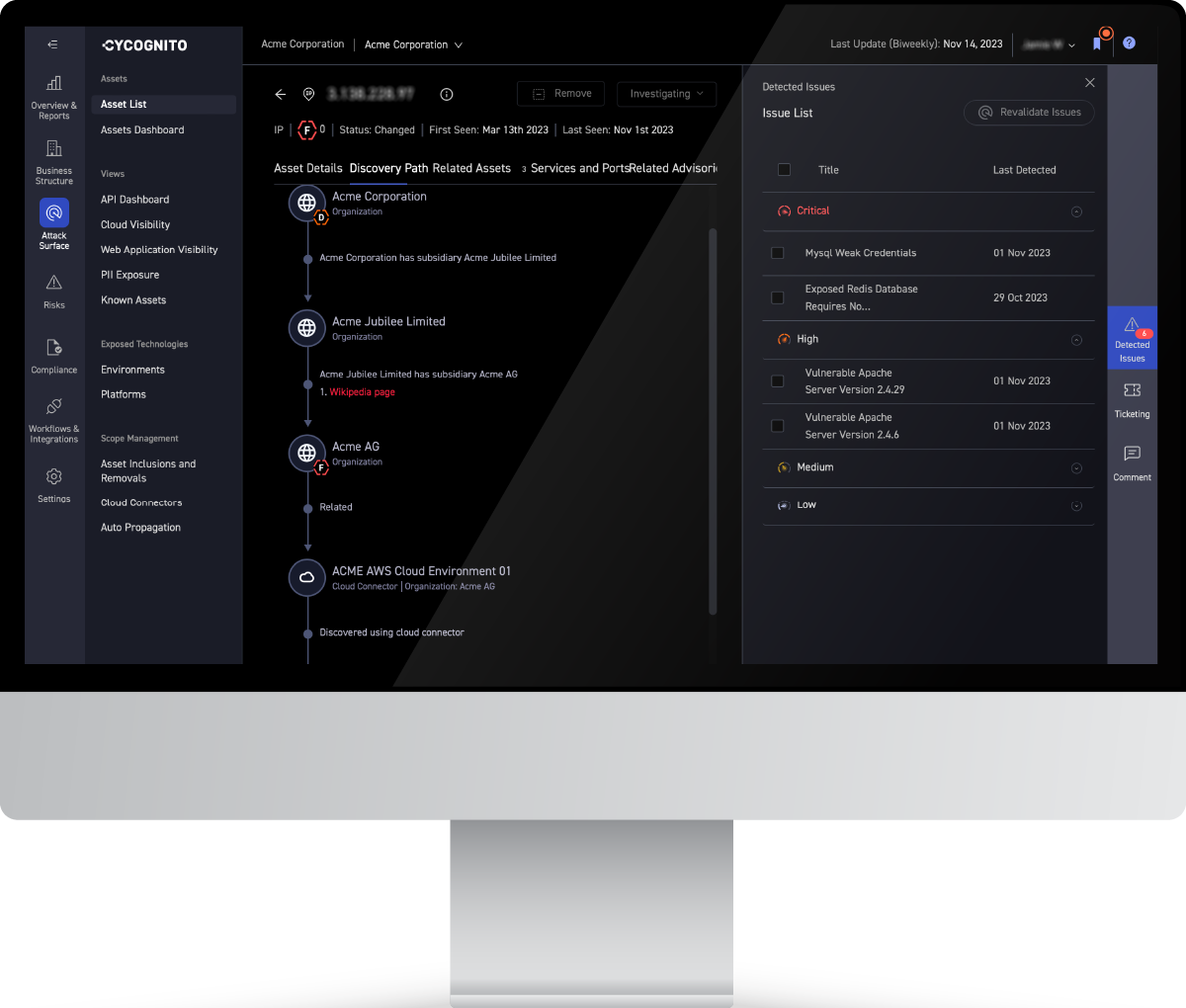
You can’t just superficially test your cyber attack surface once. Every day it continues to grow as you add new devices, users, workloads and services. As it grows the security risk grows too. Not just the risk of new vulnerabilities, but also misconfigurations, data exposures or other security gaps. It’s important to test for all possible attack vectors, and it’s important to do it continuously to prevent your understanding from becoming outdated.
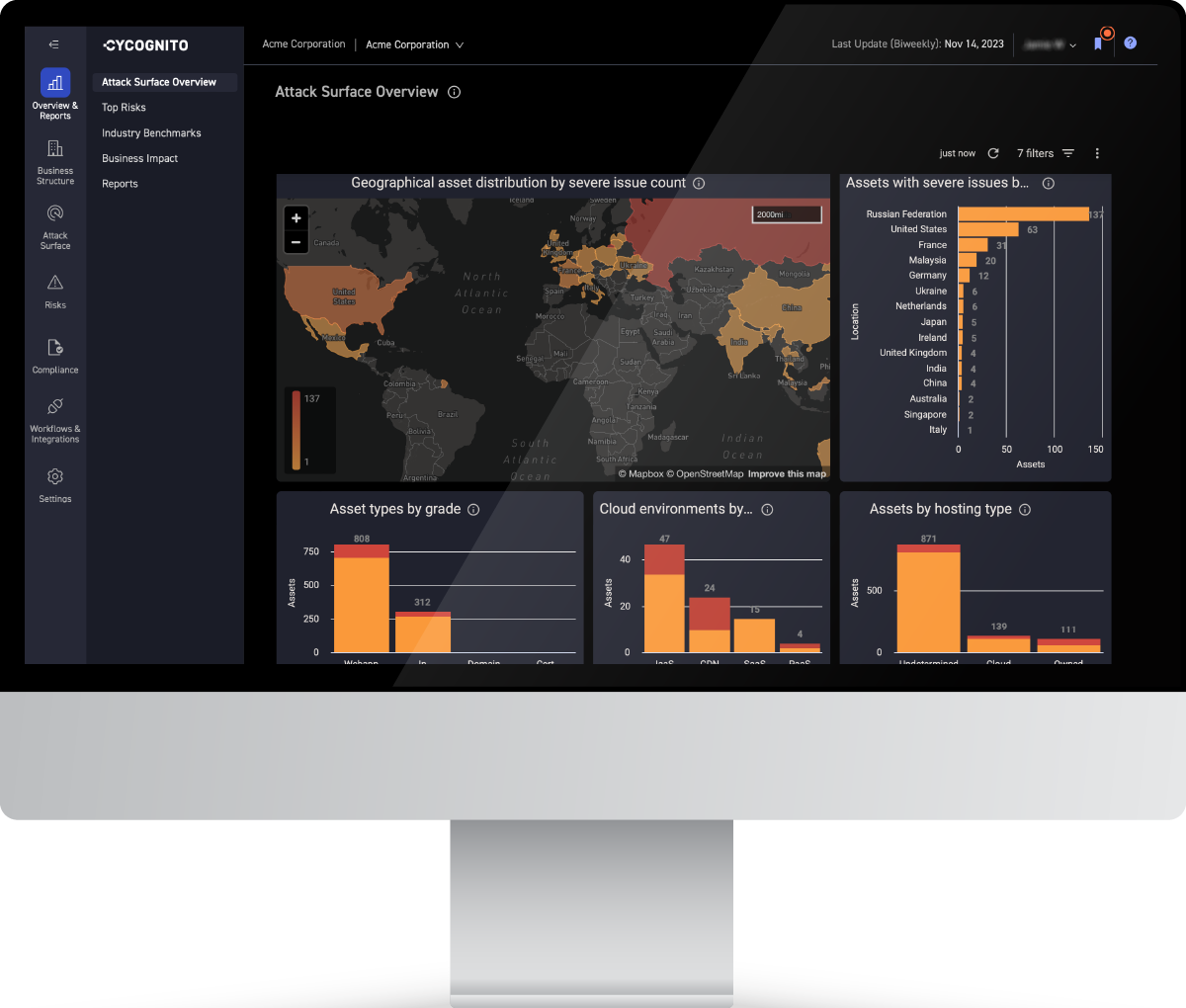
The list of potential attack vectors you discover is almost certain to be more than your security team can validate and your IT team can possibly remediate. That’s why it’s important that you’ve collected all of that context so you can use it to determine where to focus the remediation teams’ efforts. Use of criteria such as ease of exploitation, discoverability, attacker priority and remediation complexity, in addition to business context help ensure you prioritize the most urgent risks
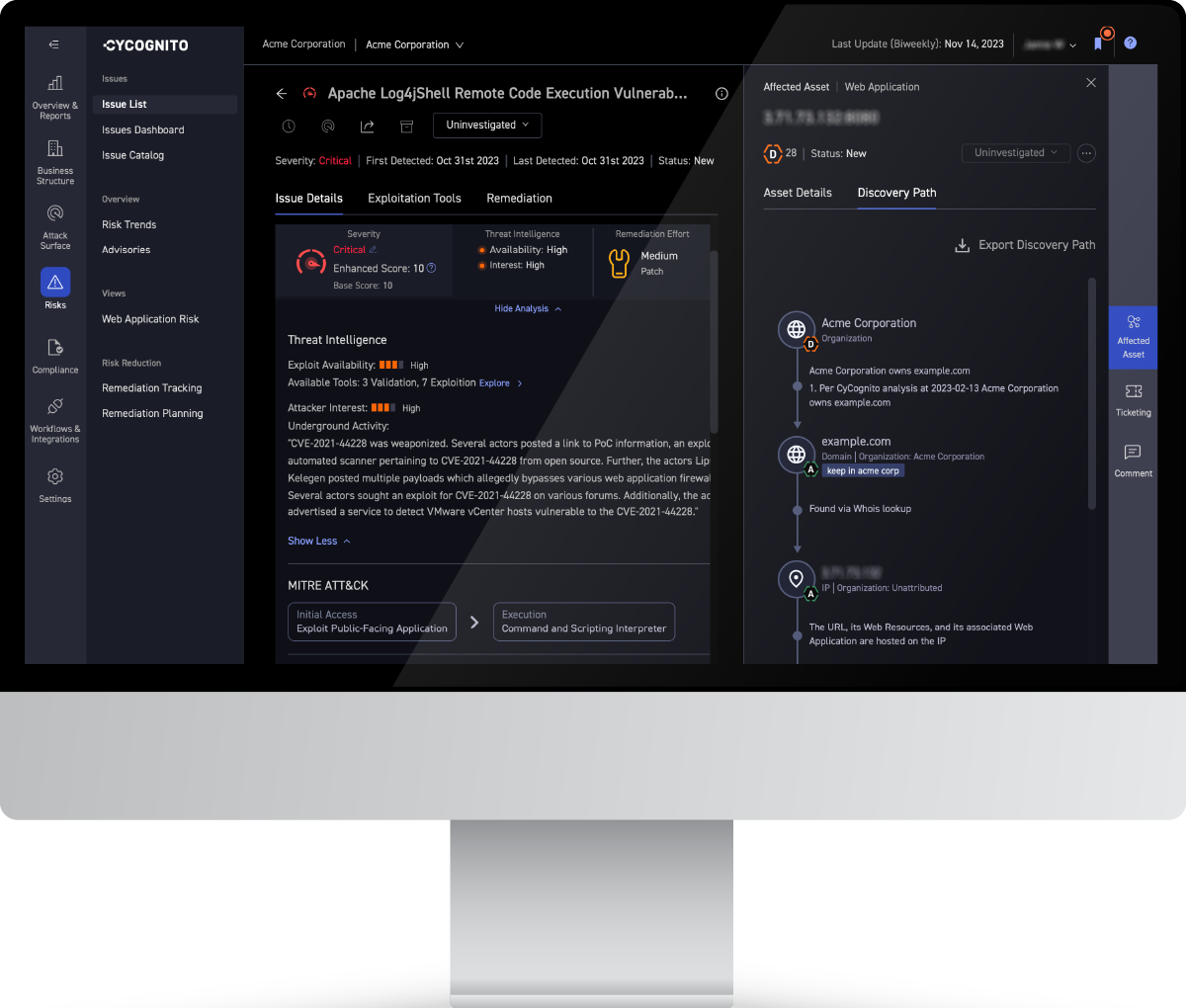
Once your attack surface is thoroughly mapped and contextualized, you can then begin the work of remediation in order of priority. To make your remediation as effective as possible, it’s a best practice to find ways to facilitate (and even automate) information handoff from the tools and teams that understand the risks and their priorities (typically security operations teams) and those teams responsible for doing the work of eliminating them (IT operations teams). Sharing business context and how-to-fix information streamlines the process and helps establish trust.
Download the IDC EASM buyers guide and understand the key capabilities to look for when selecting an External Attack Surface Management solution with expert guidance and selection criteria from analyst firm IDC.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
By clicking submit, I acknowledge receipt of the CyCognito Privacy Policy.
Click below to access your copy of the "Operationalizing CTEM With External Exposure Management" white paper.
Read the White Paper
CTEM breaks when it turns into vulnerability chasing. This whitepaper gives a practical starting point to operationalize CTEM through exposure management, with requirements, KPIs, and where to start.