We admit it – we’ve had our heads in the clouds recently. Since we started working with Wiz as one of their integration partners, we’ve been spending even more time thinking about cloud assets. And these assets are everywhere!
Gartner predicts double digit growth across all cloud segments in 2025. More and more organizations are adopting multi-cloud strategies that spread their assets across multiple hosting providers and more and more IT infrastructure spending is shifting from on-premise hosting to cloud.
While cloud computing has many benefits, we’re also seeing an increasing number of serious security issues directly affecting cloud assets. We’re not the only ones noticing this trend – researchers with Palo Alto Networks found that by the end of 2024, organizations suffered a 388% increase in cloud security alerts compared to 2023.
Given our new partnership with Wiz, we wanted to do a dive into some of the data we have about the cloud assets CyCognito monitors – where they live, what issues they may be hiding, and what techniques can make them safer.
Before we jump in, it’s worth noting that this research is not specific to the cloud platforms themselves, but rather the assets hosted on them. While we aggregated assets by cloud hosting providers, further research is needed to understand why variance existed between different populations of assets.
What we looked into
For this research, we were primarily interested in assets hosted by the three largest cloud service providers – AWS, Azure, and Google Cloud – but also looked at aggregated figures for other clouds and hosting providers.
We also looked at whether the cloud assets we saw were vulnerable to any vulnerabilities or misconfigurations and whether any of those vulnerabilities were of critical severity (defined as a Common Vulnerability Scoring System [CVSS] score of 9 or higher on a scale of 1.0 to 10.0). These vulnerabilities affect the asset, not the hosting providers.
Looking at anonymized, aggregated data across the nearly five million internet-exposed assets that CyCognito monitors, we’ve found that 1 in 3 easily exploitable vulnerabilities or misconfigurations are found on cloud assets.
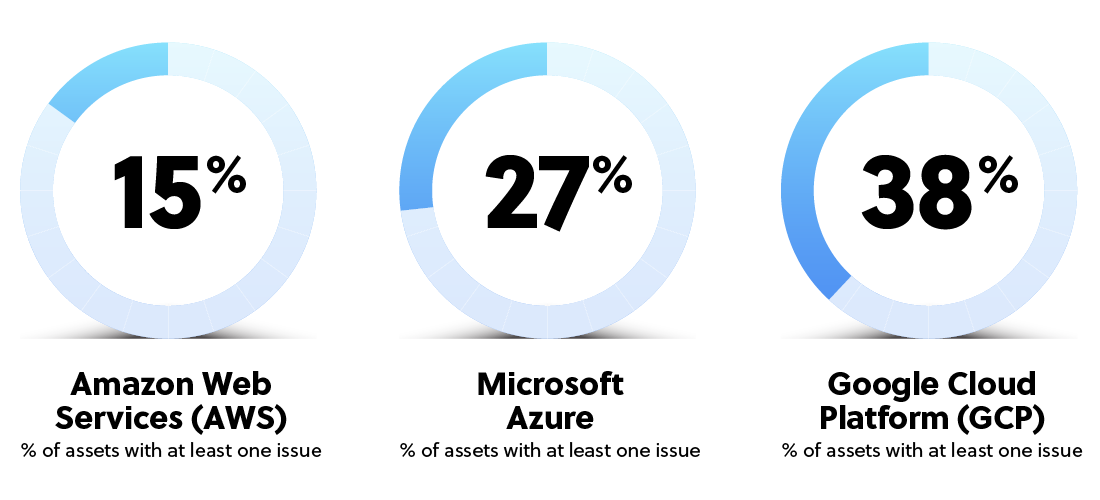
Our research shows that among the three cloud hosting providers, Google Cloud hosted the highest percentage of assets affected by at least one vulnerability or misconfiguration (38%), over 2.5x more than AWS (15%). Assets hosted by Azure ranked second in total exposure (27%). When we looked at assets hosted by other clouds and hosting providers like GoDaddy, Hetzner, and Digital Ocean aggregated together, 38% of assets found on other clouds were vulnerable to at least one vulnerability or misconfiguration and 32% of assets attributed to hosting providers were vulnerable.
Critical issues
Critical vulnerabilities and misconfigurations (CVSS 9.0 or higher) are uncommon across all environments we looked at. However, small numbers can still have gulfs between them. We found that assets hosted in Azure showed a slightly higher percentage of critical vulnerabilities (less than 0.07%) than both assets hosted in AWS and in Google Cloud (0.04%). Although these numbers are small, across attack surfaces of hundreds of thousands to millions of assets, this could represent hundreds of potential weak points – and it only takes one to let an attacker in.
Comparatively, 0.48% of assets attributed to other cloud providers and 0.32% of assets attributed to other hosting providers were affected by critical vulnerabilities. While still less than 1%, the percentage of total affected assets hosted by other cloud providers was approximately 10 times higher than with AWS or Google Cloud.
Low-hanging fruit
While the CVSS is an essential starting point for evaluating the severity of security issues, it is merely a starting point. Our research for the 2024 edition of CyCognito’s State of External Exposure Management report found that incorporating additional context about the affected asset and attack surface, like the discoverability or attractiveness of the asset to attackers, identified one in three (32%) security issues as less severe than their CVSS score would indicate.
Because of this, we also looked specifically for cloud assets with vulnerabilities that were easily exploitable, even if those vulnerabilities weren’t critical. CyCognito uses available threat intelligence on attacker behavior and trends, along with details about vulnerabilities, to measure the difficulty at which a vulnerable asset can be assessed and consequently exploited by a potential attacker, based on the complexity of the required exploitation methods.
Easily exploitable vulnerabilities were most commonly found on assets hosted by “other clouds” and “other hosting providers” – over 13% and 10% of assets, respectively.
Assets hosted by Google Cloud also had approximately double the percentage of easily exploitable vulnerabilities compared to assets hosted by AWS and Azure, with 5% of assets hosted by Google Cloud having easily exploitable vulnerabilities or misconfigurations compared with 2% of AWS-hosted assets and 2% of assets hosted in Azure.
Combined risk factors
Not all critical issues are easily exploitable and not all easily exploitable issues are critical. But when we look at the assets that are affected by issues that are both critical and easily exploitable, we see that assets residing in AWS are the least affected by these types of issues – less than a tenth of one percent of assets hosted by AWS have easily exploitable critical issues. The figures for Azure and Google Cloud are similar.
However, while it’s still true that less than 1% of assets hosted by other clouds or hosting providers are affected by easily exploitable critical issues, these issues can be found at ten times the frequency there than on AWS assets.
| % Assets with at least One Issue | Assets with Critical Issues | Assets with Easily Exploitable Issues | Assets with Critical & Easily Exploitable Issues | |
|---|---|---|---|---|
| Amazon Web Services (AWS) | 14.77% | 0.04% | 1.98% | 0.02% |
| Microsoft Azure | 26.98% | 0.07% | 2.37% | 0.05% |
| Google Cloud Platform (GCP) | 38.15% | 0.04% | 5.35% | 0.03% |
| Other Clouds | 38.15% | 0.48% | 12.72% | 0.30% |
| Hosting Providers | 32.93% | 0.32% | 9.73% | 0.25% |
Great data, but now what?
Now, we're not suggesting everyone go back to on-premises – cloud is here to stay. Instead, security teams should focus on understanding the exposures and risks affecting cloud assets.
- Complete visibility: Multi-cloud environments can lead to forgotten assets and contribute to Shadow IT. Ensure that your asset inventory is up-to-date by using an asset discovery solution that doesn’t rely on potentially outdated or inaccurate inventory information. Seedless discovery solutions don’t rely on what you know to find what missing or forgotten assets.
- Use dedicated cloud security tools: Cloud-Native Application Protection Platforms (CNAPPs), like our friends at Wiz, integrate multiple tools that scan code, check open-source libraries, secure cloud workloads, and track cloud configurations.
But make sure to close security gaps: In addition to testing during development, make sure you’re testing your cloud applications after they’re deployed. Dynamic application security testing (DAST) is crucial for AppSec as it actively tests live applications, uncovering vulnerabilities and misconfigurations that static tools miss.
Worried about vulnerabilities affecting your cloud assets?
If you’re already using Wiz, CyCognito’s Wiz integration can enhance your CNAPP coverage by:
- Enriching Wiz with active and passive test results
- Filling visibility gaps across sanctioned and unsanctioned cloud assets
- Providing an attacker’s outside-in perspective
- Improving overall visibility, threat detection, and incident response workflows.
If you want to better discover and test your cloud assets but don’t know where to start, request a customized demo.



