Demand for information security professionals is undoubtedly very high. Cyberattacks and ransomware seem to be in the news daily, and no one in the industry will soon forget (or escape) the consequences of the massive cleanup required by Log4Shell. Despite the best efforts of automation and AI, we will always need people to prevent hackers from stealing data and wreaking havoc on computer networks essential for most businesses today. In essence, a domino effect over the last two years of Covid-19 has led to the “Great Resignation” and the “Great Retirement.”
I recall first hearing of the Great Resignation in September 2021 as we saw a record surge in voluntary “quits,” especially in health care and services industries. I didn’t think much about it until the latest report from the Bureau of Labor Statistics confirmed that the trend is likely continuing into 2022 as November 2021 showed even more record-breaking resignations than in September. What is the outlook in our little section of the economy called cybersecurity? Where did this trend of resignations come from? How do we stop it?
Domino 1 of 5: Work From Home
Looking back to the beginning of 2020, we started the year with budgets and start of year kickoffs and face-to-face events like RSA in San Francisco. But by Mid-March, everything had changed. Kids couldn’t go to school, work was 100% remote unless you were in services or healthcare, and companies downsized. This set the context for what would come next for cybersecurity. The first domino fell.
Domino 2 of 5: Remote Access Surge

For business to survive, enterprises large and small needed to launch unforeseen projects deploying VPNs, remote gateways, and access controls for employees and partners. VPN usage surged as countries responded to the pandemic. And at CyCognito, we saw as much as 600% increase in these services from Feb 2020 to Feb 2021 throughout all monitored attack surfaces. In other words, in some cases an attack surface would have as few as 1:200 remote services increasing to 1:32 systems for remote access. The rush to deploy this vital infrastructure came with time pressure and limited resources. The old project mantra held true: you can have it good, fast, and cheap, but you can only pick two. As the Cybersecurity & Infrastructure Security Agency (CISA) noted, constrained on fast and cheap, good security fell by the wayside as organizations struggled to keep the lights on. The second domino began its descent.
Domino 3 of 5: High-Profile Breaches

Cybercriminals and state actors — also working from home I imagine — took advantage of this rush to execute tremendously damaging and expensive cyber attacks. The SUNBURST SolarWinds breach compromised companies via their supply chain; a vector previously assumed to be secure. Then Microsoft Exchange systems were targeted leading to cleanup that continues to this day. And we had Accellion, Colonial Pipeline, and finally to round out 2021 and beyond, Log4Shell. These high profile breaches raised awareness of the threats and how supply chain risks affect everyone. More than ever, defenders are feeling the burden of their positions.The third domino took a hit.
Domino 4 of 5: Demographics

The fourth domino is demographics and it’s teeter has been predictable for some time. It’s been noted our workplaces seem to be a melting pot of generations and some stereotypes about attitudes and technology adoption write themselves. But with a surging stock market and incentives for voluntary layoffs several older workers opted to retire rather than continue slugging it out with hyber motivated, well-funded cyber-criminals and nation state actors. Additionally we saw over 1 million fewer students in college.
Domino 5 of 5: Resignation to Demand
The Bureau of Labor Statistics (BLS) estimates the demand for Information Security Analysts will grow by 33% over the next ten years, much faster than the average for all industries of 8%. They further note that many of those openings result from needing replacements for workers transferring to different occupations or exiting the labor force, such as to retire.
Another way to view this is through the lens of job openings. For example, if we look at Cyberseek’s helpful interactive data on this subject, we see 597,767 job openings in cybersecurity out of a total employed workforce of 1,053,468. Put another way, 64% of the desired workforce is doing 100% of the work we need to do. And the problem is just getting worse.
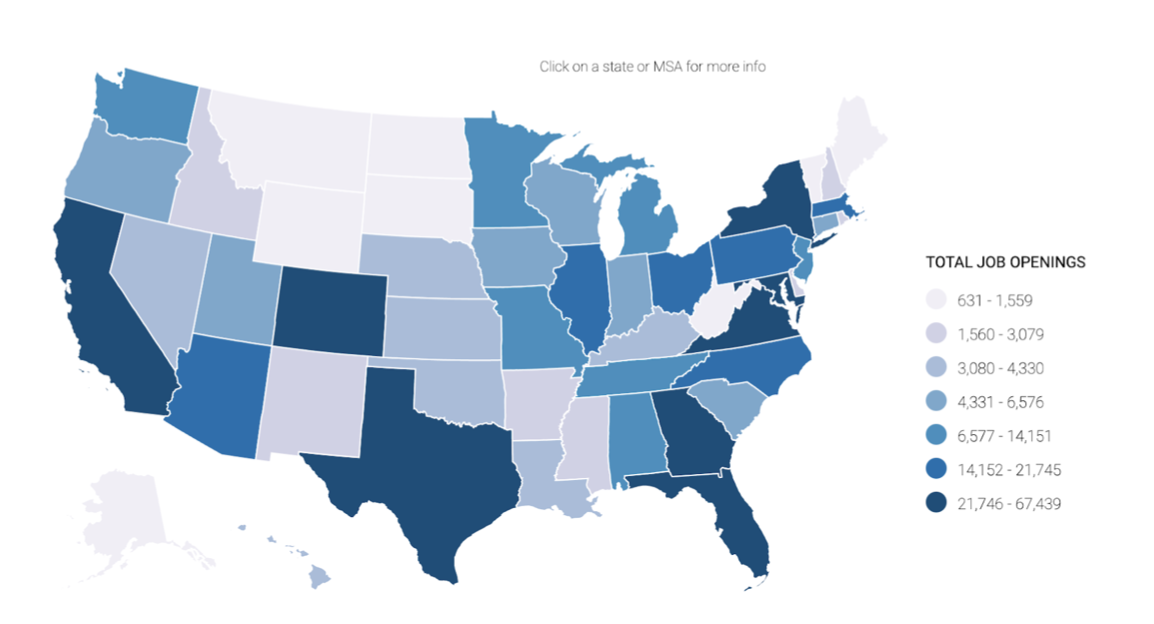
Figure 1 - Cyberseek CYBERSECURITY SUPPLY/DEMAND HEAT MAP showing state-by-state job openings. Interactive map is at: https://www.cyberseek.org/heat...
The ever increasing adoption of cloud services, expanding dynamic attack surfaces, and a rise in the number and sophistication of cybersecurity threats will increase demand for cybersecurity professionals in all industries reliant on technology for the coming decade. Financial institutions, discrete manufacturing, and other types of corporations will also need to increase their information security capabilities in the face of growing threats. In addition, as the healthcare industry relies more heavily on telehealth, ensuring patients’ privacy and protecting personal data is essential because medical records are orders of magnitude more valuable than other data for sale on the darkweb. The final domino of shortage is poised to tumble.
How to Maintain Your IT Security Team
As these dominos fall, and cybersecurity staffing becomes harder (and it was already pretty darn hard), there are several things that I recommend to combat it:
1) Embrace Automation
Most jobs have a certain amount of tedious, rote work and cybersecurity is no exception. But for most of us, the less of this work we have to do, the more we enjoy our jobs. That’s why it’s necessary for organizations to automate every process they can, enabling their staff to focus on the things that require human intervention and ingenuity.
2) Find solutions to help prioritize the workload
Burnout is a real risk in many fields, including security. Often, burnout happens when team members are consistently overloaded with more work than they can reasonably do in any given day, month, week. Managers can help with this by being clear on priorities across their team, but another way, particular to security and vulnerability management in particular, is by finding solutions that can clearly and meaningfully prioritize which attack vectors to prioritize, in what order. That way, the team knows what to work on today and what can be pushed off to tomorrow.
3) Recognize that hybrid work is here to stay
Yes, there are some teams, some industries, and some job functions that may well need to come into the office. However, for all others, in order to attract and retain the best talent, as the world opens up again after 2 years of lockdowns, it’s important to recognize that people have gotten used to and now expect to be able to maintain some level of ability to work remotely. In the fight for the best talent, don’t let this be the area that your team falls short.
4) Make room for and prioritize career growth
Give them time to take continuing education, and push your HR team to formalize a mentorship/career growth path.
5) Foster psychological safety by being prepared
Security is the frontlines in this increasingly cyber-converged world we live in. Fighting the good fight against attackers is a day in and day out, 24/365 job and stressor. This “Surface Pressure” (if you’ve heard the song from Encanto) takes a toll on the wellbeing and mental health of the team. One way to help team members mitigate the stress, so they don’t choose to join the Great Resignation, is to create a workplace environment where they don’t feel that their jobs may well be on the lines if the company is breached. As we all know, “it’s not if, but when.” First, focus on setting up a best-in-class set of solutions for proactive security to establish that strong wall keeping attackers out. Beyond that, do everything you can to be prepared to quickly and clearly answer when executives or the board ask about the organization’s exposure to a high-profile incident like Log4j or SolarWinds with data. And if the worst should happen and you have been breached, be sure you already have a response plan in place with legal, the executive team, and all other stakeholders so you don’t have to scramble at the 11th hour to work this out. See my response checklist and tips on disclosure best practices to help get you started.
6) Try CyCognito automation that virtually grows your team so they thrive
CyCognito’s platform is designed from the ground up to automate external attack surface management and prioritize the riskiest security gaps which means more satisfying and valuable work for your cybersecurity workforce. We supplement existing efforts aimed at reducing enterprise risk with our automation and AI, then merge that intelligence with security workflows to help shut down attacks before they happen which gives your teams an edge in the battle against attackers. I’m certainly biased, but give us a look to help your recruitment and retention efforts by taking some of the burden off of security and offloading it to our platform.
If you’d like to learn more check out our demo video and customer testimonials.



