What is CVE-2024-28987?
CVE-2024-28987 is a critical (CVSS v3 score: 9.1) hardcoded credential vulnerability in the SolarWinds Web Help Desk (WHD) software. If exploited, this Java deserialization remote code execution (RCE) vulnerability allows attackers remote unauthenticated access to create, read, update and delete data on specific WHD endpoints.
What assets are affected by this vulnerability?
Web Help Desk is SolarWinds IT ticketing and asset management software. CVE-2024-28987 affects WHD version 12.8.3 HF1, as well as all previous versions.
Is a fix available?
This critical vulnerability was patched by SolarWinds in August 2024. Organizations can patch this vulnerability by upgrading to version 12.8.3 HF2.
Are there any indicators of compromise?
Indicators of compromise (IOCs) can be found in the Web Help Desk log, which records limited details about requests to C:\Program Files\WebHelpDesk\Logs\whd_access_log.<YYYY-MM-DD>.log. If unrecognized IP addresses appear enumerating the OrionTicket endpoints, it may indicate exploitation of the CVE-2024-28987.
Is CVE-2024-28987 being actively exploited?
Initially, although this vulnerability was reported and listed with CISA’s Known Exploited Vulnerability (KEV) catalog as an unauthenticated vulnerability, researchers were not able to replicate the vulnerability without authentication.
On September 25th, Horizon3.ai analyst Zach Hanley published a proof of concept (POC) showing unauthenticated exploitation of this vulnerability. While no attackers have been observed in the wild leveraging this issue, another recently patched SolarWinds WHD flaw, CVE-2024-28986, is being actively exploited.
How is CyCognito helping customers identify assets vulnerable to CVE-2024-28987?
CyCognito customers will see results from active and passive tests for this vulnerability in their next data update. All customers have access to an in-platform emerging security issue announcement as of September 29th, 2024. As of this publication, no vulnerable assets have been detected.
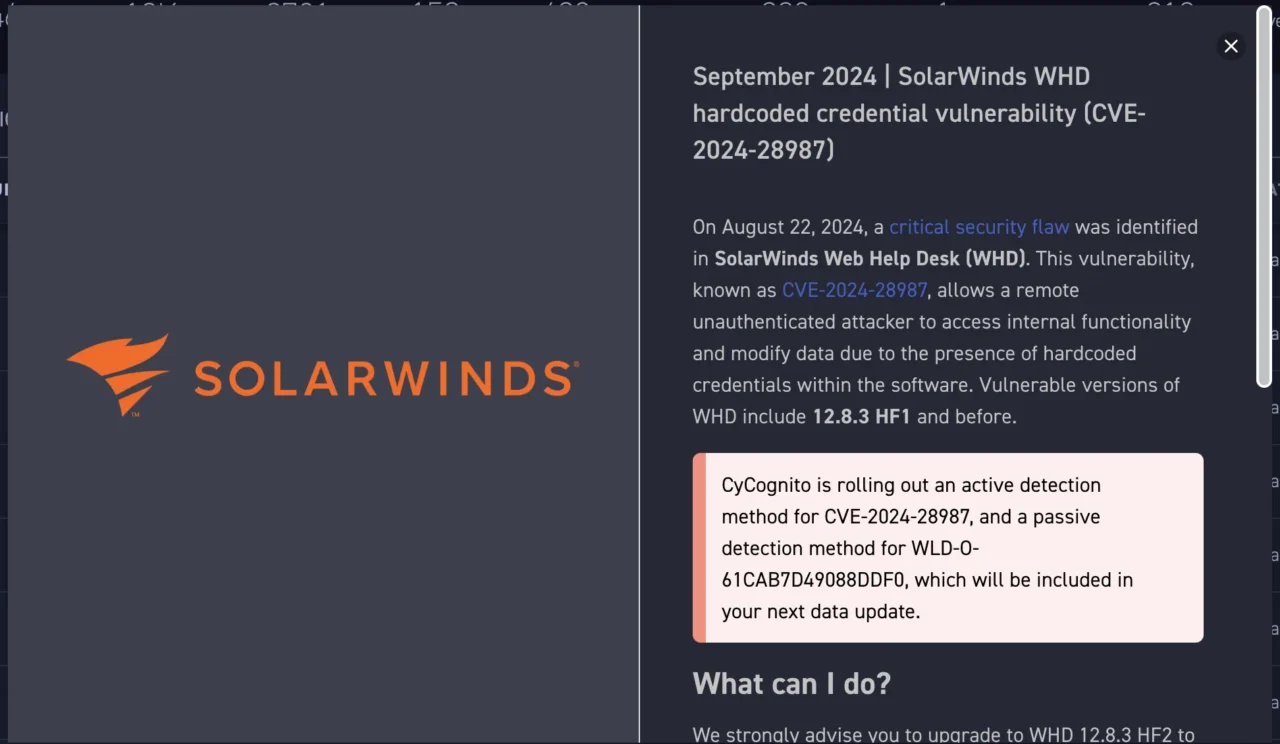
Figure 1: The alert sent by CyCognito for CVE-2024-28987
How can CyCognito help your organization?
CyCognito is an exposure management platform that reduces risk by discovering, testing and prioritizing security issues. The platform scans billions of websites, cloud applications and APIs and uses advanced AI to identify the most critical risks and guide remediation. Emerging companies, government agencies and Fortune 500 organizations rely on CyCognito to secure and protect from growing threats. Want to see how it works? Check out our website and explore our platform with a self-guided, interactive dashboard product tour. To learn how CyCognito can help you understand your external attack surface and exposed risks, please visit our Contact Us page to schedule a demo.



