Thanks to a critical bug in OpenSSL versions 3.0 and above, security teams hoping for treats and no tricks this Halloween may be out of luck.
Earlier this week, the OpenSSL Project team said a critical security flaw had been identified in versions 3.0 and above of its popular cryptographic library for encrypting internet communications. If exploited, the results could be Heartbleed spooky - allowing adversaries to remotely compromise a server’s private keys or remotely execute code on hardware, according to OpenSSL’s own description.
Anyone who remembers OpenSSL’s 2014 Heartbleed vulnerability (CVE-2014-0160) will be aware of the potential for disaster. Heartbleed gave attackers a way to eavesdrop on communications, steal data, and impersonate users of VPNs, emails and chat servers and other software that uses the nearly ubiquitous cryptographic library.
Good News, Bad News
There is a good chance that anything that securely communicates with the internet could be using OpenSSL. However, only a tiny fraction of those OpenSSL instances are likely vulnerable to attack. That is because only OpenSSL version 3.0 and above are vulnerable. And given that OpenSSL 3.0 was introduced only a year ago, most organizations run earlier versions of OpenSSL, which are not affected.
CyCognito’s assessment of its own customer assets under its security protection found less than 0.1 percent of OpenSSL assets monitored vulnerable. While 0.1 percent doesn’t sound like a lot, the ubiquity of OpenSSL worldwide combined with the vital protections the library provides to internet communications means that organizations should ensure that their most valuable assets are not at risk from this vulnerability.
“Situations like this underscore the importance of hygiene and keeping a critical and confident eye on what an adversary sees first - the external attack surface,” said Anne Marie Zettlemoyer, CyCognito’s chief security officer. “When time is critical, organizations that can quickly gain visibility and understanding of where their risk and exposure lies will be best suited to defend and recover.”
OpenSSL’s patched version (3.0.7) will not be available until Tuesday, November 1, giving organizations a few days to identify exactly which assets and applications are affected and create a prioritized remediation plan. As of October 28, there are no publicly available exploits or attacks abusing this vulnerability.
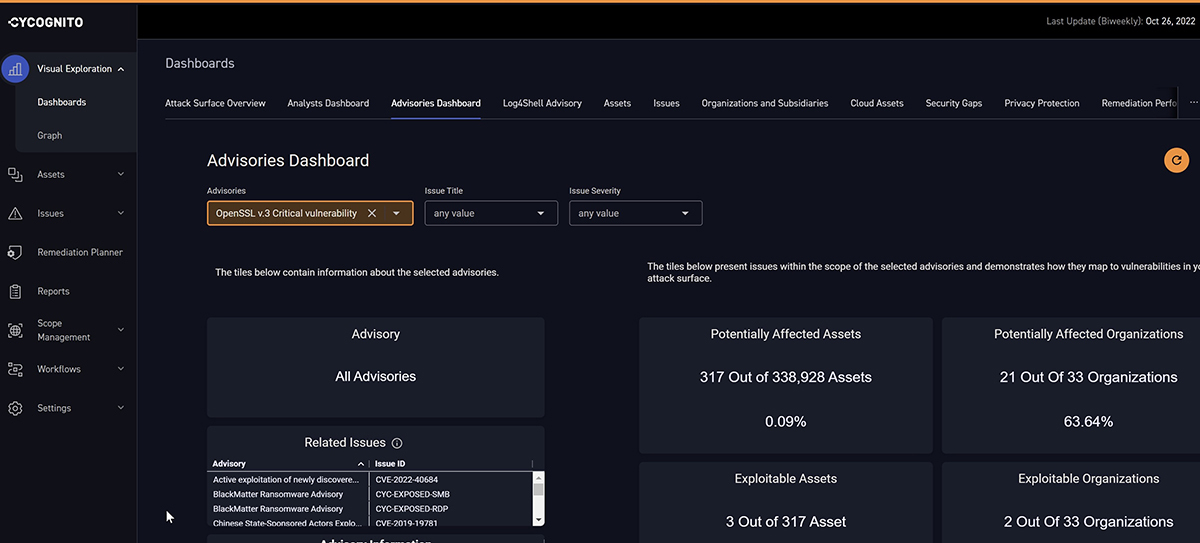
CyCognito’s Exploit Intelligence Arms You Against Future Vulnerabilities
Customers that subscribe to CyCognito’s Exploit Intelligence module can find a list of affected assets, along with further context and next steps for remediation, in their Advisories Dashboard (pictured above). CyCognito Exploit Intelligence, a part of the CyCognito platform, enhances risk prioritization by combining detailed data about gaps in their attack surface with tactical threat intelligence about in-the-wild security threats like this OpenSSL vulnerability. Teams can also use Exploit Intelligence to view and test step-by-step exploitation instructions provided by the CyCognito platform to safely simulate attacks to validate risks and generate indicators of compromise (IOCs) in SIEM, XDR and other security countermeasures.
CyCognito customers interested in subscribing to Exploit Intelligence should contact their Customer Success Manager. Not a customer but interested in how this kind of threat intelligence insight can help you manage risk? Contact us or check out more information on Exploit Intelligence.



