CVE-2026-1731 is a vulnerability disclosed in products developed by BeyondTrust. At the time of writing, publicly available technical details regarding the root cause, vulnerable code paths, and exploitation prerequisites remain limited. Based on initial advisory information, the issue affects components involved in privileged access or remote access workflows, which are typically deployed to manage high-value credentials, session brokering, or secure administrative access to enterprise systems.
Although the precise vulnerability class has not been fully detailed, the impact profile suggests that successful exploitation could enable unauthorized access, privilege escalation, or manipulation of authentication or session controls. In products designed to centralize and protect privileged credentials, such weaknesses materially increase organizational risk because they sit at a control plane layer. Any compromise of this layer can provide attackers with indirect access to downstream infrastructure, including servers, network devices, cloud consoles, and critical business applications.
From an attacker’s perspective, externally accessible administrative portals, API endpoints, or remote access gateways represent attractive entry points. If CVE-2026-1731 can be triggered without prior authentication or with low-privilege credentials, it would significantly reduce the barrier to initial compromise. Even if authentication is required, exposure of management interfaces to the public internet expands the potential attack surface and increases the likelihood of opportunistic scanning and targeted exploitation.
What assets are affected by CVE-2026-1731?
CVE-2026-1731 affects specific versions of BeyondTrust products. Organizations typically deploy these solutions either as on-premises appliances, virtual appliances, or cloud-hosted instances to manage privileged access, password vaulting, and remote support functions. Assets at risk include internet-facing administrative consoles, remote access gateways, API endpoints, and any externally routable interfaces associated with privileged access management infrastructure.
The highest-risk assets are those directly exposed to the internet without network-level restrictions. In many environments, remote support portals or privileged access gateways are intentionally published to enable third-party vendors or remote administrators to connect from untrusted networks. These deployments frequently sit behind load balancers or reverse proxies, which can obscure asset ownership and complicate inventory tracking. As a result, security teams may underestimate the number of exposed instances or overlook non-production systems that remain reachable from the public internet.
Additionally, organizations with decentralized IT operations, mergers and acquisitions activity, or shadow IT patterns may operate unmanaged or legacy instances that fall outside formal patching and vulnerability management workflows. If those instances run affected versions, they represent a materially higher risk because they are less likely to receive timely remediation and may lack compensating controls such as IP allowlisting or multifactor enforcement.
Internal-only deployments are not immune to risk, particularly in flat network architectures. If an attacker gains a foothold through phishing, credential reuse, or exploitation of another internet-facing service, lateral movement toward privileged access infrastructure can enable escalation to domain-wide or enterprise-wide compromise. Therefore, both externally exposed and internally accessible deployments should be considered in scope when assessing risk from CVE-2026-1731.
What does our data show about exposure patterns?
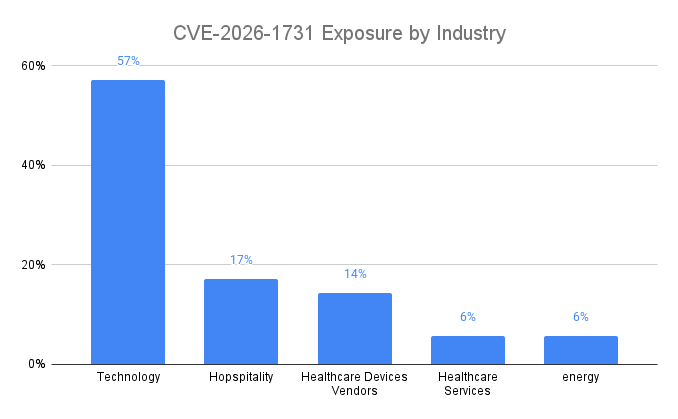
Our external exposure data shows that internet-facing instances are distributed across multiple industries, with the highest observed concentration in the technology sector, followed by hospitality, healthcare device vendors, healthcare services organizations, and energy companies. The technology sector accounts for the largest share of observed exposed instances in this dataset, indicating a higher likelihood of distributed or multi-instance deployments within that vertical.
The presence of exposed instances in hospitality and healthcare-related sectors is operationally significant. These environments frequently rely on third-party vendors and remote administrative access to maintain business systems and, in some cases, connected devices. In healthcare and energy environments in particular, privileged access platforms may sit adjacent to sensitive IT systems that interface with operational or clinical infrastructure. Compromise of the access management layer in these sectors can therefore create indirect pathways to high-impact systems.
Are fixes available?
BeyondTrust has released guidance identifying affected versions and remediation steps. Organizations should review the vendor advisory to determine whether patches, hotfixes, or version upgrades are available for their specific deployment model. In some cases, remediation may require upgrading to a later major or minor release rather than applying a standalone patch.
Where patches are available, prompt application is strongly recommended, particularly for internet-facing systems. If remediation requires downtime or coordinated change windows, organizations should prioritize instances that are externally accessible or that broker high-privilege credentials. If technical details of exploitation remain limited, defenders should assume that reverse engineering of patches may enable rapid weaponization, especially for widely deployed access management platforms.
If immediate patching is not feasible, interim mitigations described by the vendor—such as restricting network exposure, disabling affected components, or enforcing stricter authentication controls—should be implemented while planning a permanent fix.
Are there any other recommended actions to take?
Organizations should immediately inventory all BeyondTrust deployments, verify which instances are internet-facing, restrict public access to administrative interfaces, enforce strong authentication controls including multifactor authentication, and monitor logs for anomalous authentication attempts or configuration changes until remediation is fully implemented.
How can CyCognito help your organization?
CyCognito published an Emerging Threat Advisory for CVE-2026-24858 inside the CyCognito platform on February 2, 2026, and is actively researching enhanced detection capabilities for this vulnerability.
To learn how CyCognito can help your organization reduce external exposure and manage emerging threats more effectively, contact us to request a demo.



