



A key challenge for holding companies, multinational corporations, and other conglomerates is monitoring the IT security risk of their subsidiaries. Subsidiary IT environments contain assets that you don’t manage but that can still put your organization at risk. Unknown and unmanaged attacker-exposed assets in these environments can easily be the source of your organization’s most critical cybersecurity risk.
The CyCognito platform provides an automated, scalable platform that will help you manage and monitor your attacker-exposed subsidiary environments efficiently and effectively.
One of CyCognito's customers, a telecommunications company, deployed a defensive security solution, known as a deception system. The system was misconfigured by the vendor's engineer, exposing the company’s entire management system on the open web.
The CyCognito platform discovered the misconfiguration immediately, enabling the company to resolve the security weak spot before attackers could exploit it.
The CyCognito platform gives you immediate visibility into the entire organization's full scope of its legal entities, brands, and subsidiaries, even uncovering assets they didn’t know existed, and providing the business context of each asset including ownership.
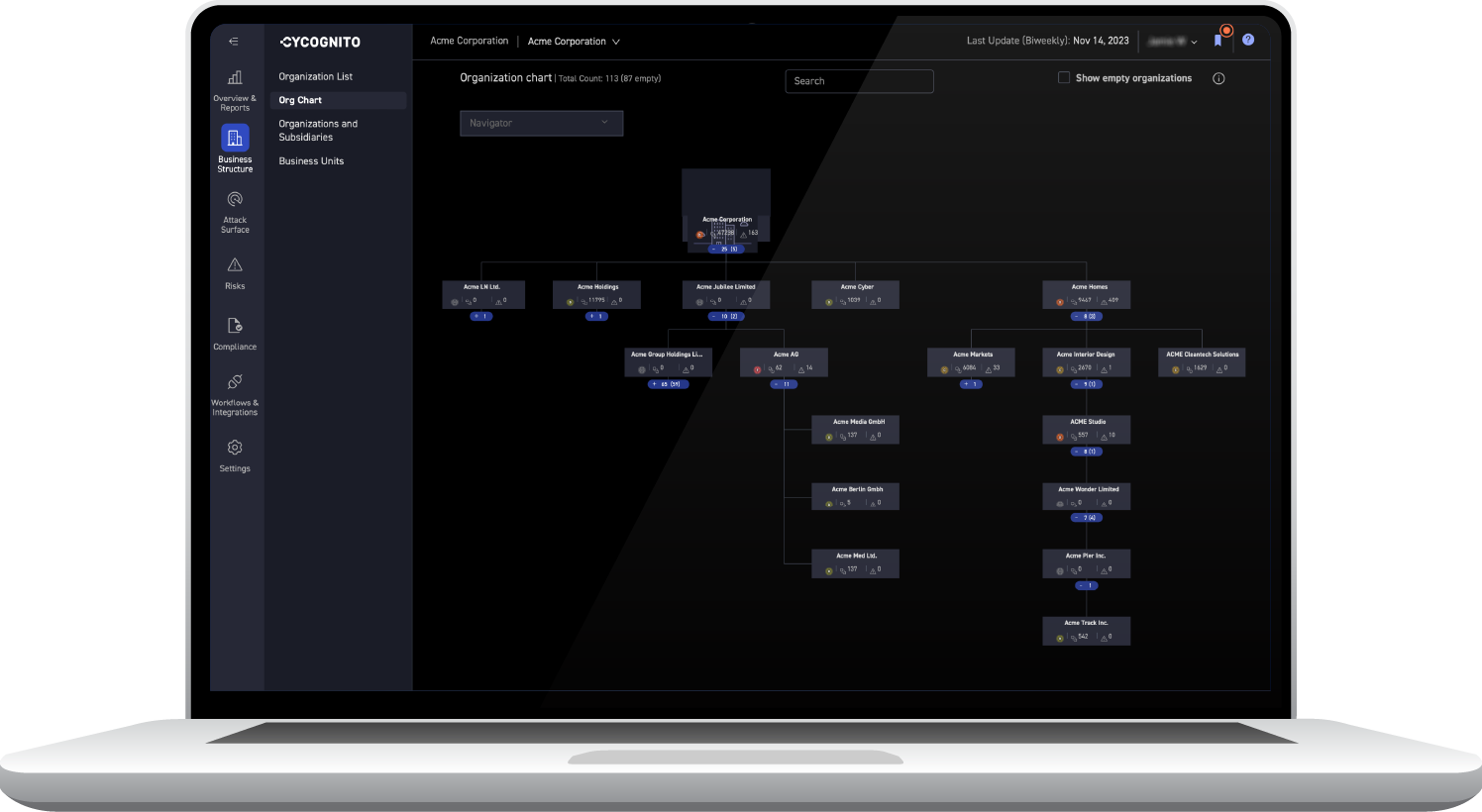
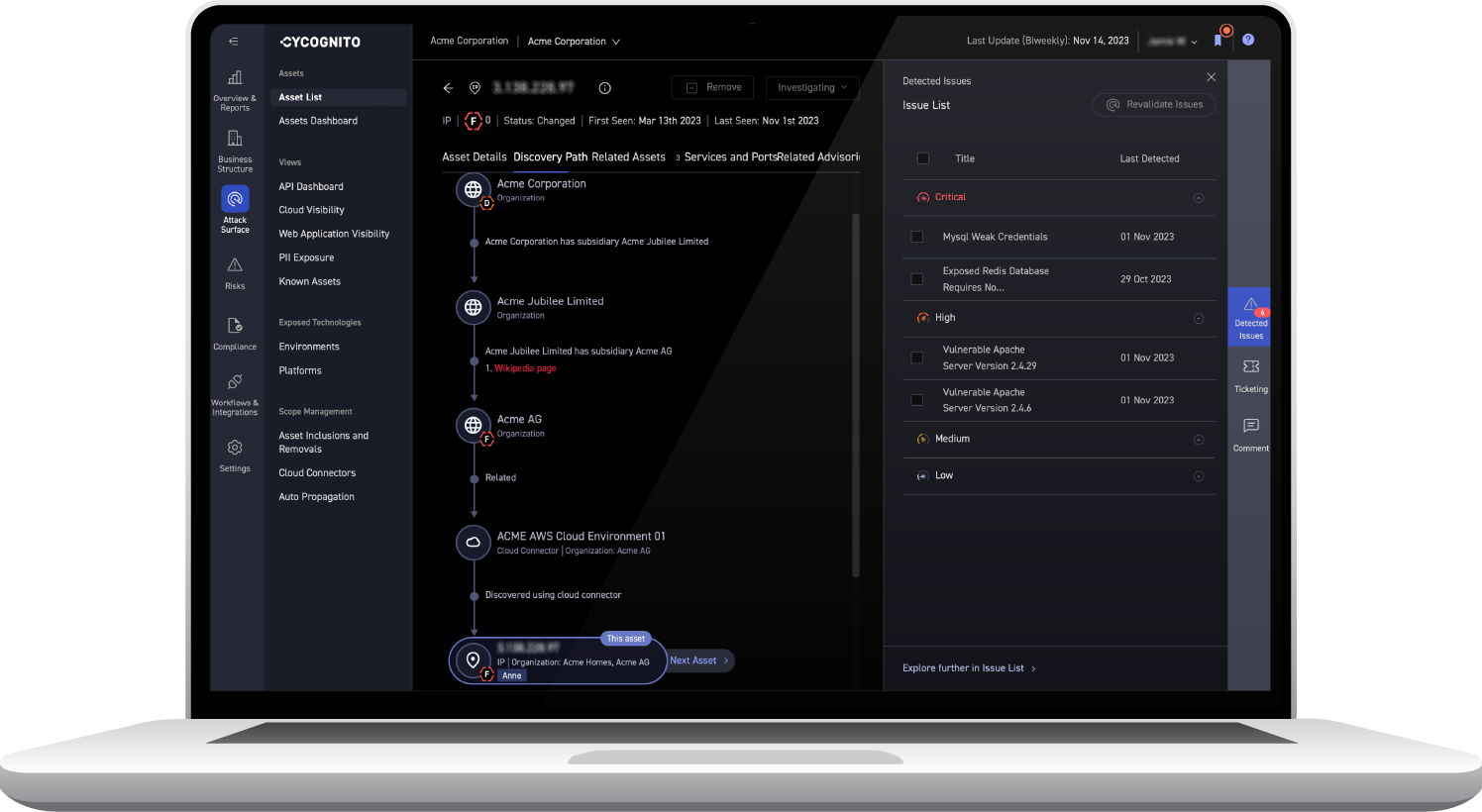
CyCognito objectively measures the risk of each subsidiary and the risk of each asset in its environment by validating evidence across multiple data sources and testing for high accuracy. This evidence includes an exact path of discovery, ownership, and critical issue remediation steps. This validated evidence establishes credibility when working with subsidiaries for remediation.
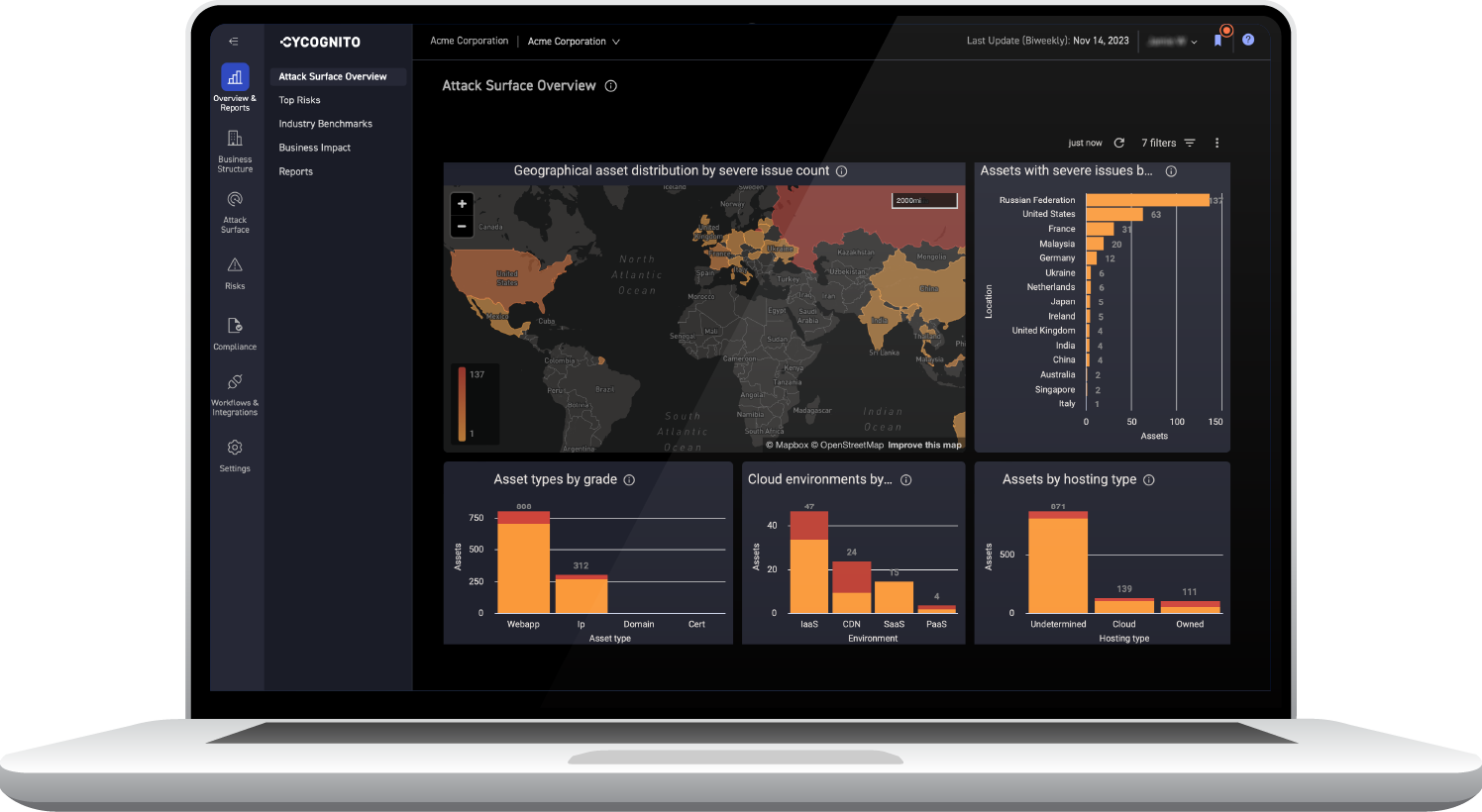
CyCognito provides an automated, scalable platform that needs no deployment or configuration to monitor subsidiaries' attack surface continuously. This is essential for maintaining visibility into the evolving attack surface, allowing the organization's subsidiaries to mitigate security risks and threats.

Benjamin Bachmann | Vice President, Group Information Security