In the late 1990s and early 2000s, the idea of external attack surface management wasn’t on anyone’s mind. Leveraging the internet for business was just emerging. Enterprise technology was procured through the IT organization and often received on shipping pallets. Organizations knew where they were exposed to attackers, and what they needed to monitor. It was during this time period that port scanners and NMAP were invaluable to the security and IT teams.
The Internet changed everything.
Then, things changed. Business use of the internet exploded. Companies and brands were built entirely online. Technology purchasing became decentralized and the IT team lost control of what belonged to the organization, in no small part thanks to Software-as-a-Service. The first generation of external attack surface management companies were born about this time -- when creating an inventory of the assets that made up your attack surface emerged as a pain point.
And now, things are changing again.
Full-blown cloud adoption, digital transformation and remote and hybrid workforces -- all accelerated by the global pandemic -- have given birth to sophisticated supply chain attacks and widespread ransomware attacks.
Enter the next generation of external attack surface management (EASM), where the purpose and goal is not just the discovery of your attack surface, but to beat attackers with:
- An accurate, honest view of your overall business risk due to internet exposure.
- Smart tagging, contextualization, prioritization, and accelerated remediation.
CyCognito has set out to change the way the world understands what attack surface management could be, and we’re doing that through our new platform.
Are you doing External Attack Surface Management the hard way?
Perhaps this is familiar to you. You attempt to get a picture of your attack surface by using any and every tool that gives you a list of what it finds; network scanners, vuln scanners, network traffic analyzers, and sometimes pen tests. Any new or previously unknown systems are added to asset management tools (which are often spreadsheets). Then, that inventory is scanned the next time your internal vulnerability scanners and application security testing tools run. Suddenly, you have a list of 10,000 things your team needs to fix.
This whole process requires a lot of human glue to work properly. And that human glue is likely already worn down by alert fatigue and constant code-switching between tools.
After three years of listening to our customers and security leader about how they do external attack surface management, we have simplified it once again.
External Attack Surface Management. Redefined. Automated. And in a single platform.
We’ve taken all of the elements needed to do EASM well, automated them, and built the CyCognito external attack surface management platform as a single solution to perform them all.
Integrating seamlessly with your security and IT operations workflows and objectives, the CyCognito platform delivers:
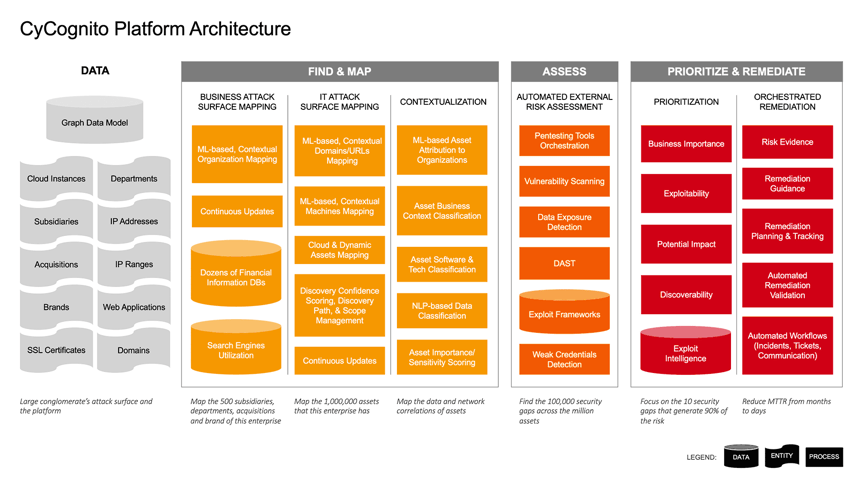
1 - Autonomous, machine learning-based attack surface discovery
A security program is only as good as its attack surface visibility. If you don’t know what you have, you don’t know what you need to protect, and protecting only 80% is futile.
Our discovery engine and processes are built on graph data modeling. We focus internet-wide to discover, understand and contextualize the IT assets that make up your attack surface, whether they are digital, physical or cloud assets.
This process is not reliant on your input, or tribal knowledge, or internal tools and spreadsheets that are out of date by the time they even come together. And the CyCognito discovery model learns from what we find to autonomously discover and map your entire internet-exposed ecosystem—business units, cloud resources, and third parties. Including assets you didn’t know about or that were forgotten from company acquisitions long ago.
We know that other tools of the trade typically yield false positives when it comes to attribution of assets to organizations. To combat that noise, when the CyCognito platform identifies something as yours, we provide the full discovery path along with the reasoning of how our platform associated it with your organization.
Even if some of the assets or business units may not look like yours at first glance, the reasoning behind why they are yours is there. That is a process that often illuminates entire areas of your attack surface that you had no idea existed.
This advanced discovery and inventory is only the first step in the CyCognito approach to EASM. A critical step. But only the first.
2 - Intelligence about what to fix to make the most impact
Once the CyCognito platform has cataloged all of your internet-exposed assets, we perform automated security tests on all of those assets. Operating like an attacker or a penetration tester, these tests go beyond surface-level assessments, giving insights into running software, vulnerabilities, and security gaps at a depth not available from other approaches.
This modern, smart, machine learning-based discovery and testing approach automatically prioritizes which issues you should fix first to reduce the greatest amount of risk.
We look at every issue with a multi-dimensional lens and account for different contributors of risk. For example:
- What is the function of the underlying asset?
- Who owns it and is responsible for fixing it?
- How attractive is the issue to an attacker who might find it?
- How exploitable is the issue?
Exploitability of a vulnerability or security weakness is, and should be, one of the biggest factors in remediation prioritization. If the CyCognito platform has discovered it, it’s accessible to attackers as well. And if there is a known proof-of-concept or an available exploit, then priorities need to be adjusted.
We take the exploitability factor to a new level with our recently introduced Exploit Intelligence capability. Our platform now provides your teams with step-by-step instructions needed to validate the exploit in your environment. This saves security and IT operations teams hours of research, and creates safe validation methods that spare them from risky maneuvers. It can help verify whether your defensive technologies will detect exploitation attempts.
3 - Accelerated Mean Time To Remediate (MTTR)
We know that the typical security or IT operations professional has multiple computer monitors so they can switch between all the tools required to do their jobs.
We designed our platform to reduce the back-and-forth between different systems and tools needed to operationalize EASM.
The CyCognito platform delivers its rich set of actionable details and remediation guidance directly into existing workflows. It does this by integrating with and orchestrating the tools used in those workflows, such as automatic ticket creation in ServiceNow, Jira, automatically updating existing tickets, and communicating with teams via popular channels like email, Slack and PagerDuty.
From a strategic standpoint, our platform’s Remediation Planner capability allows you to set goals (e.g.: “get my development infrastructure from a D grade to a B grade”) and the system automatically generates the list of issues to be resolved to meet that goal. Simple and to the point.
The new era of EASM.
CyCognito has redefined the burgeoning EASM market with a smart, platform approach that amplifies the effectiveness of your existing security resources. Our platform puts a scalable, dependable offensive security system into the hands of your team that simplifies the job of understanding and managing external attack surface risk. It also dramatically simplifies the complex tool farm needed to improve your security posture.
Let us show you how the platform can make your EASM processes better, or if you’re new to EASM, how to get started. Schedule a conversation with our team today.



