This one-day event incorporates breakouts with IANS Faculty, spotlight sessions on emerging technologies, and opportunities to network with your peers.
Topics fall into five tracks:
IANS Forum content is geared toward the entire security function. Attendees include but are not limited to CISOs, VPs and Managing Directors of Information Security, Information Security Architects, and Information Security Engineers
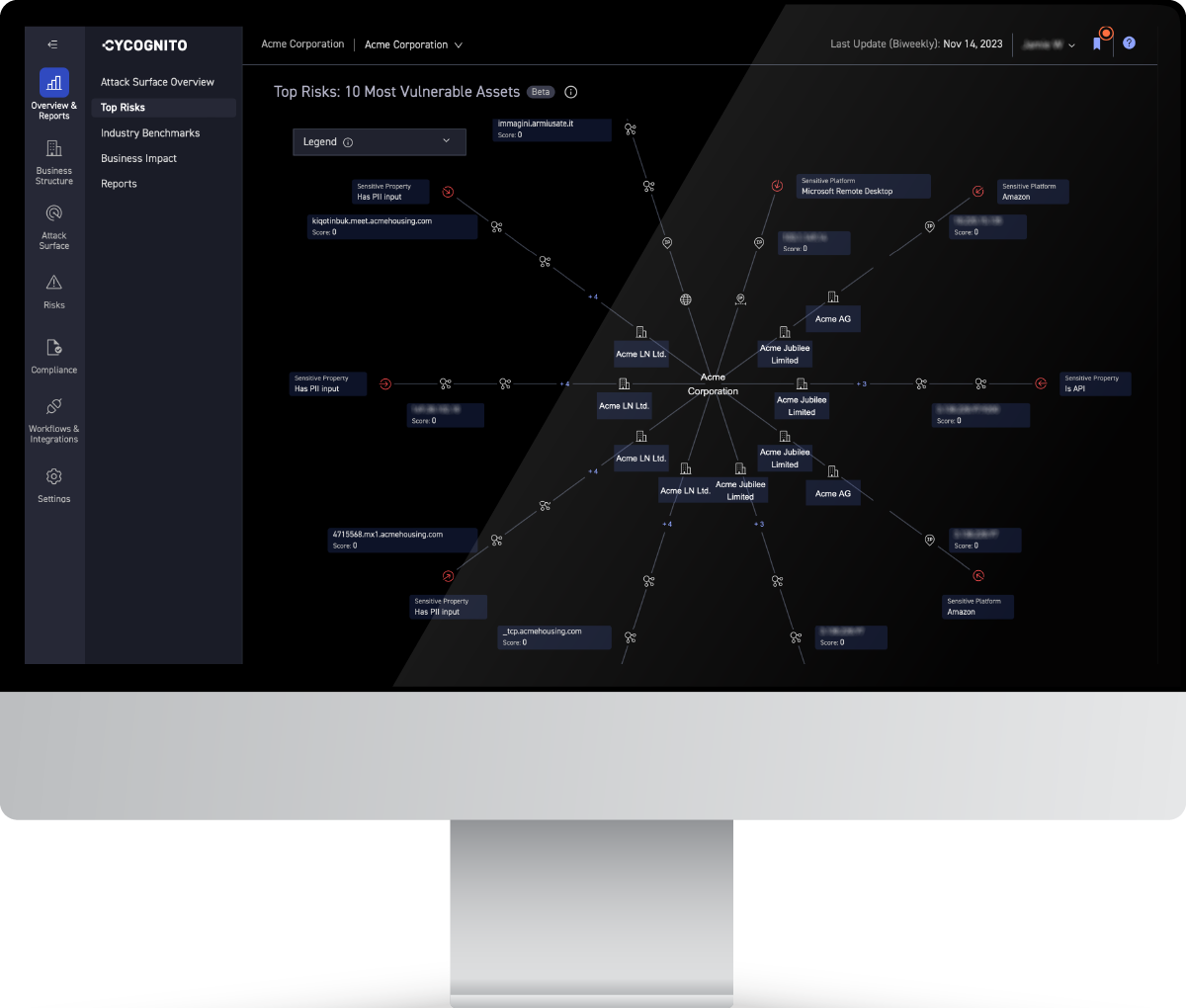
To help you stay one step ahead, CyCognito shows the attackers’ perspective to dramatically reduce overall business risk, increase efficiency and reduce cost. With our platform, security teams know where to focus to eliminate risks, get remediation guidance, and get timely validation of their work.
Request a personalized walkthrough of the CyCognito platform to see how we can help your company identify all its internet-exposed assets, focus on which are most vulnerable to attacks, and accelerate your time to remediating critical risks.