Cloud-Native Application Protection Platforms (CNAPPs) combine tools that scan your code, check your open-source libraries, protect your cloud workloads, and monitor your cloud configurations. But CNAPPs aren’t a silver bullet. They lack external active testing and blackbox cloud asset discovery, two capabilities that can leave exploitable vulnerabilities undetected.
CNAPPs depend on APIs and deployment hooks to see what’s running. But if a cloud resource or app isn’t in the right account, or is spun up in an unsanctioned cloud, CNAPPs won’t detect it, leaving it exposed and unprotected.
Active testing in AppSec, known as dynamic application security testing (DAST), is essential for catching what static-based tools miss. Many of the OWASP Top 10 risks, such as SQL injection, broken authentication, and XSS, can’t be reliably found without actively testing the live production application.
These aren’t just technical gaps, they’re blind spots that attackers look for. Closing them is key to achieving full visibility and protection across the DevSecOps lifecycle.
Bridging the Gap with CyCognito and Wiz
We’re excited to partner with Wiz to deliver blackbox cloud asset discovery and active testing. With the broader visibility and deeper cloud security insight provided by CyCognito, Wiz teams have the context they need to act faster and more confidently.
Asset Discovery: Seeing Beyond Wiz’s Scope
While CNAPPs monitor internal resources effectively, they can struggle with an organization’s external attack surface due to their reliance on known assets, configurations, and cloud APIs. Anything not explicitly deployed or integrated–like shadow IT or exposed, unmanaged apps– often goes unseen, leaving gaps where issues can appear.
CyCognito’s seedless discovery autonomously seeks out externally exposed assets across the global organization, including:
- Misconfigured or orphaned cloud assets
- Shadow IT
- Unsanctioned cloud usage
CyCognito provides Wiz users with a complete inventory of externally exposed assets and asset context.
Active Testing: Uncover and Validate Hidden Risks
CNAPPs are excellent at identifying issues during development and runtime protection after deployment. But actively testing exposed production systems is complex work and outside scope.
CyCognito provides over 80,000 tests, including DAST for web apps. It identifies OWASP Top 10 risks such as broken access control (A01) and authentication failures (A07). It also uncovers issues such as sensitive data exposure and security header misconfiguration identification.
By adding active test results to Wiz findings, CyCognito helps teams prioritize based on actual exposure, not just theoretical risk. This leads to smarter remediation, ensuring teams focus on what’s truly exploitable and urgent.
How CyCognito and Wiz Work Together
The integration is operationally seamless for Wiz users. Once CyCognito is added as an integration in the Wiz console (settings → integrations), test results and asset information flows automatically between platforms (Figure 1).
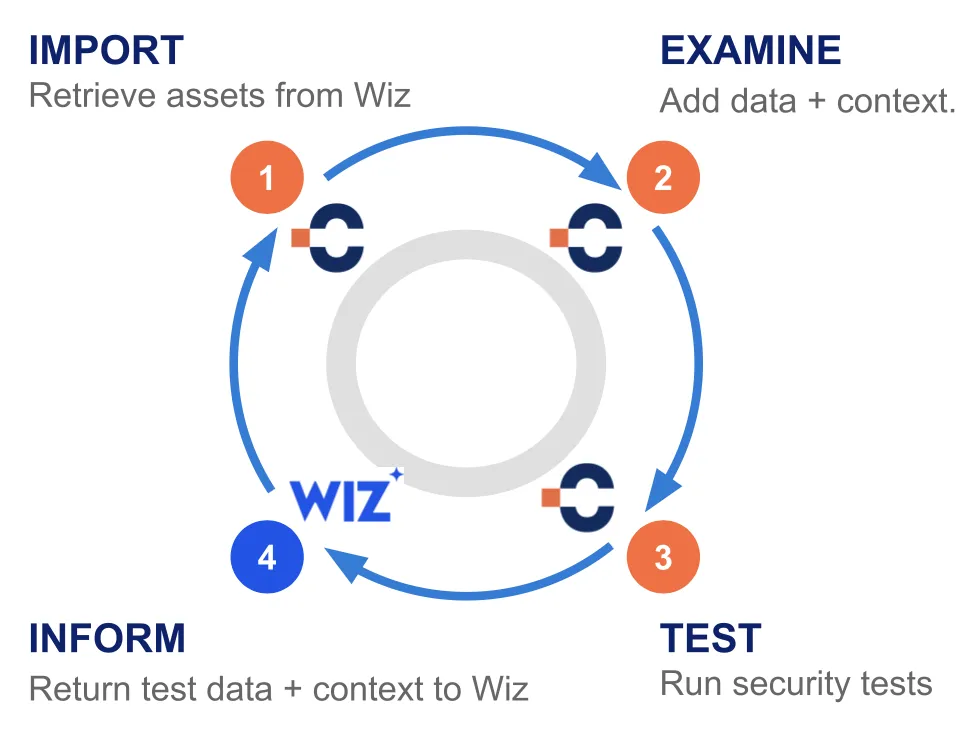
Figure 1. CyCognito runs active security tests on assets imported from Wiz
First, CyCognito retrieves Wiz’s asset inventory. Second, CyCognito gathers over 200 data points including attribution information, port status, and business purpose for every exposed asset. Third, CyCognito runs passive and active tests, such as DAST for web apps. And fourth, CyCognito delivers test and context data back to Wiz, along with issue details, remediation information, severity, and more.
An Example Walkthrough
A tier 1 security analyst using Wiz to investigate a new issue may follow this workflow:
- Start in the Wiz Vulnerability Findings. Checks for new high-risk issues (Figure 2) or from alerting integrations (e.g., Slack, Jira, SIEM).
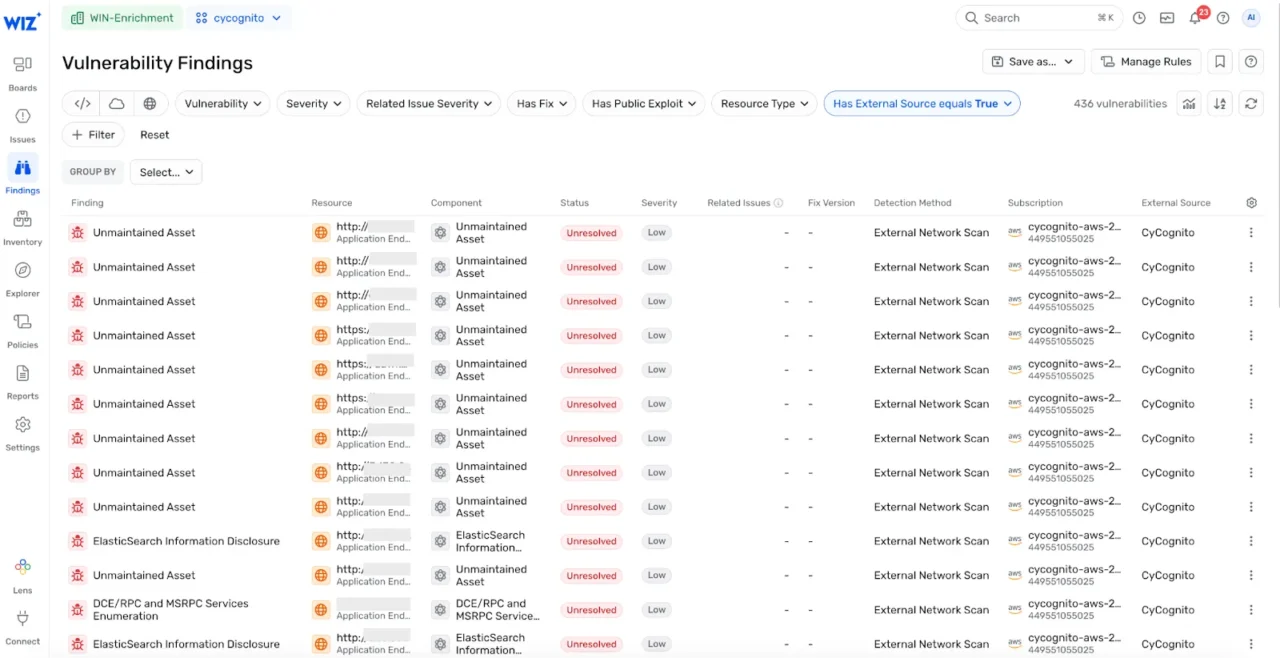
Figure 2. CyCognito test results delivered to Wiz vulnerability findings
- Pivot to the Wiz Security Graph. Open the Wiz Security Graph, where it would see CyCognito imported issues (Figure 3).
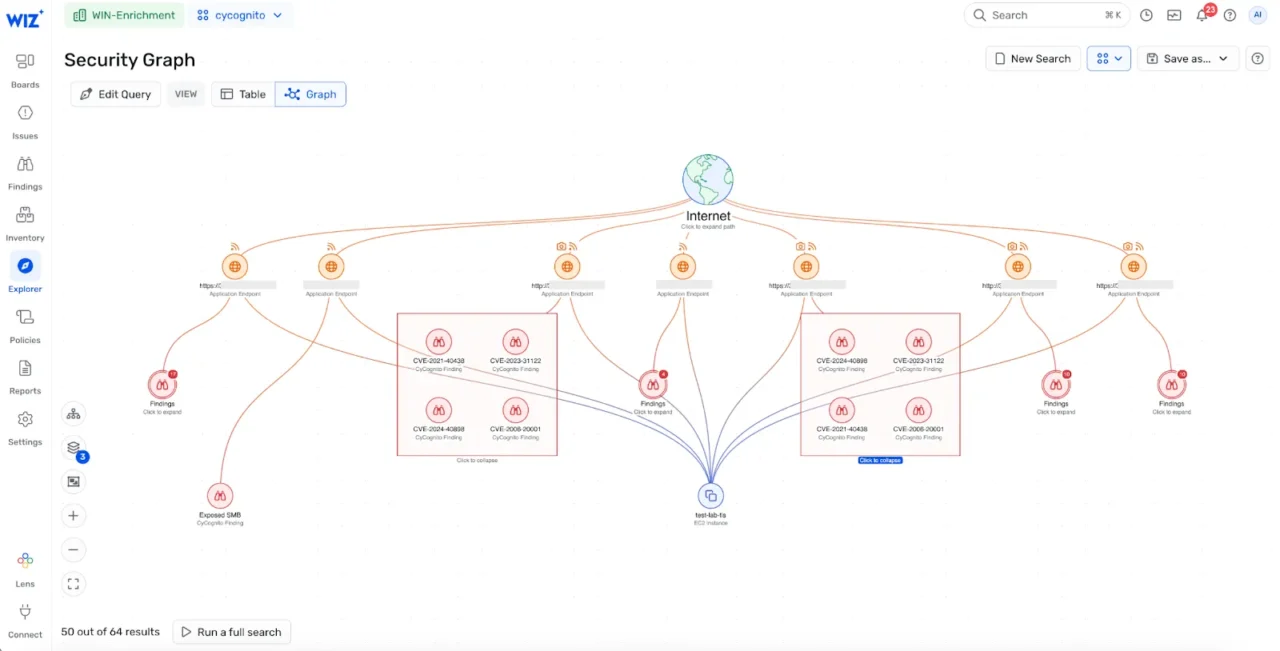
Figure 3. CyCognito test results visible in Wiz security graph
- Switch to the Issues Tab for the Asset. Dig into the issue with detailed context provided by CyCognito (Figure 4).
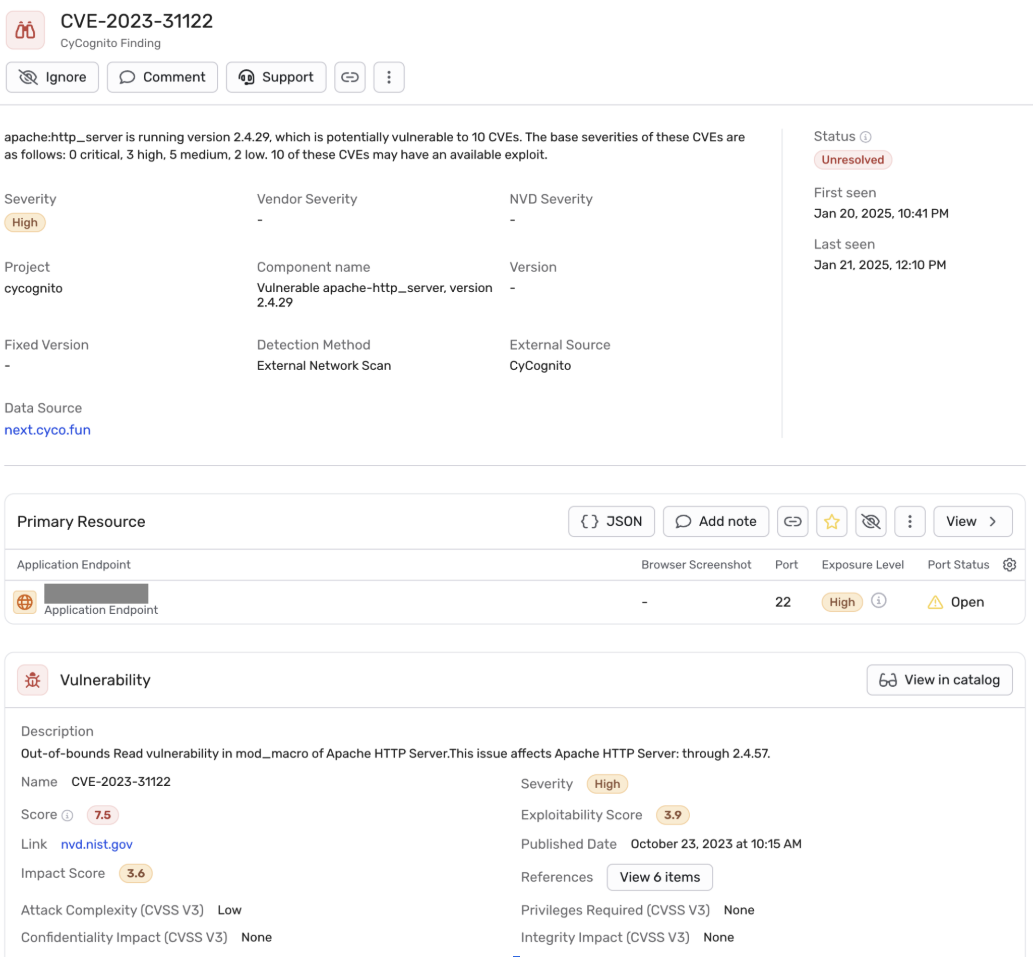
Figure 4. Detailed CyCognito test results in Wiz
- Check Fix Suggestions. Review remediation actions based on the issue type–for example, patch, config change, or access restriction, obtained from the CyCognito integration.
Summary of Integration Benefits
Through this partnership, CyCognito equips DevSecOps teams with end-to-end coverage, from pre-production risk insight to runtime protection and active security testing (Figure 5).
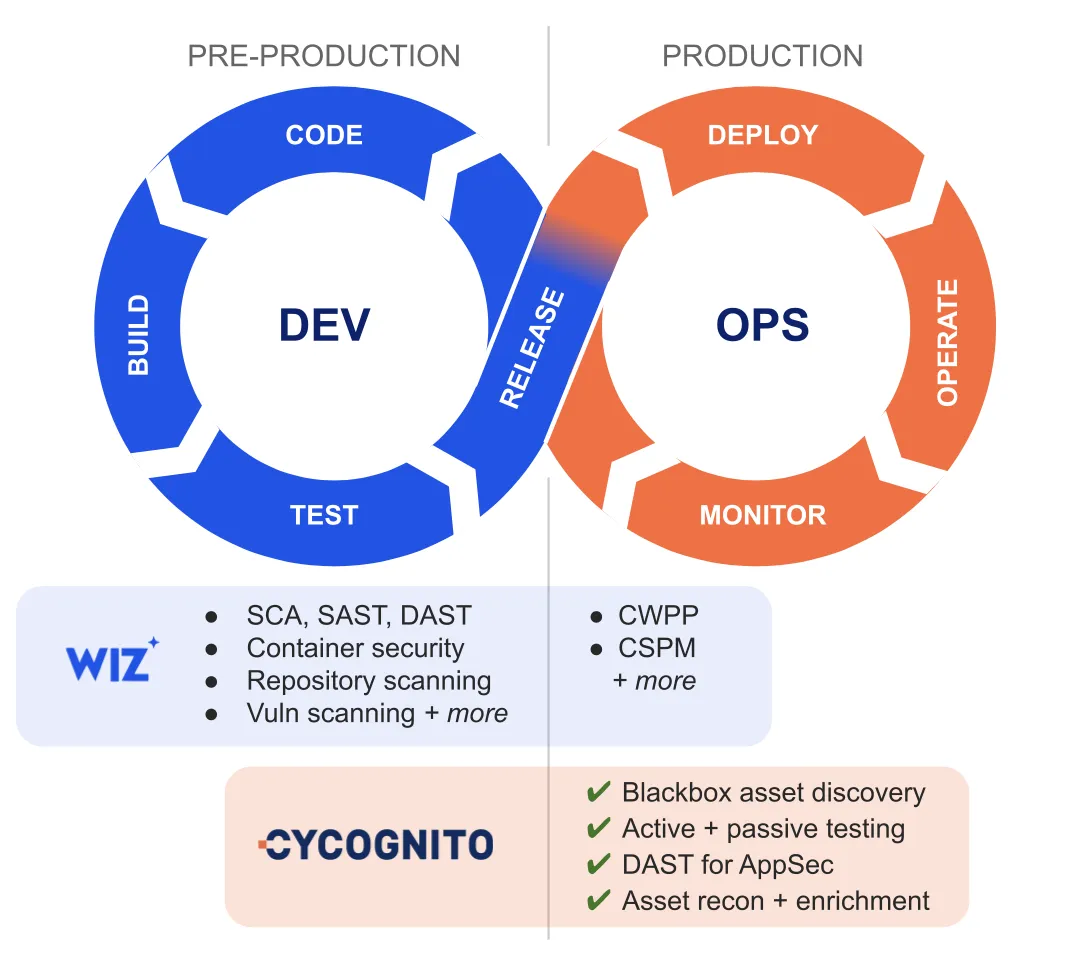
Figure 5. CyCognito provides blackbox asset discovery and DAST to Wiz
Wiz identifies vulnerabilities during development and protects what you’ve deployed, and CyCognito shows all exposed assets and whether they are actually vulnerable in production.
The CyCognito + Wiz integration helps achieve this by:
- Enriching Wiz with active and passive test results
- Filling visibility gaps across sanctioned and unsanctioned cloud assets
- Providing an attacker’s outside-in perspective
- Improving overall visibility, threat detection, and incident response workflows.
Visit our solutions page to see how CyCognito enhances CNAPP coverage.
Learn More
Want to see it in action? Request a demo and explore how CyCognito enhances your CNAPP strategy with outside-in asset discovery and dynamic application security testing!



