The shutdown of Colonial Pipeline, a major fuel pipeline in the United States, by ransomware is yet another cyberattack that highlights an important weakness in our global supply chain. Look at Solarwinds, Microsoft Exchange, and Accellion as other recent examples.
DarkSide Responsible for the Colonial Pipeline Cyberattack
On May 8, 2021, the initial investigation indicated that the ransomware gang, DarkSide, was responsible for the Colonial Pipeline cyberattack. The group has been operating their ransomware – called “DarkSide ransomware” and delivered as-a-service – against US and European companies for at least half a year. Attackers using DarkSide’s ransomware variant generally gain initial access by exploiting remote services like Citrix, Remote Desktop Web (RDWeb), or remote desktop protocol (RDP) from an external attack surface. Once they gain a foothold, they dig in deeper via lateral movement, exfiltrating data, and then encrypt everything with ransomware to extort money from their victims.
CyCognito Research Findings
Our research at CyCognito finds that about 1 in 65,000 assets in a typical Fortune 500 company will contain an unprotected remote desktop service. That may seem like good odds, but at-scale this means most major corporations are hosting between two to twenty or more easily exploited systems, right now!
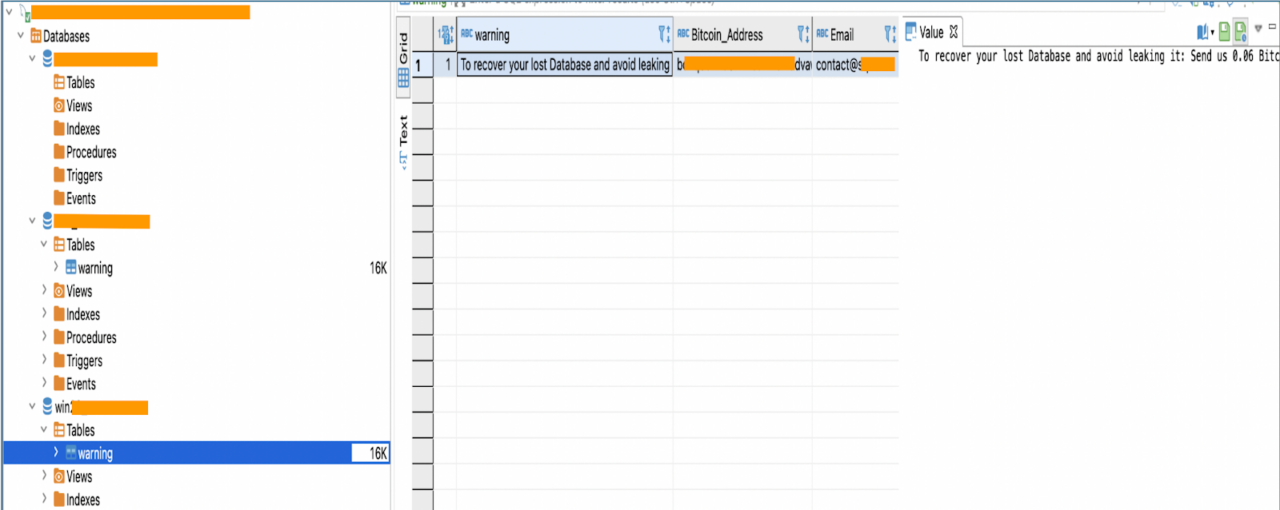
Figure 1: In this example, a Learning Management System with weak credentials was exposed to attackers. Further inspection revealed evidence of ransomware activity, specifically files used to prepare for the attack, including a ransom note. The organization was able to quickly address the issue because the CyCognito platform found and tested the asset and prioritized the issue as critical.
For context, this company has ~110,000 assets.
While any one of those easily exploitable servers may not on its own be business-critical, if it becomes a “backdoor” for a ransomware attack, the consequences can be dire. Of course, the context for the availability of this issue is the need for remote access during this global pandemic. IT is managing assets remotely and of course they are doing it well, but what if a VP of Marketing in Morocco operating at a subsidiary of a French company decides that they need an RDP service to access systems inside the firewall? You might end up in a situation where Bluekeep can be used to hack an unpatched or misconfigured system “managed” by Shadow IT.
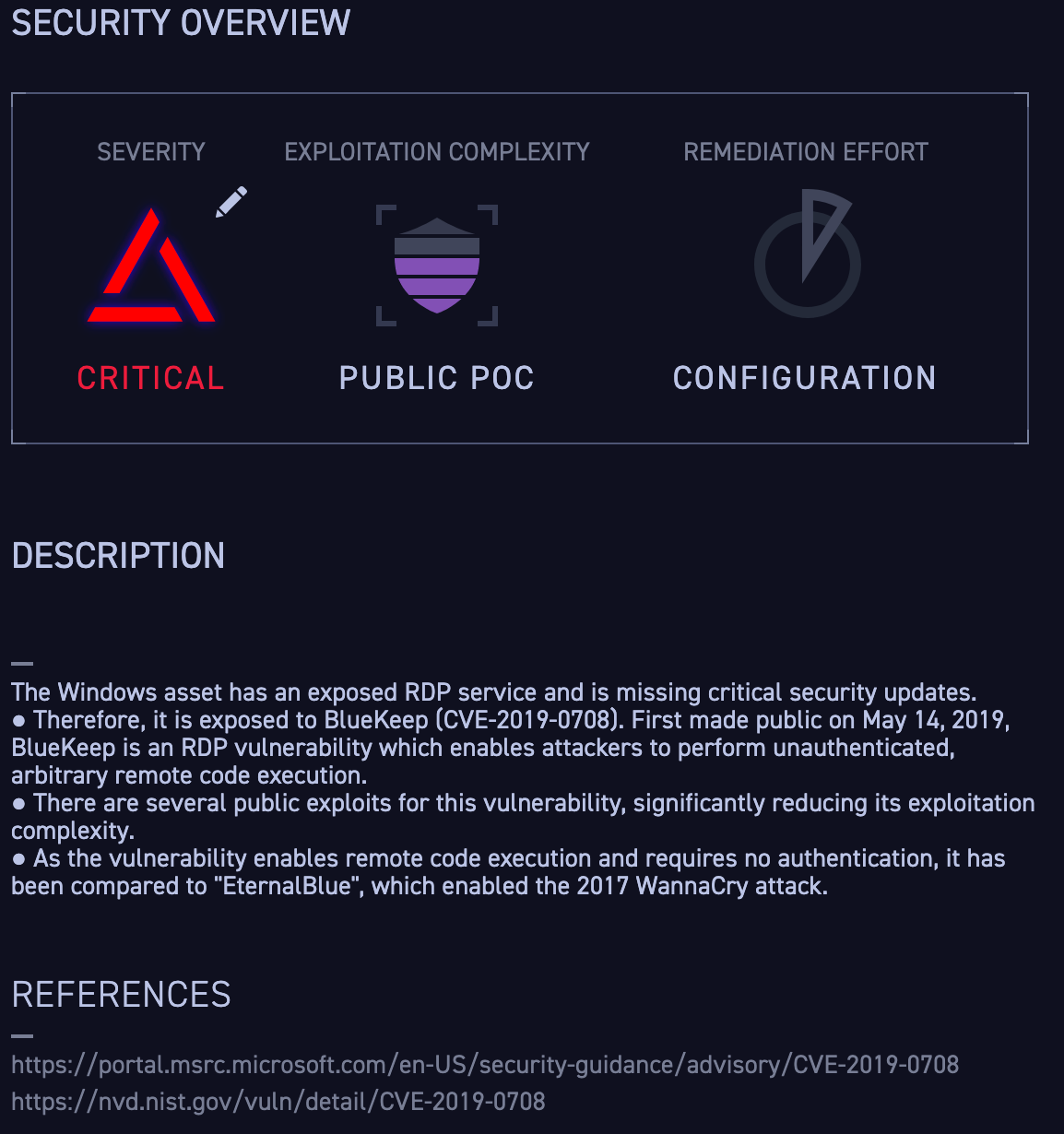
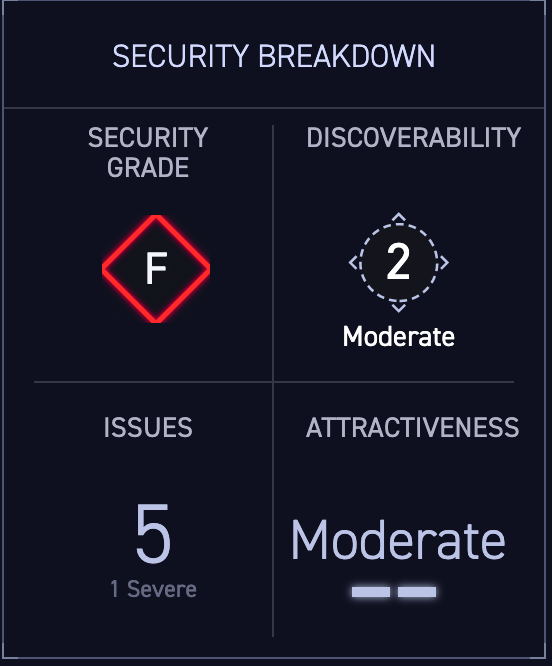
Figures 2 and 3: These are screenshots from the CyCognito platform for an asset with an exposed RDP service susceptible to BlueKeep. The platform automatically discovers assets like this and tests them for security, discoverability, issues, and attractiveness to attackers.
And there is an entire attacker economy that makes locating paths of least resistance such as those just a matter of time. To find these systems, attackers use reconnaissance to find attractive targets into a network. Then they can simply purchase access credentials from the dark web or rent botnets to interrogate systems with brute force attacks. And after extracting data, they can then purchase ransomware-as-a-service from the likes of DarkSide to get money directly from their victims. The whole business of ransomware is a lucrative one, and it's easy to see that an ROI in excess of 1,400% will draw in other criminals looking for targets who supply critical infrastructure and services. The ONLY protection is a proactive defense with continuous, complete attack surface protection, and it must be made clear that ANY asset that is exposed is a potential target and entry point for a much wider, more devastating, and expensive breach.
“Monday, May 10, 12:25 p.m.
Colonial Pipeline continues to dedicate vast resources to restoring pipeline operations quickly and safely. Segments of our pipeline are being brought back online in a stepwise fashion, in compliance with relevant federal regulations and in close consultation with the Department of Energy, which is leading and coordinating the Federal Government’s response.
Restoring our network to normal operations is a process that requires the diligent remediation of our systems, and this takes time. In response to the cybersecurity attack on our system, we proactively took certain systems offline to contain the threat, which temporarily halted all pipeline operations, and affected some of our IT systems. To restore service, we must work to ensure that each of these systems can be brought back online safely.”
Figure 4: Part of Colonial Pipeline’s Press Release About the Disruption
All major organizations such as Colonial Pipeline are increasingly under threat of ransomware. As a result, the US Federal government is taking steps to shore up defenses for critical infrastructure. As organizations focus on digital transformation they find themselves open to these attacks because of pathways in their IT ecosystem of which they are typically unaware. This includes not only their own IT assets, such as servers, applications and infrastructure, but IT assets that belong to, or are managed by their third party vendors, partners or subsidiaries, which are highly interconnected with the company. These shadow assets and attack vectors create shadow risk, which arises when organizations have not fully mapped their attack surface.
The only real defense is to think like an attacker
When attackers find these exposed and unsecured assets, they leverage them to execute ransomware attacks. Ransomware provides an easy income for cybercriminals targeting successful corporations, who typically are completely taken by surprise when they learn just how many unsecured IT assets their ecosystem partners and subsidiaries have, and what an easy target for exfiltration and ransomware those assets present.
The only real defense is to think like an attacker. To get ahead of groups like DarkSide it is essential to find the weakest links and fix them before the cybercriminals can take advantage. This is why the CyCognito platform uses an attacker’s methods like reconnaissance and botnets to discover your entire attack surface and security-test all of the assets in it so that you know where attackers are most likely to breach your organization. With that, you can shore up defenses and eliminate the paths of least resistance that attackers target first.



