



The term “attack surface” is sometimes defined as the collection of ways an organization can be breached. But that is really just the sum of your organization’s attack vectors.
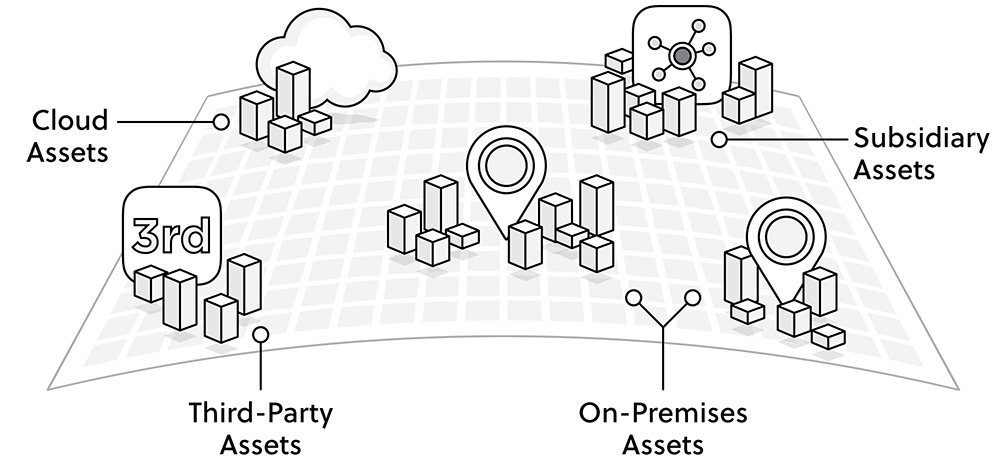
A better definition is: Your attack surface is all of your attacker-exposed IT assets, whether secure or vulnerable, known and unknown, wherever they are: on-premises, in the cloud, in third-party or partner environments, or in the networks of your subsidiaries. That’s a better definition of “attack surface” because organizations benefit from having an understanding and visibility into their entire IT ecosystem that includes all of their network interconnectivity.
One of the most critical security issues today is the fact that IT and security teams don't know where all of their organization’s digital infrastructure and assets are, or whether they’re fully protected. This ‘awareness gap’ is called shadow risk; it’s a major problem, since unknown and unmanaged assets are often the easiest points of entry for attackers.
Organizations must expose their shadow risk by mapping and assessing their full attack surface. Data breaches are a potential risk for modern organizations — and the wider your attack surface, the higher your organization's risk of a data breach.
The need for attack surface analysis and management is universally recognized by security practitioners and vendors, but a critical point that may not be explicitly called out is that managing your attack surface isn’t something you should start doing only after you have implemented your security stack. Instead, it must be a foundational step that guides your security program and resource investments.
Attackers are looking for the path of least resistance in your attack surface so that they can break and gain access to your high-value digital assets. To stay ahead, you have to think like an attacker too. That requires ongoing visibility of your attack surface, and there’s only one proven way to establish attack surface visibility: perform reconnaissance across your entire IT ecosystem, adopting an outside-in approach.
With the full view of your attacker-exposed assets, you have a good foundation for evaluating your organizational risk and establishing an effective security program that allows you and your team to focus your resources on eliminating the highest priority risks for your business.
Visibility of your entire attack surface, particularly the unknown, abandoned and unmanaged assets that attackers seek as easy points of entry.
Understanding the business relevance of each asset based on the type of business data stored on the asset and the business functions supported by the applications on the asset.
Knowing which group in your organization owns the asset, what IT environments it is part of, and whether it is part of a partner or third-party network.
Identification and prioritization of potential attack vectors in your attack surface so you know where your team should focus their efforts.
Continuous security monitoring to maintain the full and current view of your attack surface.
“Digital risk and digital trust are dynamic and vary over time based on context. Thus, risk is calculated for vulnerability management on a continuous basis to calculate the risk exposure of an organization. For example, a vulnerability may not be a significant risk today, but it can materialize into a severe risk to an organization overnight. If a continuous risk assessment is not deployed, the organization will miss addressing the risk, resulting in fatal consequences.”

Many authors providing advice on attack surface management use the term “attack surface reduction” and offer tips for reducing the size of an organization’s attack surface. What’s implied in that approach is that the attack surface is being defined as the sum of vulnerabilities, whereas a better approach is to define the attack surface expansively as the collection of all the assets associated with an organization, whether currently deemed vulnerable or not.
Thus, your goal is not to reduce your attack surface but to reduce the attack vectors in your attack surface, beginning with those that pose the greatest risk to your organization.
The CyCognito platform delivers unprecedented attack surface visibility. Organizations using the CyCognito platform find their attack surface is typically 30 to 300 percent larger than previously understood!
The difference in attack surface size is due to the fact that many assets in the attack surface were unknown to the organization's IT and security departments or were unmanaged. This includes cloud environments and applications, third-party networks, partners, subsidiaries and other shadow IT.
Visibility of your entire attack surface is critical to your ability to identify and eliminate your shadow risk, the risk associated with your attacker-exposed assets.
Elimination of shadow risk by illuminating critical blind spots in your attack surface is a goal and an outcome of using the CyCognito platform. The CyCognito platform helps your team filter out the noise resulting from the use of vulnerability scanners which surface an endless stream of potential vulnerabilities that may be rated as “high” or “critical” using the Common Vulnerability Scoring System (CVSS), but do not rise to a priority level for your organization.
Attack vectors identified by the CyCognito platform go beyond known vulnerabilities and isolated CVSS scores and are specific to your organization’s attacker-exposed assets and their business relevance.
| Capabilities for Attack Surface Management Tools (ASM) | Other ASM Vendors | CyCognito |
|---|---|---|
| Scan the internet continuously to discover assets |  |
 |
| Fingerprint assets, identifying services, software, text, graphics, attributes, etc. |  |
|
| Automatically associate assets with your organization and subsidiaries |  |
|
| Determine the business context of assets |  |
|
| Identify attack vectors impacting your assets |  |
|
| Prioritize risk based on context and impact |  |
|
| Prescribe methods to remediate risks |  |
|
| Provide easy-to-understand scoring of security posture and change over time |  |
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.