



Attackers are looking for the path of least resistance in your attack surface so that they can break into and access your high-value digital assets.
To stay ahead, you have to think like an attacker too. That requires ongoing visibility of your attack surface, and there’s only one proven way to establish attack surface visibility, and that is to do what attackers do: perform reconnaissance across your company and entire data and IT ecosystem, using an outside-in approach.
With the full view of your attacker-exposed assets, you have a good foundation for evaluating your organizational risk and establishing an effective data security program that allows you and your team to focus your resources on eliminating the highest priority risks for your business.
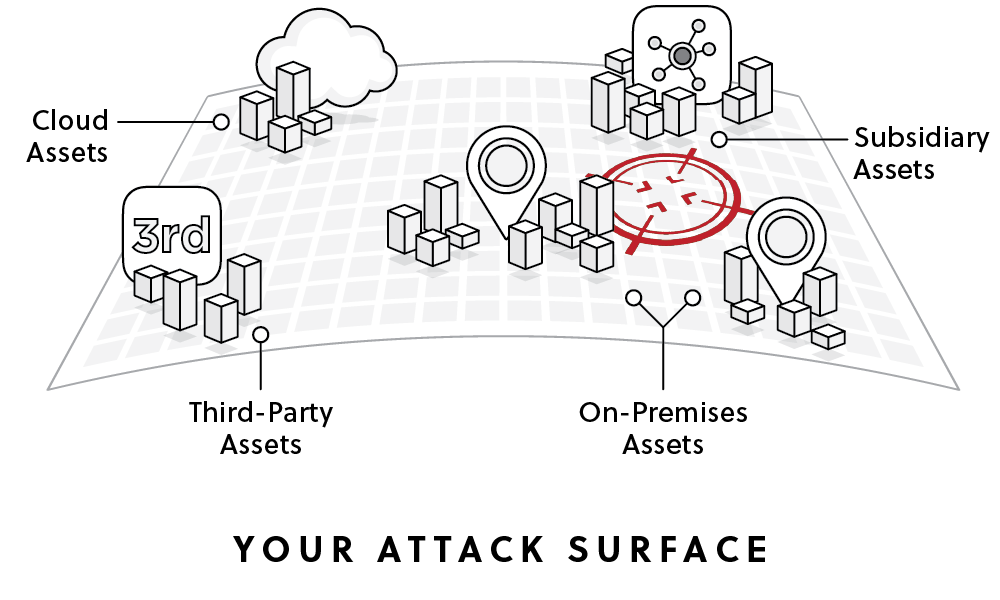
In order to protect your most-valued cloud assets well, you must have visibility across your entire attack surface, right down to the last connected device. Is your visibility up to the task?
Attackers often find your own infrastructure and security blind spots – your shadow risk – by targeting the IT assets connected to your organization that you don't know about or manage: assets in partner, cloud and subsidiary environments.
Your shadow risk goes undiscovered by the legacy security risk assessment solutions you use (e.g. vulnerability scanners) because they were designed for the IT environments of twenty years ago, not the IT ecosystem at the heart of your business today. The same is true of attack surface discovery tools like those from RiskIQ and Expanse, which are simply port scanners working within defined or easily discovered IP address ranges.
Elimination of shadow risk by illuminating critical blind spots in your attack surface is a goal and an outcome of using the CyCognito platform. The CyCognito platform helps the users on your team discover and understand more about your attack surface, and not just discover open ports.
CyCognito platform also filters out the noise resulting from the use of vulnerability scanners which surface an endless stream of potential vulnerabilities that may be rated as “high” or “critical” using the Common Vulnerability Scoring System (CVSS), but do not rise to a priority level for your organization. Attack vectors identified by the CyCognito platform go beyond known vulnerabilities and isolated CVSS scores and are specific to your organization’s attacker-exposed assets and their business relevance.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.