In our day-to-day work and conversations with security experts, one concern comes up regularly: how consistent is our WAF protection?
Our answer is always the same: not as much as you think.
The truth is that in the case of enterprises, web application firewall (WAF) coverage is rarely uniform. Protection is often a mixed bag of products from different vendors, managed by separate teams, each guarding only part of the attack surface. This makes it hard to be sure that security configurations are consistent, or to know whether any gaps have gone unnoticed.
The problem becomes worse when you consider the role WAFs play in the security stack. By now considered to be the “seat belts” of application security, WAFs are a baseline safeguard, a first line of defense assumed to be in place.
Missing coverage is risky precisely because it breaks this assumption, often leaving high-value assets exposed to credential stuffing, injection attacks, or unpatched vulnerabilities. And of course, one unprotected system can open a path into the network, putting data, services, and trust at risk.
To demonstrate just how often these gaps occur, we analyzed WAF coverage across 500,000 internet-exposed assets from F2000 and F500 enterprises. Our goal was to measure the extent of coverage, identify where gaps remain, and determine whether those uncovered assets create meaningful exposure.
Methodology
This analysis is based on more than 500,000 internet-exposed assets from Forbes Global 2000 enterprises, identified and attributed to their rightful business owners between January 1 and June 30, 2025.
To ensure the results reflect assets of business value, we excluded obvious noise such as parked domains, placeholder welcome screens and pages with default titles. Each asset was then checked for the presence of a web application firewall (WAF), using AI-assisted fingerprinting to identify 150+ distinct WAF technologies and deployment variations.
Assets were further segmented based on whether they contained mechanisms to collect personally identifiable information (PII) — such as login forms, account creation pages, contact forms or checkout pages. Finally, we conducted a manual review of a sample of uncovered assets using traffic volume indicators to assess actual usage and business relevance.
More than half of cloud assets lack WAF protection
The picture our research painted was clear: WAF coverage is far from what organizations assume it to be, even among the kinds of enterprises that should have the resources and processes to manage it consistently.
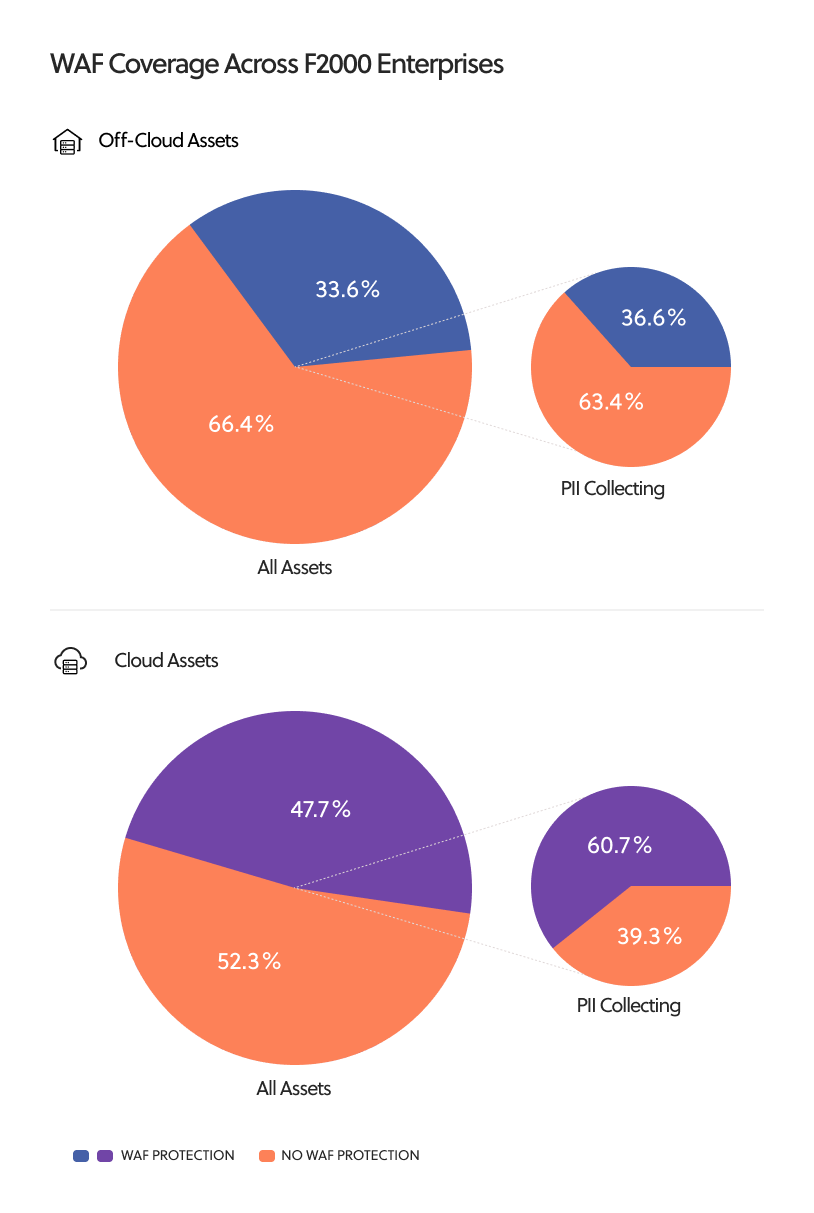
Among cloud-hosted assets, slightly more than half of those in our dataset (52.3 percent) had no WAF protection. For off-cloud assets, the gap was wider still, with two out of three (66.4 percent) uncovered.
Based on our experience, the reasons for these gaps are often rooted in the human and organizational side of security. As described below, many enterprises have multiple WAF deployments from different vendors, each managed by different teams, without a single source of truth to confirm complete coverage. In this environment, it’s easy for certain assets, especially those outside the most visible or centrally managed applications, to slip through the cracks.
There is also the challenge of the “unknown unknowns”: assets that security teams do not realize exist because they are not part of any formal inventory. Without full visibility into the entire attack surface, it is impossible to ensure that every exposed asset is protected, regardless of policy or intent.
For attackers, these uncovered assets offer a direct opportunity to attempt credential stuffing, injection attacks or exploitation of unpatched vulnerabilities, as WAFs are often used as a short-term (or even long-term) safeguard until fixes are in place.
Even PII-collecting assets are left unprotected
Drilling down, we saw that the issue persists on external assets that collect PII data, such as login portals, registration forms, checkout pages or password reset flows. For obvious reasons, these represent some of the most lucrative targets and are often the first surfaces probed during reconnaissance.
Despite focusing on this select subset of pages, we continued to discover significant gaps. In cloud environments, almost four in ten (39.3 percent) of these PII-collecting assets lacked WAF protection. For off-cloud assets, again, the proportion was even higher, with nearly two out of three (63.4 percent) unprotected.
The lack of consistent coverage for PII-handling assets suggests a crucial gap, one that leaves critical resources outside the security perimeter. These gaps are easier to understand when viewed alongside another finding from our study: the sheer number of WAFs most enterprises operate.
Dozen WAF vendors on average...
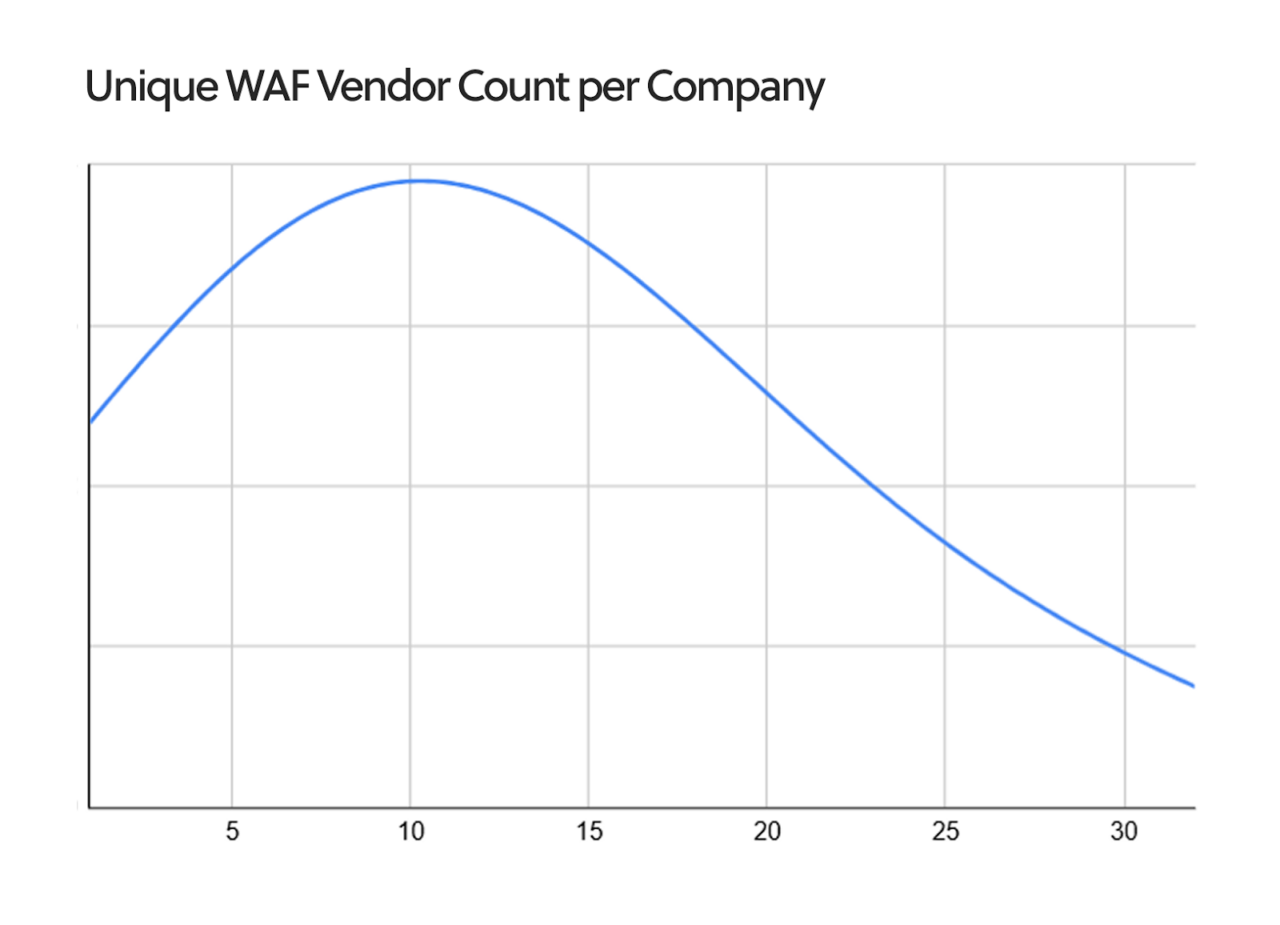
Our analysis of WAF coverage revealed not only widespread gaps, but also the fragmented way enterprises deploy these controls. On average, enterprises in our dataset operated 12 different WAF products (median of 11), with some relying on more than 30. These figures reflect years of overlapping procurement, regional rollouts, and siloed security practices that have accumulated into a sprawling and inefficient mix of technologies.
And of course, this abundance of vendors does not translate into stronger protection. Each WAF carries its own policy model, configuration requirements, and operational quirks. When divided across multiple teams and regions, these differences create a patchwork of defenses that is difficult to coordinate, costly to maintain, and nearly impossible to standardize.
The outcome is the same coverage gaps identified earlier in this study: a high percentage of assets — including those collecting sensitive data — left exposed, not because enterprises lack WAFs, but because fragmented deployment makes consistent protection unachievable.
Deep inspection across a dozen Global Enterprises
Not all unprotected assets pose the same level of danger, which is why we took things a step further and manually analyzed traffic to see which systems were actually in use. This allowed us to separate theoretical risk from genuine operational exposure.
We applied this approach across a dozen of the world’s most iconic enterprises, spanning industries from airlines to retail to financial services and media. What we found was striking: even within these global leaders, multiple high-traffic applications were operating without WAF protection. In several cases, these unprotected assets sat alongside flagship applications that were fully covered—proof that the challenge is not technology, but consistent execution at scale.
This inconsistency makes the risk anything but theoretical. And the fact that these gaps exist within massive, globally impactful organizations underscores just how widespread and consequential the problem really is.
What This Means for Security Leaders
For security executives, these findings serve as a reminder that WAF coverage can vary more than expected. The data shows that gaps are widespread, even among enterprises with significant resources. Leaders should treat this as a call to verify, not assume, that safeguards are consistently in place.
The first step is reviewing the organization’s external asset inventory using black-box discovery tools. This helps uncover shadow IT and “unknown unknowns” that sit outside formal inventories but still expose the business to risk.
Once identified, uncovered assets need to be triaged, either brought under protection or removed if they no longer serve a business purpose. Treating this as an ongoing hygiene effort helps reduce attack surface size while focusing resources where they matter most.
Finally, executives should push for a review of WAF deployment and configuration across teams. Multiple vendors and fragmented ownership create blind spots that can be resolved by improving consistency, consolidating technologies, and aligning on a unified operational standard. Done well, this approach reduces exposure, improves efficiency, and ensures that high-value assets receive the consistent protection they require.



