CyCognito releases next-generation of the CyCognito platform with advanced data collection, organizational data modeling and workflow management
Increased attack surface visibility and security workflow for greater effectiveness
Organizations are collectively spending billions of dollars on cyber security products to protect themselves, but successful breaches continue largely unabated. The CyCognito platform performs reconnaissance the way sophisticated attackers do, so you can prevent breaches by efficiently and effectively eliminating your shadow risk — the paths that attackers are likely to use to compromise your organization.
CyCognito is today announcing the immediate availability of a major release of new CyCognito platform capabilities, which further increases attack surface visibility and control, along with the announcement of US$23M in funding. The CyCognito platform is a SaaS offering, and new capabilities are introduced in a continuous flow, but these new features are significant and represent a next-generation release of the platform.
In particular, we’ve made major advancements in information visualization and exploration, as well as workflow integration that will further streamline and enhance the platform’s intuitive functionality.
Before we explore these areas in more detail, here’s a quick overview of what our unique platform offers.
Discovering Hundreds of Terabytes of Data: Our Botnet
The CyCognito platform automates a series of difficult processes that are at the core of discovering and eliminating “shadow risk,” the blind spots that are an artifact of modern IT. Specifically, the platform maps the assets in your entire attack surface, determines their business context (i.e., relevance), detects attack vectors, prioritizes those, and recommends remediation steps. The platform automates those processes so that security and risk management teams can focus on the most important risks facing their organizations -- and can stop relying on legacy solutions that are simply not up to the task.
Making it easy for CyCognito platform users to identify and eliminate their shadow risk involves assembling and organizing a lot of data extremely well, which is one of the major innovations being announced today.
Organizing Hundreds of Terabytes of Data: Our Graph Data Model
When it comes to organizing hundreds of terabytes of data, the CyCognito platform automatically creates a graph data model, a mathematical model of your attack surface. This graph data model reflects the assets in your extended IT ecosystem, their connections to other assets, business classifications of assets, attack vectors and more. It’s a complex internal structure that produces a lot of value for users, and makes it easy for you to understand what’s most important to focus on right now.
Even Better Data Model Navigation and Visualization
We’ve introduced three capabilities in the data model that expose more of its power to users.
1. Data Model Navigation and Visualization: We have introduced the concepts of “Platforms,” “Business Units,” and “Environments” as logical groupings of assets.
Business Units reflect organizational groups most likely to own responsibility for the assets. For example, the screen capture below reflects that Remote Desktops are likely to be owned by the IT team, whereas Cisco ASAs are most likely the responsibility of the Security team. At the same time, both Remote Desktop and Cisco ASA assets fall under the Gateways and VPNs Environment classification based on their business purpose: serving as conduits for users who need to access to enterprise IT resources. Organizing assets in a way that makes them easier to understand enables security professionals to navigate their attack surface faster, more accurately, and find what they are looking for successfully.
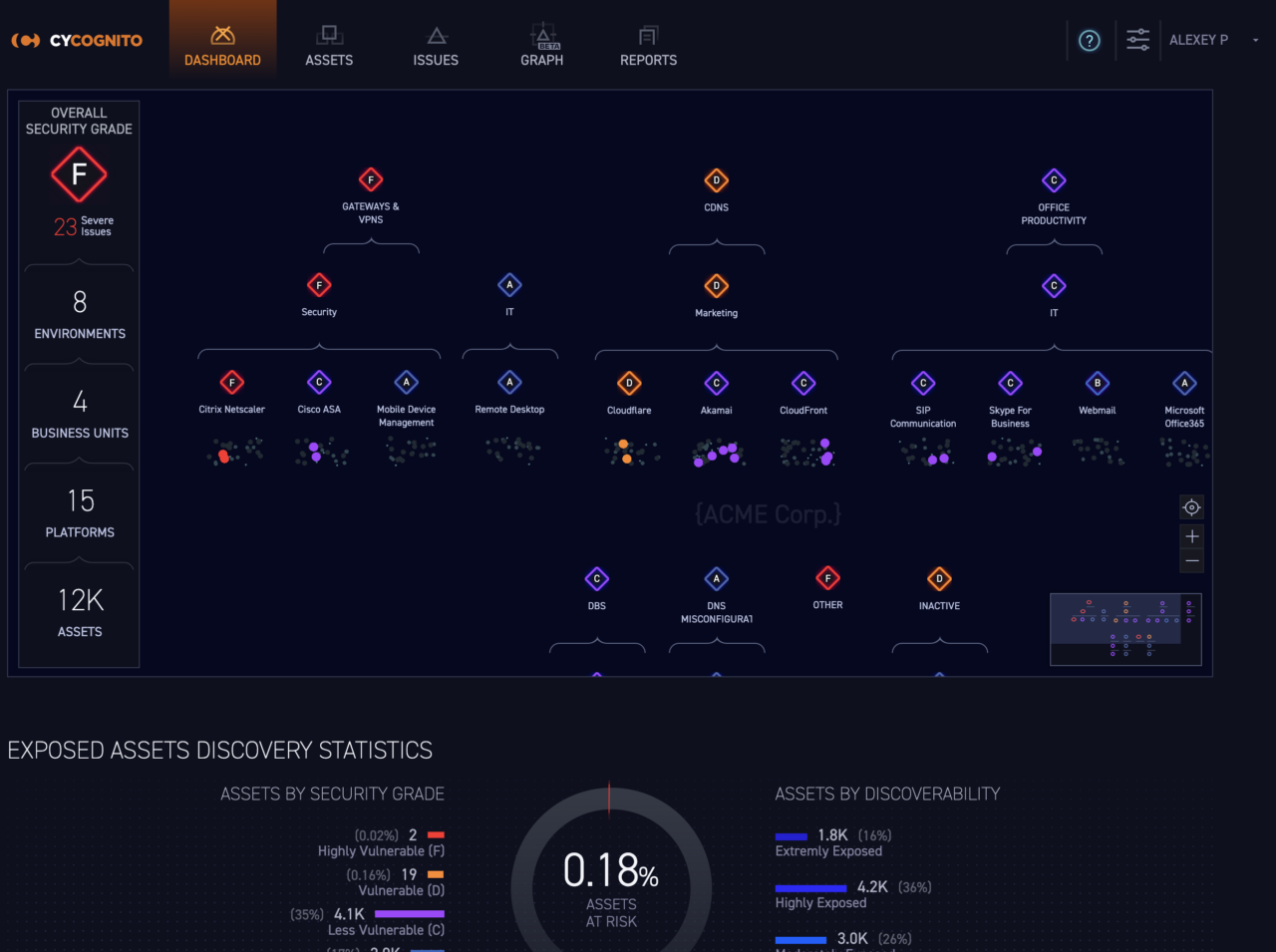
Data Model Nav & Visualization Fig 1. The CyCognito platform automatically groups your assets by function and business ownership.
2. Data Model Navigation and Visualization
We also added a mapping that reflects the relative security – or risk level – of different sub organizations (e.g., subsidiaries), as seen below, so that organizations can understand and manage risk across the entire organization.
ACME IT Services has a number of severe risks, as reflected by its size and color. That’s a natural place for a risk or security team to turn their attention. This understanding of exposure by organization greatly increases the efficiency and effectiveness of security teams.
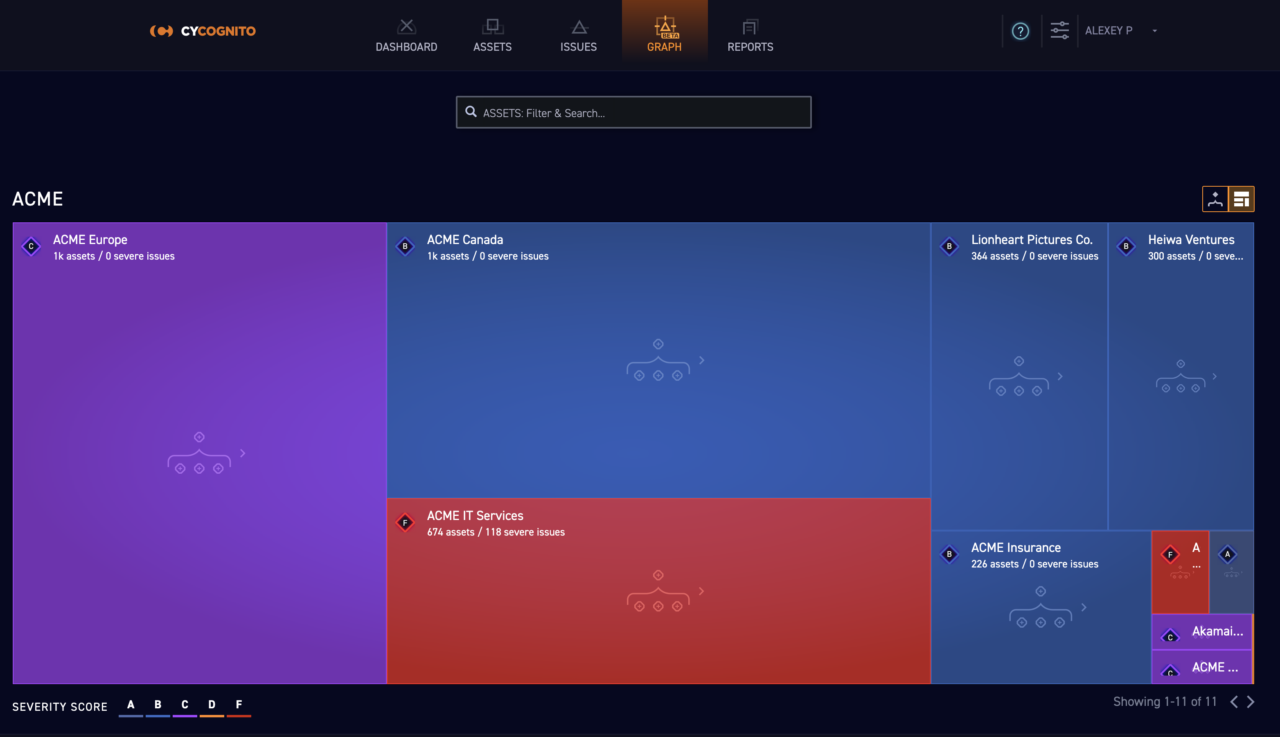
Data Model Nav & Visualization Fig 2. The organizational view in the dashboard gives you a quick view of risk levels of the different sub-organizations that impact your overall risk.
3. Data Model Navigation and Visualization
The third significant addition to the data model is the introduction of “web applications” as a logical entity, which no other solution on the market offers.
The CyCognito platform looks at the existing assets and attack vectors in your attack surface and automatically associates related application servers, databases, load balancers, etc. that form a web application and groups them together. This provides additional business context for those managing attack surface security and enables the identification of new attack vectors. This capability means that even those who aren’t directly familiar with the underlying IT assets – such as new security team members or business executives -- can now quickly understand when critical web applications are exposed when they shouldn’t be, or are in need of further attention from security teams.
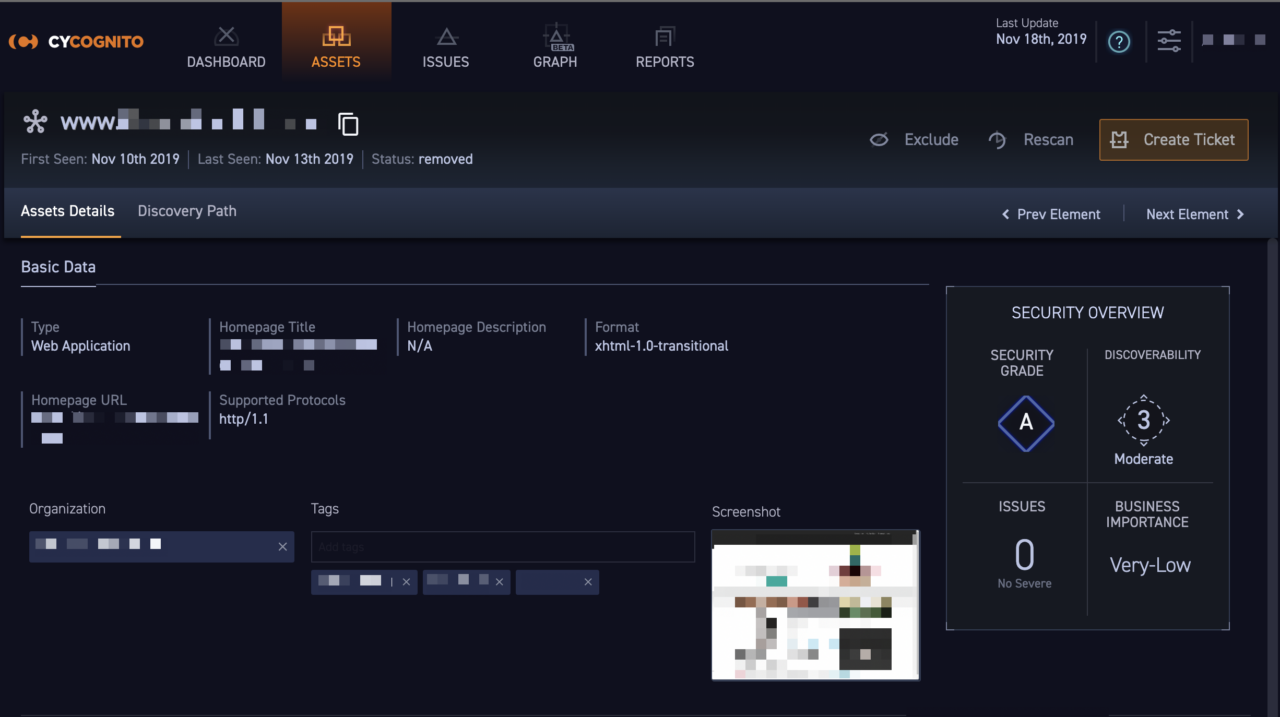
Data Model Nav & Visualization Fig 3. The CyCognito platform automatically
discovers those assets that are associated with a web application.
Robust Workflow Integration Improvements
The second major area of new functionality in the CyCognito platform is workflow integration.
CyCognito customers are eager to incorporate the platform’s intelligence into business processes they already have. Integration allows you to quickly realize value from the platform, and operationalize that value in a way that helps you efficiently eliminate risk. To that end, CyCognito has introduced three significant new capabilities.
1. Workflow Integration: Native Integration with Third Party solutions
When you are working to remediate issues, the CyCognito platform accelerates the workflow by providing native ticketing integration with Jira and ServiceNow. The platform pre-populates all of the data related to the attack vector, including how to remediate it, delivering ticket creation at the click of a button. And, once you have remediated the issue, CyCognito automatically recognizes it has been remediated and marks the ticket as Resolved.
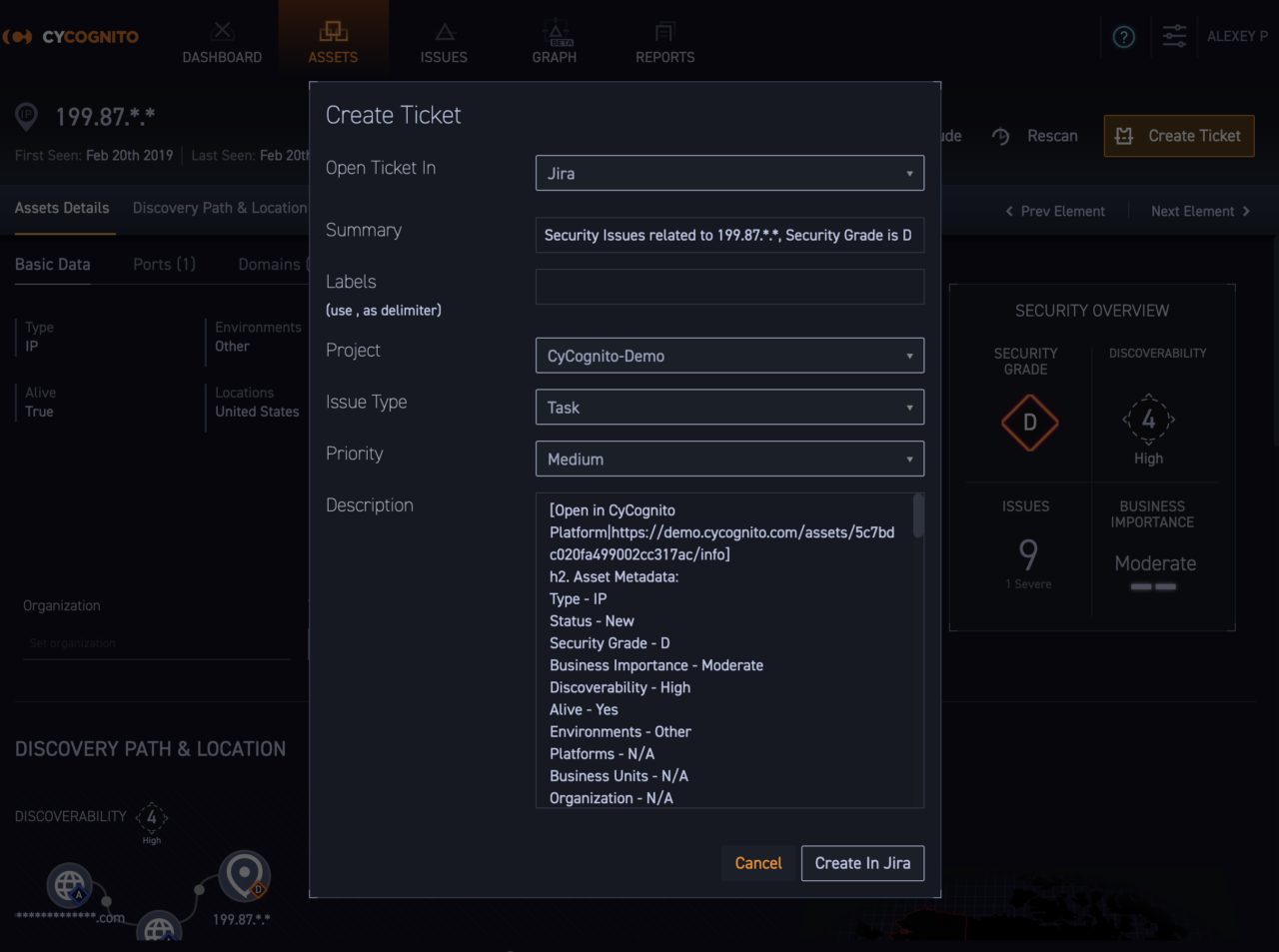
Workflow Integration Fig 1. Native integration, including with Jira and ServiceNow ticketing platforms, makes it easy to integrate the CyCognito platform into existing risk management workflows.
2. Workflow Integration: Application Programming Interface
Adding to our native integration with leading ticketing systems, CyCognito has introduced an application programming interface (API) so that customers can access the data that matters most to their risk prioritization and remediation efforts (see API documentation screen capture below). This modern representational state transfer (REST) API feeds your existing risk management workflows with CyCognito platform data using secure API keys and end-to-end encryption.
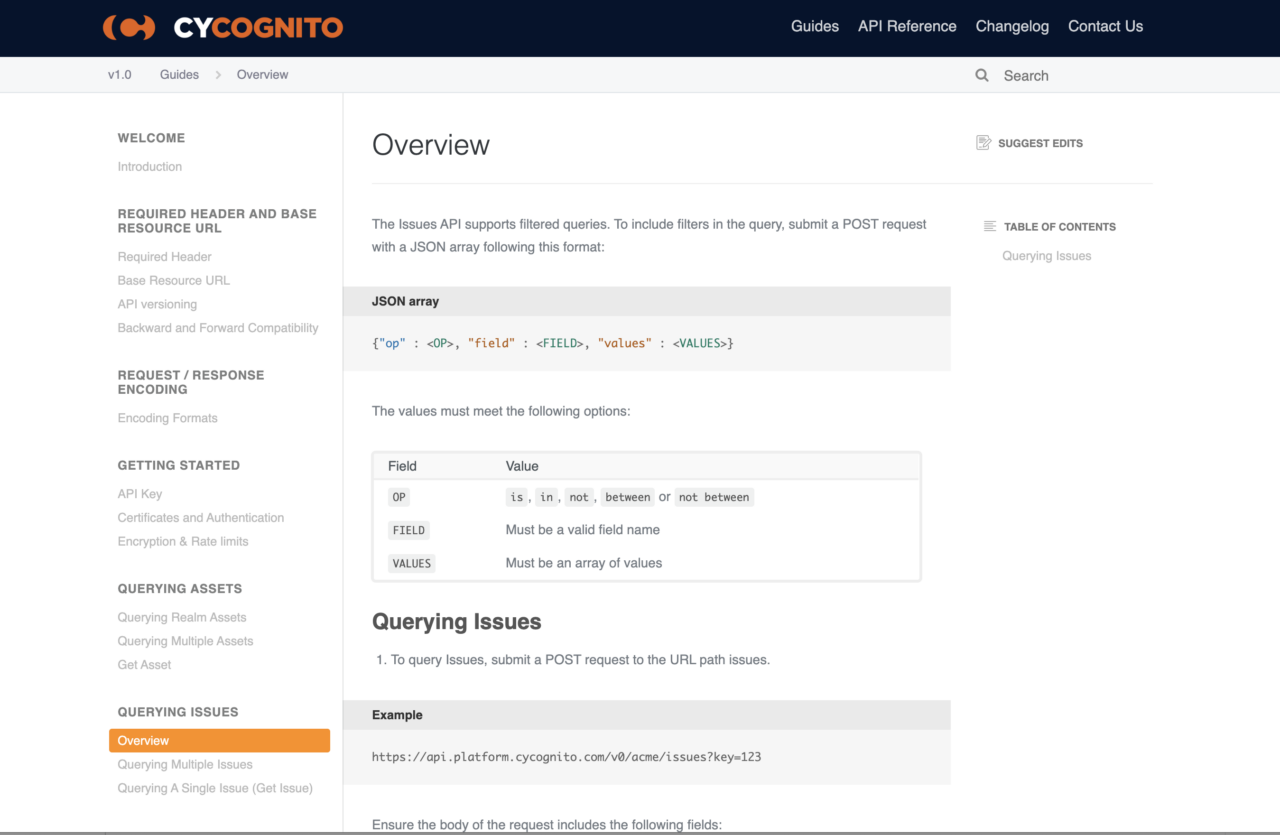
Workflow Integration Fig 2. CyCognito provides the resources you need to use its REST API so that your other solutions and workflows are informed by the CyCognito platform data.
3. Workflow Integration: Role Based Access Control
The third workflow addition to the platform is role-based access control (RBAC), which provides compartmentalized access to data to optimize workflows. Subsidiaries, business units and partners can be granted selective access so that they have a view of risks in their unit, but not a view of the risks of other groups. This makes it possible for organizations with complex governance structures to seamlessly incorporate the CyCognito platform and its data into their existing workflows.
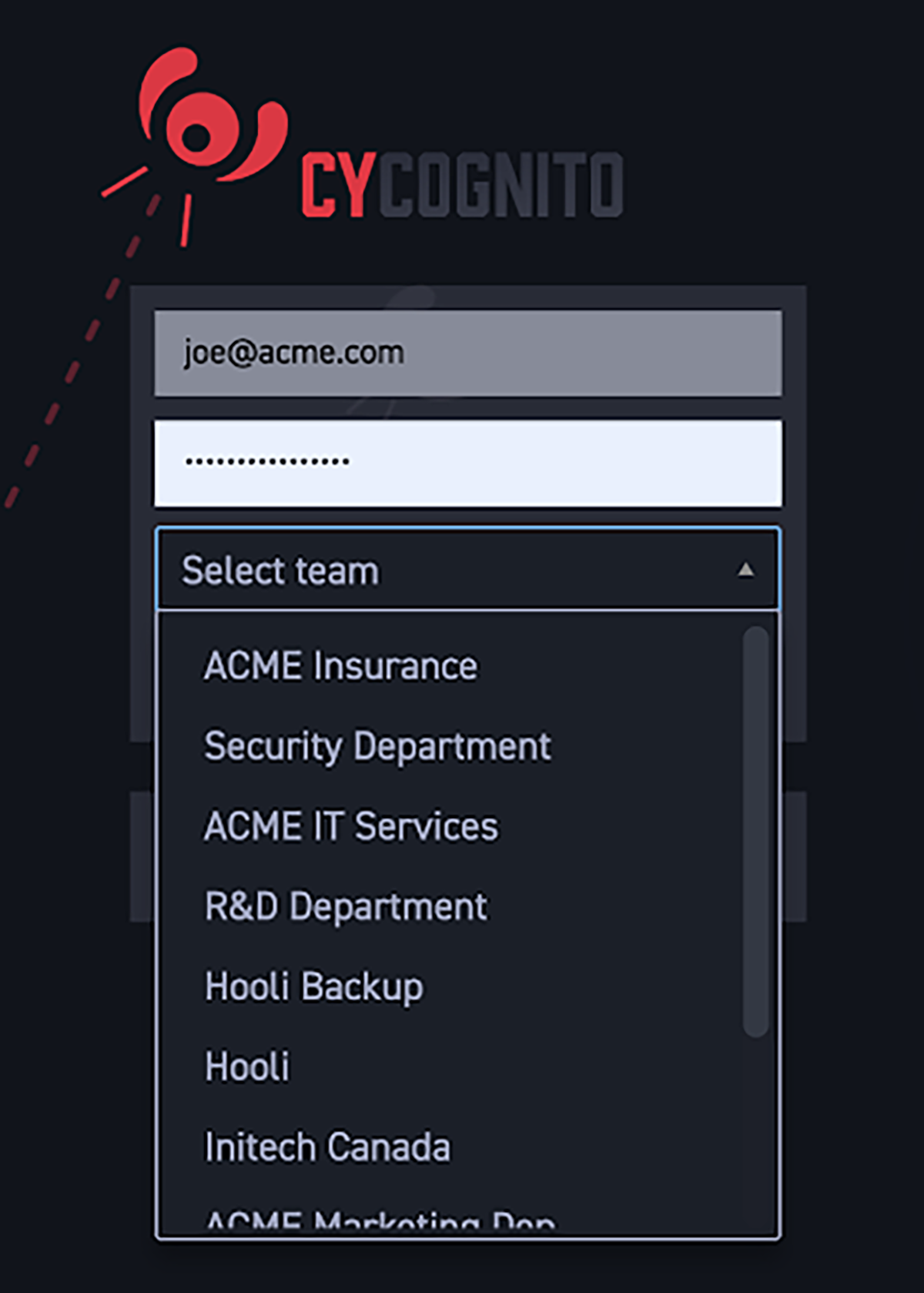
Workflow Integration Fig 3. Different groups can have their own login and view of their attack surface risks with the RBAC feature
Continuous Innovation
Stay tuned to our blog for upcoming information about product innovations as CyCognito continues to pioneer and define a new category of security solutions, Shadow Risk Elimination, working in tight partnership with customers and prospects.



