Web Application Firewalls (WAFs) are the most common protection for web applications. WAFs protect web applications by filtering and monitoring HTTP traffic between the application and the internet. However, WAFs need to be deployed and configured to protect web applications specifically. If they are not, this leaves open a potential route for an attacker.
Gaps in WAF protection are a substantial risk to organizations. According to research by Verizon, web application attacks are involved in 26% of all breaches, making them the second most common attack pattern. CyCognito’s semi-annual State of Exposure Management report reveals the average number of web applications in a large organization is a surprising 12,000. Given the severity of web attacks and the prevalence of web applications, CyCognito recently introduced a feature that discovers if web applications are protected by a WAF, and if so, which one. This post will explain how the feature works and how an organization can use it to prioritize and remediate exposed web applications.
How WAF Detection Works and What WAFs Are Covered
The CyCognito platform can identify over 150 WAFs, including popular ones like Akamai, AWS CloudFront, Azure Front Door, Cloudflare, Fastly, Fortinet, and Imperva. Since CyCognito understands the entire attack surface of an organization, all web applications are probed for WAF protection. Figure 1 below shows all the web applications for Acme Corporation.
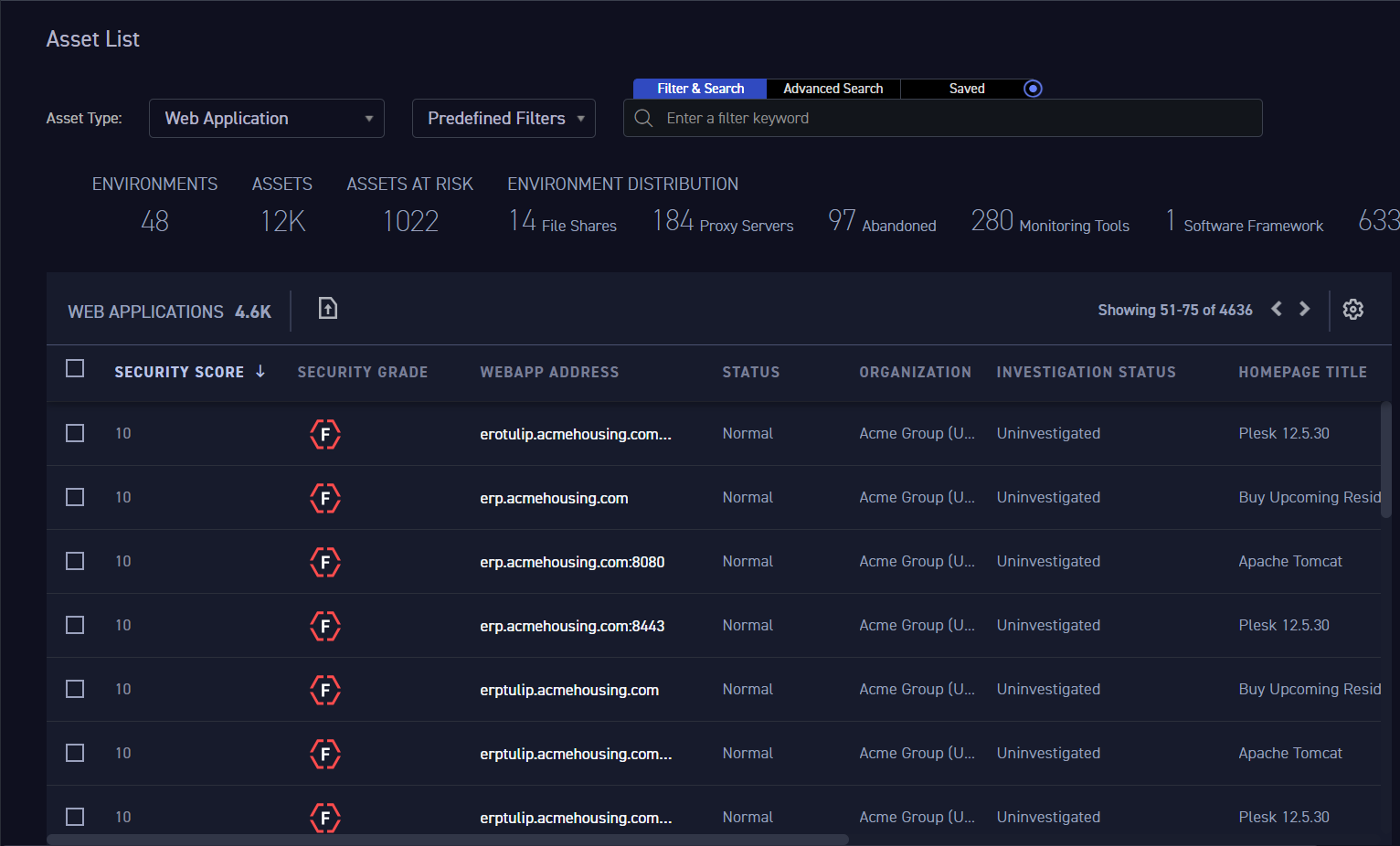
Figure 1: Web applications for Acme Corporation shown in CyCognito
CyCognito detects the presence of a WAF and the type of WAF by sending several HTTP requests to each web application. By analyzing the response from the web application, the CyCognito platform identifies patterns that match known WAFs, such as specific HTTP headers, cookies or HTML content.
If the above is not enough to identify that a WAF is present, or which WAF is present, a series of potentially malicious requests will be sent to the tested target, to attempt and identify the WAF using error messages and behavior of blocked requests. For example, Cloudflare is a great example of a WAF with a very indicative error message and is easily identifiable by its “Sorry, you have been blocked” message.
Taking Advantage of WAF Detection
Users can see both the overall WAF coverage and individual application details in the CyCognito console. There are three main use cases:
- Understanding general WAF adoption - as shown in Figure 2 (below), users can see the total number of web applications that are protected or not protected by a WAF. These can be filtered by risk to give a more meaningful picture of the risk to an organization.
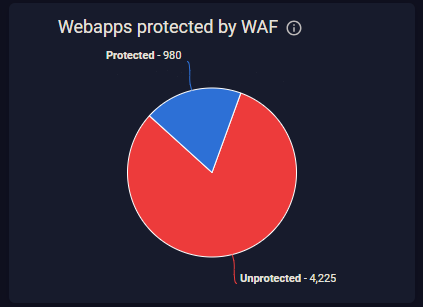
Figure 2: Dashboard report shows that 4225 web applications are not protected by a WAF
- Understanding specific WAF adoption - Security can ascertain which WAFs are in use in their organization. This gives security teams a better understanding of their security controls. For example, they may find one or more WAFs that are not monitored by the security team and may not be compliant with current security policies or regulatory requirements.
- If several different WAFs are in use, it presents an opportunity for consolidation. This may have cost benefits as well as security benefits, as consolidation may simplify the job of the security team.
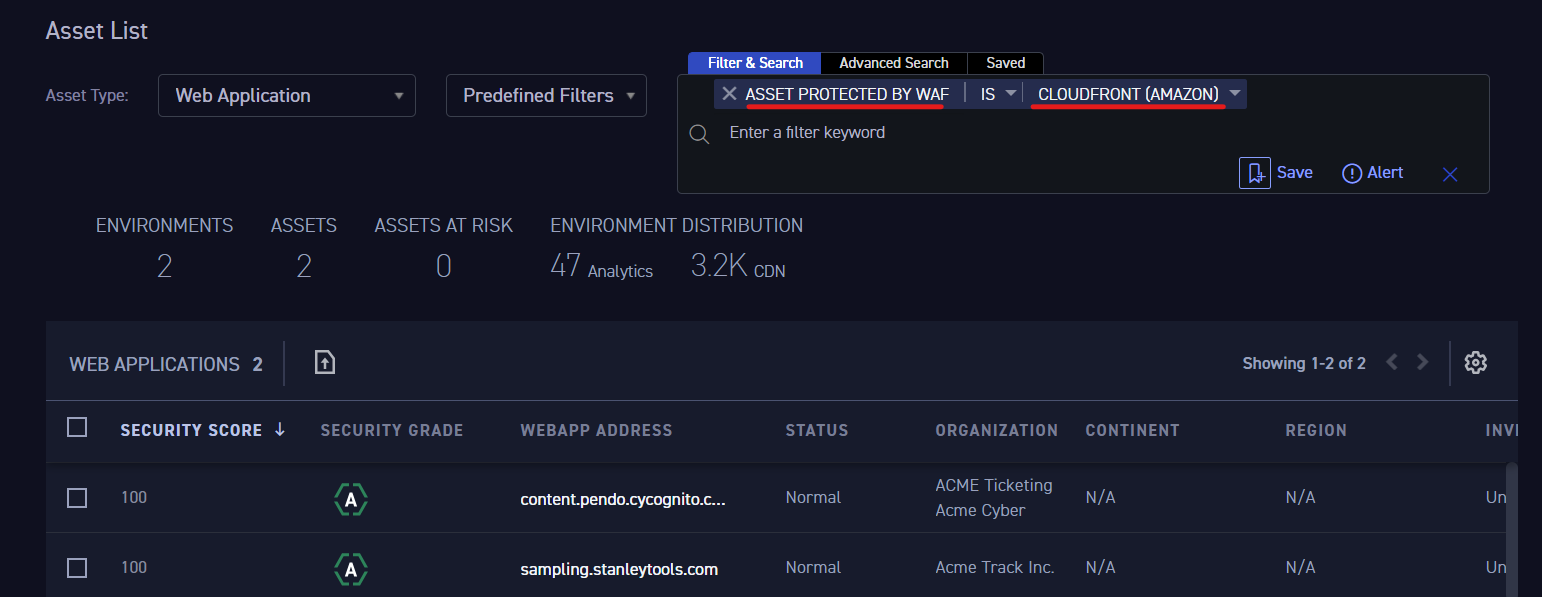
Figure 3: Filtering to show assets protected by AWS Cloudfront.
The functionality is also available via the CyCognito API, allowing Integrations with SIEM, SOAR, ITSM, CMDB, and other types of IT and security products. A common action would be to open a ticket in Jira or ServiceNow and assign it to a security team member for investigation.
The feature is currently available to all CyCognito customers. Simply navigate to the Asset List section (shown above in Figure 3) and you’ll be able to filter out web applications according to which WAF was found to be protecting them. If you are not a CyCognito customer and are interested in a demo, please contact us.



