When Gartner introduced Continuous Threat Exposure Management (CTEM) in 2022, it formalized a problem security teams had been struggling with for years: patching large volumes of vulnerabilities was not translating into meaningful risk reduction. CTEM reframed the problem. Instead of measuring progress by the number of CVEs addressed, it shifted focus to whether attackers could actually reach and exploit assets that matter to the business.
What Gartner did not provide was a concrete recipe for execution. CTEM defines stages, but not the specific requirements needed to make each stage work in practice. As a result, many programs struggle to operationalize CTEM beyond high-level intent.
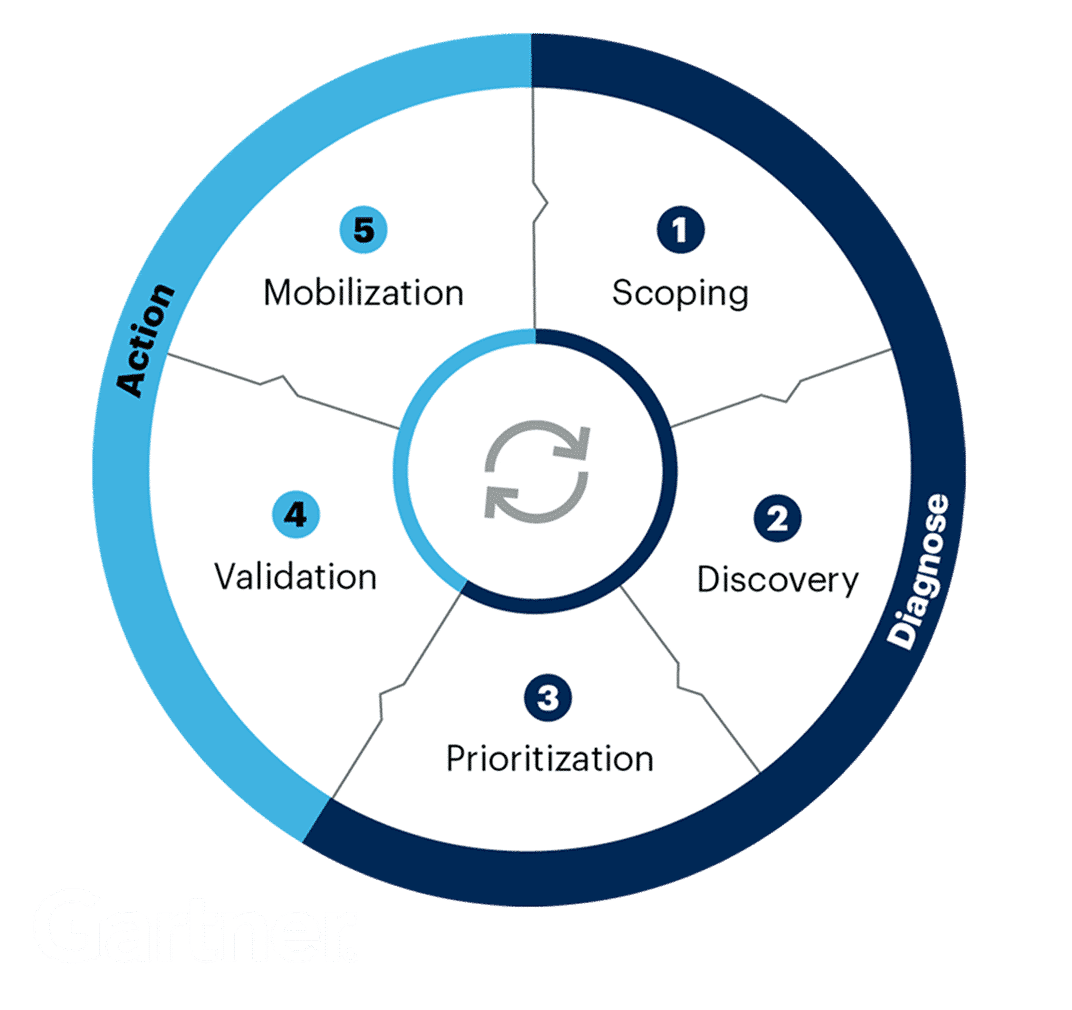
This blog focuses on what CTEM requires at an operational level. Rather than re-explaining the framework, it examines what each stage demands in practice: the capabilities needed, the common gaps teams encounter, and how external exposure management supports effective CTEM execution.
If you want to learn more about these topics, check out other blogs in this series:
- From Activity to Impact: How CTEM Refocuses Security KPIs
- Permission to Ignore: Leveraging the CTEM Framework to Focus on Real Risk
Let's walk through each stage.
Scoping: Define What Matters Before You Scan Everything
"Using a defined scope in a CTEM process means organizations do not have to tackle all exposures at once, but can start with what is most critical to the business." - Gartner, Strategic Roadmap for Continuous Threat Exposure Management
CTEM doesn't expect you to tackle all exposures at once. Scoping sets boundaries based on issues such as business priorities, compliance requirements, and risk tolerance.
The practical question: What's critical enough that its compromise would materially impact the business?
This sounds obvious, but most programs skip it. They fall into the first CTEM anti-pattern: 'scan everything' masquerading as scoping. Without business-driven boundaries, teams alert on everything, overwhelm themselves with noise, and wonder why nothing gets fixed.
CyCognito supports scoping by mapping exposed assets to organizational structure and business context, helping teams focus on what actually matters.
Discovery: See What Attackers See
"Discovery tools should prioritize external attack surface assessment, as it provides visibility into attacker-reachable assets." - Gartner, Use Continuous Threat Exposure Management to Reduce Cyberattacks
Attackers start with reconnaissance. They map what's reachable from the outside-exposed services, forgotten assets, shadow IT, and third-party integrations. Then they look for what's exploitable.
Most discovery approaches fall short. They rely on seed-based scanning that misses unknown assets. Worse, they produce discovery without ownership or attribution - a list of exposed assets with no connection to who's responsible for them or why they matter. Findings pile up with no clear path to action.
The requirements and how CyCognito makes it happen:
- Discover and attribute externally reachable assets - Continuous seedless discovery across environments with correlation of discovered assets to organizational structure.
- Identify risk conditions beyond CVEs - Detection of exploitable issues such as weak or missing authentication, security controls gaps.
- Produce evidence-backed findings - Provision of detailed "chain of discovery" evidence for each detected asset.
CyCognito also provides holistic exposure management by integrating seamlessly with existing asset intelligence tools like Armis and Axonius, providing external-internal attack paths."
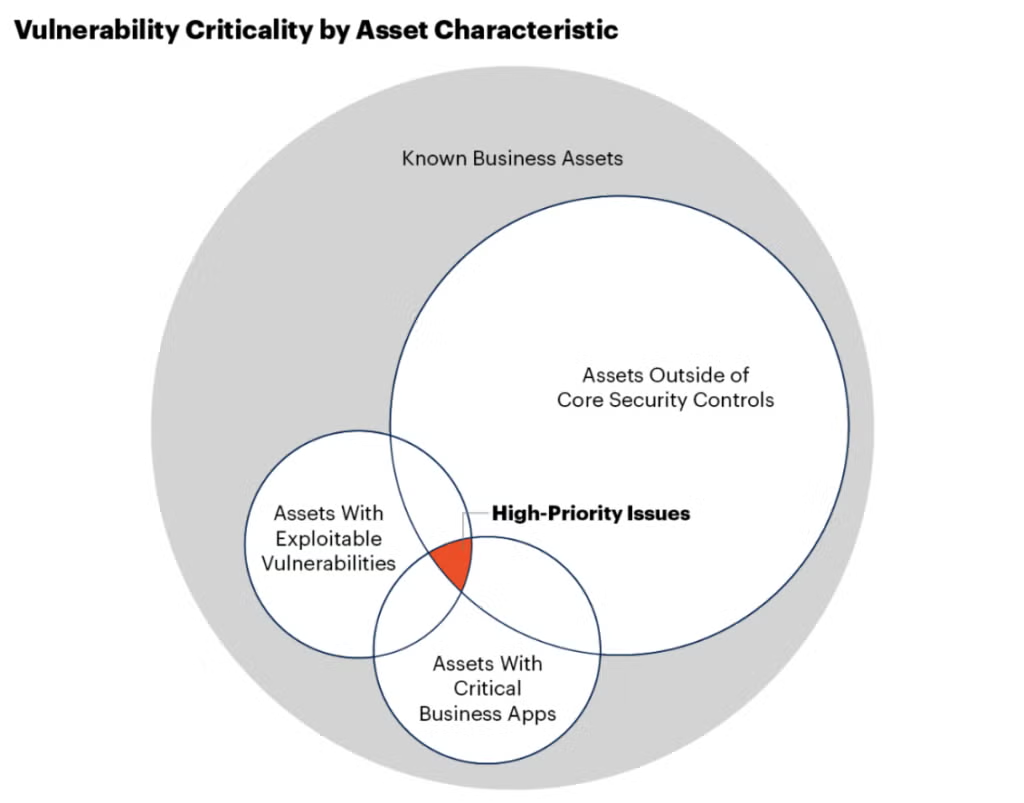
Prioritization: Focus on Risks that Actually Matter
"Contextualized and reprioritized exposure risk data should be used as a new source of truth, rather than raw vulnerability scores." - Gartner, Reference Architecture Brief: Exposure Management
CTEM lets teams distinguish between issues demanding urgent response and those suited to standard hygiene, patching cycles, and infrastructure refreshes. This creates a clear roadmap for action, ensuring that security resources are always concentrated on the exposures that pose a genuine threat.
Most tools still surface vulnerabilities as the primary signal - prioritization driven by CVSS inflation. A CVSS 9.8 on an unreachable internal dev server gets treated the same as one on a customer-facing payment gateway. Teams generate massive alert volumes that look critical but lack context about reachability or attacker behavior
The requirements and how CyCognito makes it happen:
- Align exposure prioritization with business context - Mapping of exposed assets to organizational structure and underlying infrastructure, associating exposures with business-critical services and potential attack paths.
- Incorporate attacker behavior and threat intelligence - Evaluation based on reachability, attractiveness, and ease of discovery, with priority adjustment based on observed exploitation evidence in the wild.
Validation: Prove It Before You Escalate It
"Validation works as a filter to prove which discovered exposures could actually impact the organization." - Gartner, Strategic Roadmap for Continuous Threat Exposure Management
Organizations rely on point-in-time testing - annual pentests, periodic red team exercises. This is validation treated as annual assurance instead of continuous proof. These engagements provide depth in limited scope but can't sustain coverage across attack surfaces that change daily. By the time the report lands, the environment has already shifted.
Without continuous validation, teams make remediation decisions without proof of exploitability. They escalate issues that might not be exploitable. Engineering loses trust. Security loses credibility.
The requirements and how CyCognito makes it happen:
- Continuously and safely validate exploitability as conditions change - Active security testing using non-disruptive techniques aligned with real attacker methods, with ongoing revalidation as assets, configurations, and exposure conditions change.
- Validate exploitability across a broad range of conditions and controls - Execution of 90,000+ security tests across 30+ categories covering OWASP weaknesses, data exposure, abandoned assets, authentication bypass, and security control effectiveness.
- Produce concrete, actionable validation evidence - Enriched scoring combining validated exploitability with attacker interest signals and potential impact, plus detailed technical findings with supporting artifacts for self-verification.
Mobilization: Route to the Right Team with the Right Context
"Mobilization is the process of engaging teams outside of security to remediate exposures based on business risk." - Gartner, Mobilize Threat Exposure Management to Accelerate Remediation
When it works: teams stop getting hammered by repeated escalations for issues lacking context, proof, or clear ownership. When it fails: security loses credibility fast.
The breakdown usually happens because of mobilization that relies on manual trust-building every time. Each escalation requires security to re-prove the issue, re-explain the risk, and re-negotiate priority. Findings lack clear ownership, proof of exploitability, or actionable remediation guidance. Engineering pushes back. Issues sit unresolved.
The requirements and how CyCognito makes it happen:
- Deliver exposure-specific remediation guidance and evidence - Detailed technical findings with supporting artifacts for self-verification, plus remediation guidance tailored to each issue with clear step-by-step instructions.
- Assign ownership to the correct teams and systems - Owner-linked logic that maps issues to responsible teams and systems, with integration to ITSM, ticketing, and DevOps tools.
- Track progress and confirm exposure reduction - Remediation planning and progress visibility across teams prioritized by severity and business impact, with follow-up validation to confirm exploitable conditions have been reduced.
Making CTEM Work
Whether you're adding external exposure management to an existing vulnerability program, extending a discovery tool into full CTEM execution, or starting from scratch, the path forward is the same. Ground decisions in what attackers can actually reach and exploit. Validate before you escalate. Route findings to the right teams with proof and clear remediation guidance.
CyCognito supports all three scenarios and turns CTEM into an operational reality for global enterprises, including Fortune 500 companies. By applying a real-world attacker perspective, CyCognito moves teams beyond legacy vulnerability management, replacing abstract theory with a concrete, step-by-step deployment model that delivers measurable risk reduction.
Want to see what this looks like in your environment? Schedule time with a CyCognito expert to walk through your external attack surface and discuss how CTEM can work for your organization.



