



The CyCognito platform helps you eliminate critical attack vectors with a continuously updated and prioritized view of your attacker-exposed IT ecosystem. You and your security team can use the CyCognito platform to pinpoint critical risks just as attackers do.
Organizations that still have to perform legacy external testing to meet customer agreements or compliance regulations use the CyCognito platform to augment and optimize those processes by focusing the legacy tests on the areas of greatest risk that the CyCognito platform has identified.
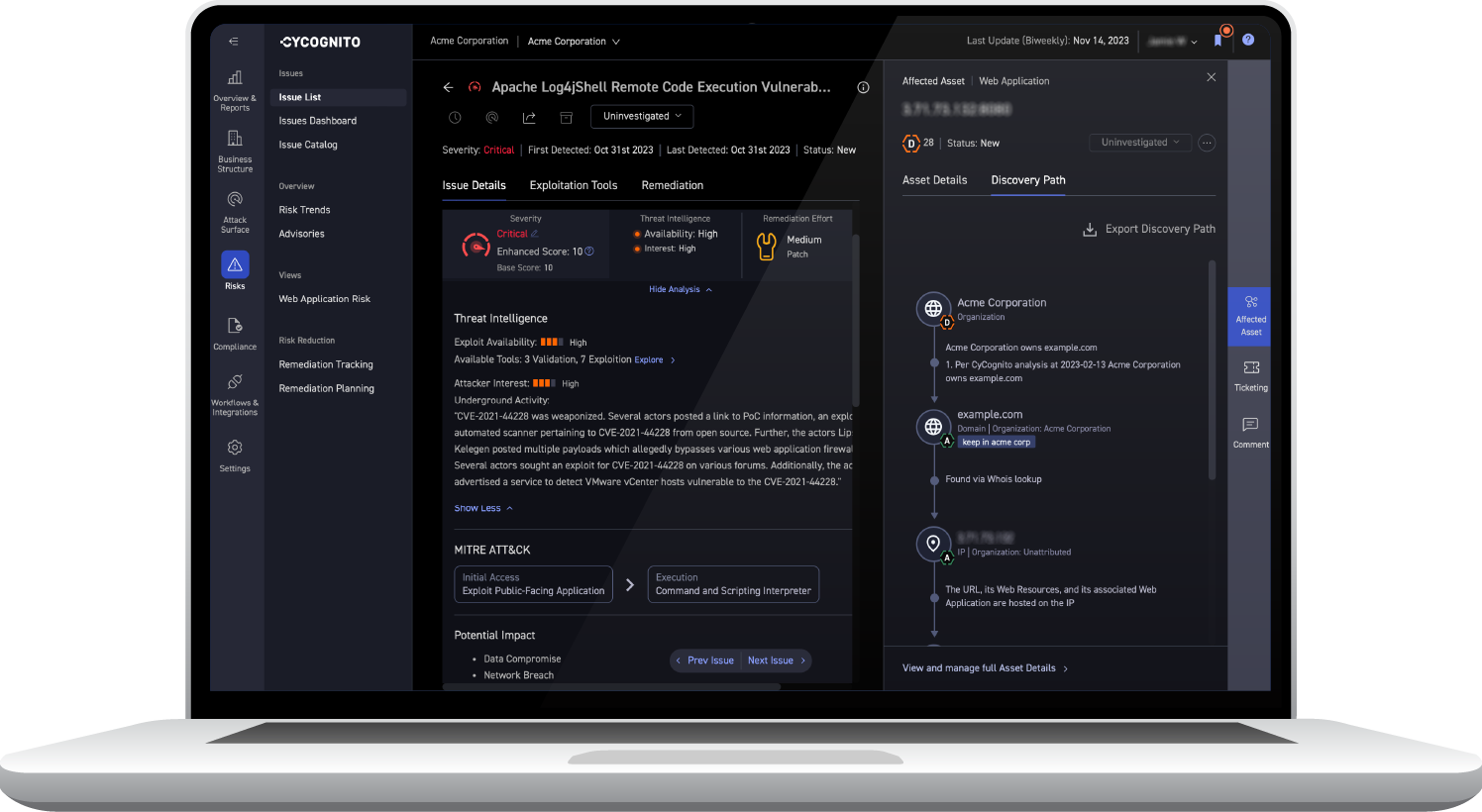
Continuous security monitoring is essential for maintaining visibility on the evolving attack surface. CyCognito solves one of the most fundamental business problems in cybersecurity: understanding how attackers view your organization from an external perspective, including paths of least resistance to internal assets.
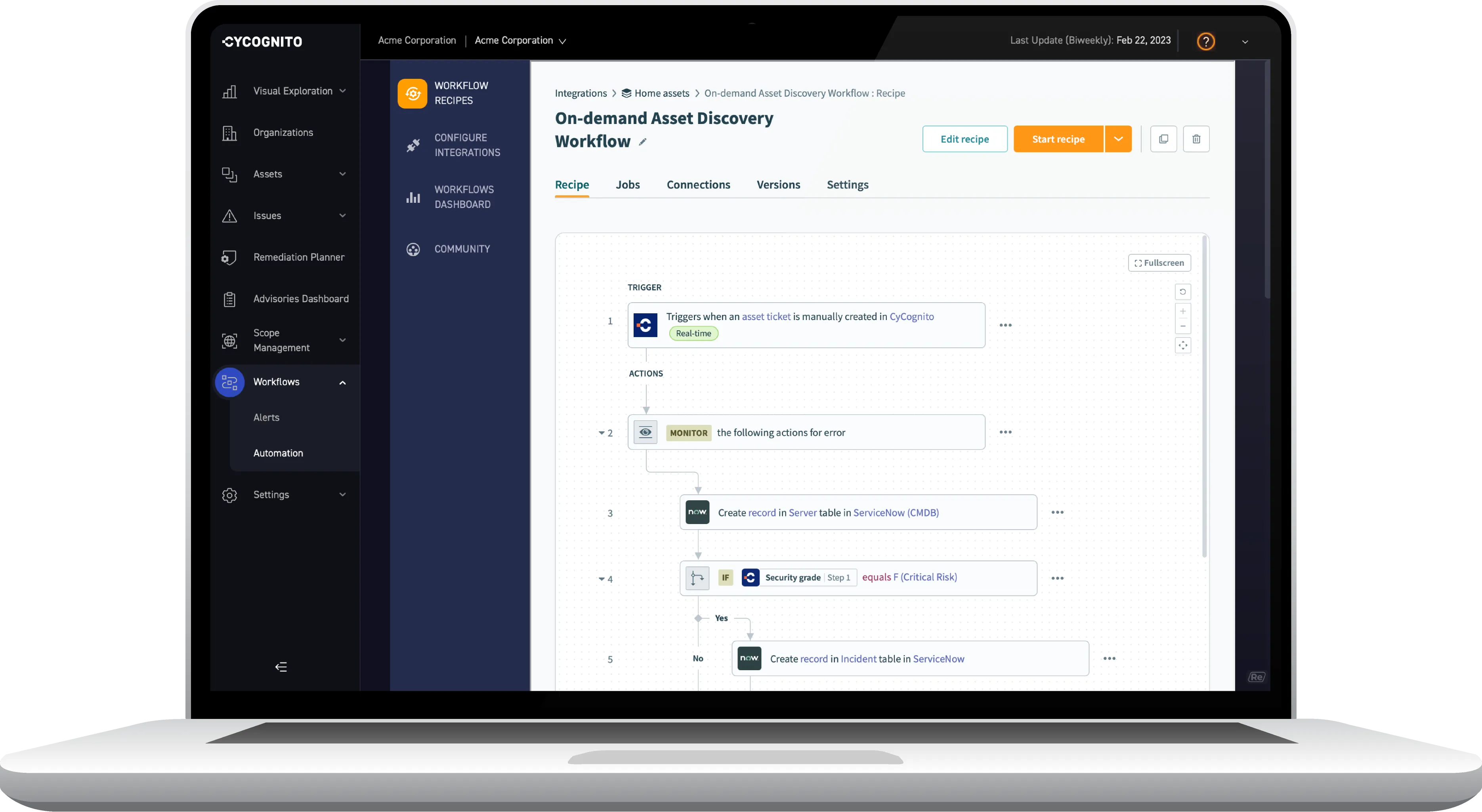
Configurable workflows and automations help get all the right information in the right places right away. CyCognito integrates seamlessly with leading ticketing systems, SIEMs and vulnerability management platforms, including ServiceNow, Jira, ZenDesk, Tenable, and Splunk.
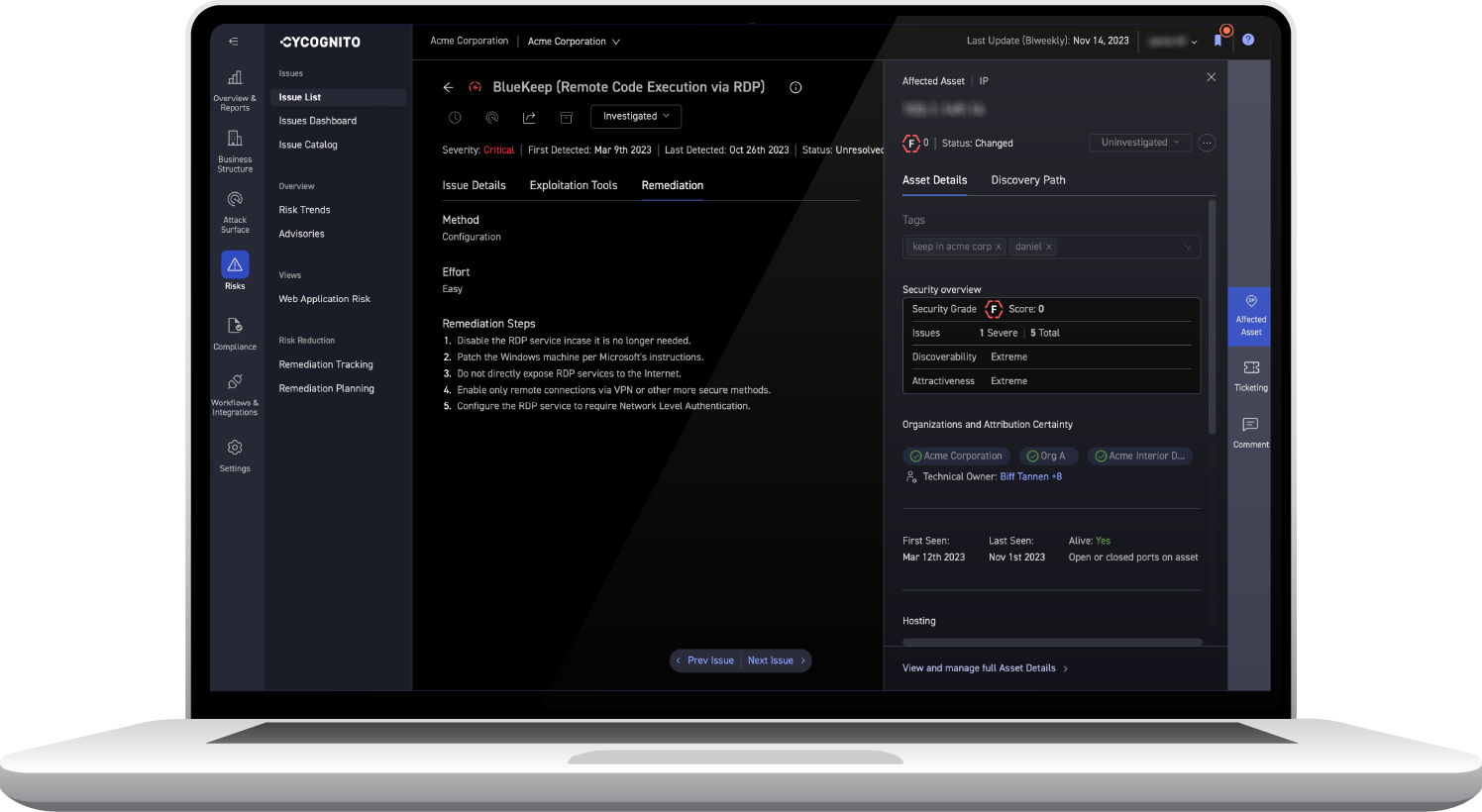
The CyCognito platform streamlines communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and validated remediation instructions.
Darrell Jones | Chief Information Security Officer
Ares Management Corporation, Kaiser Permanente
Darrell Jones
Chief Information Security Officer
Ares Management Corporation, Kaiser Permanente