Shutting Down
Rogue Access
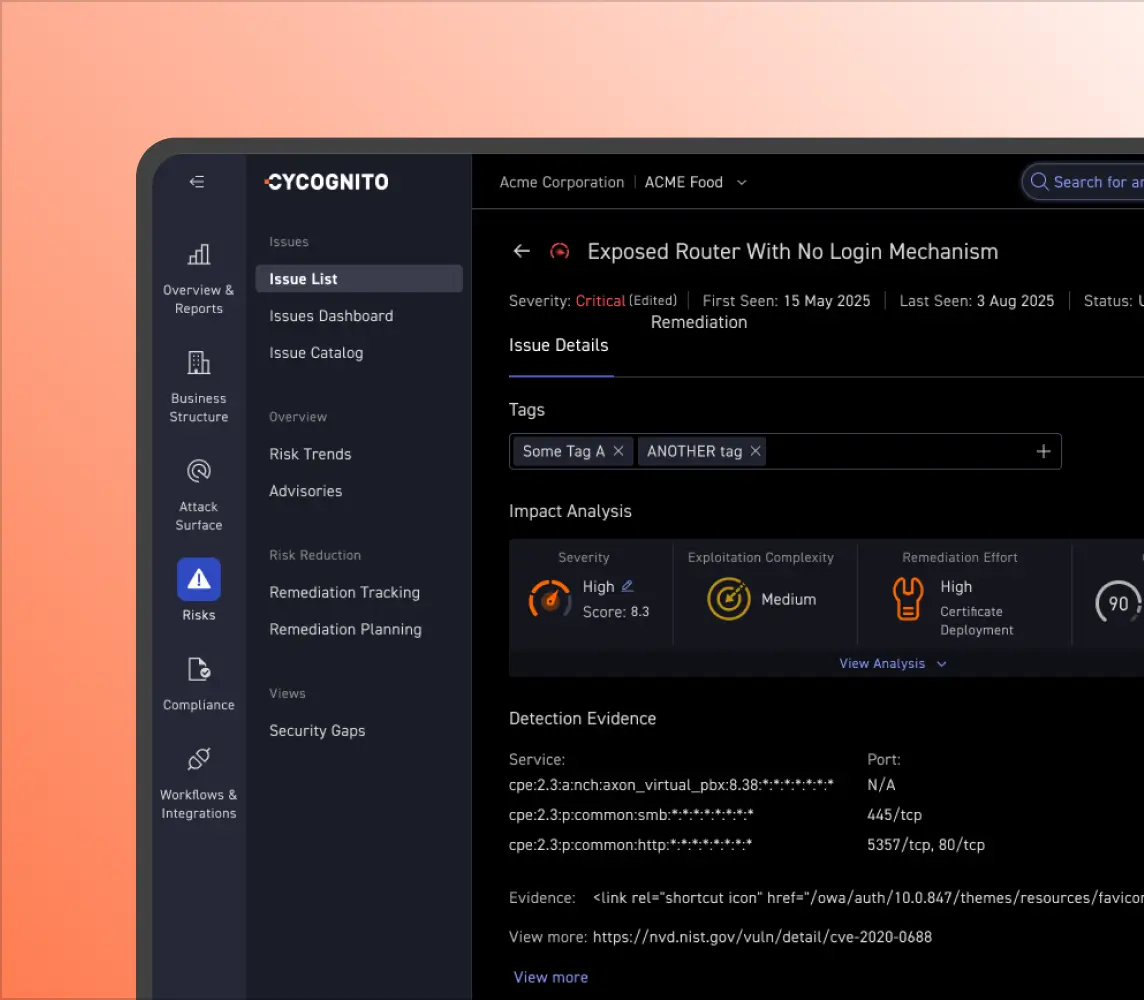
An engineer at a large international hospitality company created a basic Javascript web interface that allowed him to run commands on the mainframe and debug mainframe code from home. That interface was exposed to the internet, however, and if discovered by attackers, it would have allowed them access to the organization’s reservation system and customers’ personal information.
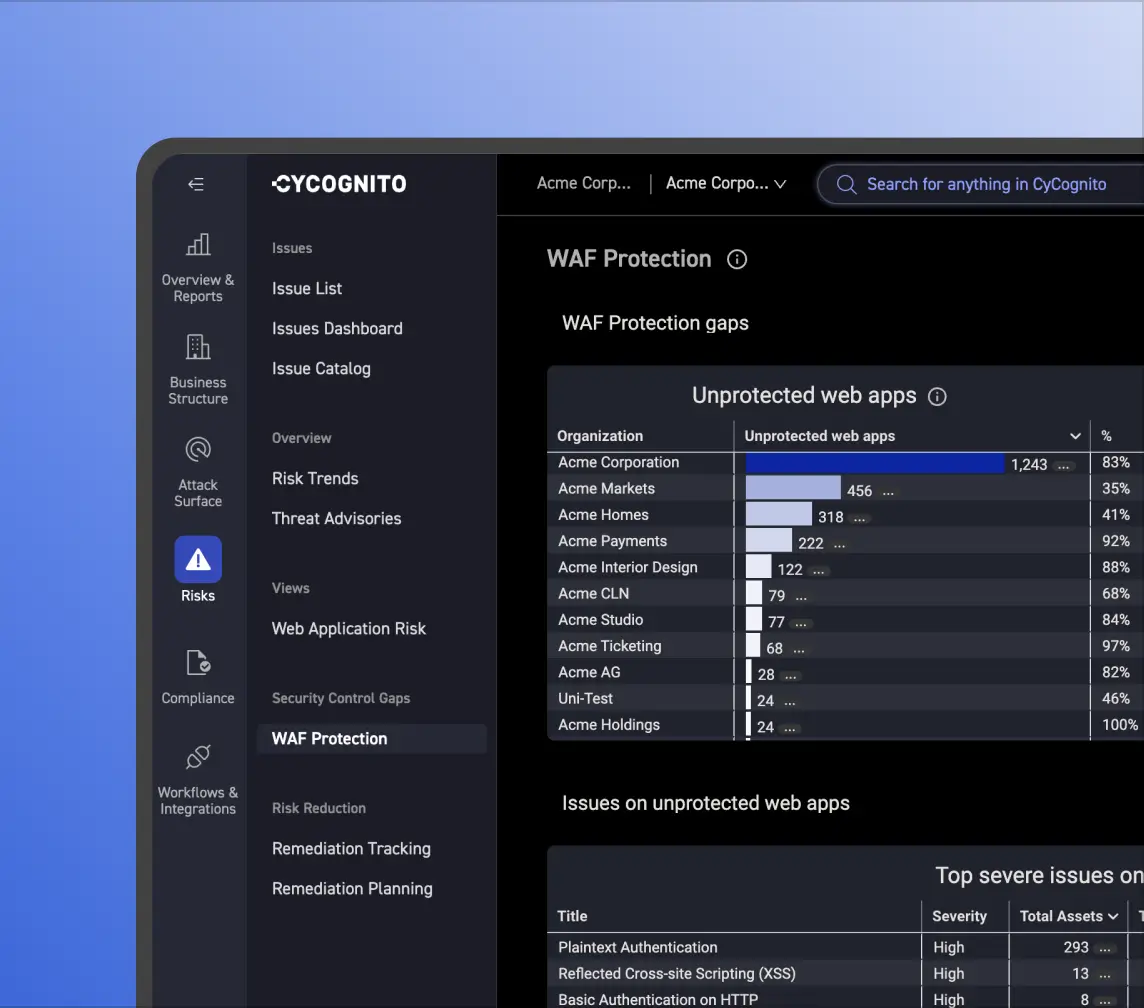
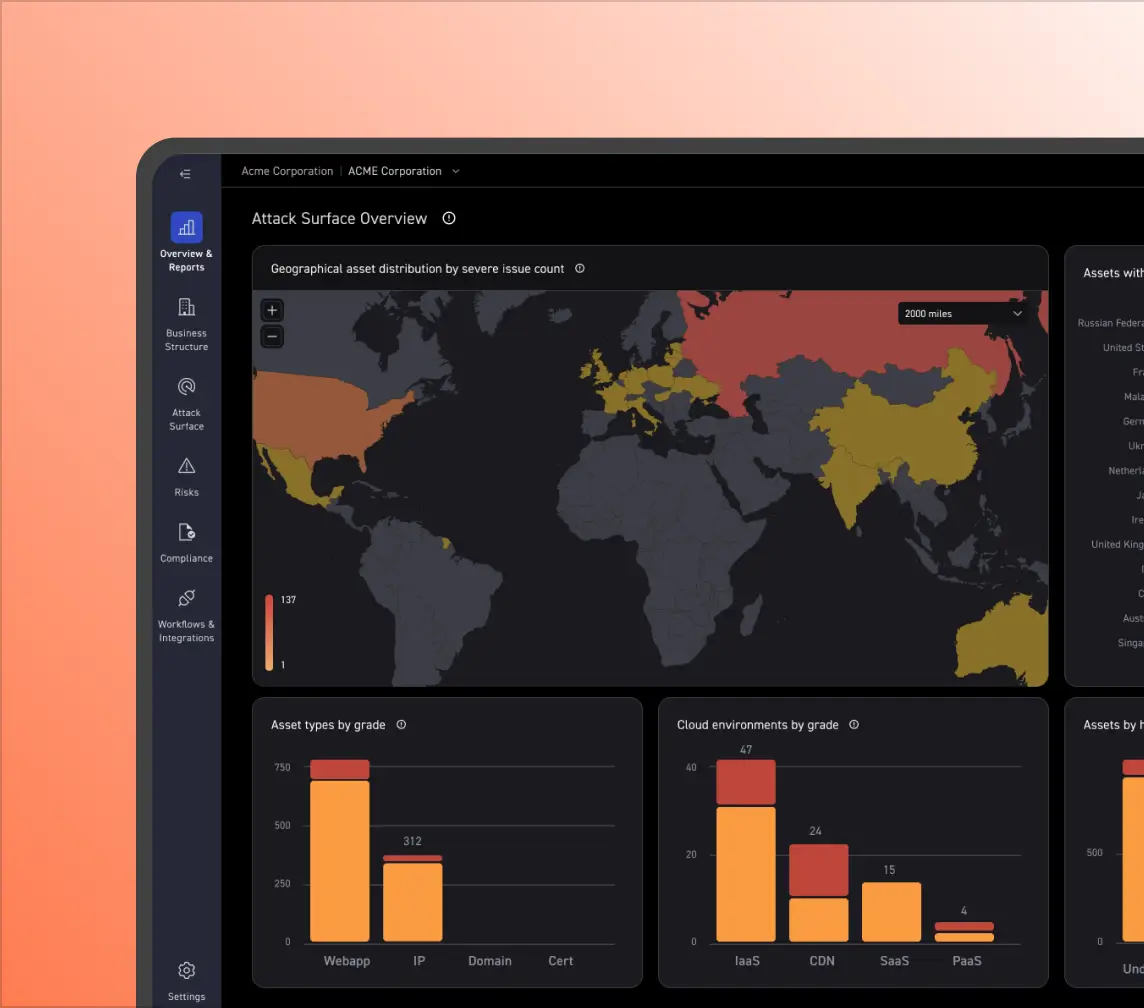
With CyCognito, IT security teams can rapidly detect this type of misuse and take prompt action to eliminate it.