Why finding and securing your attack surface is a problem
Here’s the situation. If you manage a security team focused on security testing, you’re tasked with keeping the organization secure and preventing breaches, but your budget only stretches so far. You know that there are a number of things standing between you and your goal:
- The growing attack surface and shadow IT
- The challenges presented by remote or hybrid work environments
- The assets and risks you don’t even know about
A daunting challenge by any measure. So where do you start? The first step is to get a handle on your attack surface. Your entire attack surface. I say “entire” because it’s bigger than you know. It’s more than just your live IP addresses. It encompasses all of your attacker-exposed IT assets, whether you know about them already or not, wherever they are: on-premises, in the cloud, in third-party or partner environments, or in the networks of your subsidiaries.
For example, Figure 1 shows our actual results from a recent attack surface reconnaissance where our customer estimated they had 10,000 IP addresses but CyCognito found 13,936 IP addresses which means at least 39% were unknown. Our platform goes beyond IP addresses and classifies assets into web applications, domains and certificates, and when these are counted the platform found 21,115 total assets in this particular attack surface, including 7,179 other assets that were not estimated by the customer at all:
Actual Assets in Attack Surface (Initial Estimate of 10K IPS)
| IP ADDRESSES | WEB APPS | DOMAINS | CERTIFICATES |
| 13,936 | 1,267 | 3,378 | 2,534 |
Figure 1. An attack surface discovery by the CyCognito platform shows a total of 21,115 assets.
But how can you possibly get a handle on your attack surface when you have teams spinning up microservices they don’t tell you about, mergers and acquisitions and failed devops projects happening on the regular, and fewer employees operating within the secure corporate environment of the office than ever before? Answer: an external attack surface management solution (EASM). Because with the scope and the constantly changing nature of your attack surface, you can’t possibly protect it manually and, if you try, your budget will need to be… prohibitively large.
The eternal question: build vs buy?
You could attack this problem by building a solution in-house (and some large companies have tried), but EASM isn’t exactly a core competency any enterprise wishes to invest in because it will be costly and difficult to design, develop, maintain and operate, especially when independent software vendors can use cloud services to provide a better, more cost effective solution. To simplify the build vs. buy question, I sometimes draw a parallel to how I engage with my lawn. And, if you happen to be an American, you’ll be able to relate to this because, like 79% of Americans I value my lawn. Nowadays I don’t own a lawnmower because I am fortunate enough to have someone else who mows and trims my lawn for me (as do 40% of Americans who have lawns). While I could buy a lawn mower and trimmer, and spend the sweaty hours maintaining my lawn myself, I would never do it as well or as often as I would want. And I would lose the opportunity to spend my time on things where my skills are better put to use, like grilling, writing blogs or playing with my kids. And while I give up money by purchasing the lawn mowing service, I know it’s done well, I get to benefit from the results, and I don’t have to do that drudgery.
Very much like that, your cybersecurity team doesn’t want to do the error prone work of manually combing through public data like news stories, company websites, and SEC filings, or scanning IP ranges, banners and DNS records looking for assets in your attack surface. You don’t want your highly skilled team spending their time sifting through passive DNS data or old financial records to find that forgotten-about subsidiary or branch office in Singapore with access into your corporate network that’s still using an Accellion FTA. To continuously find all of the assets from all of your owned and related entities would almost certainly require a much larger team than you can justify, and they’d need much more time than you have (and I didn’t even address storing and curating the data you’d collect). More so, is that really where you want your security team spending their time?
It’s time to consider the Iron Triangle (see Figure 2) of project management. When building your own solution in-house you can’t have coverage, cadence, and low (or even reasonable) cost. Realistically, only two are possible at any one time with legacy or homegrown solutions. And if you consider what’s most likely to happen, it’s that your budget will rule the day, and you’re going to end up with whatever coverage and investigation cadence you can shoehorn into your existing budget. So going the do-it-yourself route, you need to make some tough decisions. Do you sacrifice coverage (i.e., how much of your attack surface do you get to know and protect), cadence (i.e., how often do you monitor) or money?
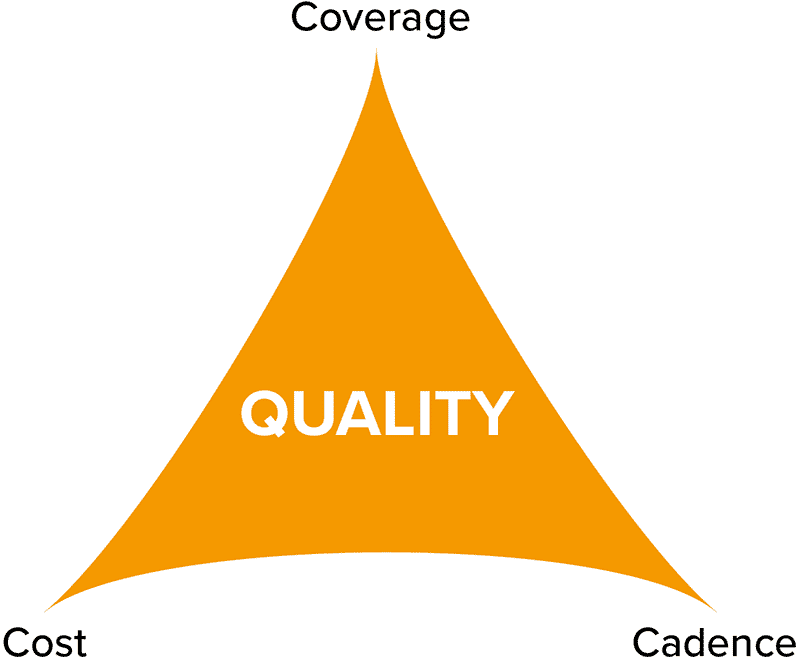
Figure 2. The Iron Triangle is a project management model that illustrates that the quality of a project’s work is constrained by its coverage (scope), cadence (schedule) and cost.
Fortunately, you don’t have to sacrifice coverage and cadence, and your security, to stay on budget. CyCognito was founded to answer the fundamental question of "where are valuable assets exposed and presenting a path of least resistance to attackers?" CyCognito recognizes that solving this problem requires complete visibility, context, and security assessment of the whole attack surface. Built by ex-intelligence agency reconnaissance experts, CyCognito is the only company to do this.
CyCognito delivers coverage and cadence more cost-effectively than what you're doing
So, what exactly do I think you’re doing today to manage your attack surface that allows me to make that claim? I’m sure that attaining even a small portion of the visibility you have now requires many tools and hours of work per week, many weeks per year and, at some large organizations, several people working at it full time. See Figure 3 for a list of the many types of tools organizations used today to do attack surface management.
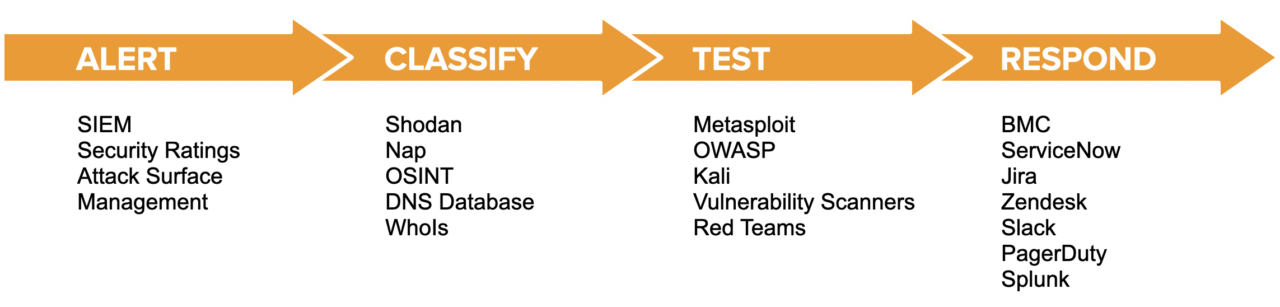
Figure 3. Common tools and workflow used to provide attack surface visibility.
To see and protect all of your attacker-exposed assets with a set of tools like this (and the implied manual process that go with it), would cost a ton.
We’ve created a solution that goes far beyond legacy attack surface management approaches and manual processes to provide more comprehensive, continuous, and cost-effective coverage than you can get anywhere else, including manual or in-house efforts. CyCognito delivers visibility and protection across your entire internet-exposed attack surface by combining three key areas:
- Asset Discovery with classification and attribution
- Automatic risk detection via evidence-based security testing
- Contextual prioritization, fix validation and security posture improvement analytics
Rather than ask you to do part or all of it yourself with a host of disparate tools and tedious manual labor, CyCognito offers one solution that does it all. Our attack surface protection solution continuously discovers all attacker-exposed assets; identifies and prioritizes risks across the entire IT ecosystem, even on those assets your team doesn’t yet know about (or forgot); offers remediation guidance and validation; and does this at a lower cost.
We’ve done thousands of hours of research to determine what it takes to manage attack surface management workflows with existing tools and processes, and I’ll expand upon that in an upcoming blog post. Based on that research, we created a total cost of ownership calculator that shows exactly how CyCognito compares to the tools depicted in the diagram above, and if you're interested in seeing a comparison, I think you’ll be astounded by the value CyCognito can offer!
Until that next post, schedule some time and we can walk through the TCO calculator if you’re intrigued.



