Update
Fixes and required actions
On December 3 2025, the React team released patched versions of the affected React Server Components packages. Framework vendors, including Next.js, provided updated builds on the same day. Any environment using React Server Components or frameworks that embed the RSC pipeline should:
- Confirm all builds reference the patched versions
- Rebuild and redeploy affected applications
- Review logs from December 3 onward for indicators of scanning or exploitation attempts
CyCognito response
On December 4 2025, CyCognito issued an Emerging Threat Advisory for CVE-2025-55182 (React2Shell) in the platform and prioritized identification of externally exposed assets that may be affected. Customers can use these insights to focus investigation and remediation on the systems most likely to be running vulnerable RSC components.
Evidence of active exploitation
Public confirmation that CVE-2025-55182 (React2Shell) was being exploited in the wild emerged in the days following its disclosure, as cloud providers and security vendors released advisories showing that automated attacks were already underway.
By December 4, fully weaponized public exploits, including a Metasploit module, were available. On December 5, CISA added the vulnerability to its Known Exploited Vulnerabilities list, confirming active exploitation in the wild. Any unpatched externally reachable service should be treated as potentially compromised beginning on December 3.
Cloudflare outage related to mitigations
On December 5 2025, Cloudflare deployed updated WAF request parsing intended to block React2Shell payloads. The change caused a brief global outage at 08:56 UTC and was rolled back within minutes. The outage resulted from the mitigation logic itself rather than an attack.
What is CVE-2025-55182?
CVE-2025-55182, also referred to as React2Shell, is a critical (CVSS 10.0) unauthenticated remote code execution vulnerability in React Server Components (RSC) used in React 19 and multiple frameworks built on top of it, including Next.js 15 and 16.
The issue stems from unsafe deserialization of untrusted payloads inside the RSC Flight protocol. When a malicious request is sent to a Server Function endpoint, vulnerable RSC packages deserialize attacker-controlled input in a way that breaks the intended execution flow. This allows arbitrary JavaScript to run on the server under the privileges of the application.
Affected packages include:
- react-server-dom-webpack: 19.0.0, 19.1.0, 19.1.1, 19.2.0
- react-server-dom-parcel: 19.0.0, 19.1.0, 19.1.1, 19.2.0
- react-server-dom-turbopack: 19.0.0, 19.1.0, 19.1.1, 19.2.0
Even applications that do not explicitly use Server Functions may still bundle these vulnerable components, making this a wide-impact supply-chain risk.
What assets are affected by CVE-2025-55182?
This vulnerability affects any application using React Server Components in the impacted versions, including those built with:
- React 19 production builds
- Next.js 15.x and 16.x (App Router)
- Other frameworks and tools with RSC integration such as React Router (RSC preview), Expo (RSC support), Redwood, Parcel RSC, Vite with RSC plugins, Waku and other experimental RSC frameworks
High-risk external assets include:
- Publicly accessible web applications built with React or Next.js
- SaaS environments processing sensitive or regulated data
- Cloud workloads where application servers can reach internal APIs, secrets or management interfaces
- Shadow IT or experimental deployments that were never fully onboarded into security programs
Because RSC dependency chains often sit deep within frameworks, organizations frequently discover affected assets only through external discovery or dependency analysis.
Are fixes available?
Yes. Patches are available and should be applied immediately.
The React team released fixed versions of all affected RSC packages:
- react-server-dom-webpack: 19.0.1, 19.1.2, 19.2.1
- react-server-dom-parcel: 19.0.1, 19.1.2, 19.2.1
- react-server-dom-turbopack: 19.0.1, 19.1.2, 19.2.1
Next.js also published patched releases for the related CVE-2025-66478, which is rooted in the same underlying RSC flaw.
Organizations should:
- Upgrade all React RSC dependencies to the fixed versions
- Update Next.js or related frameworks to their patched releases
- Update CI/CD pipelines and infrastructure as code templates to prevent re-introducing vulnerable versions
No configuration-only workaround fully removes the RCE risk. Upgrading is essential to address React2Shell.
Are there any other recommended actions to take?
Security teams should immediately:
- Discover and inventory all external React and Next.js applications, including forgotten assets, subsidiaries, cloud accounts and applications deployed outside central IT
- Prioritize assets by exposure and business impact, moving customer applications, authentication portals, PII-processing systems and administrative interfaces to the top of the remediation queue
- Deploy compensating controls while patching rolls out, such as WAF rules targeting malformed or suspicious RSC Flight payloads, tighter access controls for internal or administrative routes and stricter least privilege around backend systems that interact with these applications
- Monitor for indicators of exploitation, including spikes in traffic to RSC endpoints, unexpected process execution and unusual outbound network activity
- Update SBOMs and dependency management so that future builds cannot silently reintroduce vulnerable versions
Is CVE-2025-55182 (React2Shell) being actively exploited?
Yes. As of early December 2025, React2Shell is being actively exploited. Indicators include:
- Public PoC exploit code and weaponized modules are available
- Researchers have demonstrated reliable remote code execution in controlled environments
- Multiple advisories and threat intelligence feeds confirm scanning and exploitation attempts in the wild
- CISA has added CVE-2025-55182 to its Known Exploited Vulnerabilities catalog
Given the simplicity of the payload and the large footprint of React and Next.js, organizations should assume exploitation will spread quickly and treat unpatched assets as at meaningful risk.
What our data shows about exposure patterns
In our recent analysis of externally exposed assets, we found that roughly 18 percent were running vulnerable React Server Components affected by CVE-2025-55182 (React2Shell).
When looking across industries, exposure is not evenly distributed. Media organizations account for roughly 40 percent of the exposed assets in our dataset, followed by manufacturing at about 16 percent and professional services at around 10 percent. Technology, public sector environments and hospitality each contribute a smaller but still meaningful share, with the remainder spread across finance, healthcare, retail and other sectors.

A likely reason media organizations lead is how their frontend stacks use React. They rely heavily on server rendered frameworks such as Next.js to run public entry points like homepages, article and video pages, section fronts, search results and campaign microsites.
In many of these applications, React Server Components are used for server side data fetching, layout composition and streaming partial page updates. That puts the vulnerable react-server-dom-* packages directly in the request path on exposed web assets.
Further analysis showed that across the assets vulnerable to CVE-2025-55182 (React2Shell), roughly 63 percent sit behind a WAF, about 33 percent have no WAF, and just over 4 percent both lack WAF protection and collect PII.
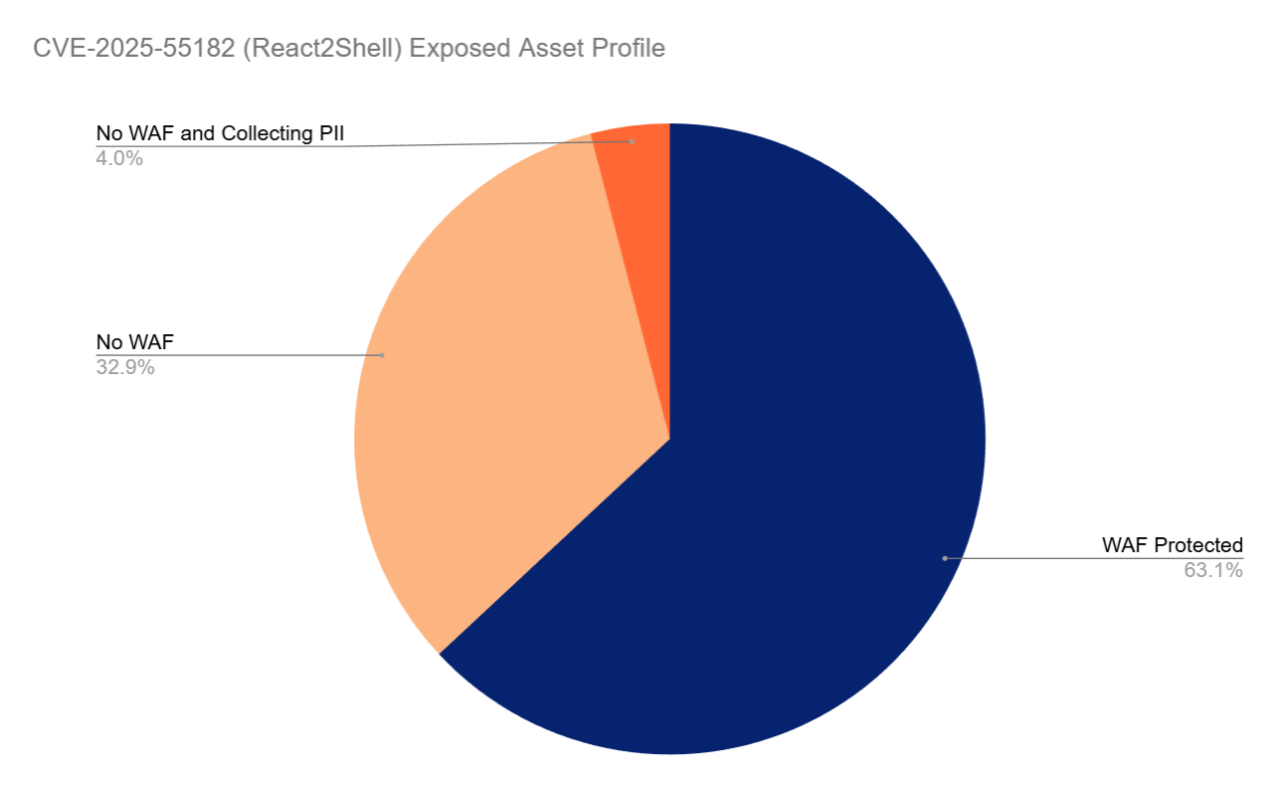
Patching the underlying React Server Components is the only way to eliminate React2Shell risk. However, the presence of a WAF can help block exploit attempts and buy defenders more time.
Assets without a WAF are fully exposed to any scanner or exploit kit, which increases the likelihood of opportunistic compromise during the patch window. Most importantly, the small set of assets that both lack WAF protection and handle PII should be treated as the highest priority, because they combine remote code execution risk with direct access to sensitive data.
How is CyCognito helping customers identify assets vulnerable to CVE-2025-55182?
CyCognito published an Emerging Threat Advisory for CVE-2025-55182 (React2Shell) inside the platform on December 4 2025 and is actively researching enhanced detection capabilities for this vulnerability. The platform already surfaces externally exposed assets tied to this technology stack, helping customers quickly understand whether React Server Components or related frameworks appear in their environment.
CyCognito also advises customers to review any systems running React, Next.js, Apache Tomcat or associated web services to assess potential exposure, even if those assets are not explicitly identified as running vulnerable versions. Modern applications often contain transitive dependencies that teams may not be aware of, and CyCognito external discovery brings these systems into visibility.
Check out the CyCognito Emerging Threats page for updates on this and other high-impact vulnerabilities.
How can CyCognito help your organization?
CyCognito gives security teams a clear view of every external asset, including systems they may not know exist. That visibility makes it easier to find applications built on React, Next.js and other components tied to CVE-2025-55182, and to understand which ones are both vulnerable and externally exposed. Instead of working through large, noisy alert lists, teams see which systems matter most based on business impact, sensitivity and real-world exploit paths.
CyCognito also helps verify that the issue is fixed and continues monitoring for changes as environments evolve. If a previously internal system becomes externally reachable, or if a vulnerable framework appears in a new build, the platform flags it before attackers find it. This allows organizations to move faster, reduce real risk with confidence and stay ahead of attackers instead of responding after the fact.
To learn more CyCognito, schedule a tech demo here to see it in action.



